Cybersecurity Services For Building Cyber Resilience Theresa A.
37 Slides3.15 MB

Cybersecurity Services For Building Cyber Resilience Theresa A. Masse Cyber Security Advisor – Region 10 (Oregon) Cybersecurity and Infrastructure Security Agency March 10, 2022

2

3

CYBERSECURITY AND RESILIENCE 4

Resilience Defined “ the ability to prepare for and adapt to changing conditions and withstand and recover rapidly from disruptions. Resilience includes the ability to withstand and recover from deliberate attacks, accidents, or naturally occurring threats or incidents ” - Presidential Policy Directive 21 February 12, 2013 Protect (Security) Sustain (Continuity) Perform (Capability) Repeat (Maturity) 5

CISA Shields Up Constantly updating Shields Up webpage www.cisa.gov/shields-up Reduce the likelihood of a damaging cyber intrusion Ensure that software is up to date, prioritizing updates that address known exploited vulnerabilities identified by CISA. Take steps to quickly detect a potential intrusion Ensure that the organization is prepared to respond if an intrusion occurs Maximize the organization's resilience to a destructive cyber incident 6

CISA Shields Up CISA Resources CISA Insights: Preparing for and Mitigating Forei gn Influence Operations Targeting Critical Infrast ructure (pdf) (February 2022) CISA Insights: Implement Cybersecurity Measure s Now to Protect Against Potential Critical Threat s (pdf) (January 2022) CISA Insights: Preparing For and Mitigating Pote ntial Cyber Threats (pdf) (December 2021) Russia Cyber Threat Overview and Advisories 7

CISA Shields Up CISA Tools COVID-19 Disinformation Toolkit Free Public and Private Sector Cybersecurity Tool s and Services Mis-, Dis-, and Malinformation Resources CISA Releases New Insight to Help Critical Infrast ructure Owners Prepare for and Mitigate Foreign Influence Operations MDM Rumor Control Page Start-Up Guide 8
CISA – Stop Ransomware Visit – CISA.gov/stopransomware Guidance & Resources Good Cyber Hygiene Habits Keep Your Network Healthy Backing Up is Your Best Bet When in Doubt – Report it Out Keep Calm and Patch On 9

CISA CYBERSECURITY SERVICES 10

Range of Cybersecurity Assessments Vulnerability Scanning TECHNICAL Web Application Scanning Phishing Campaign Assessment Remote Penetration Test Risk and Vulnerability Assessment Cyber Protective Visit Cyber Resilience Review External Dependencies Management Cyber Infrastructure Survey Cybersecurity Evaluations Tool STRATEGIC 11

Cyber Hygiene System & Application Vulnerability Scanning CRITICAL Automated scanning of Internet accessible systems Helps individual customer understand their exposure HIGH MEDIUM LOW Informs national risk management efforts Weekly reports that include current scan results, historic trends, and result comparisons to the national average No wait time for service; duration - Ongoing NONE Unlimited capacity of subscribers INACTIVE 12

Cyber Hygiene (CH) - FAQ What information is included in the report? – A listing of systems detected, open ports, services/applications (with version number) and operating system running on those systems – A listing of known vulnerabilities (if any) specific to the applications running – A listing of vulnerabilities identified on each system – For comparison statistics, non-attributable Federal Totals & Averages for all previous data points will be provided – Reports will also provide trending/history and highlight any delta’s between the current and previous report What value will be provided In addition to providing a free, 3rd party, objective perspective of the vulnerabilities present and risks to your Agency's Internet connected assets, participation will benefit the Federal government as a whole. A major objective is to provide non-attributable but quantifiable data to leadership to ensure initiatives and policy directives are well informed, fact based, and focused on areas with the greatest need. 13 13

Cyber Hygiene Web Application Scanning CRITICAL HIGH MEDIUM Internet scanning-as-a-service Assesses the “health” of publicly accessible web applications Maintain enterprise awareness of publicly accessible web-based assets Provide insight into how systems and infrastructure appear to potential attackers LOW NONE Drive proactive mitigation of vulnerabilities to help reduce overall risk INACTIVE Informs national risk management efforts 14

Cyber Hygiene: Web Application Scanning (WAS) The CISA Assessments team supports Federal, State, Local, Tribal and Territorial Governments and Critical Infrastructure partners by providing proactive testing and assessment services. CISA’s Cyber Hygiene Web Application Scanning is “internet scanning-as-aservice.” This service assesses the “health” of your publicly accessible web applications by checking for known vulnerabilities and weak configurations. Additionally, we can recommend ways to enhance security in accordance with industry and government best practices and standards. SCANNING OBJECTIVES Maintain enterprise awareness of your publicly accessible web-based assets Provide insight into how systems and infrastructure appear to potential attackers Drive proactive mitigation of vulnerabilities to help reduce overall risk SCANNING PHASES AND OVERALL PROCESS Scanning Phases Discovery Scanning: Identify active, internet-facing web applications Vulnerability Scanning: Initiate non-intrusive checks to identify potential vulnerabilities and configuration weaknesses OVERALL PROCESS Plannin g Request service (Existing Cyber Hygiene Customers) Provide target list (scope) Confirm scanning schedule Pre-scan notification Executi on Initial discovery scan of submitted list Conduct vulnerability scan Reporti ng Provide detailed report of findings Follow on discussion (if necessary) to review 15

Cyber Hygiene Phishing Evaluations and Campaigns Measures propensity to click on phishing lures Library of crafted emails of varying levels of sophistication (obvious to stealthy) and targeting (general to targeted) Sent without warning and at random Can be used to test technical controls, user awareness and susceptibility Helps provide focused guidance and justify additional resources 16

Phishing Campaign Assessment (PCA) Week Campaign Please Help! Date Sent Complexity User Click Level Rate 3/18/16 1 0.17% # Emails Sent 401 1 2 3 4 5 6 Reveal Your Past Password Expire Alert Severe Weather Checklist Federal Employee Survey Salary Guidelines 3/31/16 4/6/16 4/15/16 4/20/16 4/27/16 402 401 402 401 402 2 3 4 5 6 2.54% 12.62% 7.41% 15.57% 32.03% 17 17

Cyber Hygiene Remote Penetration Testing Emphasis on the perimeter and rapid identification and elimination of external vulnerabilities and attack paths prior to their exploitation by a malicious external actor Leverages all of the other Cyber Hygiene services and data collected as a starting point Ideal for testing centralized data repositories and assets accessible online 18

Remote Penetration Testing SCENARIOS External Penetration Test: Verifying if the stakeholder network is accessible from the public domain by an unauthorized user by assessing open ports, protocols, and services. External Web Application Test: Evaluating web applications for potential exploitable vulnerabilities; the test can include scanning, manual testing, or a combination of both methods. automated Phishing Assessment: Testing the stakeholder email infrastructure through carefully crafted phishing emails variety of malicious payloads to the trusted point of contact. containing a Open-Source Information Gathering: Identify publicly available information about the stakeholder may be useful in preparing for an attack. environment which ASSESSMENT OBJECTIVES Conduct assessments to identify vulnerabilities and work with customers to eliminate exploitable pathways. Simulate the tactics and techniques of real-world threats and malicious adversaries. Test centralized data repositories and externally accessible assets/resources. Avoid causing disruption to the customer’s mission, operation, and network infrastructure. ASSESSMENT TIMELINE Pre-Planning Planning Request RPT Receive RPT Capabilities Brief Sign and return RPT Rules of Engagement Determine RPT services, scope, and logistics during preassessment call(s) Confirm schedule Establish trusted points of contact Execution (Up to Six Weeks) Dependent on resource availability Critical findings are immediately disclosed Reporting Briefing and initial recommendation s Final report review and receipt – 10 days 19

Risk Evaluation Risk and Vulnerability Assessment One-on-one engagements with customers that combine national threat and vulnerability information with data collected and discovered through onsite assessment activities Provides customers risk analysis reports with actionable remediation recommendations prioritized by risk Components include scenario-based network penetration testing, web application testing, social engineering testing, wireless testing, configuration management reviews of servers and databases, and operational response maturity evaluation. 20
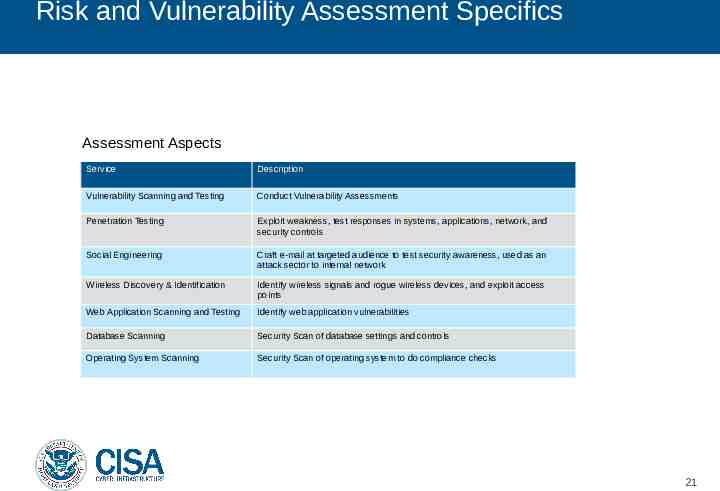
Risk and Vulnerability Assessment Specifics Assessment Aspects Service Description Vulnerability Scanning and Testing Conduct Vulnerability Assessments Penetration Testing Exploit weakness, test responses in systems, applications, network, and security controls Social Engineering Craft e-mail at targeted audience to test security awareness, used as an attack sector to internal network Wireless Discovery & Identification Identify wireless signals and rogue wireless devices, and exploit access points Web Application Scanning and Testing Identify web application vulnerabilities Database Scanning Security Scan of database settings and controls Operating System Scanning Security Scan of operating system to do compliance checks 21

Cyber Protective Visit One-on-one engagement (either virtual or onsite) with customers focused on a broad range of cyber security topics Generally takes about 45 minutes Provides customers with an updated assessment and additional information requested during the discussion. Information gathered is only aggregated 22

Incident Management Planning Helps Mitigate Effects 1. Get leadership support for incident management planning. 2. Establish an event-detection process. 3. Establish a triage-and-analysis process. 4. Establish an incident-declaration process. 5. Establish an incident-response and recovery process. 6. Establish an incident-communications process. 7. Assign roles and responsibilities for incident management. 8. Establish a post-incident analysis and improvement process. Resource: CRR Supplemental Resource Guide, Incident Management. 23

Cyber Exercises and Planning CISA’s National Cyber Exercise and Planning Program develops, conducts, and evaluates cyber exercises and planning activities for state, local, tribal and territorial governments and public and private sector critical infrastructure organizations. Exercise Planning and Conduct Cyber Exercise Consulting and Subject Expertise Support Cyber Planning Support Off-the-Shelf Resources 24
Malware Analysis To submit malware: Email submissions to NCCIC at: [email protected] Send in password-protected zip file(s). Use password “infected.” Upload submission online: https://malware.us-cert.gov 25

Protected Critical Infrastructure Information Program Protected Critical Infrastructure Information (PCII) Program Guards Your Information Sensitive critical infrastructure information voluntarily given to CISA is protected by law from Public release under Freedom of Information Act requests, Public release under State, local, tribal, or territorial disclosure laws, Use in civil litigation and Use in regulatory purposes. 26

Criticality of Periodic Assessments Periodic assessments are essential for resilience Can’t protect if you don’t know what needs protection Can’t fix what needs if you don’t know what’s wrong 27

Cyber Resilience Review Purpose: Evaluate operational resilience and cybersecurity practices of critical services. Delivery: Either CSA-facilitated, or Self-administered Benefits include: Helps public and private sector partners understand and measure cybersecurity capabilities as they relate to operational resilience and cyber risk CRR Question Set & Guidance 28
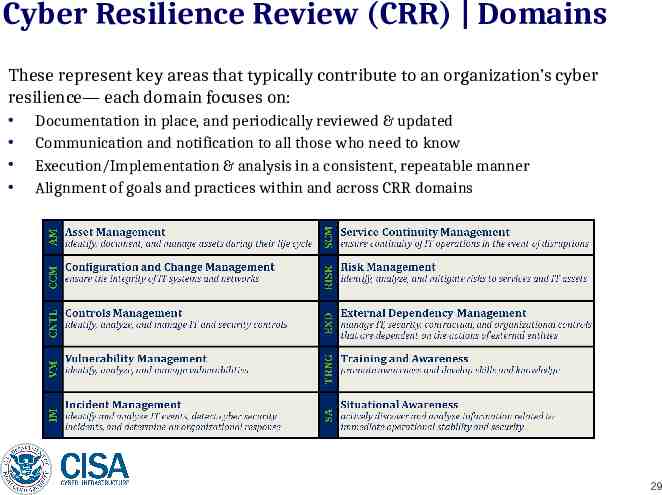
Cyber Resilience Review (CRR) Domains These represent key areas that typically contribute to an organization’s cyber resilience— each domain focuses on: Documentation in place, and periodically reviewed & updated Communication and notification to all those who need to know Execution/Implementation & analysis in a consistent, repeatable manner Alignment of goals and practices within and across CRR domains 29

Cyber Resilience Review (CRR) Maturity Maturity, Not Just Capability: A MIL (Maturity Indicator Level) measures process institutionalization, and describes attributes indicative of mature capabilities. 30
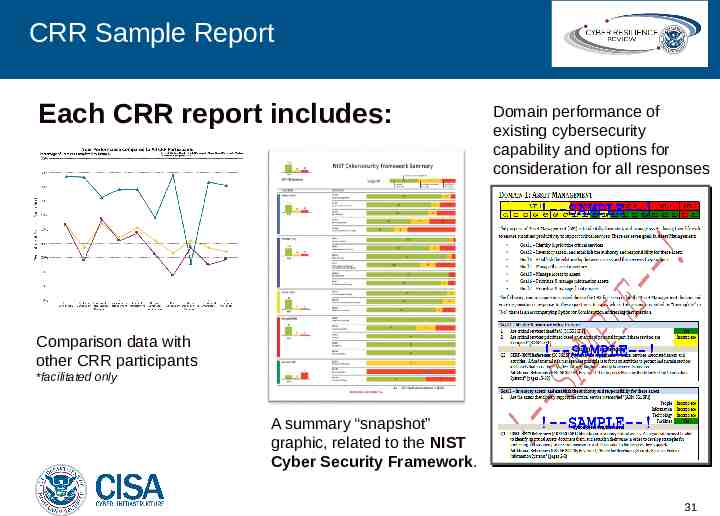
CRR Sample Report Each CRR report includes: Domain performance of existing cybersecurity capability and options for consideration for all responses Comparison data with other CRR participants *facilitated only A summary “snapshot” graphic, related to the NIST Cyber Security Framework. 31

EDM Assessment Organization and Structure External Dependencies Management (EDM) Structure and scoring similar to Cyber Resilience Review Uses one Maturity Indicator Level (MIL) scale with three lifecycle domains. Relationship Formation Assesses whether the acquirer evaluates and controls the risks of relying on external entities before entering into relationships with them. Relationship Management and Governance Assesses whether the acquirer manages ongoing relationships to maintain the resilience of the critical service, and mitigate dependency risk. Service Protection and Sustainment Assesses whether the acquirer accounts for its dependence on external entities as part of its operational activities around managing incidents, disruptions, and threats. 32
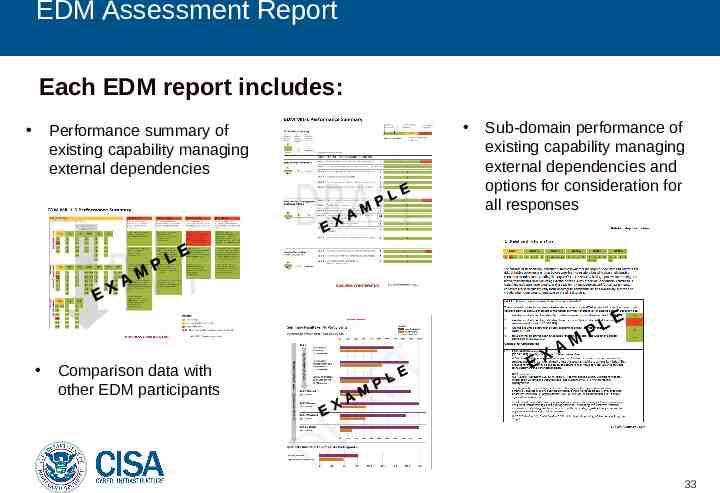
EDM Assessment Report Each EDM report includes: Performance summary of existing capability managing external dependencies Comparison data with other EDM participants Sub-domain performance of existing capability managing external dependencies and options for consideration for all responses A EX M PL E 33

Cyber Infrastructure Survey (CIS) Highlights Purpose: Evaluate security controls, cyber preparedness, overall resilience. Delivery: CSA-facilitated Benefits: Effective assessment of cybersecurity controls in place for a critical service, Easy-to-use interactive dashboard to support cybersecurity planning and resource allocation), and Access to peer performance data visually depicted on the dashboard. 34

R Cyber Security Evaluation Tool Purpose: Assesses control system and information technology network security practices against industry standards. Facilitated: Self-Administered, undertaken independently Benefits: Immediately available for download upon request Understanding of operational technology and information technology network security practices Ability to drill down on specific areas and issues Helps to integrate cybersecurity into current corporate risk management strategy 35

Our Nation’s Cyber Workforce Foundation The National Cybersecurity Workforce Framework is a collection of definitions that describe types of cybersecurity work and skills requires to perform it. When used nationally, the definitions help establish universally applicable cybersecurity skills, training/development, and curricula 7 Categories, 30 Specialty Areas Baselines knowledge, skills, and abilities & tasks Operate & Maintain Securely Provision Analyze Collect & Operate Oversight & Development Protect & Defend Investigate 36

Contact Information CSA Contact Information Theresa A. Masse Cyber Security Advisor, Region 10 (Oregon) Cybersecurity Infrastructure Security Agency U.S. Department of Homeland Security Email: [email protected] Mobile: (503) 930-5671 37






