pwc Compliance and a Culture of Integrity Data and Privacy October
20 Slides621.38 KB

www.pwc.com Compliance and a Culture of Integrity Data and Privacy October 29, 2014

Cyber security and Privacy . . . . a Board level issue Increase in the Security and Privacy regulatory mandates in recent years, as well as expected changes in upcoming years Emerging technologies and reliance on third parties have created a borderless infrastructure Growing demand by business leaders to understand how privacy (“what” data is sensitive to the business) and security (“how” to protect the data deemed sensitive) is integrated Increase in threats and vulnerabilities to sensitive data and corporate assets Even companies that place great emphasis on securing their business processes can become the victim of cybercrime. Cybercrime can manifest in many ways Having a documented, demonstrated and regularly tested program helps in the event of regulator oversight PwC 2
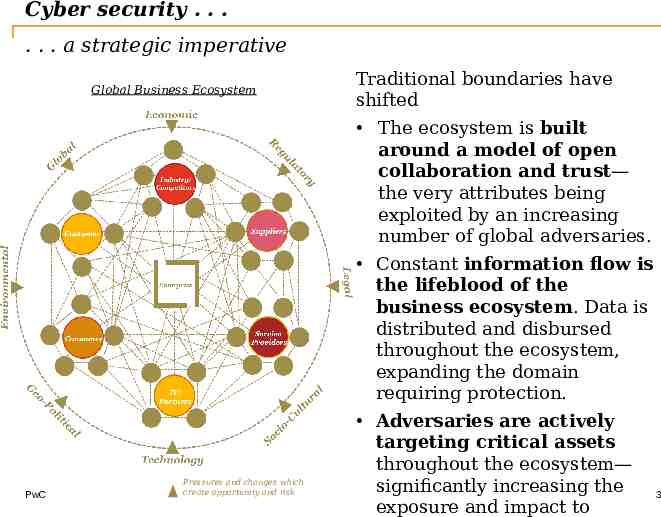
Cyber security . . . . . . a strategic imperative Global Business Ecosystem PwC Pressures and changes which create opportunity and risk Traditional boundaries have shifted The ecosystem is built around a model of open collaboration and trust— the very attributes being exploited by an increasing number of global adversaries. Constant information flow is the lifeblood of the business ecosystem. Data is distributed and disbursed throughout the ecosystem, expanding the domain requiring protection. Adversaries are actively targeting critical assets throughout the ecosystem— significantly increasing the 3 exposure and impact to
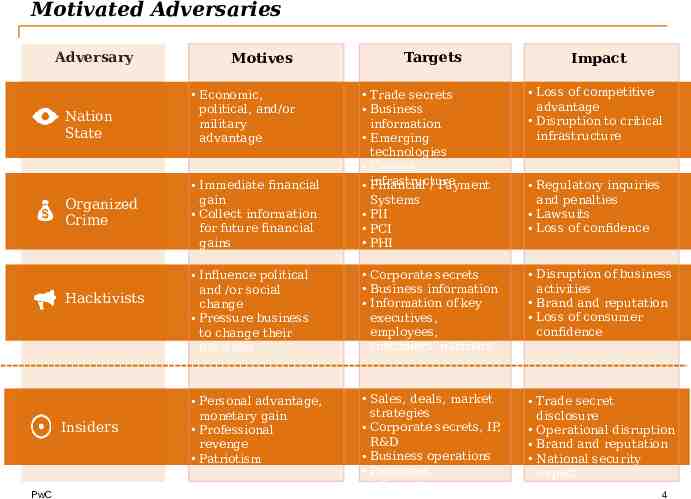
Motivated Adversaries Adversary Nation State Organized Crime Hacktivists Insiders PwC Motives Economic, political, and/or military advantage Immediate financial gain Collect information for future financial gains Targets Trade secrets Business information Emerging technologies Critical infrastructure Financial / Payment Systems PII PCI PHI Impact Loss of competitive advantage Disruption to critical infrastructure Regulatory inquiries and penalties Lawsuits Loss of confidence Influence political and /or social change Pressure business to change their practices Corporate secrets Business information Information of key executives, employees, customers, partners Disruption of business activities Brand and reputation Loss of consumer confidence Personal advantage, monetary gain Professional revenge Patriotism Sales, deals, market strategies Corporate secrets, IP, R&D Business operations Personnel information Trade secret disclosure Operational disruption Brand and reputation National security impact 4
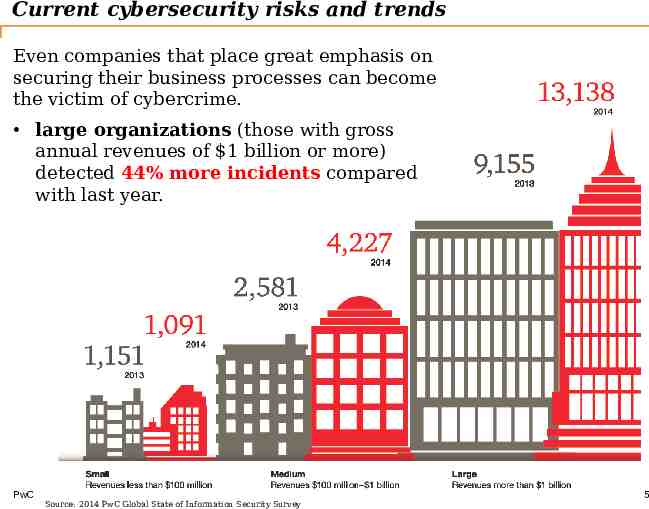
Current cybersecurity risks and trends Even companies that place great emphasis on securing their business processes can become the victim of cybercrime. large organizations (those with gross annual revenues of 1 billion or more) detected 44% more incidents compared with last year. PwC Source: 2014 PwC Global State of Information Security Survey 5
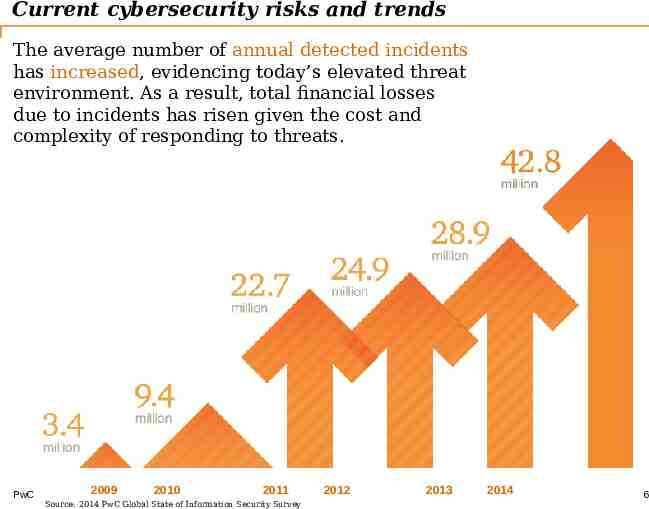
Current cybersecurity risks and trends The average number of annual detected incidents has increased, evidencing today’s elevated threat environment. As a result, total financial losses due to incidents has risen given the cost and complexity of responding to threats. PwC 2009 2010 2011 Source: 2014 PwC Global State of Information Security Survey 2012 2013 2014 6

Current cybersecurity risks and trends Mobile security is an area of continued vulnerability. Mobility has generated a deluge of data, but deployment of mobile security has not kept pace Companies are increasingly sharing data with third parties. While services can be outsourced, accountability for security and privacy cannot Compromises attributed to third parties with trusted access 55%while have due security baselines for external partners, increases diligence weakens: suppliers, and vendors (60% in 2013) 50% perform risk assessments on third-party vendors (53% in 2013) Very few organizations have true visibility into third party business partners Changing relationship between the organization and consumersmultiple channels/consumer touch points (e.g. website/mobile PwC site/app/store) without centralized oversight and “control” 7

Current cybersecurity risks and trends Current and former employees are the most-cited culprits of security incidents, but implementation of key insider-threat safeguards is declining: 56% have privileged user-access tools (65% in 2013) 51% monitor user compliance with security policies (58% in 2013) 51% have an employee security training and awareness program (60% in 2013) While less frequent, incidents attributed to nation-states, organized crime, and competitors increased sharply in 2014: 86% jump in incidents by nation-states PwC 64% rise in compromises by competitors 26% increase in incidents by organized crime 8
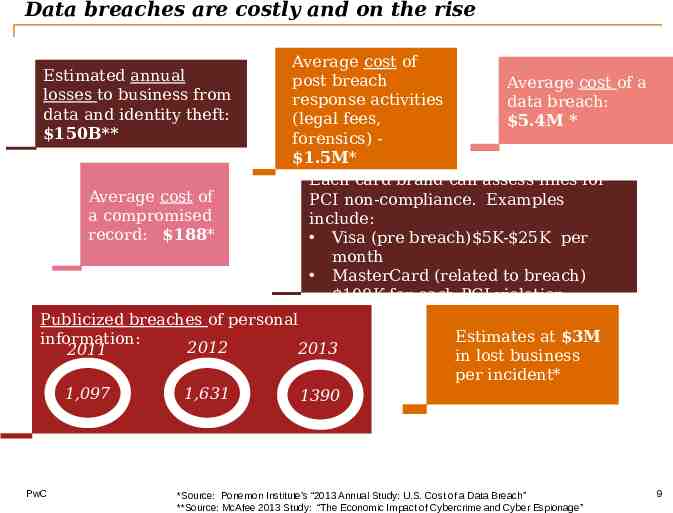
Data breaches are costly and on the rise Estimated annual losses to business from data and identity theft: 150B** Average cost of a compromised record: 188* Average cost of post breach Average cost of a response activities data breach: (legal fees, 5.4M * forensics) 1.5M* Each card brand can assess fines for PCI non-compliance. Examples include: Visa (pre breach) 5K- 25K per month MasterCard (related to breach) 100K for each PCI violation Publicized breaches of personal information: 2012 2013 2011 1,097 PwC 1,631 Estimates at 3M in lost business per incident* 1390 *Source: Ponemon Institute’s “2013 Annual Study: U.S. Cost of a Data Breach” **Source: McAfee 2013 Study: “The Economic Impact of Cybercrime and Cyber Espionage” 9
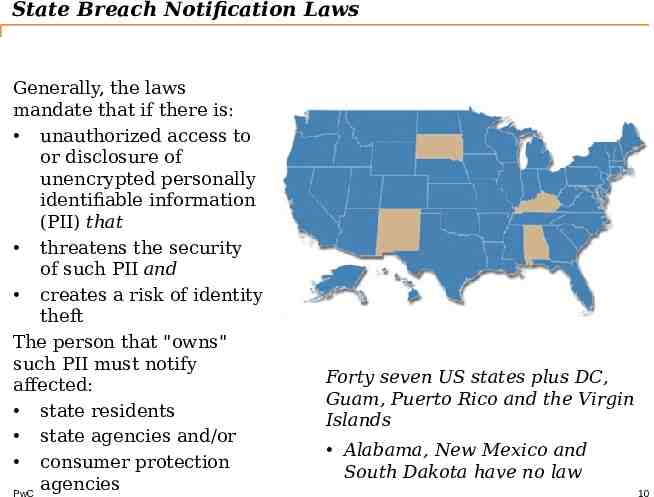
State Breach Notification Laws Generally, the laws mandate that if there is: unauthorized access to or disclosure of unencrypted personally identifiable information (PII) that threatens the security of such PII and creates a risk of identity theft The person that "owns" such PII must notify affected: state residents state agencies and/or consumer protection agencies PwC Forty seven US states plus DC, Guam, Puerto Rico and the Virgin Islands Alabama, New Mexico and South Dakota have no law 10
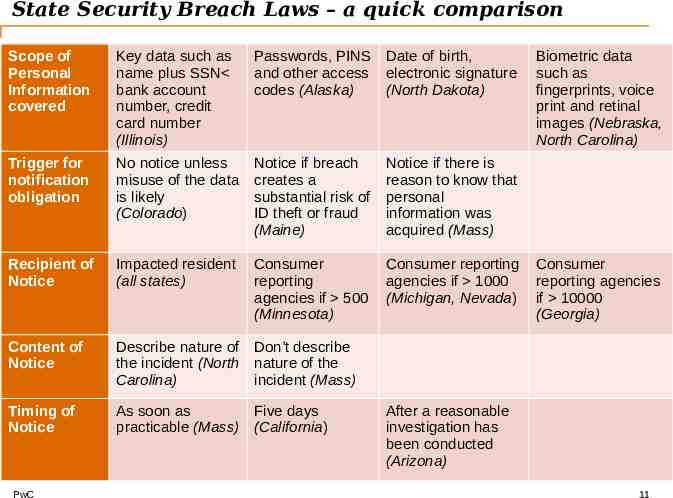
State Security Breach Laws – a quick comparison Scope of Personal Information covered Key data such as name plus SSN bank account number, credit card number (Illinois) Passwords, PINS and other access codes (Alaska) Date of birth, electronic signature (North Dakota) Trigger for notification obligation No notice unless misuse of the data is likely (Colorado) Notice if breach creates a substantial risk of ID theft or fraud (Maine) Notice if there is reason to know that personal information was acquired (Mass) Recipient of Notice Impacted resident (all states) Consumer reporting agencies if 500 (Minnesota) Consumer reporting agencies if 1000 (Michigan, Nevada) Content of Notice Describe nature of Don’t describe the incident (North nature of the Carolina) incident (Mass) Timing of Notice As soon as Five days practicable (Mass) (California) PwC Biometric data such as fingerprints, voice print and retinal images (Nebraska, North Carolina) Consumer reporting agencies if 10000 (Georgia) After a reasonable investigation has been conducted (Arizona) 11

Typical Data Breach Legal Response Most incidents are not cyber security or hacking events, for example: Lost or stolen employee laptop (encryption will help) HR employee accidentally sending spreadsheet to the wrong person Vendor accidentally uploading file to the wrong server Even the small ones take time to address: What data was involved? Was it encrypted? Who accessed it? How trustworthy are they? How can it be used by the person who accessed it? Is there a likelihood of harm? (some states don’t care) Finding the individuals’ names and contact information Drafting letters based on state requirements PwC 12

Typical Data Breach Legal Response Need to do analysis to determine if notice is required: Look at the various state laws Look at your customer contracts (for B to B) Comply with your privacy notices Even if notice is not required, it may be appropriate: Is there an ethical responsibility to notify? If notify in one state, should you notify in all? Could it be a bad PR move not to notify, even if not required? But over-notification also has its issues A robust Incident Response Plan is necessary to enable prompt reaction. Prompt reaction is key to a successful response. PwC 13
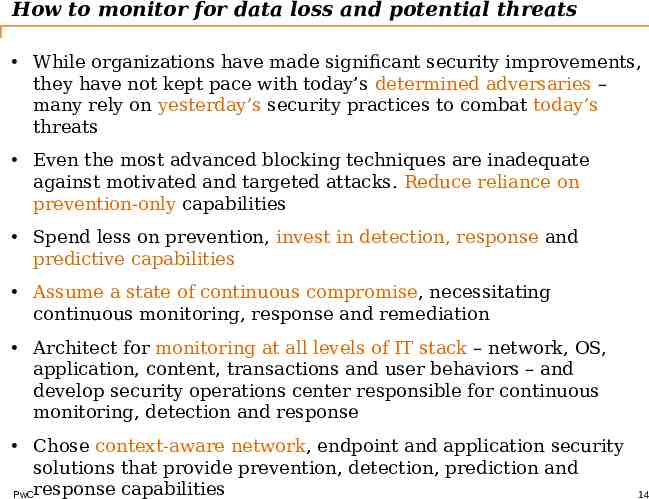
How to monitor for data loss and potential threats While organizations have made significant security improvements, they have not kept pace with today’s determined adversaries – many rely on yesterday’s security practices to combat today’s threats Even the most advanced blocking techniques are inadequate against motivated and targeted attacks. Reduce reliance on prevention-only capabilities Spend less on prevention, invest in detection, response and predictive capabilities Assume a state of continuous compromise, necessitating continuous monitoring, response and remediation Architect for monitoring at all levels of IT stack – network, OS, application, content, transactions and user behaviors – and develop security operations center responsible for continuous monitoring, detection and response Chose context-aware network, endpoint and application security solutions that provide prevention, detection, prediction and PwCresponse capabilities 14
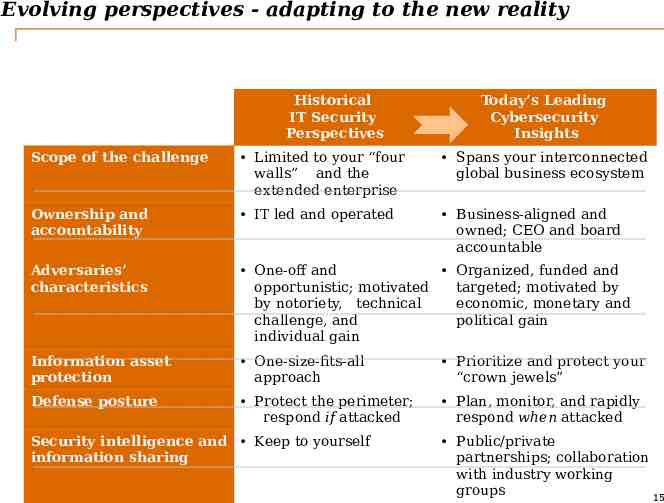
Evolving perspectives - adapting to the new reality Historical IT Security Perspectives Today’s Leading Cybersecurity Insights Scope of the challenge Limited to your “four walls” and the extended enterprise Spans your interconnected global business ecosystem Ownership and accountability IT led and operated Business-aligned and owned; CEO and board accountable Adversaries’ characteristics One-off and Organized, funded and opportunistic; motivated targeted; motivated by by notoriety, technical economic, monetary and challenge, and political gain individual gain Information asset protection One-size-fits-all approach Prioritize and protect your “crown jewels” Defense posture Protect the perimeter; respond if attacked Plan, monitor, and rapidly respond when attacked Security intelligence and Keep to yourself information sharing PwC Public/private partnerships; collaboration with industry working groups 15

Building a Cyber Security & Privacy Program PwC 16

Common challenges and keys to an effective program Creating a robust strategy that accounts for a complex, multi-regulatory & changing environment Managing individual concerns and perceptions across differing cultures Understanding the information the organization collects & processes Managing information across the data lifecycle, within and outside your organization Building secure networks and systems Standardizing practices across all entities and regions, including all channels Coordinating incident response Driving policy and controls into business practices and technology Adopting privacy values throughout the enterprise PwC Ensuring Business Continuity & Disaster 1. An effective governance structure 2. A strong culture and attitude at all levels 3. An effective risk assessment process 4. A complete, dynamic, current lifecycle data inventory that includes third parties 5. Controls aligned with a selected framework 6. An effective training and awareness program 7. An effective team that ensures compliance with laws and regulations 8. An effective auditing and monitoring function 9. Policies and procedures that are current, communicated, and followed 10. An effective, documented, and tested incident response plan 17
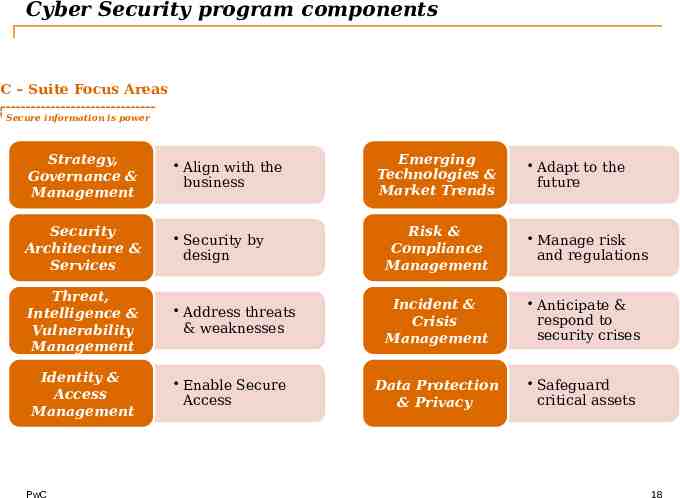
Cyber Security program components C – Suite Focus Areas Secure information is power Strategy, Governance & Management Align with the business Security Architecture & Services Security by design Risk & Compliance Management Manage risk and regulations Threat, Intelligence & Vulnerability Management Address threats & weaknesses Incident & Crisis Management Anticipate & respond to security crises Data Protection & Privacy Safeguard critical assets Identity & Access Management PwC Enable Secure Access Emerging Technologies & Market Trends Adapt to the future 18

Taking action: 5 steps toward a strategic cyber program 1 Ensure that your cybersecurity strategy is aligned with business objectives and is strategically funded 2 Identify your most valuable information assets, and prioritize protection of this high-value data 3 4 5 PwC Understand your adversaries, including their motives, resources, and methods of attack to help reduce the time from detect to respond Assess cybersecurity of third parties and supply chain partners, and ensure they adhere to your security policies and practices Collaborate with others to increase awareness of cybersecurity threats and response tactics 19

Contacts Bonnie L. Yeomans VP, Assistant General Counsel and Privacy Officer CA Technologies (631) 342-2678 [email protected] Jacqueline T Wagner Managing Director – New York Privacy Leader PwC (646) 471-5644 [email protected] Ariel Litvin Director - IT Risk & Security Assurance PwC (646) 471-0999 [email protected] 2014 PricewaterhouseCoopers LLP, a Delaware limited liability partnership. All rights reserved. PwC refers to the United States member firm, and may sometimes refer to the PwC network. Each member firm is a separate legal entity. Please see www.pwc.com/structure for further details. This content is for general information purposes only, and should not be used as a substitute for consultation with professional advisors. PwC 20






