Xen and the Art of Binary Modification Lies, Damn Lies, and Page
8 Slides175.00 KB

Xen and the Art of Binary Modification Lies, Damn Lies, and Page Frame Addresses Greg Cooksey and Nate Rosenblum, March 2007 1
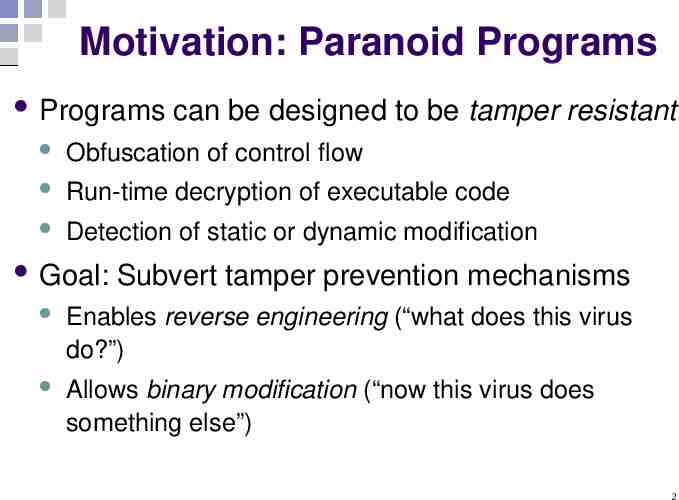
Motivation: Paranoid Programs Programs can be designed to be tamper resistant Obfuscation of control flow Run-time decryption of executable code Detection of static or dynamic modification Goal: Subvert tamper prevention mechanisms Enables reverse engineering (“what does this virus do?”) Allows binary modification (“now this virus does something else”) 2
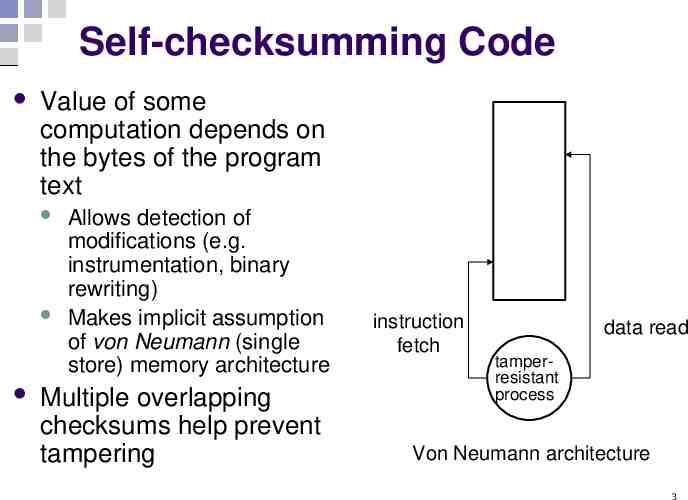
Self-checksumming Code Value of some computation depends on the bytes of the program text Allows detection of modifications (e.g. instrumentation, binary rewriting) Makes implicit assumption of von Neumann (single store) memory architecture Multiple overlapping checksums help prevent tampering instruction fetch data read tamperresistant process Von Neumann architecture 3
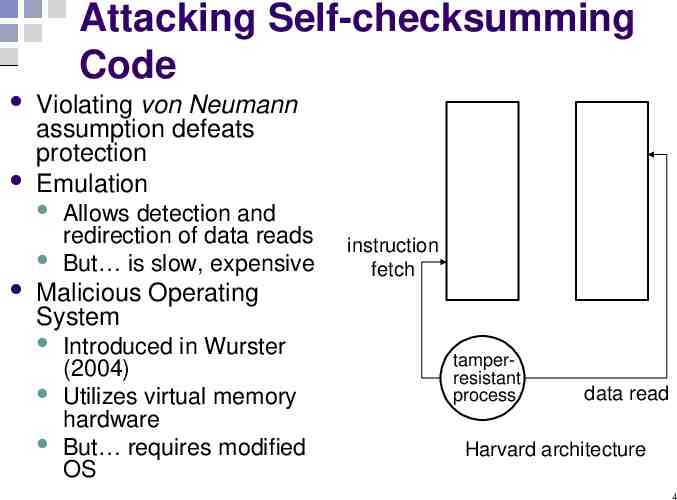
Attacking Self-checksumming Code Violating von Neumann assumption defeats protection Emulation Allows detection and redirection of data reads But is slow, expensive instruction fetch Malicious Operating System Introduced in Wurster (2004) Utilizes virtual memory hardware But requires modified OS tamperresistant process data read Harvard architecture 4

Malicious Virtualization Hypothesis: The Virtual Machine Monitor is a superior malicious agent VMM is responsible for managing virtual memory Able to modify virtual memory without operating system assistance Allows attacks on commodity operating systems (e.g. Microsoft Windows) Virtualization is significantly less expensive than emulation Xen: Linux-based open source VMM 5
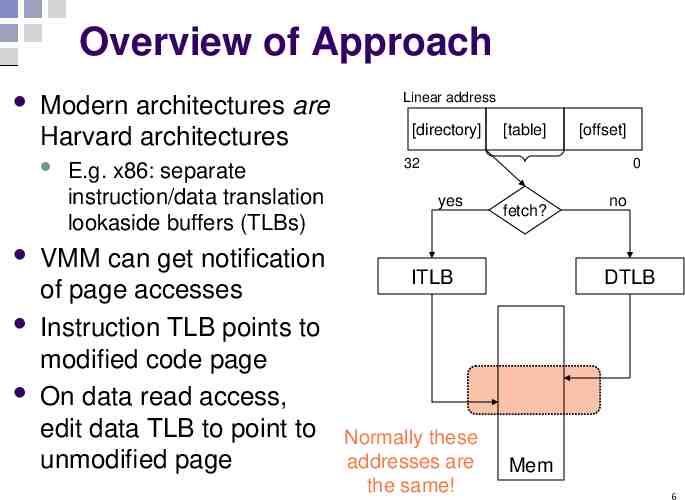
Overview of Approach Modern architectures are Harvard architectures E.g. x86: separate instruction/data translation lookaside buffers (TLBs) VMM can get notification of page accesses Instruction TLB points to modified code page On data read access, edit data TLB to point to unmodified page Linear address [directory] [table] [offset] 32 0 yes fetch? ITLB Normally these addresses are the same! no DTLB Mem 6
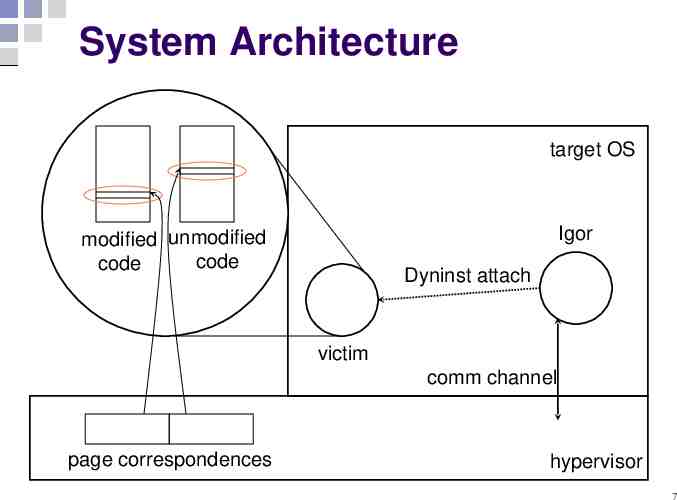
System Architecture target OS Igor modified unmodified code code Dyninst attach victim comm channel page correspondences hypervisor 7
Current Status Running modified Xen and XenLinux installations Tracking of page faults in target program address space Currently implemented with device driver that makes hypercalls to Xen Remaining tasks: TLB entry installation Igor process Communication channel from Igor to Xen hypervisor Performance measurements 8