Frameworks, Standards, Guidelines, and Best Practices Dan
34 Slides6.05 MB

Frameworks, Standards, Guidelines, and Best Practices Dan Wagner, B.S., CISSP, CRISC, CISA, VCE-CIA Compliance Auditor, Cyber Security WECC Reliability & Security Workshop San Diego, CA – October 23–24, 2018 W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G
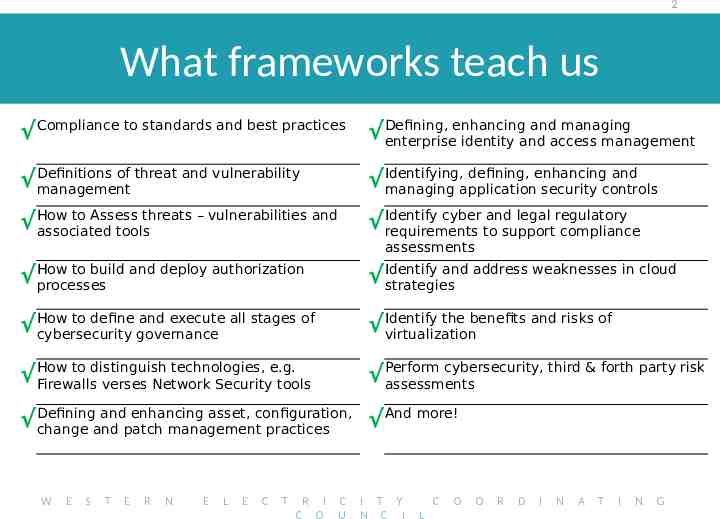
2 What frameworks teach us enhancing and managing Compliance to standards and best practices Defining, enterprise identity and access management of threat and vulnerability Definitions management defining, enhancing and Identifying, managing application security controls to Assess threats – vulnerabilities and How associated tools cyber and legal regulatory Identify requirements to support compliance assessments to build and deploy authorization How processes and address weaknesses in cloud Identify strategies to define and execute all stages of How cybersecurity governance the benefits and risks of Identify virtualization to distinguish technologies, e.g. How Firewalls verses Network Security tools cybersecurity, third & forth party risk Perform assessments and enhancing asset, configuration, And more! Defining change and patch management practices W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

3 Early Stages W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

4 NIST, DRII, BCI, CSA, ISO, COBIT, VRMMM, SCRM, DAMA, ITIL, SDLC Each of the above voluntary Frameworks present standards, guidelines, and best practices for managing cybersecurity-related risks. The NIST Cybersecurity Framework’s prioritized and flexible approach promotes the protection and resilience of critical infrastructure and other sectors important to the economy and national security. W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

5 W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G
6 W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G
7 Constantly learning? W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

Industry Advice

9 NIST, DRII, BCI, CSA, ISO, COBIT, VRMMM, SCRM, DAMA, ITIL, SDLC Each of the above voluntary Frameworks integrate standards, guidelines, maturity models and best practices for managing cybersecurity-related risks. The NIST Cybersecurity Framework’s prioritized and flexible approach promotes the protection and resilience of critical infrastructure and other sectors important to the economy and national security. W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

10 Frameworks, Standards, Guidelines, and Best Practice - Examples Disaster Recovery Institute International (DRII) https://drii.org/ The Business Continuity Institute (BCI) https://www.thebci.org/ The DAMA Guide to the Data Management Body of Knowledge (DAMA-DMBOK) https://dama.org/content/body-knowledge VENDOR RISK MANAGEMENT MATURITY MODEL (VRMMM) https://sharedassessments.org/vrmmm/ Supply-Chain Risk Management (SCRM) http://www.scrlc.com/ W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G
11 Frameworks, Standards, Guidelines, and Best Practice - Examples Framework for Improving Critical Infrastructure Cybersecurity and related news, information: www.nist.gov/cyberframework Additional cybersecurity resources: http://csrc.nist.gov/ Questions, comments, ideas: [email protected] COBIT (Control Objectives for Information and Related Technologies) http://www.isaca.org/Knowledge-Center/COBIT/Pages/Overview.aspx Capability Maturity Model Integration (CMMI) https://cmmiinstitute.com/ W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

Disaster Recovery Institute Intl (DRII)

The Business Continuity Institute (BCI)

The DAMA Guide to the Data Management Body of Knowledge (DAMA-DMBOK)
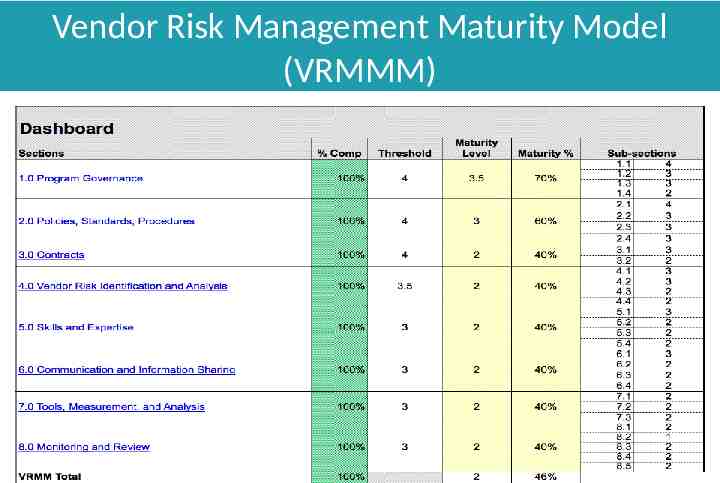
Vendor Risk Management Maturity Model (VRMMM)
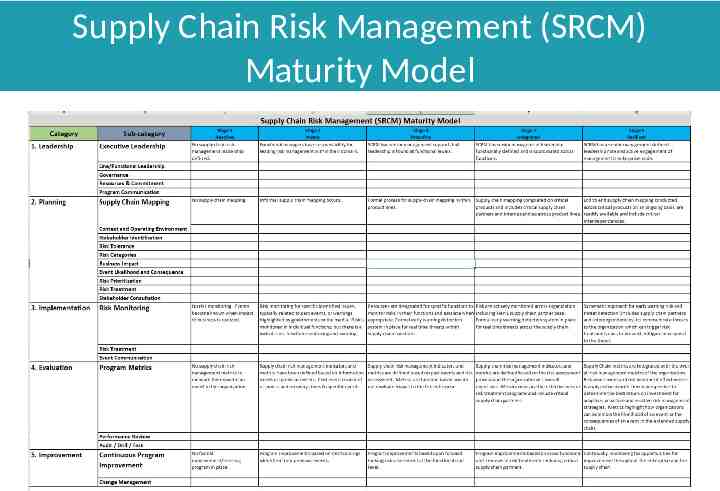
Supply Chain Risk Management (SRCM) Maturity Model
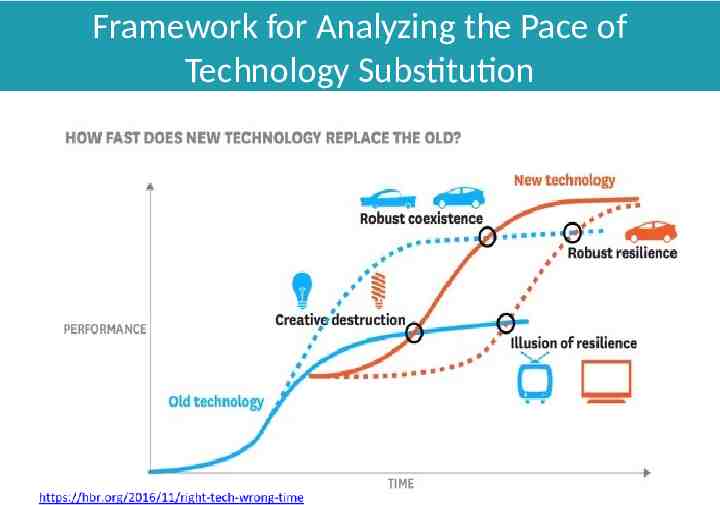
Framework for Analyzing the Pace of Technology Substitution
Cannot Predict Professional Advice

19 What is significant to your role W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G

The Business Continuity Institute (BCI)
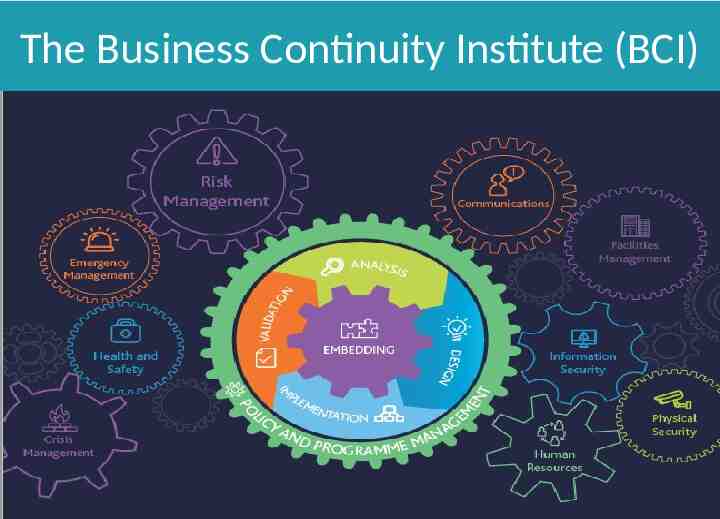
The Business Continuity Institute (BCI)

BCI – PP1
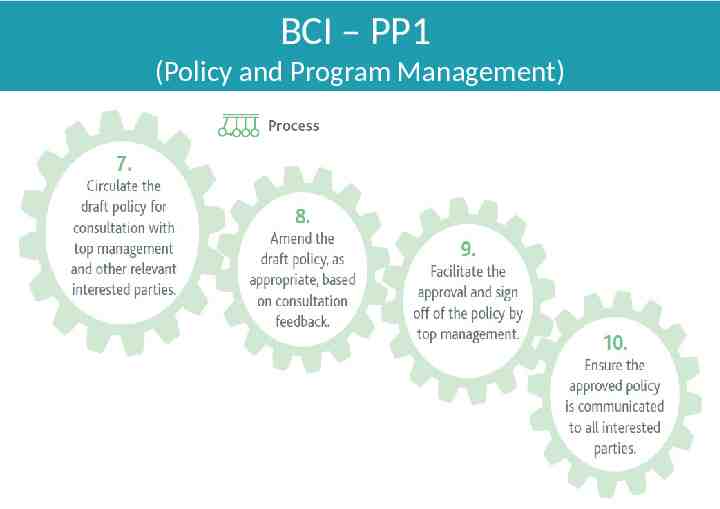
BCI – PP1 (Policy and Program Management)

BCI – PP2
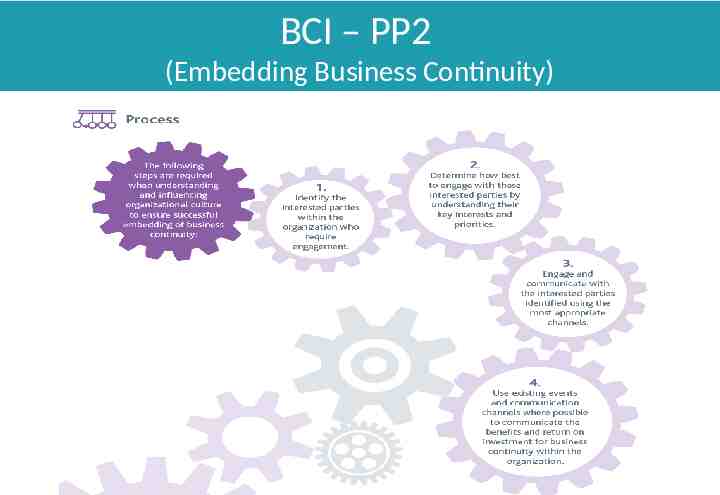
BCI – PP2 (Embedding Business Continuity)

BCI – PP3
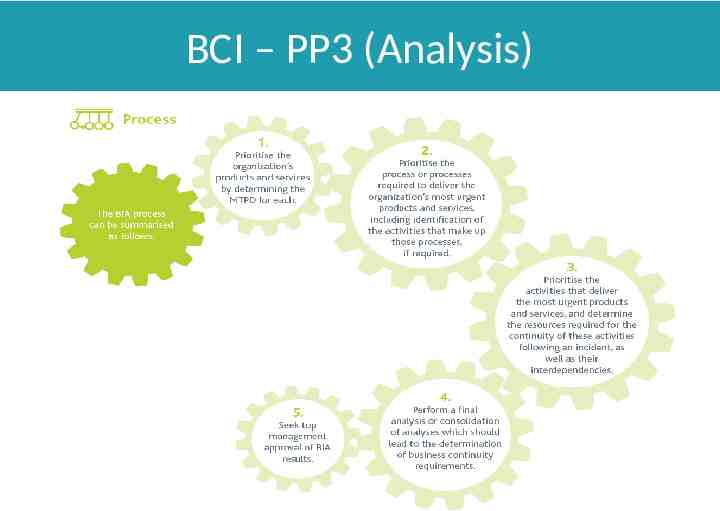
BCI – PP3 (Analysis)
BCI – PP4
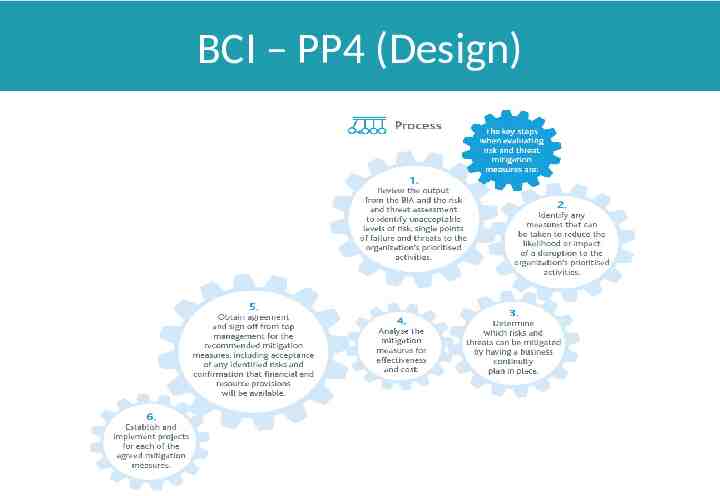
BCI – PP4 (Design)

BCI – PP5
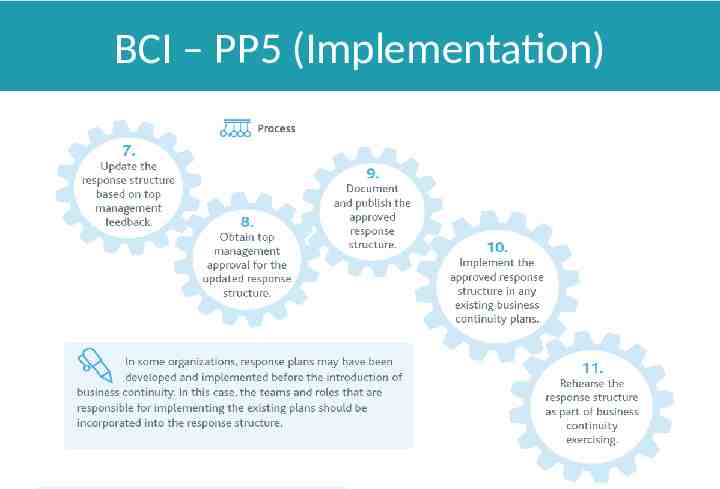
BCI – PP5 (Implementation)

BCI – PP6
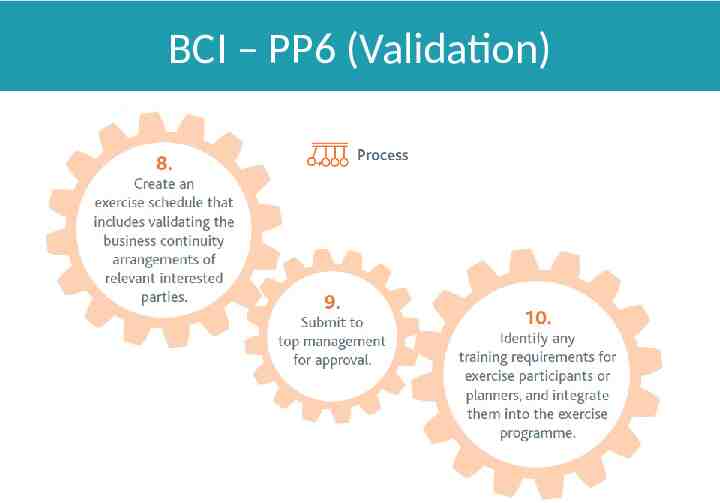
BCI – PP6 (Validation)

34 Questions? Dan Wagner B.S., CISSP, CRISC, CISA, VCE-CIA Compliance Auditor, Cyber Security Audits Western Electricity Coordinating Council 155 N 400 West Suite 200, Salt Lake City, UT 84103 [email protected] W E S T E R N E L E C T R I C O C U I T Y N C I C L O O R D I N A T I N G