Navigating Compliance Requirements DCM 6.2 Regs and Codes
24 Slides170.39 KB

Navigating Compliance Requirements DCM 6.2 Regs and Codes linford&co llp

Navigating Compliance Requirements Data centers may choose to comply with many different rules and regulations such as, HIPAA, SSAE 16 (f. SAS 70), ISO, LEED, etc. We will break down the requirements and discuss where overlaps exist, how to leverage work between audits, and how to minimize audit impact.

Myriad of Regulations, Frameworks and Standards HIPAA PCI DSS FISMA SSAE 16 / SOC 1 ISO 27001 SOC 2, SOC 3 LEED

HIPAA Health Insurance Portability and Accountability Act of 1996 Privacy rule Security rule – Three types of safeguards Administrative Physical Technical Required vs. addressable specifications Why would a data center choose to be HIPAA compliant? House ePHI for clients

HIPAA Continued How to demonstrate compliance No HIPAA “certification” Self audit Independent audit Cost of compliance Resource to implement required policies and procedures and perform self assessment Independent audit – 10K to 100K – depending on size and complexity Cost of breach

FISMA Federal Information Security Management Act of 2002 Requirements Categorize information systems according to risk level (FIPS 199) Security controls Risk management System security plan Why would a data center need to be compliant with FISMA? House federal agency clients or contractors to federal agencies

FISMA Continued How to demonstrate compliance No FISMA “certification” Independent audit Cost of compliance Resource to implement required policies and procedures, perform risk assessment, implement controls to remediate gaps Independent audit – 20K to 100K – depending on size and complexity

ISO 27001:2005 Information security standards published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) in 2005 Requirements Specifies a security management system Required Every three years Why might a data center choose to be ISO certified? Data center is located outside of the United States Data center does business with European clients

ISO 27001:2005 Continued How to demonstrate compliance Certification by an ISO Registrar Cost of compliance Readiness assessment and consultations necessary Separate ISO Registrar necessary 50K to 100K Every Triennial
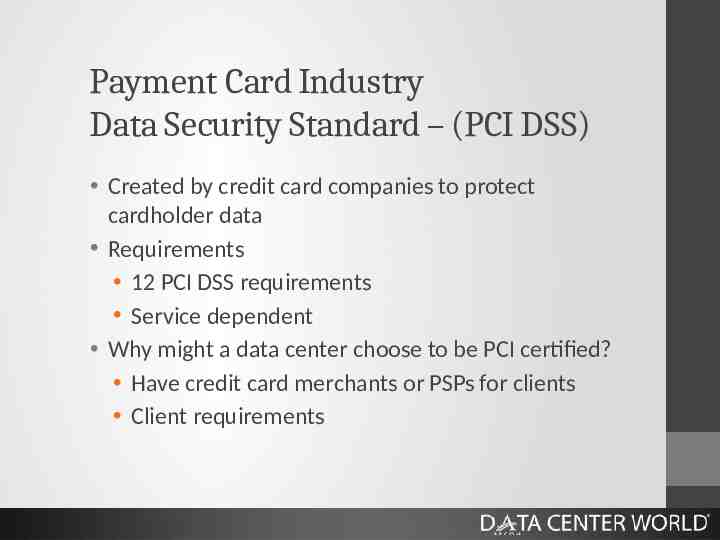
Payment Card Industry Data Security Standard – (PCI DSS) Created by credit card companies to protect cardholder data Requirements 12 PCI DSS requirements Service dependent Why might a data center choose to be PCI certified? Have credit card merchants or PSPs for clients Client requirements

PCI DSS Continued How to demonstrate compliance Self assessment questionnaires (SAQ) PCI Report of Compliance (ROC) Listing on Credit Card Company’s Directory Cost of compliance Only QSAs Can Perform 15K to 100K Per Annum

LEED System LEED - Leadership in Energy and Environmental Design – Designed by the US Green Building Council in 1998. Requirements Voluntary Energy efficiency evaluation Four categories (Certified, Silver, Gold, and Platinum) Why might a data center choose to be LEED certified? Lower operating costs and increased asset value Demonstrate energy efficiency to clients and prospects Qualify for tax rebates, zoning allowances and other incentives

LEED Continued How to demonstrate compliance Project must satisfy LEED prerequisites and earn a minimum of 40 points on a 110 point LEED rating scale Independent, third party verification that a company meets LEED Cost of compliance Implement LEED prerequisites to earn enough points to satisfy desired level of LEED certification – cost varies by project Certifications fees vary by project size, the average cost is 2000

Service Organization Control Audits - SOC 1, 2, 3 SOC 1 / SSAE 16 – (f. SAS 70) – Statement on Standards for Attestation Engagements Internal Controls over Financial Reporting (ICFR) SOC 2 and SOC 3 Security, Availability, Processing Integrity, Confidentiality, or Privacy Detailed vs High-Level Why might a data center choose to obtain a SOC report? Hosting General Ledger or ERP Systems User Auditors’ Requirement

SOC 1, 2, 3 Continued How to demonstrate compliance Internal Controls In Place Design Effectiveness Operating Effectiveness Cost of compliance Only CPA Firms with Specialists Can Perform 15K – 1M Per Annum

Ways to Demonstrate Compliance Internal Testing Independent Audits Various External Audits

Cost of Compliance Expensive Value Judgment How much is the customer or potential customer worth to company? How much are lost or failed opportunities worth? Quality of Audit Firm Reports must be accepted by user organizations Get it right the first time Questions to ask

Framework Overlap Many of the regulations and frameworks overlap How to demonstrate compliance One audit, multiple reports
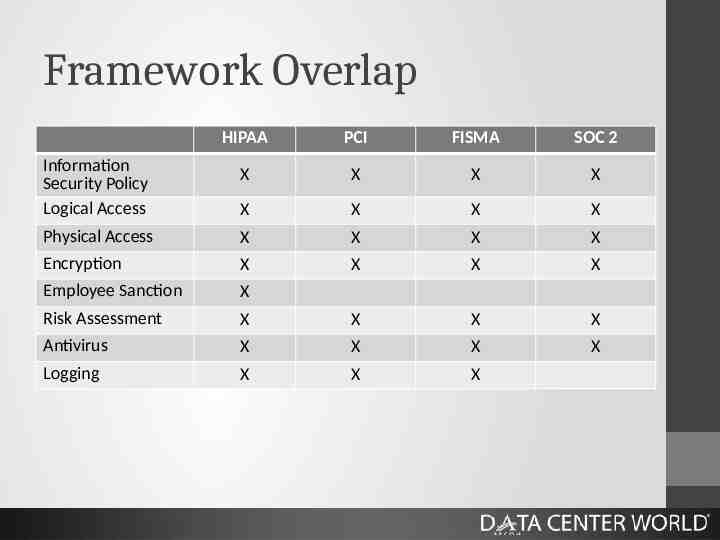
Framework Overlap HIPAA PCI FISMA SOC 2 X X X X X X X X Physical Access X X X X Encryption X X X X Employee Sanction X Risk Assessment X X X X Antivirus X X X X Logging X X X Information Security Policy Logical Access

Framework Drilldown Risk management is a common theme within many information security standards HIPAA - 164.308(a)(1)(ii)(A) FISMA - §3544(a)(b)(1) ISO 27001 – Clause 4.2.1 SOC 2 – 3.1 within the Security, Availability, Processing Integrity, and Confidentiality Trust Services Principles PCI – 12.2.1
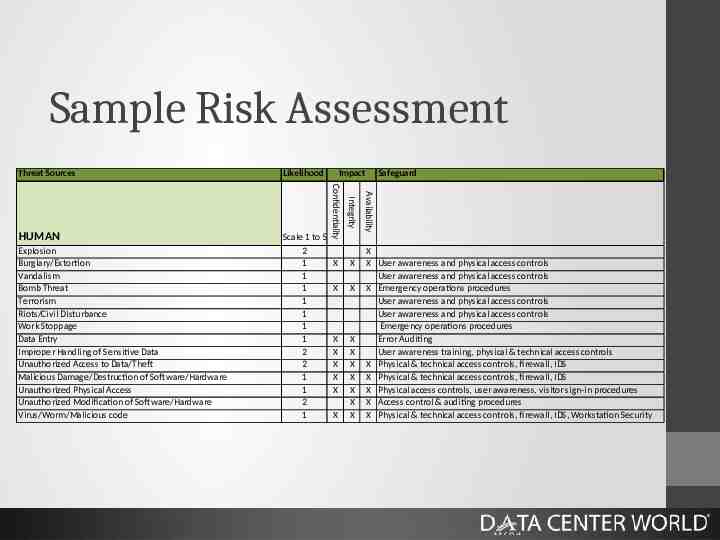
Sample Risk Assessment Scale 1 to 5 2 1 1 1 1 1 1 1 2 2 1 1 2 1 Explosion Burglary/Extortion Vandalism Bomb Threat Terrorism Riots/Civil Disturbance Work Stoppage Data Entry Improper Handling of Sensitive Data Unauthorized Access to Data/Theft Malicious Damage/Destruction of Software/Hardware Unauthorized Physical Access Unauthorized Modification of Software/Hardware Virus/Worm/Malicious code X X X X X X X X X X X X X X X X X Safeguard Availability HUMAN Impact Integrity Likelihood Confidentiality Threat Sources X X User awareness and physical access controls User awareness and physical access controls X Emergency operations procedures User awareness and physical access controls User awareness and physical access controls Emergency operations procedures Error Auditing User awareness training, physical & technical access controls X Physical & technical access controls, firewall, IDS X Physical & technical access controls, firewall, IDS X Physical access controls, user awareness, visitor sign-in procedures X Access control & auditing procedures X Physical & technical access controls, firewall, IDS, Workstation Security

Tips for Successfully Passing an Audit 1. Have one or more established, positive, goals 2. Establish expectations with training 3. Evaluate your strengths, assess your weaknesses, identify your exposures 4. Review prior audit results 5. Practice, practice, practice

Tips for Successfully Passing an Audit – Cont. 6. Copy when you can 7. Be ready to respond as issues arise 8. Coaching staff 9. Document and train on processes 10. Have fun!

Thank You Newel Linford and Robert Pierce [email protected] [email protected] www.linfordco.com linford&co llp