Information Technology Security: Fitting Into the Big Picture
51 Slides3.22 MB

Information Technology Security: Fitting Into the Big Picture Brandon Hoffman, KPMG LLP

Topics for Discussion Typical IT Security Technical Work Intrusion Detection/Prevention Ethical Hacking/Penetration Testing IT Security in the Business Risk, Audit Support, Compliance Policies, Standards, and Procedures IT Security’s Role in Creation and Enforcement

Intrusion Detection Intrusion Detection Systems are just what they seem to be. Detect and Alert Host How Based and Network Based they work? Statistical Modeling Heuristics Trending End result? Similar to home security system

Intrusion Prevention Systems Actively participates in defense of security violations Host based IPS: Resident to the host machine. Monitors system calls and inbound traffic. Creates a baseline and can prevent internal “bad” behavior through system controls. Typically works in conjunction with Anti-virus Sandboxing – Creates isolated “scratch” disk space to run untrusted platforms or applications from untrusted third parties
Intrusion Prevention cont’d Network based IPS has several operating modes or implementations: Inline IPS is directly inline with the data stream similar to a firewall Gateway Interaction performs packet analysis interactively with the router/firewall
Intrusion Prevention cont’d Network intrusion prevention action methods: Content based – Inspects packet contents for unique sequences or “signatures” to prevent known attacks Protocol analysis – Decodes known protocols to detect anomalous behavior Rate based – Used to prevent Denial of Service attacks
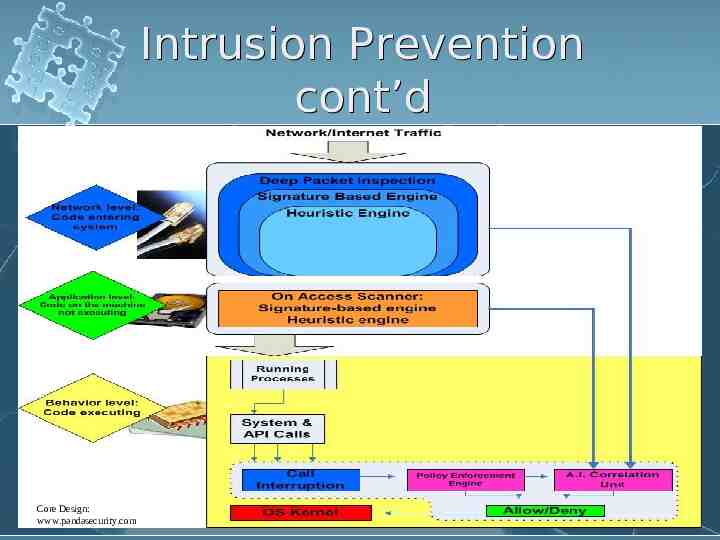
Intrusion Prevention cont’d Core Design: www.pandasecurity.com

IPS Business Case 1 Company X requires a homogeneous solution due to compliance and governance restrictions. The facts: Cisco is the network hardware provider for all communications. All connections need to be monitored: VOIP Hosts Gateways VPN Routers and Switches Ingress/Egress traffic (Firewall) The aggregation point for analysis and statistics must be built on a windows server platform The solution must be licensed The solution should not be built on open source code Support from the vendor must be highly available regardless of cost
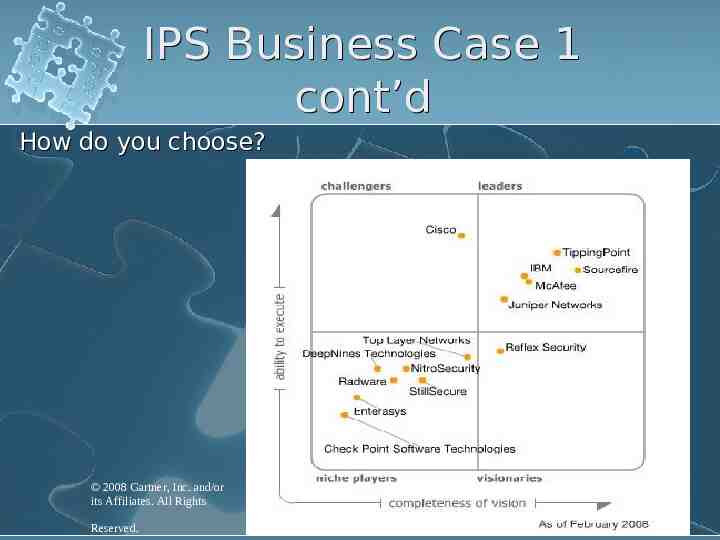
IPS Business Case 1 cont’d How do you choose? 2008 Gartner, Inc. and/or its Affiliates. All Rights Reserved.

IPS Business Case 1 cont’d Cisco Solutions Sourcefire Solutions Points to consider: Points to consider: Homogeneous solution Homogeneous solution Proprietary Code Base Visionary Leader Supreme Support Controls SNORT signature Current Vendor engine Management easy but Cost Potentially lacking not intuitive Fewer vulnerability support New vendor signatures Cost Technically complicated Open Source based
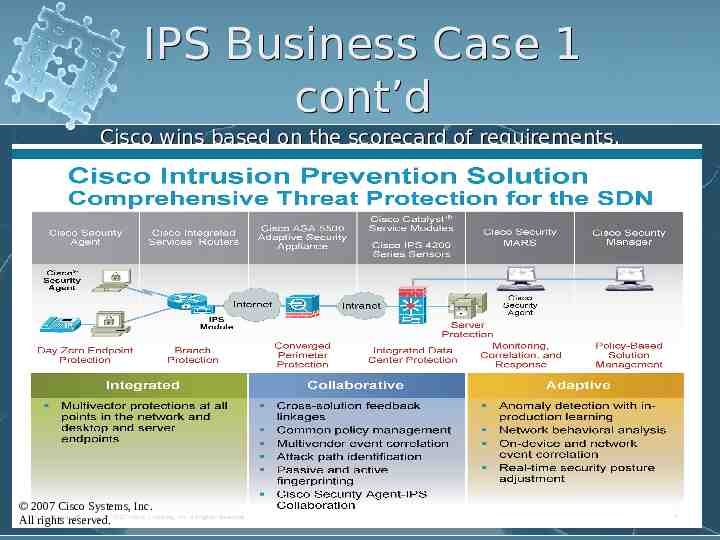
IPS Business Case 1 cont’d Cisco wins based on the scorecard of requirements. 2007 Cisco Systems, Inc. All rights reserved.
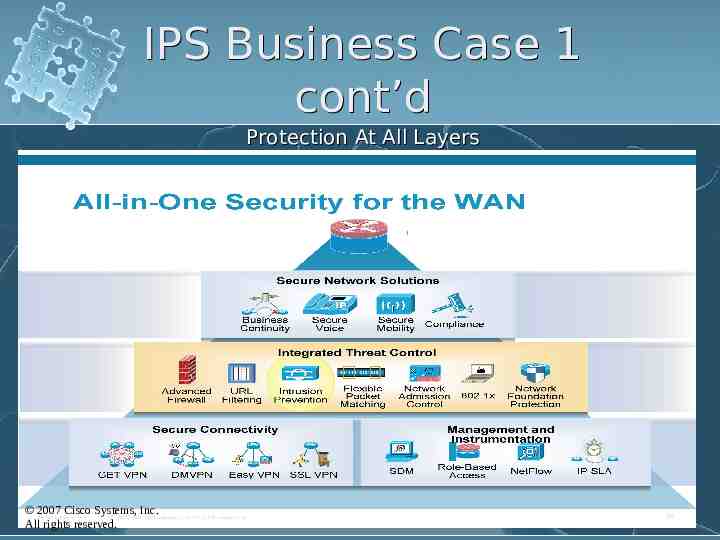
IPS Business Case 1 cont’d Protection At All Layers 2007 Cisco Systems, Inc. All rights reserved.

Ethical Hacking Ethical hacking is a very common profession within the IT security industry. White hat, Grey hat, Black hat Sometimes synonymous with penetration testing – A method of assessing the security posture of a system or network by simulating an “attack”
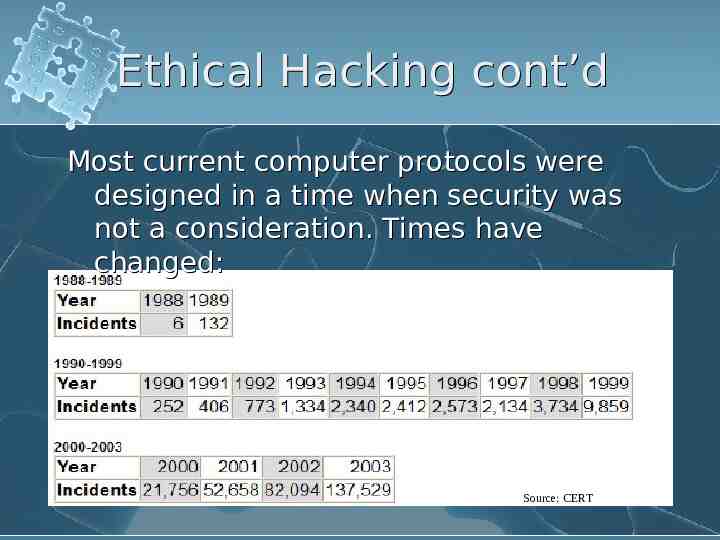
Ethical Hacking cont’d Most current computer protocols were designed in a time when security was not a consideration. Times have changed: Source: CERT

Ethical Hacking cont’d Why perform an ethical hack? Determine flaws and vulnerabilities Provide a quantitative metric for evaluating systems and networks Measure against pre-established baselines Determine risk to the organization Design mitigating controls
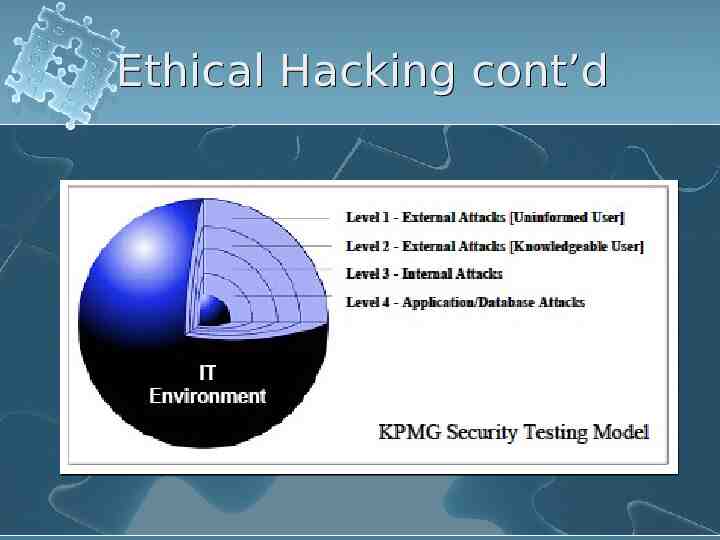
Ethical Hacking cont’d
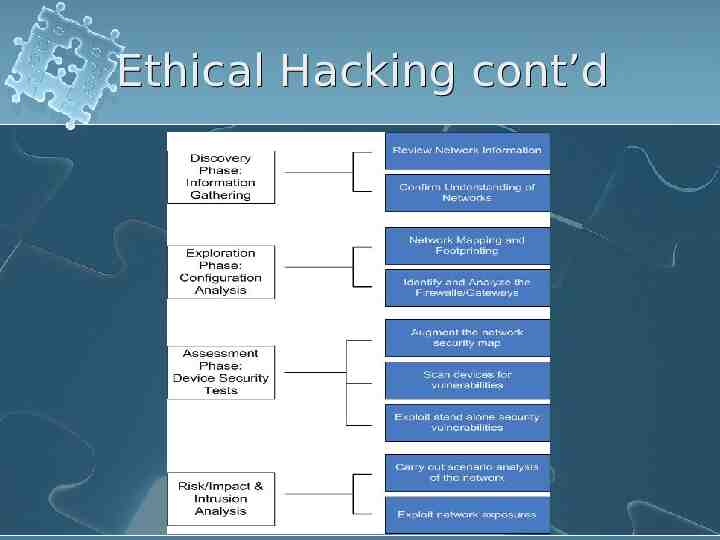
Ethical Hacking cont’d
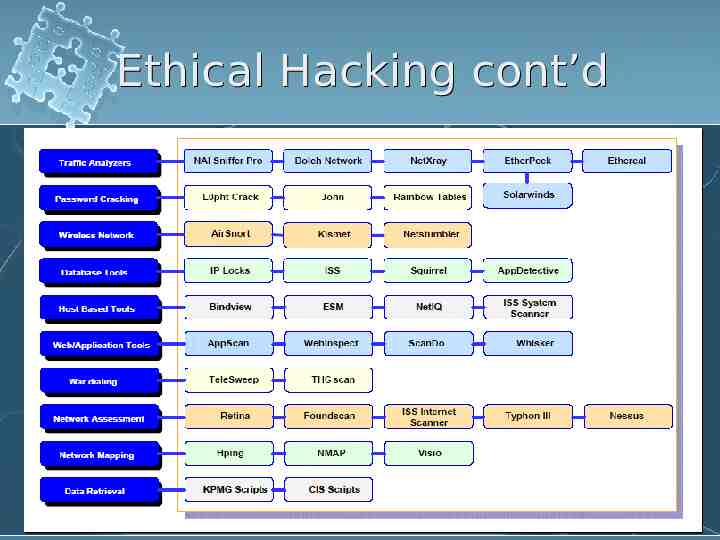
Ethical Hacking cont’d

Ethical Hacking cont’d We will now explore some free tools and simple techniques to break into a machine. Disclaimer: Don’t Try This At Home Statute 1030, Fraud and Related Activity in Connection with Computers, specifically states that whoever intentionally accesses a protected computer without authorization, and as a result of such conduct, recklessly causes damage or impairs medical treatment, can receive a fine or imprisonment of five to 20 years. http://www.usdoj.gov/criminal/cybercrime/1030NEW.htm Cyber Security Enhancement Act 2002 implicates life sentences for hackers who 'recklessly' endanger the lives of others, and several U.S. statutes address cyber crime. http://www.usdoj.gov/criminal/cybercrime/homeland CSEA.htm
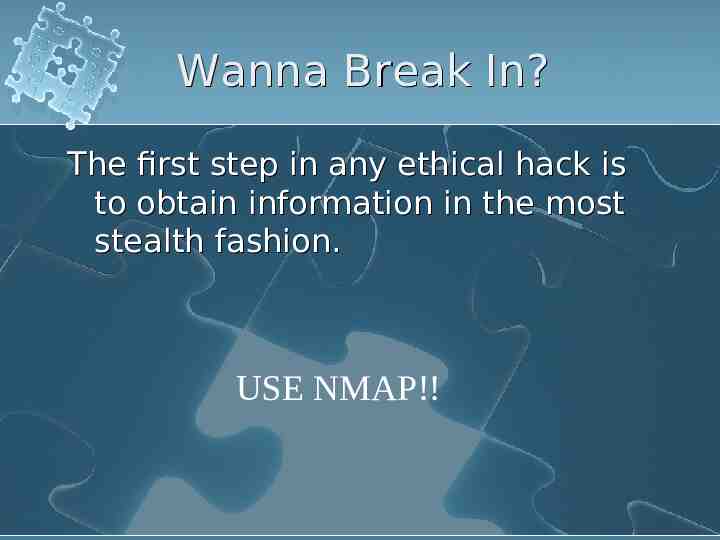
Wanna Break In? The first step in any ethical hack is to obtain information in the most stealth fashion. USE NMAP!!
NMAP nmap is an open-source port/security scanner http://insecure.org/ It’s primary function is the discovery and mapping of hosts on a network nmap is consistently voted as one of the most used security tools

NMAP Host Discovery – Identifying computers on a network Port Scanning – Enumerating the open ports on one or more target computers Version Detection – Interrogating listening network services listening on remote computers to determine the application name and version number OS Detection – Remotely determining the operating system from network devices
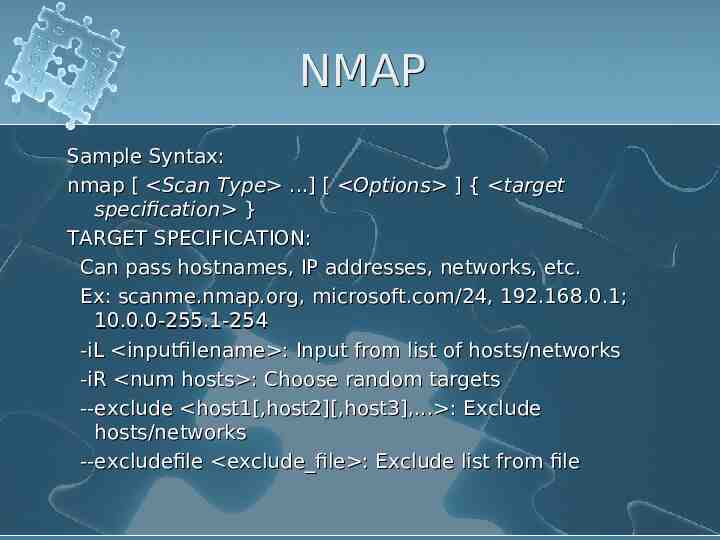
NMAP Sample Syntax: nmap [ Scan Type .] [ Options ] { target specification } TARGET SPECIFICATION: Can pass hostnames, IP addresses, networks, etc. Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254 -iL inputfilename : Input from list of hosts/networks -iR num hosts : Choose random targets --exclude host1[,host2][,host3],. : Exclude hosts/networks --excludefile exclude file : Exclude list from file
NMAP cont’d Analyze your results: NMAP OUTPUT PRINTED

Vulnerabilities Find any hosts worthwhile? Your next step should be scanning for exploitable vulnerabilities. USE NESSUS!!! Copyright 2002 - 2009 Tenable Network Security(R). All Rights Reserved.
Nessus Nessus is an open-source vulnerability scanner Public domain software, such as Nessus, isn't always inferior and sometimes it is actually superior ! Technical support available at tenablesecurity.com Three steps 1. Run a port-scan (using nmap) on the target host to determine which ports are open 2. Once open ports are identified, Nessus runs a set of exploits on the open ports. Nessus assumes standard processes run on standard ports (i.e., http on port 80) 3. Check for and reporting vulnerabilities
Nessus Vulnerability checks are implemented through plugins. Plugins are written in Nessus Attack Scripting Language (NASL), a scripting language optimized for custom network interaction. New plugins are added as vulnerabilities are discovered. Many plugins check for a vulnerability by actually exploiting the vulnerability. The ‘safe checks’ option specifies that no vulnerability check capable of crashing a remote host be used (such as DOS attacks).
Nessus Check your results!! Nessus Sample Report
How Do We Exploit? Now that you have found a useful exploit, what do we use? USE METASPLOIT!!! Copyright 2003-2009 Metasploit LLC Metasploit is a registered trademark Contact us at msfdev[at]metasploit.com

MetaSploit Metasploit was created in 2003 as a portable network game using the Perl scripting language. Later, the Metasploit Framework was then completely rewritten in the Ruby programming language. It is most notable for releasing some of the most technically sophisticated exploits to public security vulnerabilities. In addition it is a powerful tool for third party security researchers to investigate potential vulnerabilities.
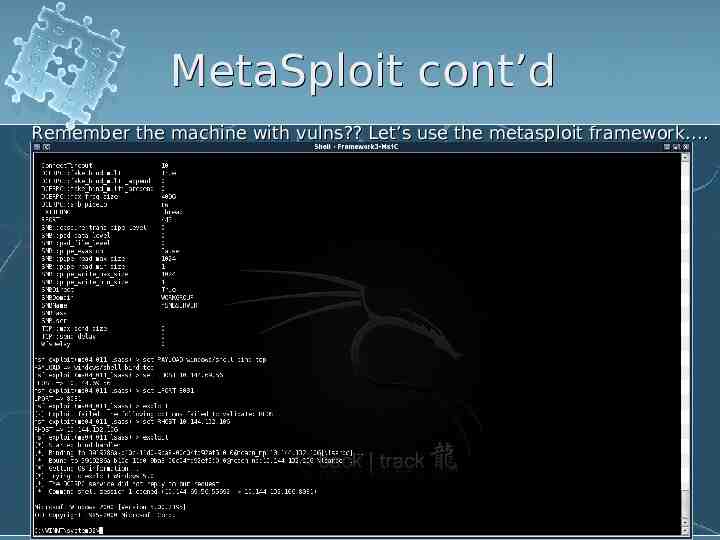
MetaSploit cont’d Remember the machine with vulns? Let’s use the metasploit framework .
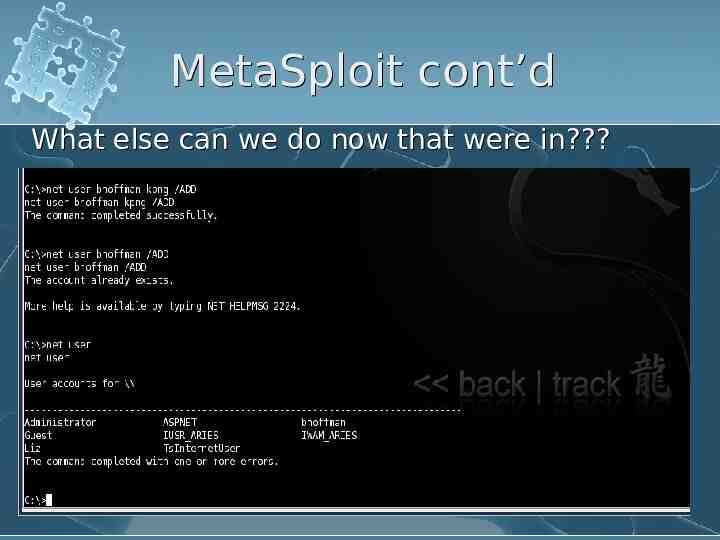
MetaSploit cont’d What else can we do now that were in?
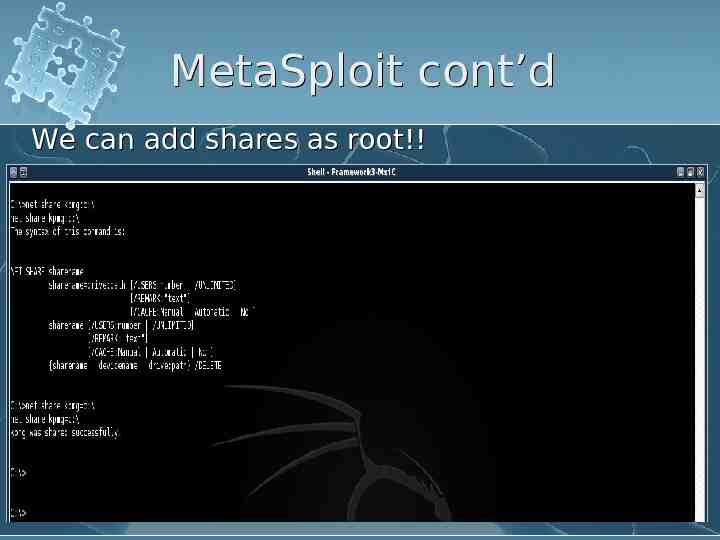
MetaSploit cont’d We can add shares as root!!

Ethical Hacking cont’d Administrative items: Authorization letter – “Get out of jail free card” Risk report Likelihood of risk Mitigation plans Trends (performed with recurring clients)
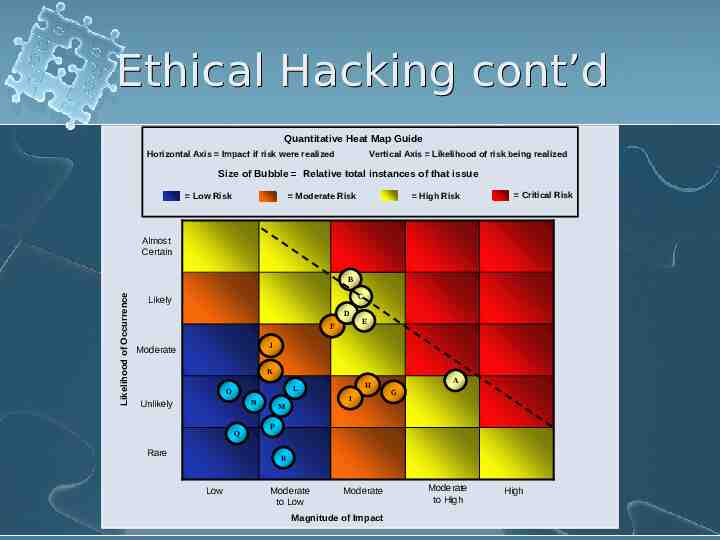
Ethical Hacking cont’d Quantitative Heat Map Guide Vertical Axis Likelihood of risk being realized Horizontal Axis Impact if risk were realized Size of Bubble Relative total instances of that issue Low Risk High Risk Moderate Risk Critical Risk Almost Certain Likelihood of Occurrence B C Likely D F E J Moderate K N Unlikely Q Rare H L O I M A G P R Low Moderate to Low Moderate Magnitude of Impact Moderate to High High

Q&A ANY QUESTIONS?
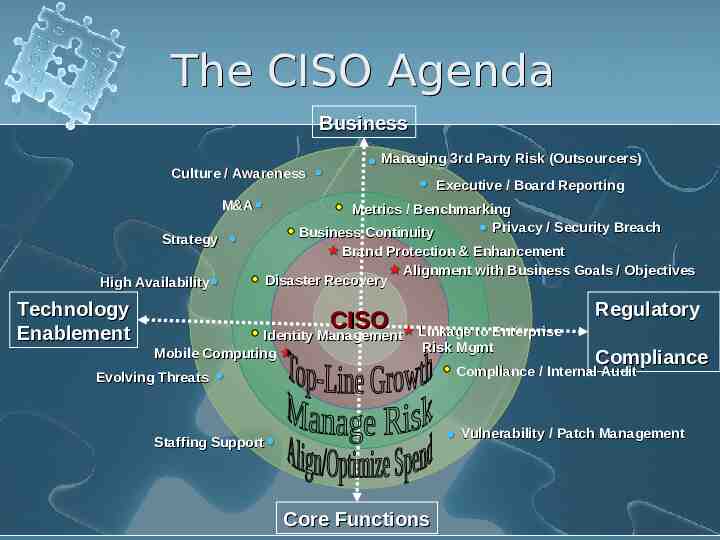
The CISO Agenda Business Culture / Awareness M&A Executive / Board Reporting Metrics / Benchmarking Privacy / Security Breach Business Continuity Strategy Brand Protection & Enhancement Alignment with Business Goals / Objectives Disaster Recovery High Availability Technology Enablement Managing 3rd Party Risk (Outsourcers) CISO Identity Management Identity Management Mobile Computing Regulatory Linkage to Enterprise Risk Mgmt Compliance Compliance / Internal Audit Evolving Threats Vulnerability / Patch Management Staffing Support Core Functions

Risk IT Security performs a critical role in assessing risk in the organization. Vulnerability Scanning Penetration Testing Industry Trends IT Strategy Familiarity with Audit and Compliance measures

Audit Support In many cases, IT Security is heavily relied upon to perform in depth testing required by an audit organization. Security is enlisted by audit because: Technical expertise Familiarity with current issues from internal testing Familiarity with Policies, Standards, and Procedures

Compliance Compliance may relate to internal compliance or external compliance. Internal compliance: Policies and Standards Security and Configuration baselines Framework use – ISO, COBIT, ITIL, GAISP, NIST Best Practices

Compliance cont’d External compliance: SOX (Sarbanes Oxley) COSO Framework HIPAA PCI Safe Harbor
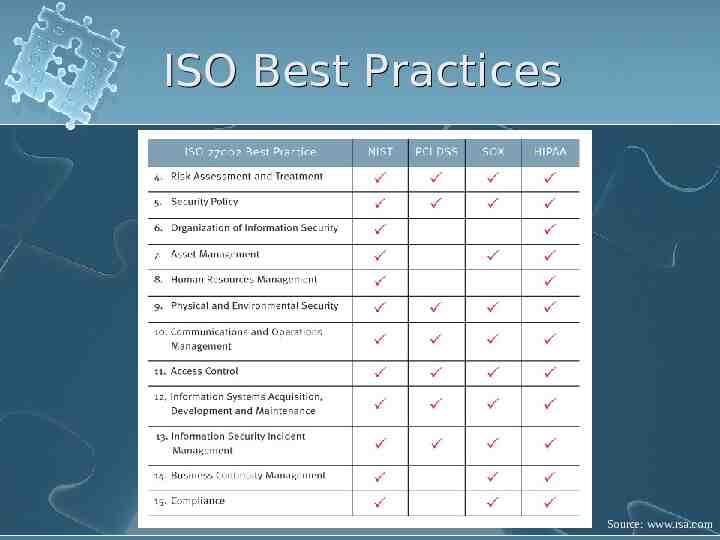
ISO Best Practices Source: www.rsa.com
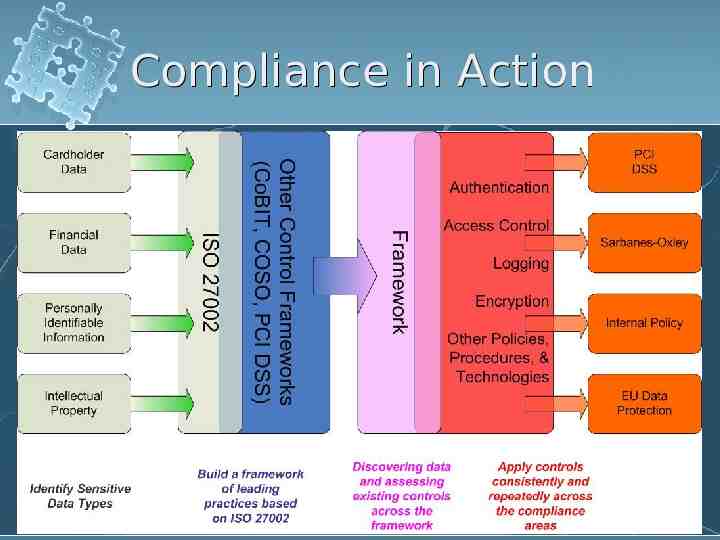
Compliance in Action Source: www.rsa.com

Internal Policy IT Security is regularly tasked with creation and enforcement of IT policies, standards, and procedures. Creation and enforcement of these documents require: Understanding of audit roles and procedures Familiarity with all systems, networks, and applications Compliance considerations

Internal Policy cont’d Definitions: A Policy is a set of directional statements and requirements aiming to protect corporate values, assets and intelligence. Policies serve as the foundation for related standards, procedures and guidelines. A Standard is a set of practices and benchmarks employed to comply with the requirements set forth in policies. A standard should always be a derivation of a policy, as it is the second step in the process of a company’s policy propagation. A Procedure is a set of step-by-step instructions for implementing policy requirements and executing standard practices.
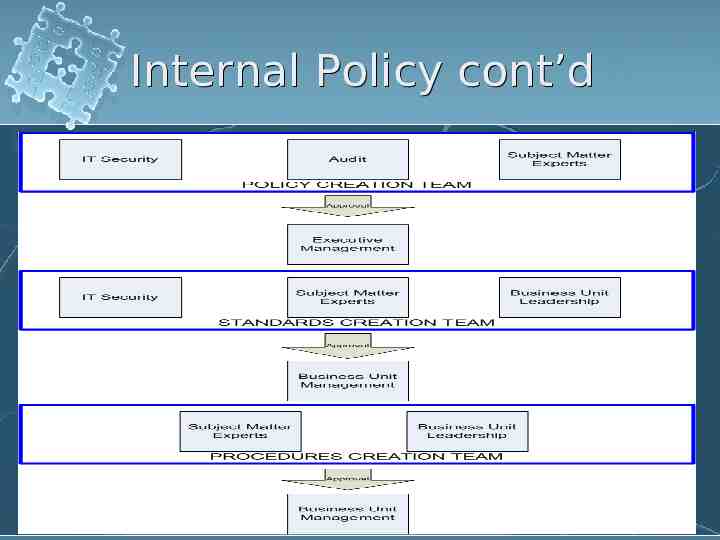
Internal Policy cont’d
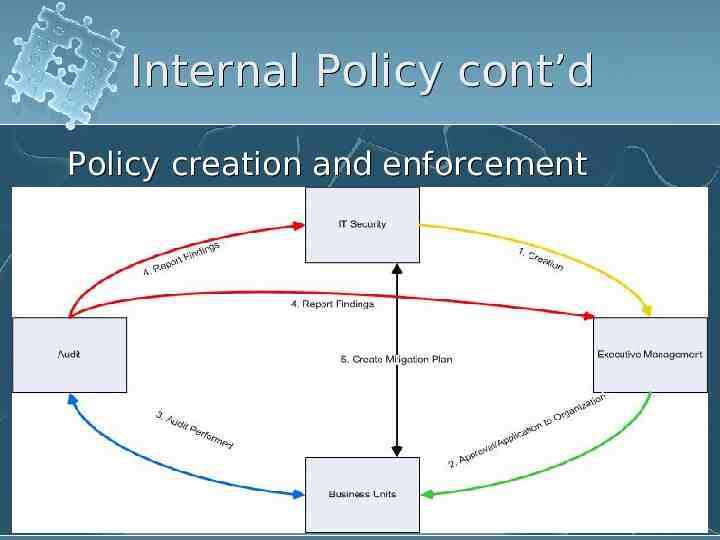
Internal Policy cont’d Policy creation and enforcement cycle

Policy Business Case A top 5 global food retailer has a massive IT/IS infrastructure and good governance .but no real policies! Policies are the foundation for enforcing IT compliance and governance. What policies were written for the client

Policy Business Case cont’d Policies written for IT Security: Acceptable Use Policy Information Classification & Ownership Policy Risk Assessment & Mitigation Policy Access Control Policy Network Configuration and Communication Policy Remote Access Policy Business Continuity Policy Incident Response Policy Third Party Data Sharing Policy System Implementation & Maintenance Secure Application Development Cryptography & Key Management Mobile Computing Physical & Environmental Security

Policy Business Case cont’d Sample Policies Cryptography and Key Management Policy Access Control Policy

Q&A Any Questions? Contact Information Brandon Hoffman [email protected] 312.665.2775