Pushback: Remedy for DDoS attack Introduction. Overview of Pushback.
10 Slides104.50 KB

Pushback: Remedy for DDoS attack Introduction. Overview of Pushback. Architecture of router. Pushback mechanism. Conclusion.

Introduction DDoS attacks – Disturbance to the global internet. How do DDoS attacks occur? Congestion could be caused by flash crowds too. Non malicious www.Olympics.com during 2000 Sydney Olympics. Victim can do nothing to protect itself. Can anything be done inside the network to defend?

What is Pushback? Pushback - Defense against DDoS. A mechanism that allows a router to request adjacent upstream routers to limit the rate of traffic. Concept - Aggregate congestion control (ACC). Aggregate - Subset of traffic with identifiable property. Congestion Signature - Set of properties of the aggregate identified as causing problems.
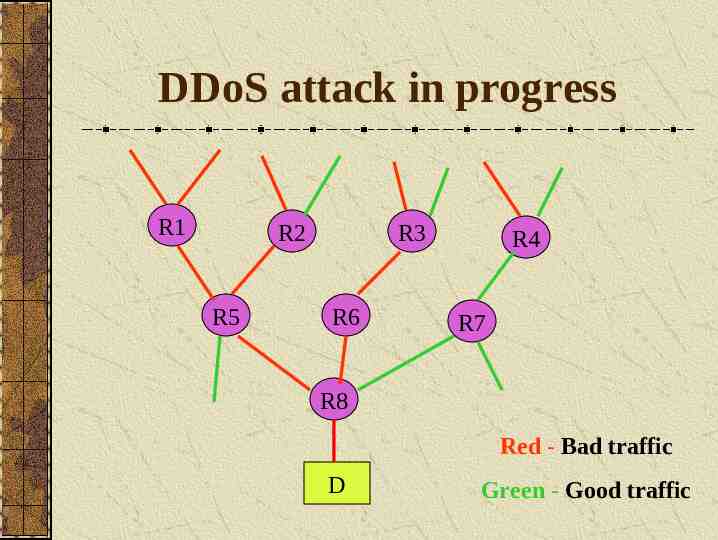
DDoS attack in progress R1 R2 R5 R3 R6 R4 R7 R8 Red - Bad traffic D Green - Good traffic
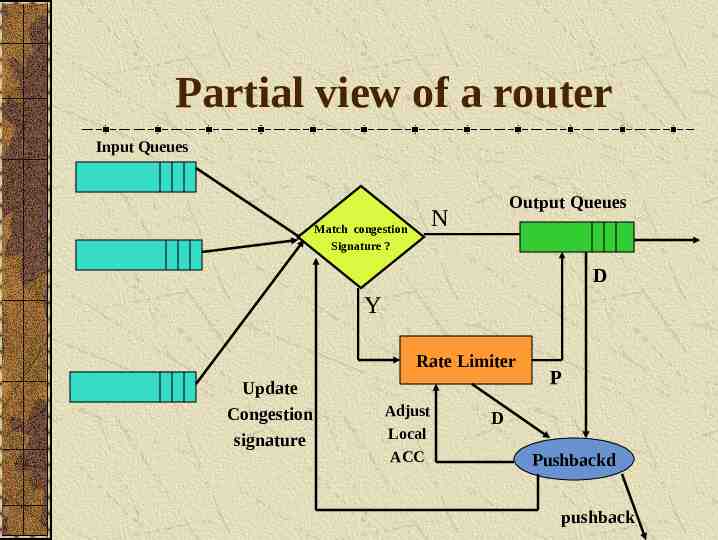
Partial view of a router Input Queues Output Queues N Match congestion Signature ? D Y Rate Limiter Update Congestion signature Adjust Local ACC P D Pushbackd pushback

Dropped Packet Report Is sent by the rate-limiter to the Pushback daemon. Magic Number IP Destination address Input interface Output interface Timestamp Packet size Reason

How does the Pushback daemon identify an attack and the victim? Algorithm Step1: If (wi 1.2 * wo) then attack is in progress. Step2: Dropped packets are grouped according to the longest matching prefix in the routing table. Step3: The prefix with the highest number of dropped packets is the set to be used in step4. Step4: The set in step3 is scanned to find the host to which most of the packets are destined to. Step5: If (wi – wb 1.2 * wo) then repeat steps 2 to 5.

Pushback Request The Pushback daemon uses a pushback request to tell the upstream links about the prefix to ratelimit. Pushback request is as shown below. Congestion Signature Bandwidth Limit Expiration time RLS-ID Depth of Requesting Node

Pushback Response Sends responses downstream. The response is very similar to request as shown here. Congestion Signature Bandwidth Used Time in effect RLS-ID Depth of Requesting Node
Conclusion Conclusion Successfully implemented in the lab under FreeBSD operating system. Deployment becomes complex as it requires lot of resources. Any Questions?