Pete Cooper Pavisade, CEO Cyber Strategy
23 Slides4.35 MB

Pete Cooper Pavisade, CEO Cyber Strategy

SAFETY?

SECURITY?
CYBERSECURITY?

Culture Safety Culture Security Culture Cybersecurity culture This is about how we work together

Pictures
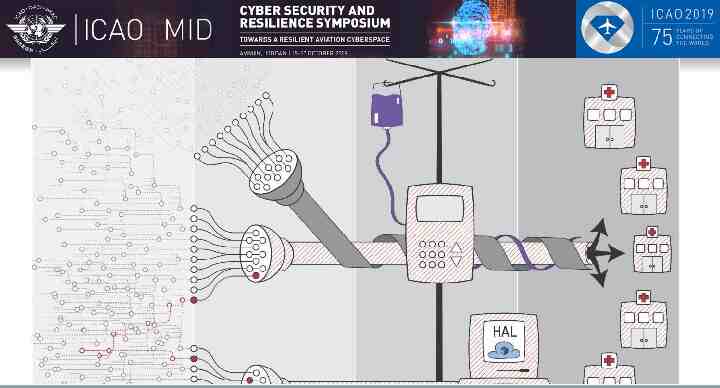
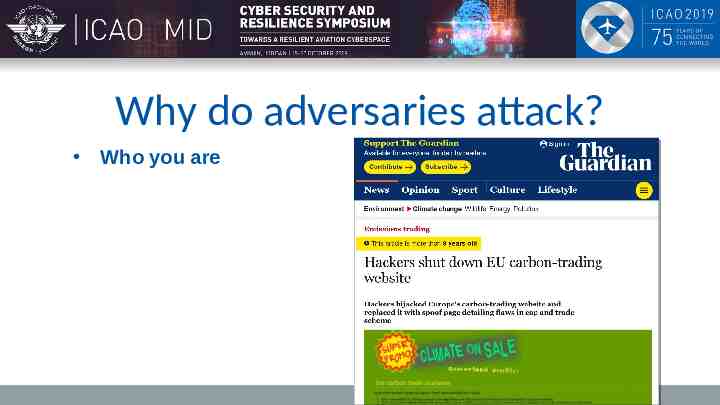
Why do adversaries attack? Who you are
Why do adversaries attack? Who you are What you are doing
Why do adversaries attack? Who you are What you are doing What you have
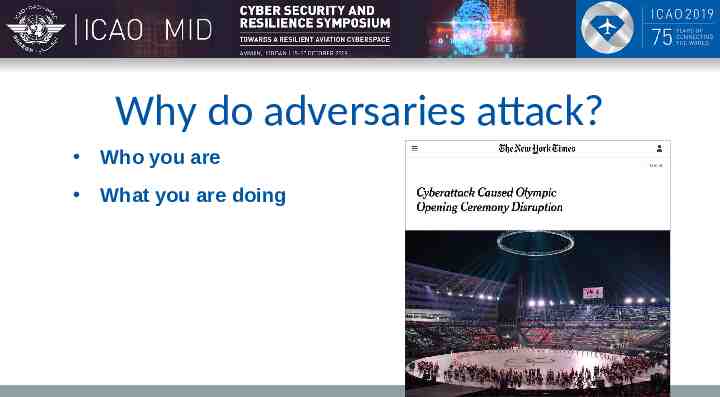
Why do adversaries attack? Who you are What you are doing What you have

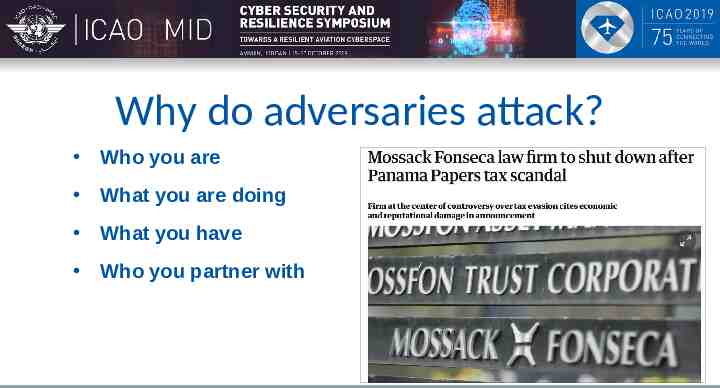
Why do adversaries attack? Who you are What you are doing What you have Who you partner with
Why do adversaries attack? Who you are What you are doing What you have Who you partner with What you are using and how you use it
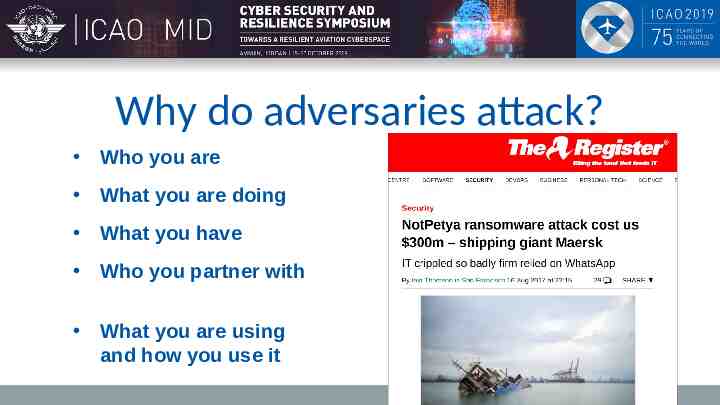
Why do adversaries attack? Who you are What you are doing What you have Targeted adversary effort to achieve their aims – Which are . Who you partner with What you are using and how you use it Technology .
How are we being attacked? Adversary leadership & teamwork Adversary mindset – Vision / Outcome focussed – Clear Strategy – Well defined aims – Path of least resistance “Where is the battlefield?” “ . Everywhere” When are we engaged? .All the time (Unrestricted warfare, Liang & Xiangsui 1999) (Me, 2015) Strategy Operations Tactics

How attacks will evolve st 1 generation Data Integrity System Availability Deny / Disrupt Data Confidentiality From air / ground / space data-links to on-board wifi Safety critical information / instructions nd 2 generation

Availability Attacks Planning for failure Back-ups Bandwidth

Confidentiality Attacks Anonymity?

Integrity Attacks Vs People

Integrity Attacks Vs People Vs Technology?
Changing our thinking Culture – Org national international Strategic Foresight vs technical solutions Strive to find, fix gaps – minimise attack surface Anticipate and collaboratively train for attacks Strive for objectivity

Thank You








