TRRespass: Exploiting the Many Sides of Target Row Refresh
34 Slides748.25 KB

TRRespass: Exploiting the Many Sides of Target Row Refresh Pietro Frigo1 Emanuele Vannacci1 Hasan Hassan2 Victor Van der Veen3 Onur Mutlu2 Herbert Bos1 Cristiano Giuffrida1 Kaveh Razavi1 1 Vrije Universiteit Amsterdam 2 ETH Zürich 3 Qualcomm Technologies Inc. 1

Teaser Memory vendors advertise RowHammer-free devices What is Target Row Refresh (TRR)? Not a single mitigation! Reverse-engineering of in-DRAM mitigations The Many-sided RowHammer Hammering up to 20 aggressor rows 3 major vendors all vulnerable: Samsung, Micron, SK Hynix Currently representing over 95% of the DRAM market 2
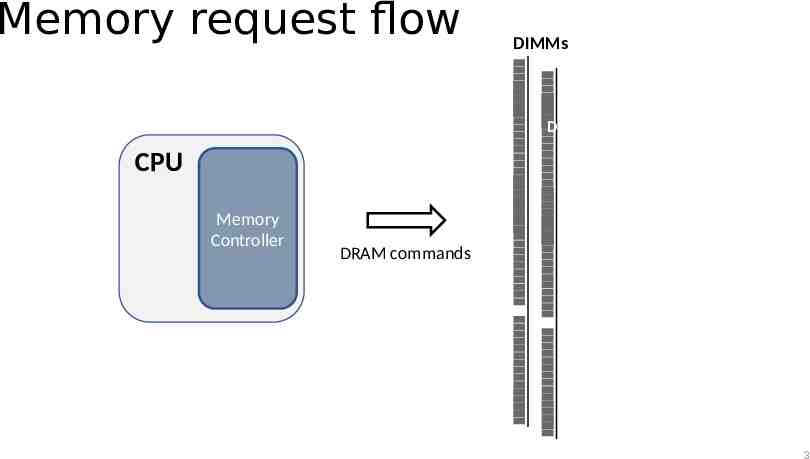
Memory request flow DIMMs DRAM CPU Memory Controller DRAM commands 3

DRAM Refresh DRAM is dynamic because data must be refresh periodically Retention time (i.e., 64ms) The MC issues a REFRESH command every 7.8µs Only a small portion of memory is refreshed with a command 8192 refreshes within a 64ms interval 4
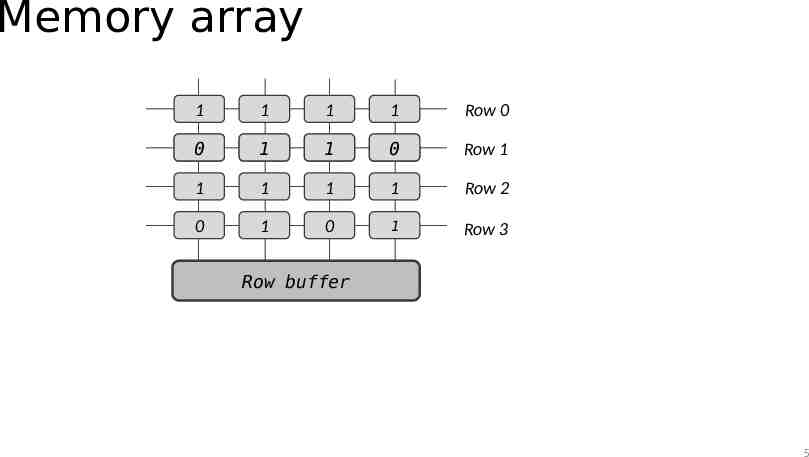
Memory array 1 1 1 1 Row 0 0 1 1 0 Row 1 1 1 1 1 Row 2 0 1 0 1 Row 3 Row buffer 5
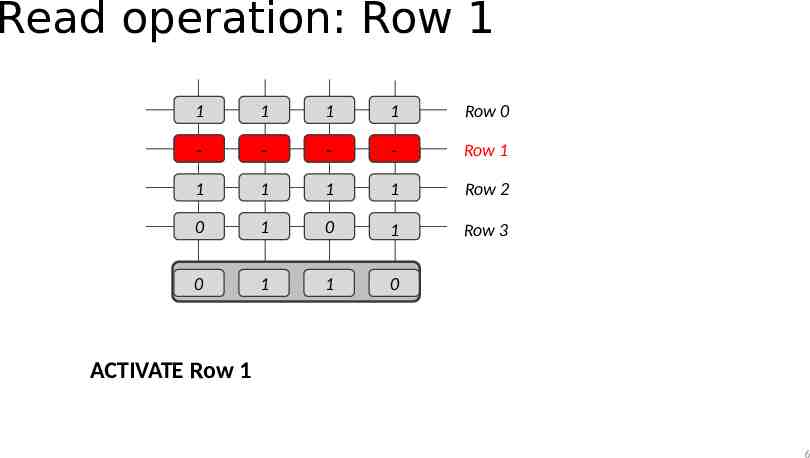
Read operation: Row 1 1 1 1 1 Row 0 - - - - Row 1 1 1 1 1 Row 2 0 1 0 1 Row 3 0 1 1 0 ACTIVATE Row 1 6
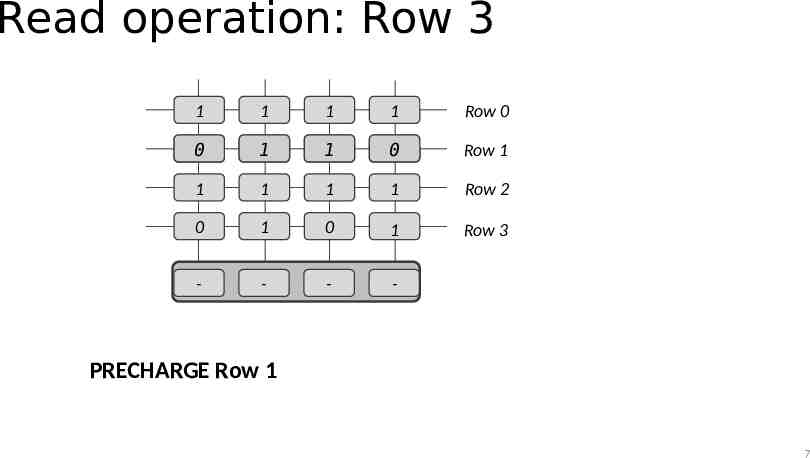
Read operation: Row 3 1 1 1 1 Row 0 0 1 1 0 Row 1 1 1 1 1 Row 2 0 1 0 1 Row 3 - - - - PRECHARGE Row 1 7
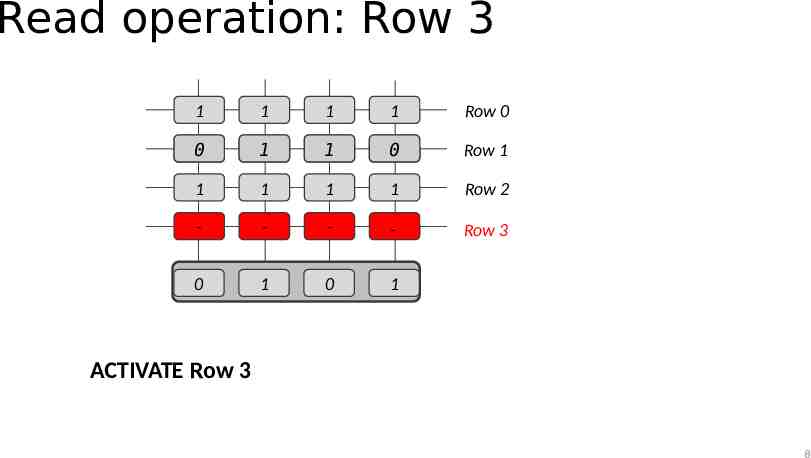
Read operation: Row 3 1 1 1 1 Row 0 0 1 1 0 Row 1 1 1 1 1 Row 2 - - - - Row 3 0 1 0 1 ACTIVATE Row 3 8
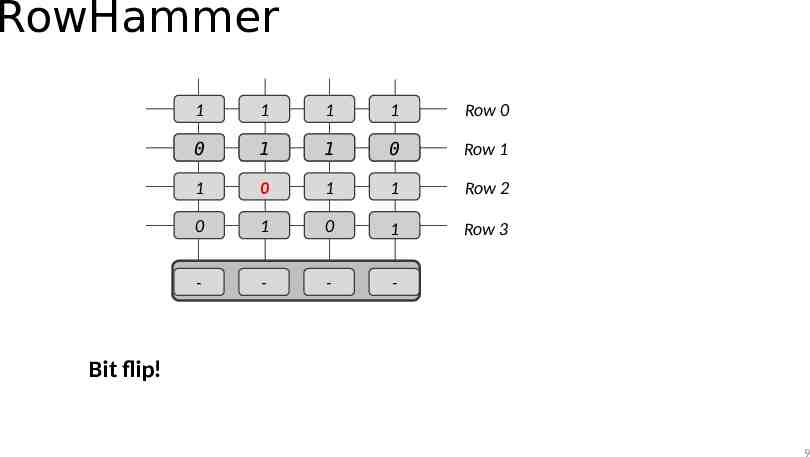
RowHammer 1 1 1 1 Row 0 0 1 1 0 Row 1 1 0 1 1 Row 2 0 1 0 1 Row 3 - - - - Bit flip! 9
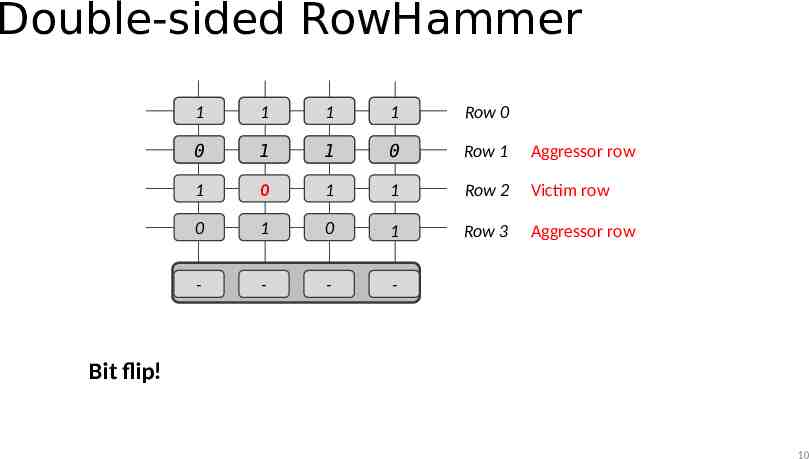
Double-sided RowHammer 1 1 1 1 Row 0 0 1 1 0 Row 1 Aggressor row 1 0 1 1 Row 2 Victim row 0 1 0 1 Row 3 Aggressor row - - - - Bit flip! 10

Hardware mitigations Error-correcting code (ECC) [1] Refreshing a row restores the cells electric charge: it prevents flips. Double refresh Target Row Refresh (TRR) [1] L. Cojocaret al., “Exploiting Correcting Codes: On the Effectiveness of ECC Memory Against Rowhammer Attacks,” in S&P, 2019. 11

Target Row Refresh TRR-like mitigations track rows activations and refresh victim rows Many possible implementations in practice Security through obscurity Pseudo TRR (pTRR) Memory controller implementation In-DRAM TRR Embedded in the DRAM circuitry 12
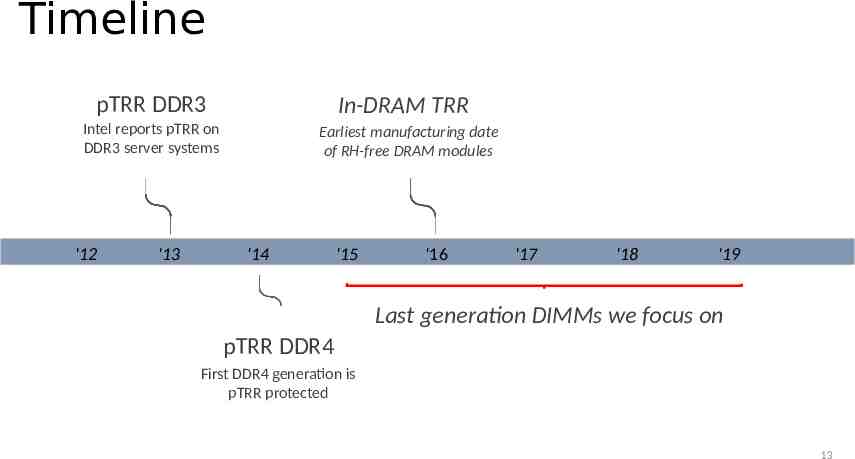
Timeline pTRR DDR3 In-DRAM TRR Intel reports pTRR on DDR3 server systems '12 '13 Earliest manufacturing date of RH-free DRAM modules '14 '15 '16 '17 '18 '19 Last generation DIMMs we focus on pTRR DDR4 First DDR4 generation is pTRR protected 13
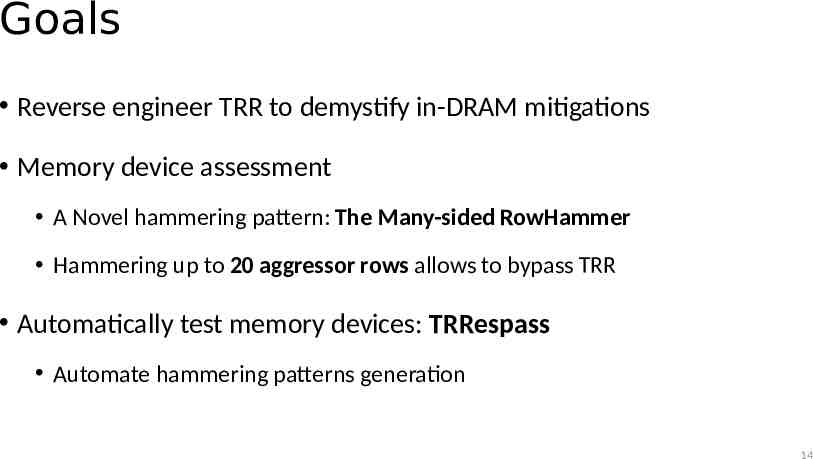
Goals Reverse engineer TRR to demystify in-DRAM mitigations Memory device assessment A Novel hammering pattern: The Many-sided RowHammer Hammering up to 20 aggressor rows allows to bypass TRR Automatically test memory devices: TRRespass Automate hammering patterns generation 14
Challenges Analysis from the CPU side not possible No timing side-channels FPGA-based memory controller [1,2] [1] H. Hassan et al., “SoftMC: A Flexible and Practical Open-Source Infrastructure for Enabling Experimental DRAM Studies,” in HPCA, 2017 [2] SAFARI Research Group, “SoftMC — GitHub Repository,” https:// github.com/CMU-SAFARI/SoftMC. 15
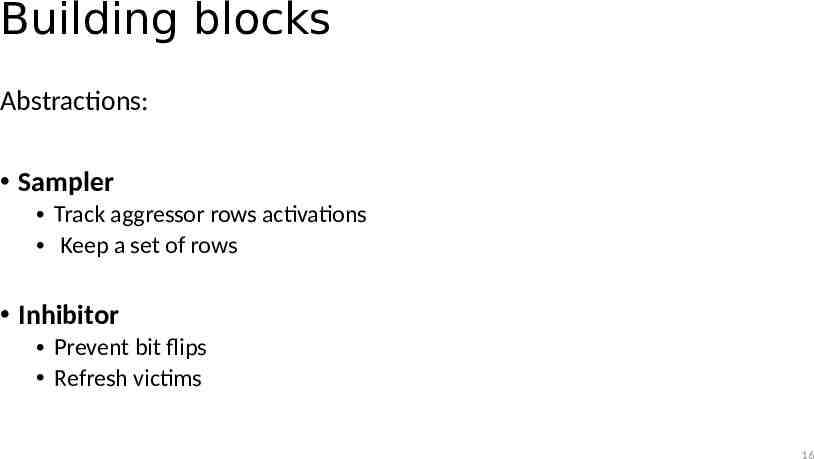
Building blocks Abstractions: Sampler Track aggressor rows activations Keep a set of rows Inhibitor Prevent bit flips Refresh victims 16

Case study: Vendor C How big is the sampler? Pick N aggressor rows Perform a series of hammers (activations of aggressors) 8K activations After each series of hammers, issue R refreshes 10 Rounds Activations Refreshes Activations Refreshes Round 17
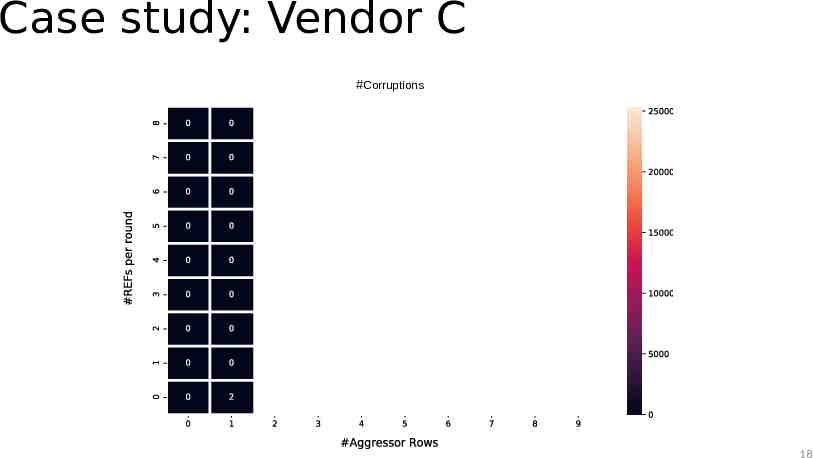
Case study: Vendor C #Corruptions 18
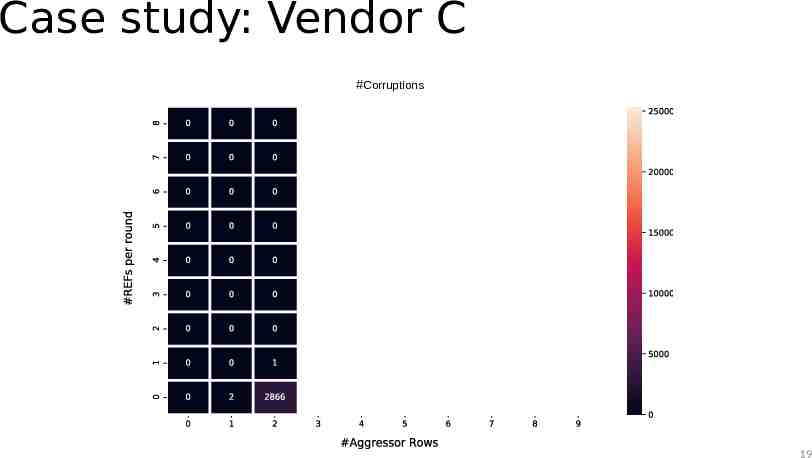
Case study: Vendor C #Corruptions 19
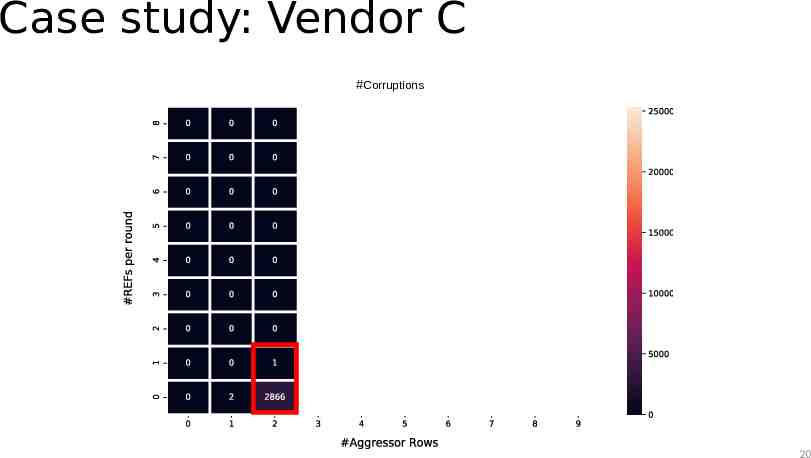
Case study: Vendor C #Corruptions 20

Case study: Observations The TRR mitigation acts on every refresh command 21
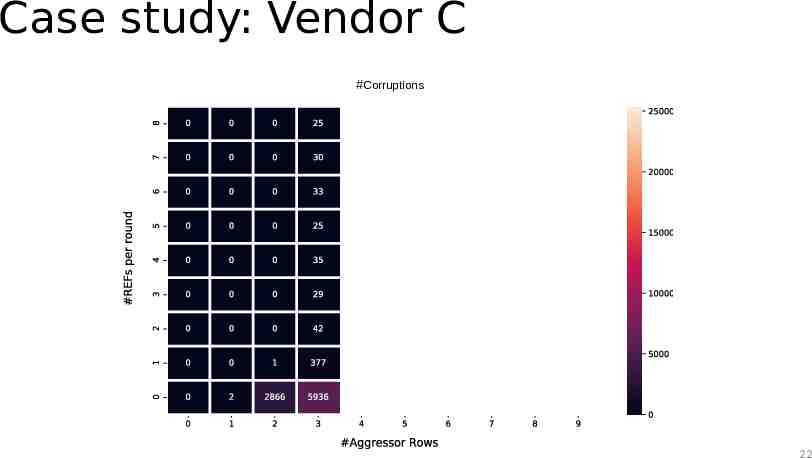
Case study: Vendor C #Corruptions 22
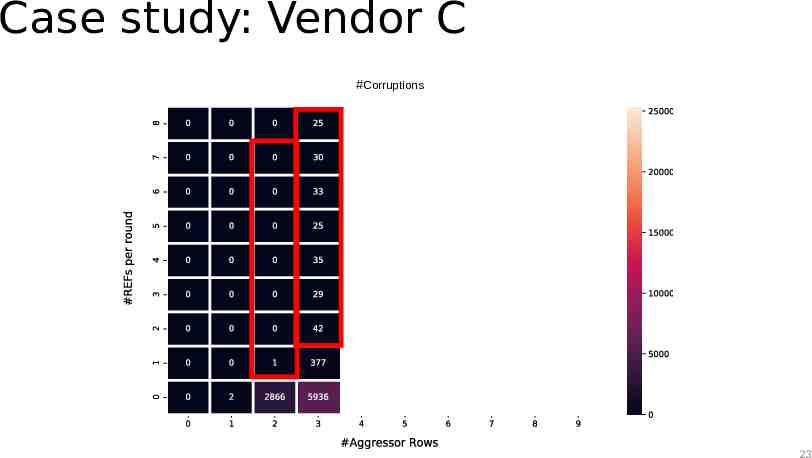
Case study: Vendor C #Corruptions 23

Case study: Observations The TRR mitigation acts on every refresh command The mitigation can sample more than one aggressor per refresh interval The mitigation can refresh only a single victim within a refresh operation 24
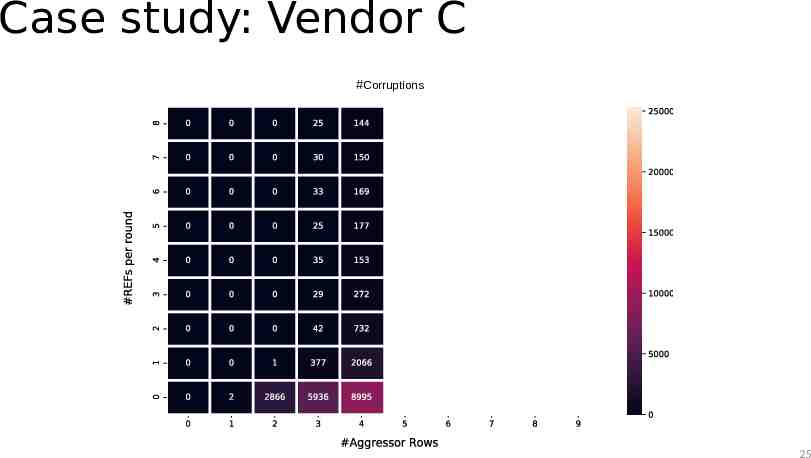
Case study: Vendor C #Corruptions 25
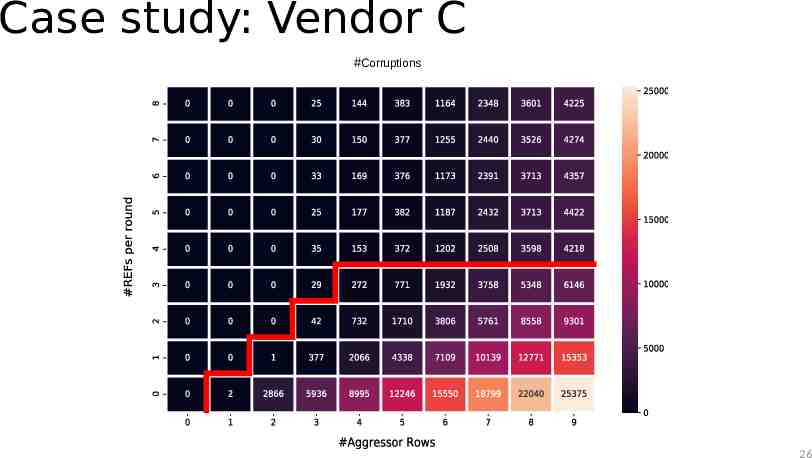
Case study: Vendor C #Corruptions 26

Case study: Observations The TRR mitigation acts on every refresh command The mitigation can sample more than one aggressor per refresh interval The mitigation can refresh only a single victim within a refresh operation Sweeping the number of refresh operations and aggressor rows while hammering reveals the sampler size 27
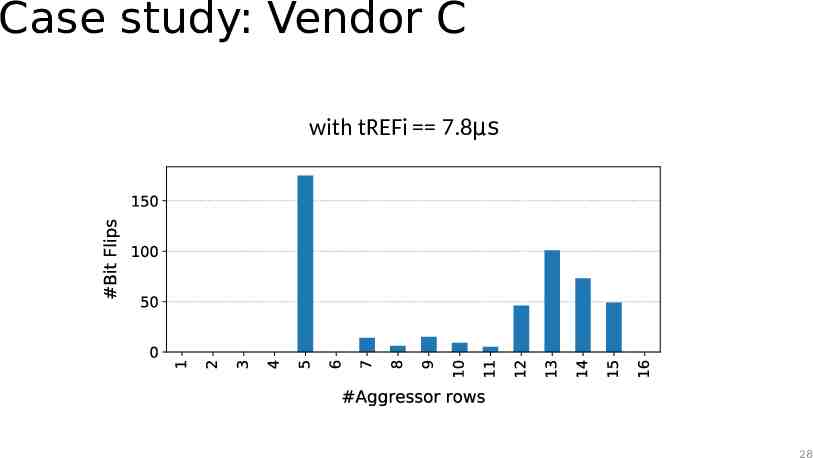
Case study: Vendor C with tREFi 7.8μs 28

Case study: Observations The TRR mitigation acts on every refresh command The mitigation can sample more than one aggressor per refresh interval The mitigation can refresh only a single victim within a refresh operation Sweeping the number of refresh operations and aggressor rows while hammering reveals the sampler size The sampling mechanism is affected by the addresses of aggressor rows 29

TRRespass: The RowFuzzer Black-box fuzzing for RowHammer Ignore the MC optimizations Scalable approach for testing The sampler can track a limited number of aggressor rows # Aggressors The sampler design may be row address dependent Aggressor Location 30

TRRespass: Results 42 DIMMS from 3 of the major vendors: Samsung, Micron, SK Hynix 95% of the market Testing 256MB of contiguous memory against the best pattern 13 DIMMs with bit flips Multiple effective patterns for each of them Bit flips with double refresh Fuzzing is effective. How to Improve? Parameter selection. 31

Exploitation Memory templating Find the right hammering pattern Locations of aggressors not always fundamental Bit flips are repeatable Spurious flips We demonstrate the feasibility of 3 example attacks: Privilege escalation [1] Access to co-hosted VM via RSA key corruption [2] Sudo exploit: opcode flipping [3] [1] M. Seaborn and T. Dullien, “Exploiting the DRAM Rowhammer Bug to Gain Kernel Privileges,” in Black Hat USA, 2015 [2] K. Razavi et al., “Flip Feng Shui: Hammering a Needle in the Software Stack,” in USENIX Sec., 2016 [3] D. Gruss et al., “Another Flip in the Wall of Rowhammer Defenses,” in S&P, 2018. 32

Conclusion Bit flips with more than 20 aggressor rows! DDR4 devices are much more vulnerable than DDR3 Bit flips with less than 50K activations Fuzzing can help in memory testing Reverse engineering to find meaningful parameters RowHammer is still a serious problem No prompt mitigations available 33

Questions! 34