A Taxonomy of DDoS Attack and DDoS Defense Mechanisms By Jelena
35 Slides178.00 KB

A Taxonomy of DDoS Attack and DDoS Defense Mechanisms By Jelena Mirkovic and Peter Reiher

DDoS Attack Overview DDoS – A distributed denial of service attack uses multiple machines to prevent the legitimate use of a service Examples: 1. Stream of packets consuming a key resource - renders resource unavailable to legitimate clients 2. Malformed packets confusing an application or protocol - forces it to freeze or reboot 3. Overload the Internet infrastructure

Why are DDoS attacks possible? Internet security is highly interdependent - each host depends on the state of security in the rest of global Internet Internet resources are limited - not enough resources to match the number of users Resources are not collocated - end networks only have small amount of bandwidth compared to abundant resources of network

Why are DDoS attacks possible? Accountability is not enforced - source address spoofing Control is distributed - networks run according to local policy - impossible to investigate cross-network traffic behavior

DDoS Attack Phases Recruiting - multiple agents (slaves, zombies) machines Exploiting - utilize discovered vulnerability Infecting - plant attack code Using - send attack packets via agents

Why make DDoS attacks? Personal reasons - target specific computers for revenge Prestige - gain respect of hacker community Material gain - damage resources Political reasons - compromise enemy’s resources

Taxonomy of DDoS Attacks DA: Degree of Automation EV: Exploited Vulnerability to Deny Service SAV: Source Address Validity ARD: Attack Rate Dynamics PC: Possibility of Characterization PAS: Persistence of Agent Set VT: Victim Type IV: Impact on the Victim
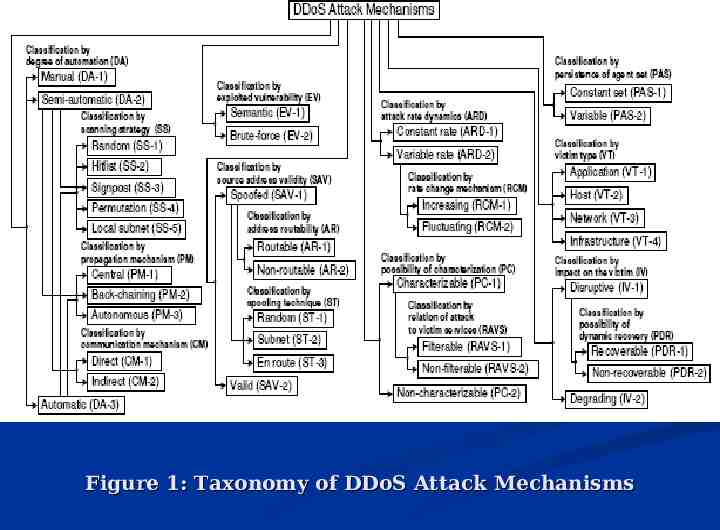
Figure 1: Taxonomy of DDoS Attack Mechanisms

DA-2 and DA-3:SS: Scanning Strategy Locate as many vulnerable machines as possible while creating a low traffic volume DA-2 and DA-3:SS-1: Random Scanning - compromised hosts probe random addresses in the IP address space, using a different seed (ex: Code Red) - high traffic volume can lead to detection DA-2 and DA-3:SS-2: Hitlist Scanning - probe all addresses from an externally supplied list - if list is too large, high traffic volume results - if list is too small, small agent population results

DA-2 and DA-3:SS: Scanning Strategy DA-2 and DA-3:SS-3: Signpost Scanning - uses information on compromised host to select new targets (ex: address book) - depends on agent machines and their user behavior DA-2 and DA-3:SS-4: Permutation Scanning - psuedo-random permutation of the IP address space with indexing - semi-coordinated, comprehensive scan with benefits of random probing DA-2 and DA-3:SS-2: Local Subnet Scanning - scan for targets on the same subnet as the compromised host - a single copy of the scanning program can compromise many machines behind a firewall (ex: Code Red II and Nimda Worm)

DA-2 and DA-3:PM: Propagation Mechanism Utilized during the infection phase DA-2 and DA-3:PM-1: Central Source Propagation - attack code resides on central server - large burden on central server, creating high traffic and single point of failure (ex: 1i0n worm) DA-2 and DA-3:PM-2: Back-Chaining Propagation - attack code is downloaded from the machine that exploited the system - avoids single point of failure (ex: Ramen and Morris Worms) DA-2 and DA-3:PM-3: Autonomous Propagation - injecting attack instructions into target host during exploit phase - reduces frequency of network traffic needed (ex: Code Red and Warhol Worm)

EV: Exploited Vulnerability to Deny Service EV-1: Semantic - exploit a specific feature or implementation bug of some protocol or application - consume excess amounts of its resources - ex: TCP SYN (connection queue space) EV-2: Brute-Force (aka flooding attacks) - high number of attack packets exhaust victim’s resources - misuse of legitimate services

SAV: Source Address Validity SAV-1: Spoofed Source Address SAV-1:AR-1: Routable Source Address - reflection attack: multiple requests made using spoofed address SAV-1:AR-2: Non-Routable Source Address - spoof address belonging to reserved set of addresses or part of assigned but not used address space of some network

SAV: Source Address Validity SAV-1:ST-1: Random Spoofed Source Address - random source addresses in attack packets SAV-1:ST-2: Subnet Spoofed Source Address - random address from address space assigned to the agent machine’s subnet SAV-1:ST-3: En Route Spoofed Source Address - address spoofed en route from agent machine to victim

SAV: Source Address Validity SAV-2: Valid Source Address - used when attack strategy requires several request/reply exchanges between an agent and the victim machine - target specific applications or protocol features

ARD: Attack Rate Dynamics Agent machine sends a stream of packets to the victim ARD-1: Constant Rate - attack packets generated at constant rate, usually as many as resources allow ARD-2: Variable Rate - delay or avoid detection and response

ARD: Attack Rate Dynamics ARD-2:RCM: Rate Change Mechanism ARD-2:RCM-1: Increasing Rate - gradually increasing rate causes a slow exhaustion of the victim’s resources ARD-2:RCM-2: Fluctuating Rate - occasionally relieving the effect - victim can experience periodic service disruptions

PC: Possibility of Characterization Looking at the content and header fields of attack packets PC-1: Characterizable - target specific protocols or applications at the victim - identifiable by content and header fields PC-2: Non-Characterizable - attack attempts to consume network bandwidth using a variety of packets that engage different applications and protocols - ex: various combinations of TCP is actually characterizable as a TCP attack

PC: Possibility of Characterization PC-1:RAVS: Relation of Attack to Victim Services PC-1:RAVS-1: Filterable - malformed packets or packets for noncritical services of victim’s operation - use firewall - ex: UDP flood PC-1:RAVS-2: Non-Filterable - well-formed packets that request legitimate victim services - indistinguishable from legitimate client - ex: HTTP flood

PAS: Persistence of Agent Set Recently, attacks have varied the set of agents active at any one time PAS-1: Constant Agent Set - all agent machines act in a similar manner - pulsing attack can provide a constant agent set if the “on” and “off” periods match over all agent machines PAS-2: Variable Agent Set - attacker divides all available agents into several groups, engaging only one group of agents at any one time

VT: Victim Type Not necessarily a single host machine VT-1: Application - exploit some feature of a specific application on victim host - disables legitimate client use of that application and possibly strains resources - indistinguishable from legitimate packets - semantics of application must be heavily used in detection VT-2: Host - disable access to the target machine completely by overloading or disabling its communication mechanism (ex: TCP SYN attack) - attack packets carry real destination address of target host

VT: Victim Type VT-1: Network Attacks - consume incoming bandwidth of a target networks - attack packets have destination addresses within address space of network - high volume makes detection easy VT-2: Infrastructure - target some distributed service that is crucial for the global Internet operation or operation of a sub-network - ex: DNS server attacks

DDoS Defense Challenges Distributed response needed at many points on Internet - attacks target more than one host - wide deployment of any defense system cannot be enforce because Internet is administered in a distributed manner Economic and social factors - distributed response system must be deployed by parties that do not suffer direct damage from DDoS attacks - many good distributed solutions will achieve only sparse deployment

DDoS Defense Challenges Lack of detailed attack information - attacks are only reported to government (it is believed making this knowledge public damages the business reputation of the victim network) Lack of defense system benchmarks - currently no benchmark suite of attack scenarios that would enable comparison between defense systems Difficulty of large-scale testing - defenses need to be tested in a realistic environment - lack of large-scale testbeds
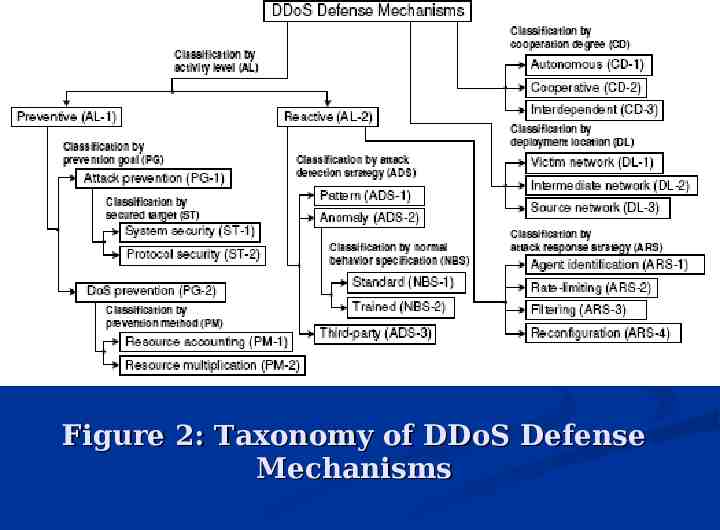
Figure 2: Taxonomy of DDoS Defense Mechanisms

AL: Activity Level AL-1: Preventive - eliminate possibility of DDoS attack altogether - enable potential victims to endure attack without denying services to legitimate clients AL-2: Reactive - alleviate the impact of the attack on the victim - must detect and respond to attack

AL: Activity Level AL-1:PG: Prevention Goal AL-1:PG-1: Attack Prevention - modify systems and protocol - never 100% effective because global deployment cannot be guaranteed AL-1:PG-2: DoS Prevention - enforce policies for resource consumption - ensure that abundant resources exists

AL: Activity Level AL-1:PG-1:ST: Secured Target AL-1:PG-1:ST-1: System Security - removing application bugs and updating protocol installations - ex: security patches, firewall systems, etc. AL-1:PG-1:ST-2: Protocol Security - address problem of a bad protocol design - ex: authentication server attack, fragmented packet attack

AL: Activity Level AL-1:PG-2:PM: Prevention Method AL-1:PG-2:PM-1: Resource Accounting - resources access based on the privileges and behavior of the user AL-1:PG-2:PM-2: Resource Multiplication - abundance of resources to counter threat (costly but proven sufficient) - ex: pool of servers with high bandwidth links

AL: Activity Level AL-2:ADS: Attack Detection Strategy AL-2:ADS-1: Pattern Detections - store signatures of known attacks in a database - known attacks are reliably detected - helpless against new attacks AL-2:ADS-2: Anomaly Detection - have a model of normal system behavior with which to compare AL-2:ADS-3: Third-Party Detection - rely on an external message that signals the occurrence of the attack and provides attack confirmation

AL: Activity Level AL-2:ADS-2:NBS: Normal Behavior Specification AL-2:ADS-2:NBS-1: Standard - rely on some protocol standard or a set of rules - all legitimate traffic must comply AL-2:ADS-2:NBS-2: Trained - monitor network traffic and system behavior and generate threshold values for different traffic parameters - threshold setting: too low leads to too many false positives and too high reduces sensitivity - model update to reflect evolution with time

AL: Activity Level AL-2:ARS: Attack Response Strategy - relieve the impact of the attack while imposing minimal collateral damage to legitimate clients AL-2:ARS-1: Agent Identification - necessary for enforcement of liability for attack traffic - ex: traceback AL-2:ARS-2: Rate-Limiting - impose a rate limit on a stream that has been characterized as malicious - lenient response technique because it will allow some attack traffic through

AL: Activity Level AL-2:ARS-3: Filtering - filter our attack streams completely - ex: dynamically deployed firewalls, TrafficMaster AL-2:ARS-4: Reconfiguration - change the topology to either add more resources to the victim or to isolate the attack machines

DL: Deployment Location DL-1: Victim Network - defense mechanisms deployed here protect this network from attacks and respond to detected attacks by alleviating the impact on the victim - ex: resource accounting, protocol security mechanisms DL-2: Intermediate Network - provide infrastructural protection service to a large number of Internet hosts - ex: pushback and traceback DL-3: Source Network - prevent network customers from generating DDoS attacks

Conclusion DDoS attacks are complex and serious problem - affecting not only a victim but the victim’s legitimate clients DDoS defense approaches are numerous - need to learn how to combine the approaches to completely solve the problem Internet community must cooperate to counter threat - global deployment of defense mechanisms






