October 2015 The Evolving Malware Threat (Past, Present, & Future)
85 Slides6.14 MB
October 2015 The Evolving Malware Threat (Past, Present, & Future) Larry G. Wlosinski, Company CISSP, CAP, CCSP, CISM, CISA, CRISC, CBCP, CDP, ITIL v3 L [email protected] LOGO 1

Larry G. Wlosinski CISSP, CAP, CCSP, CISM, CISA, CRISC, CBCP, CDP, ITIL v3 Federal Government Experience (25 yrs) EPA, NIH, CMS, DOJ, DHS, DOE, DIA, NOAA, SSA Commercial Industry Experience (14 yrs) Insurance, International & Interstate Banking, Collections, Small Business Consulting Experience Veris Group, LLC – Senior Associate Computer Sciences Corp. (CSC) – Section Manager Lockheed Martin – IT Security Manager Booz Allen Hamilton (BAH) – Associate And others – Sr. IT Security Engineer, Project Manager, etc. IT Security Expertise (16 yrs) Cybersecurity IT Security Assessments (C&A/A&A, Risk, Audit) Continuity Planning (OEP, BIA, ISCP, COOP, DRP, Devolution, etc.) Cloud Security Policy, Procedures, Guidance, Standards, Templates, Checklists Incident Response & Planning 2

Agenda Malware – Past Types of Viruses Malware Hiding Places Types of Trojan Horses Type of Botnet Attacks Recent Examples - Present Takedowns - Past Trends and Predictions - Future Threats & Countermeasures – Past & Present Malware as a Service (MaaS) – Future? 3
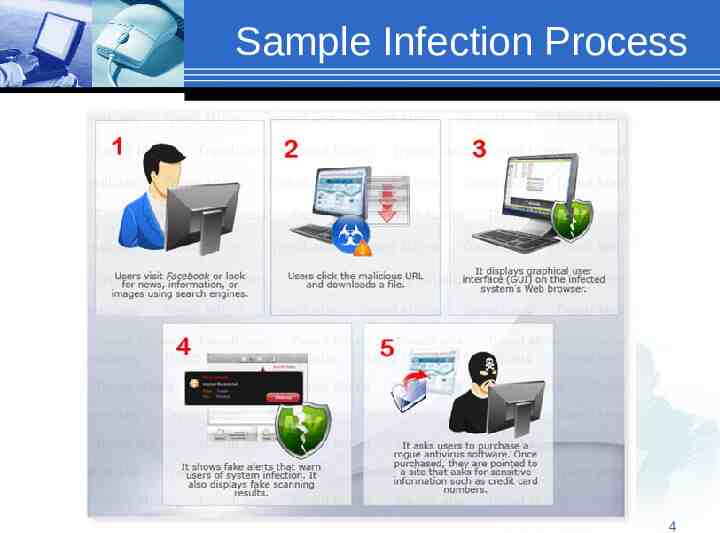
Sample Infection Process 4

Malware - Past Company LOGO 5
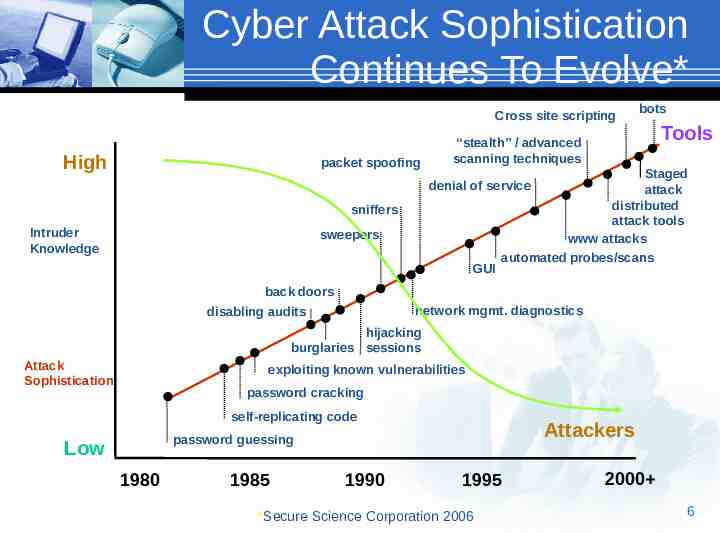
Cyber Attack Sophistication Continues To Evolve* Cross site scripting High packet spoofing bots “stealth” / advanced scanning techniques Tools Staged attack distributed attack tools www attacks automated probes/scans denial of service sniffers Intruder Knowledge sweepers GUI back doors network mgmt. diagnostics disabling audits hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking self-replicating code Low Source: CERT Attackers password guessing 1980 1985 1990 1995 *Secure Science Corporation 2006 2000 6 6

Types of Malicious Code Virus Trojan Horse Worm Logic Bomb Trap Door Keylogger Rootkit Spyware Adware Scareware Crimeware Malicious Apps Command & Control (C&C) Bots & Botnets Data Proximity Copier 7
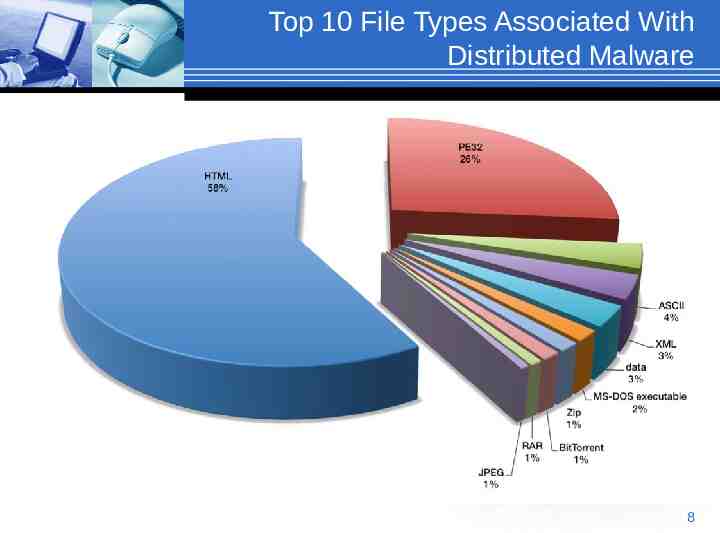
Top 10 File Types Associated With Distributed Malware 8
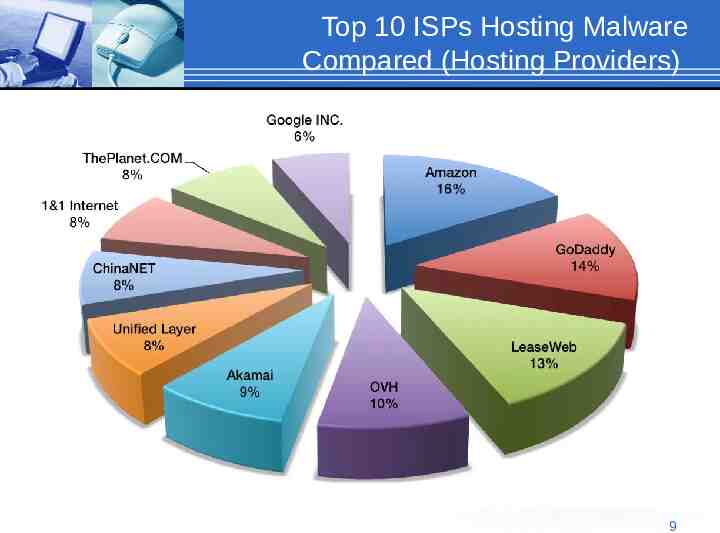
Top 10 ISPs Hosting Malware Compared (Hosting Providers) 9
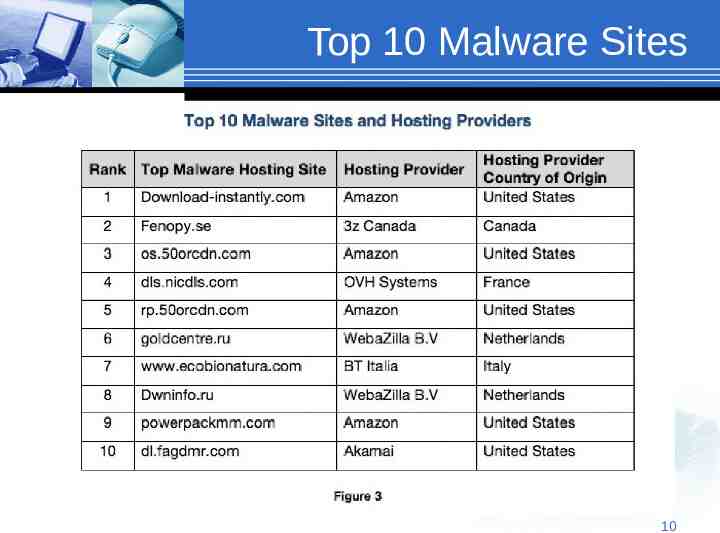
Top 10 Malware Sites 10
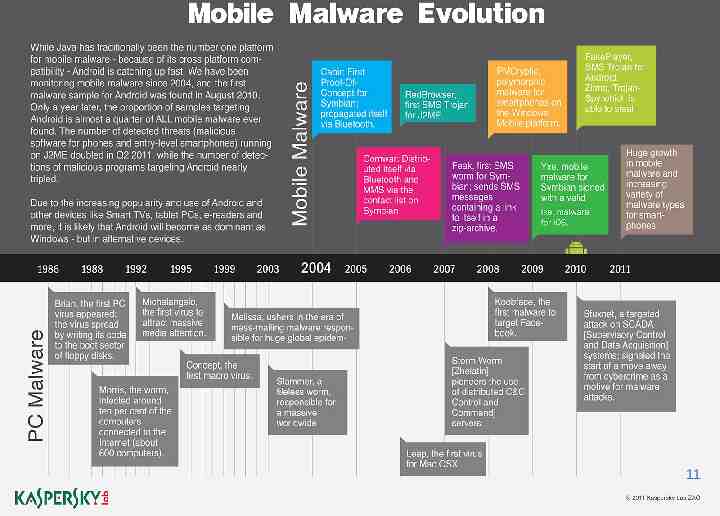
11 11
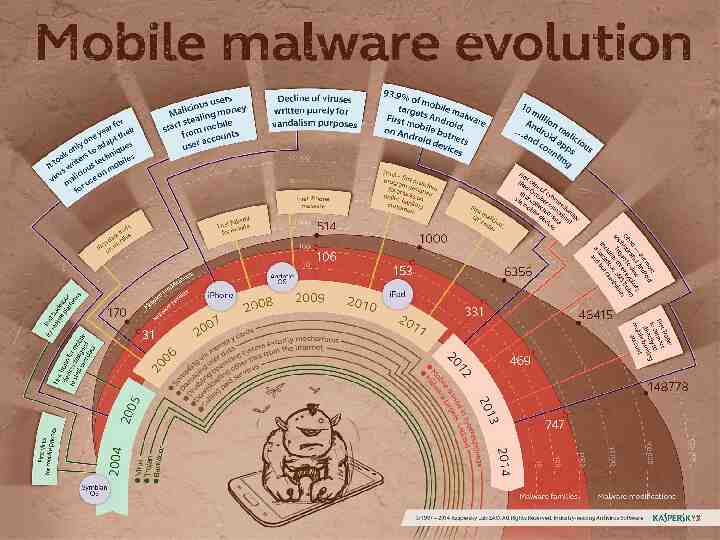
12
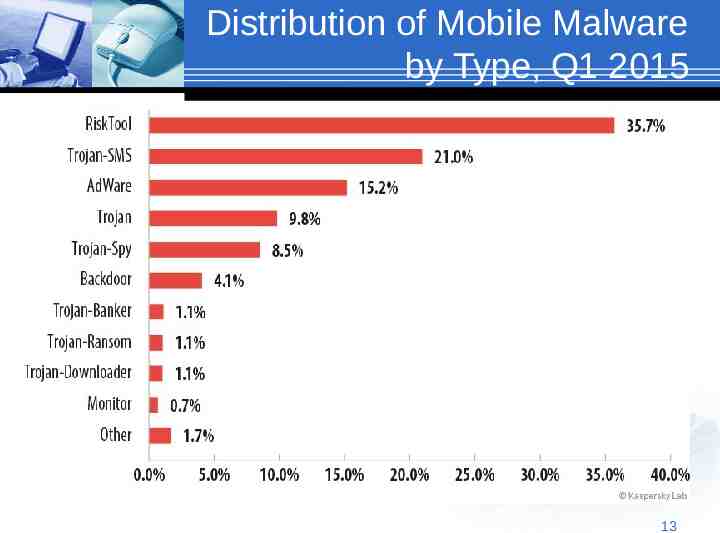
Distribution of Mobile Malware by Type, Q1 2015 13
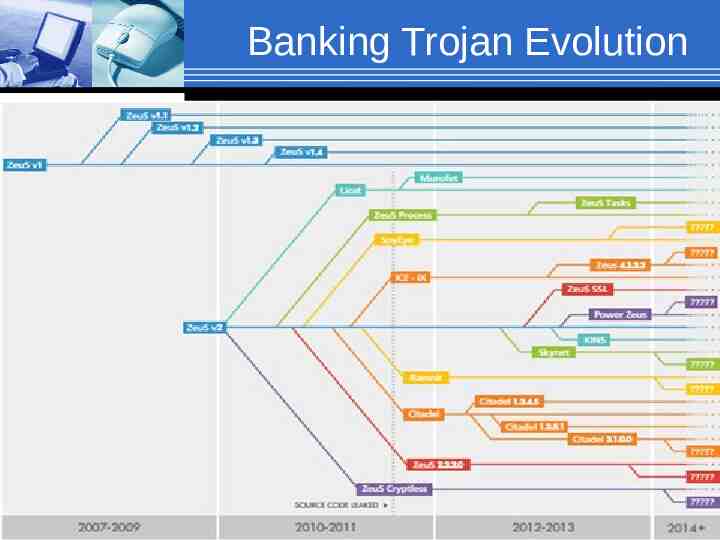
Banking Trojan Evolution 14
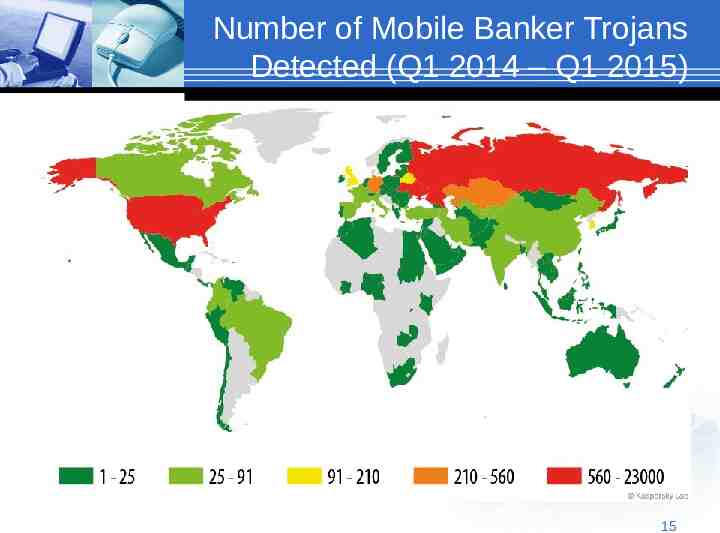
Number of Mobile Banker Trojans Detected (Q1 2014 – Q1 2015) 15

Vulnerable WordPress Versions Discovered 16
WordPress Exploited WordPress is a Content Management System (CMS) used extensively to create business web sites. “Thousands of WordPress sites host Neutrino Exploit Kit” http://securityaffairs.co/wordpress/39495/cyber-crime/neutrino-exploit-kit-wordpress.h tml?utm source hs email&utm medium email&utm content 21503522& hsenc p2 ANqtz-8ktT2A upOdPiuC3FONJq-68HSeKCAsb22S8hWsbg4Dn qkX5cFleXABXz741mhRC8iEcoMv2tShBOMbYAHb0JOLXQA& hsmi 21503522 “Solving WordPress Security Weaknesses for 10 Million Websites” http://www.verisgroup.com/wp-content/uploads/2015/06/Securing-WordPress-whitepaper.pdf 17

Types of Viruses Multipartite Appending Overwriting Companion Cluster Polymorphic Company LOGO Tunneling Stealth Bimodal Self-garbling Memory Resident Proof of Concept 18

Virus Types Multipartite – a multi-part virus, a virus that attempts to attack both the boot sector and the executable, or program, files at the same time. When the virus attaches to the boot sector, it will in turn affect the system s files, and when the virus attaches to the files, it will in turn infect the boot sector. Appending - A virus that inserts a copy of its malicious code at the end of the file. The goal of an appending virus is not to harm the host program, but to modify it to hold the virus code and then be able to run itself. Overwriting - A type of computer virus that will copy its own code over the host computer system's file data, which destroys the original program. After your computer system has been cleaned using an antivirus program, users will need to install the original program again. http://www.webopedia.com/TERM/V/virus.html 19

Virus Types Companion - A type of computer virus that compromises a feature of DOS that enables software with the same name, but different extensions, to operate with different priorities. For example you may have program.exe on your computer, and the virus may create a file called program.com. When the computer executes program.exe, the virus runs program.com before program.exe is executed. In many cases, the real program will run so users believe that the system is operating normally and aren't aware that a virus was run on the system. Cluster - A type of computer virus that associates itself with the execution of programs by modifying directory table entries to ensure the virus itself will start when any program on the computer system is started. If infected with a cluster virus it will appear as if every program on the computer system is infected; however, a cluster virus is only in one place on the system. http://www.webopedia.com/TERM/V/virus.html 20
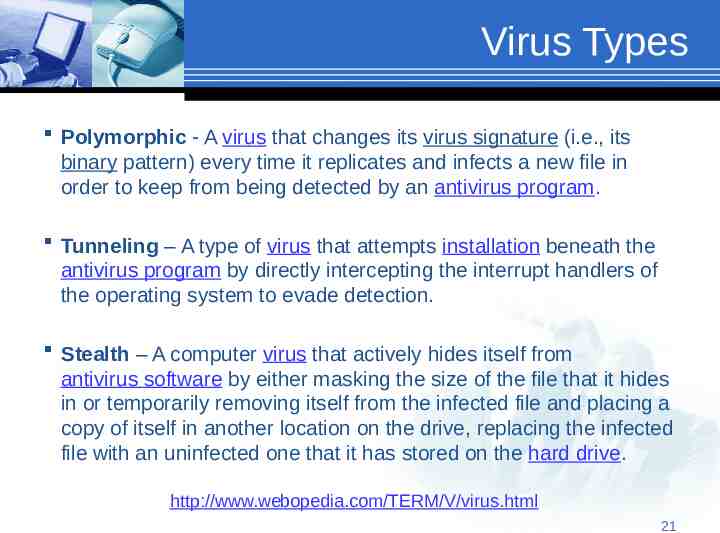
Virus Types Polymorphic - A virus that changes its virus signature (i.e., its binary pattern) every time it replicates and infects a new file in order to keep from being detected by an antivirus program. Tunneling – A type of virus that attempts installation beneath the antivirus program by directly intercepting the interrupt handlers of the operating system to evade detection. Stealth – A computer virus that actively hides itself from antivirus software by either masking the size of the file that it hides in or temporarily removing itself from the infected file and placing a copy of itself in another location on the drive, replacing the infected file with an uninfected one that it has stored on the hard drive. http://www.webopedia.com/TERM/V/virus.html 21
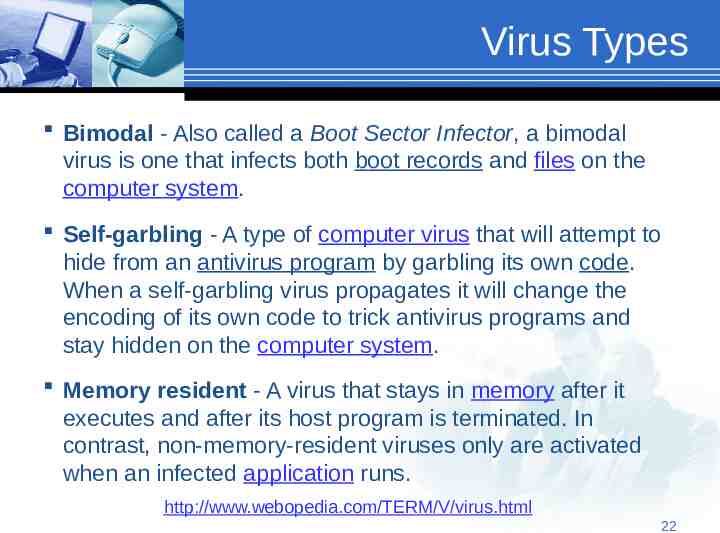
Virus Types Bimodal - Also called a Boot Sector Infector, a bimodal virus is one that infects both boot records and files on the computer system. Self-garbling - A type of computer virus that will attempt to hide from an antivirus program by garbling its own code. When a self-garbling virus propagates it will change the encoding of its own code to trick antivirus programs and stay hidden on the computer system. Memory resident - A virus that stays in memory after it executes and after its host program is terminated. In contrast, non-memory-resident viruses only are activated when an infected application runs. http://www.webopedia.com/TERM/V/virus.html 22

Virus Types Proof of Concept - A proof of concept virus is written by an individual with advanced programming skills, usually to 'show off' their programming talents or to point out a vulnerability in a specific software. Usually authors of proof-of-concept viruses will send these programs to an anti-virus software developer, and the programmer would be more apt to produce a blueprint on how the virus would work, rather than launching the virus maliciously. http://www.webopedia.com/TERM/V/virus.html 23

Malware Hiding Places Executables Word Excel PowerPoint Company Obfuscation Techniques LOGO 24 24
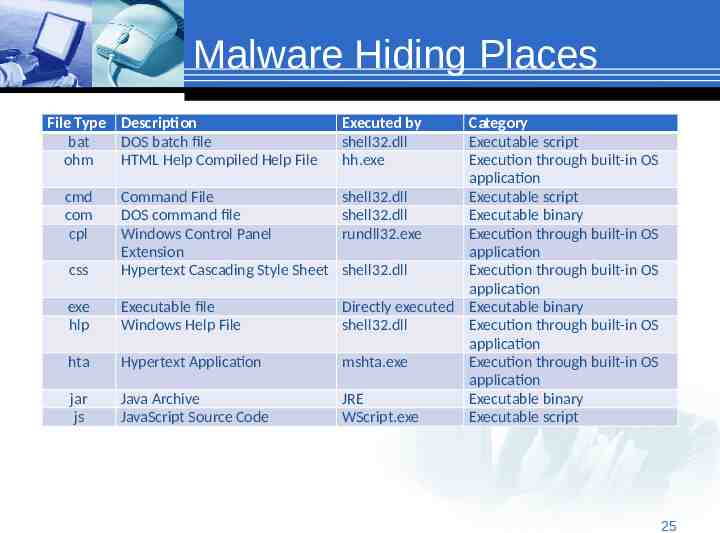
Malware Hiding Places File Type Description bat DOS batch file ohm HTML Help Compiled Help File cmd com cpl css exe hlp hta jar js Executed by shell32.dll hh.exe Category Executable script Execution through built-in OS application Command File shell32.dll Executable script DOS command file shell32.dll Executable binary Windows Control Panel rundll32.exe Execution through built-in OS Extension application Hypertext Cascading Style Sheet shell32.dll Execution through built-in OS application Executable file Directly executed Executable binary Windows Help File shell32.dll Execution through built-in OS application Hypertext Application mshta.exe Execution through built-in OS application Java Archive JRE Executable binary JavaScript Source Code WScript.exe Executable script 2525
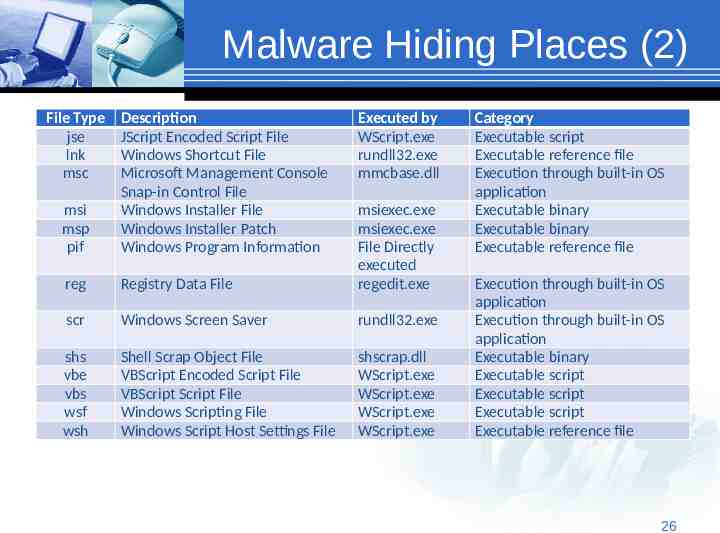
Malware Hiding Places (2) File Type jse lnk msc msi msp pif Description JScript Encoded Script File Windows Shortcut File Microsoft Management Console Snap-in Control File Windows Installer File Windows Installer Patch Windows Program Information Executed by WScript.exe rundll32.exe mmcbase.dll reg Registry Data File msiexec.exe msiexec.exe File Directly executed regedit.exe scr Windows Screen Saver rundll32.exe shs vbe vbs wsf wsh Shell Scrap Object File VBScript Encoded Script File VBScript Script File Windows Scripting File Windows Script Host Settings File shscrap.dll WScript.exe WScript.exe WScript.exe WScript.exe Category Executable script Executable reference file Execution through built-in OS application Executable binary Executable binary Executable reference file Execution through built-in OS application Execution through built-in OS application Executable binary Executable script Executable script Executable script Executable reference file 2626
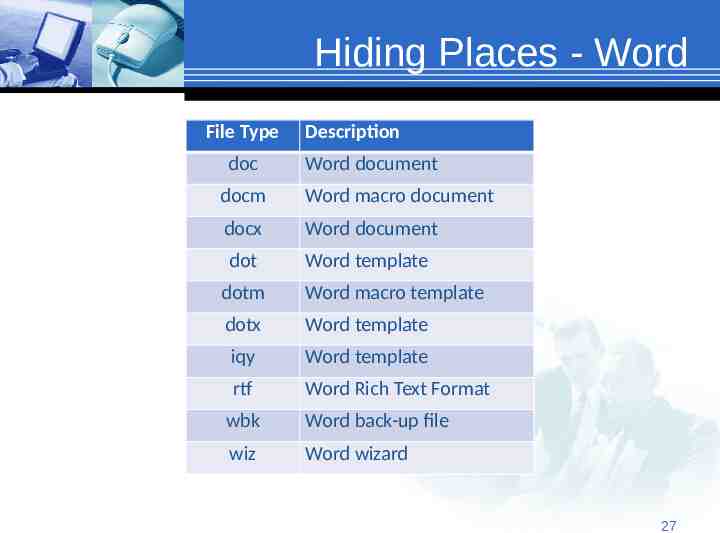
Hiding Places - Word File Type doc Description Word document docm Word macro document docx Word document dot Word template dotm Word macro template dotx Word template iqy Word template rtf Word Rich Text Format wbk Word back-up file wiz Word wizard 2727
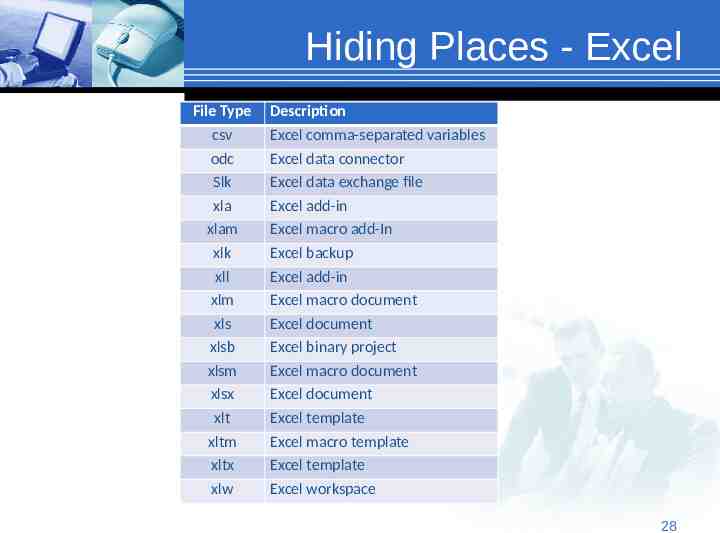
Hiding Places - Excel File Type csv odc Slk xla xlam xlk xll xlm xls xlsb xlsm xlsx xlt xltm xltx xlw Description Excel comma-separated variables Excel data connector Excel data exchange file Excel add-in Excel macro add-In Excel backup Excel add-in Excel macro document Excel document Excel binary project Excel macro document Excel document Excel template Excel macro template Excel template Excel workspace 2828
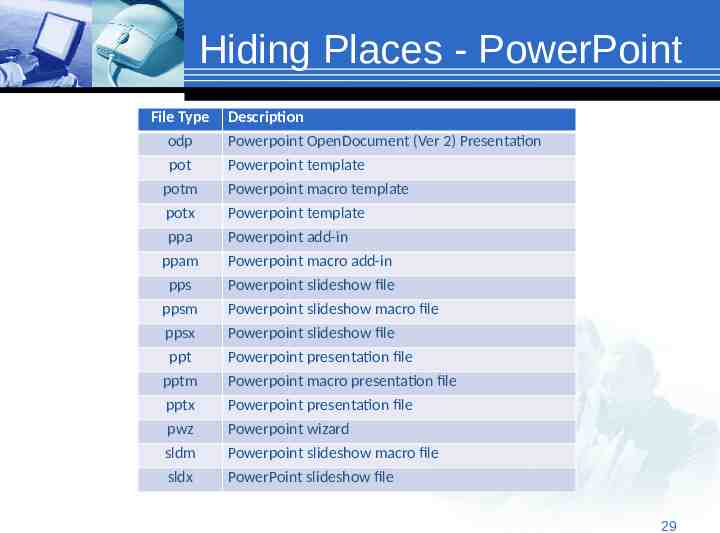
Hiding Places - PowerPoint File Type odp pot Description Powerpoint OpenDocument (Ver 2) Presentation Powerpoint template potm Powerpoint macro template potx Powerpoint template ppa Powerpoint add-in ppam pps Powerpoint macro add-in Powerpoint slideshow file ppsm Powerpoint slideshow macro file ppsx Powerpoint slideshow file ppt Powerpoint presentation file pptm pptx Powerpoint macro presentation file Powerpoint presentation file pwz Powerpoint wizard sldm Powerpoint slideshow macro file sldx PowerPoint slideshow file 2929

Obfuscation Techniques: [MPack] Utilizes the Javascript escape function to convert ASCII characters to hexadecimal equivalents. Uses a simple rotation cipher Utilizes Javascript to split strings apart Saves the payload to execute as a partially random filename, starting with ‘sys’ on the victim machine 3030

Types of Trojan Horses Company LOGO 31
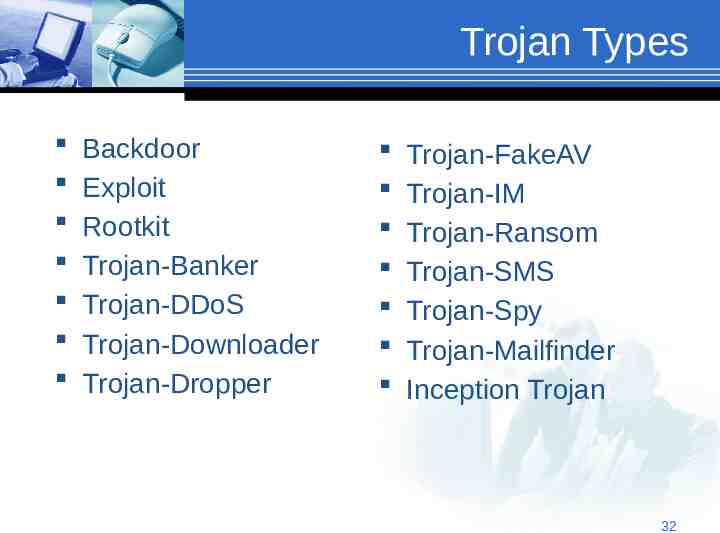
Trojan Types Backdoor Exploit Rootkit Trojan-Banker Trojan-DDoS Trojan-Downloader Trojan-Dropper Trojan-FakeAV Trojan-IM Trojan-Ransom Trojan-SMS Trojan-Spy Trojan-Mailfinder Inception Trojan 32
Trojan Types Backdoor Gives malicious users remote control over the infected computer. Enables the author to do anything they wish on the infected computer – including sending, receiving, launching, and deleting files, displaying data, and rebooting the computer. Often used to unite a group of victim computers to form a botnet or zombie network that can be used for criminal purposes. Exploit - Exploits are programs that contain data or code that takes advantage of a vulnerability within application software that’s running on your computer. https://usa.kaspersky.com/internet-security-center/threats/trojans#.VYbKY1KPuv0 33

Trojan Types Rootkit - Rootkits are designed to conceal certain objects or activities in your system. Often their main purpose is to prevent malicious programs being detected – in order to extend the period in which programs can run on an infected computer. Trojan-Banker - Trojan-Banker programs are designed to steal your account data for online banking systems, e-payment systems, and credit or debit cards. https://usa.kaspersky.com/internet-security-center/threats/trojans#.VYbKY1KPuv0 34

Trojan Types Trojan-DDoS - These programs conduct DoS (Denial of Service) attacks against a targeted web address. By sending multiple requests – from your computer and several other infected computers – the attack can overwhelm the target address leading to a denial of service. Trojan-Downloader - Can download and install new versions of malicious programs onto your computer – including Trojans and Adware. https://usa.kaspersky.com/internet-security-center/threats/trojans#.VYbKY1KPuv0 35

Trojan Types Trojan-Dropper – Used to install Trojans and/or viruses, or to prevent the detection of malicious programs. Trojan-FakeAV - Simulates the activity of antivirus software. Designed to extort money from you for the detection and removal of threats even though the threats they report are actually non-existent. https://usa.kaspersky.com/internet-security-center/threats/trojans#.VYbKY1KPuv0 36
Trojan Types Trojan-IM - Steal your logins and passwords for instant messaging programs (e.g., ICQ, MSN Messenger, AOL Instant Messenger, Yahoo Pager, Skype). Trojan-Ransom - Can modify data on your computer so that your computer doesn’t run correctly, or you can no longer use specific data. The criminal will only restore your computer’s performance or unblock your data, after you have paid them the ransom money that they demand. https://usa.kaspersky.com/internet-security-center/threats/trojans#.VYbKY1KPuv0 37
Trojan Types Trojan-SMS - Can cost you money by sending text messages from your mobile device to premium rate phone numbers. Trojan-Spy - Can spy on how you’re using your computer (e.g., tracking the data you enter via your keyboard, taking screen shots, or getting a list of running applications). Trojan-Mailfinder - Can harvest email addresses from your computer. https://usa.kaspersky.com/internet-security-center/threats/trojans#.VYbKY1KPuv0 38

Inception Trojan The ‘Inception’ trojan can respond to 14 commands: 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. photo - uploads photo from your gallery contact - uploads phone contacts call log - uploads call history upload message - uploads text messages location - uploads location of the user's device send message - send text message phone - uploads phone info including phone number list file - uploads file paths of files on external storage upload file - uploads file from device by path delete file - delete file by file path download - download file call number - makes phone call record - record microphone for designated period of time, and upload it combine - combination of four commands (phone, contact, call log, upload message) commands 39
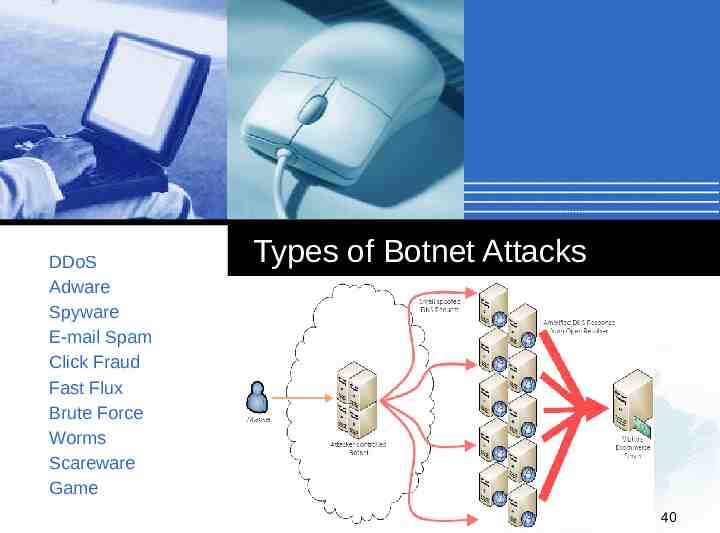
DDoS Adware Spyware E-mail Spam Click Fraud Fast Flux Brute Force Worms Scareware Game Types of Botnet Attacks Company LOGO 40
Types of Botnet Attacks Distributed Denial-of-Service (DDoS) - Multiple systems submit as many requests as possible to a single Internet computer or service, overloading it and preventing it from servicing legitimate requests. An example is an attack on a victim's phone number. The victim is bombarded with phone calls by the bots, attempting to connect to the Internet. Adware - Advertises a commercial offering actively and without the user's permission or awareness. For example by replacing banner ads on web pages with those of another advertiser. 41
Types of Botnet Attacks Spyware - Software which sends information to its creators about a user's activities (e.g., passwords, credit card numbers, and other information that can be sold on the black market. Compromised machines that are located within a corporate network can be worth more to the bot herder, as they can often gain access to confidential corporate information (e.g., Aurora botnet). 42
Types of Botnet Attacks E-mail spam - E-mail messages disguised as messages from people, but are either advertising, annoying, or malicious. Click fraud - When the user's computer visits websites without the user's awareness to create false web traffic for personal or commercial gain. Fast Flux - DNS technique used by botnets to hide phishing and malware delivery sites behind an everchanging network of compromised hosts acting as proxies. 43
Types of Botnet Attacks Brute-forcing remote machines services such as FTP, SMTP and SSH. Worms - The botnet focuses on recruiting other hosts. Scareware - Software that is marketed by creating fear in users. Once installed, it can install malware and recruit the host into a botnet. For example users can be induced to buy a rogue anti-virus to regain access to their computer. Exploiting systems by observing users playing online games such as poker and see the players' cards. 44

Recent Examples - Present Company LOGO 45

Zeus Virus Zeus, ZeuS, or Zbot is a Trojan horse malware package that runs on versions of Microsoft Windows. While it is capable of being used to carry out many malicious and criminal tasks, it is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. It is also used to install the CryptoLocker ransomware. Zeus is spread mainly through drive-by downloads and phishing schemes. Zeus is very difficult to detect even with up-to-date antivirus and other security software as it hides itself using stealth techniques. It is considered that this is the primary reason why the Zeus malware has become the largest botnet on the Internet: some 3.6 million PCs are said to be infected in the U.S. alone. https://en.wikipedia.org/wiki/Zeus %28malware%29 46

Malware News Date Category Headline 9/15/15 DDoS The Rise in Repeated 'Low and Slow' DDoS attacks 9/10/15 Ransomware PIN-changing, screen-locking Android ransomware 9/9/15 C&C Russian hacking group uses satellites to hide C&C servers DD4BC extortionist group launched over 140 DDoS attacks: 9/9/15 DDoS Akamai. Zimperium releases exploit code for testing against Stagefright 9/9/15 Exploit Kit vulnerability 9/8/15 Malware Turla Malware Group Hid C&C Traffic in Satellite Links 9/8/15 Malware Verified Play Store apps found to be spreading MKero malware Ransomware risk from over 140 million websites, researchers 9/7/15 Ransomware warn 47
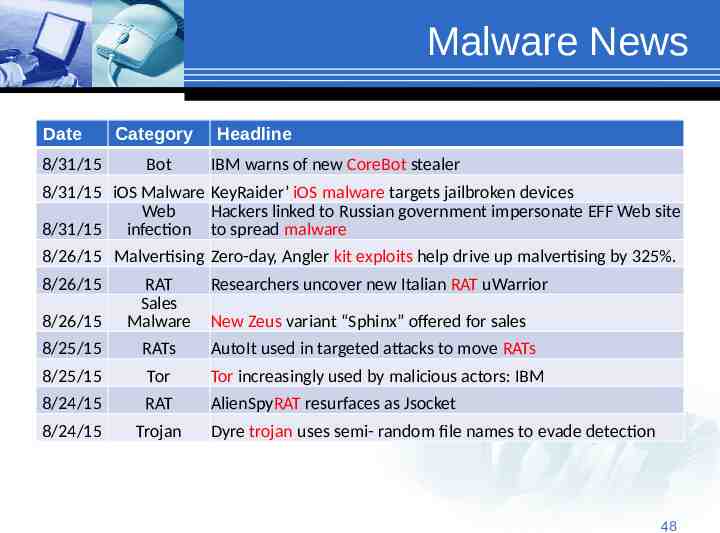
Malware News Date 8/31/15 Category Bot Headline IBM warns of new CoreBot stealer 8/31/15 iOS Malware KeyRaider’ iOS malware targets jailbroken devices Web Hackers linked to Russian government impersonate EFF Web site 8/31/15 infection to spread malware 8/26/15 Malvertising Zero-day, Angler kit exploits help drive up malvertising by 325%. 8/26/15 8/26/15 RAT Sales Malware Researchers uncover new Italian RAT uWarrior 8/25/15 RATs AutoIt used in targeted attacks to move RATs 8/25/15 Tor Tor increasingly used by malicious actors: IBM 8/24/15 RAT AlienSpyRAT resurfaces as Jsocket 8/24/15 Trojan New Zeus variant “Sphinx” offered for sales Dyre trojan uses semi- random file names to evade detection 48
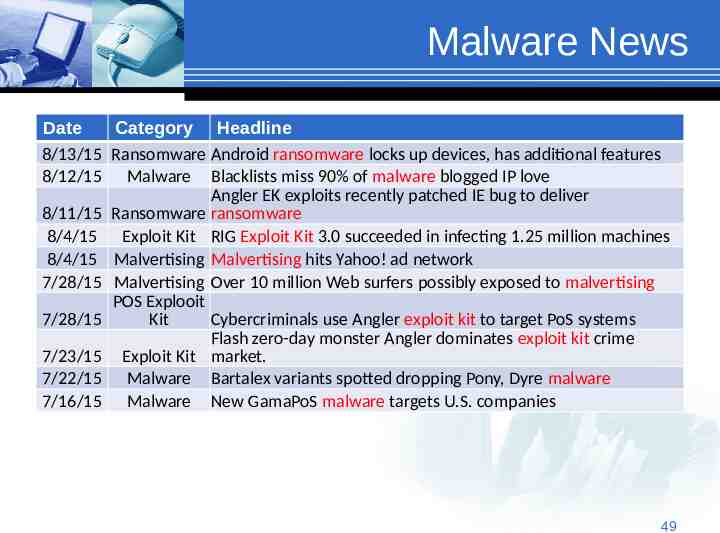
Malware News Date Category Headline 8/13/15 Ransomware Android ransomware locks up devices, has additional features 8/12/15 Malware Blacklists miss 90% of malware blogged IP love Angler EK exploits recently patched IE bug to deliver 8/11/15 Ransomware ransomware 8/4/15 Exploit Kit RIG Exploit Kit 3.0 succeeded in infecting 1.25 million machines 8/4/15 Malvertising Malvertising hits Yahoo! ad network 7/28/15 Malvertising Over 10 million Web surfers possibly exposed to malvertising POS Explooit 7/28/15 Kit Cybercriminals use Angler exploit kit to target PoS systems Flash zero-day monster Angler dominates exploit kit crime 7/23/15 Exploit Kit market. 7/22/15 Malware Bartalex variants spotted dropping Pony, Dyre malware 7/16/15 Malware New GamaPoS malware targets U.S. companies 49
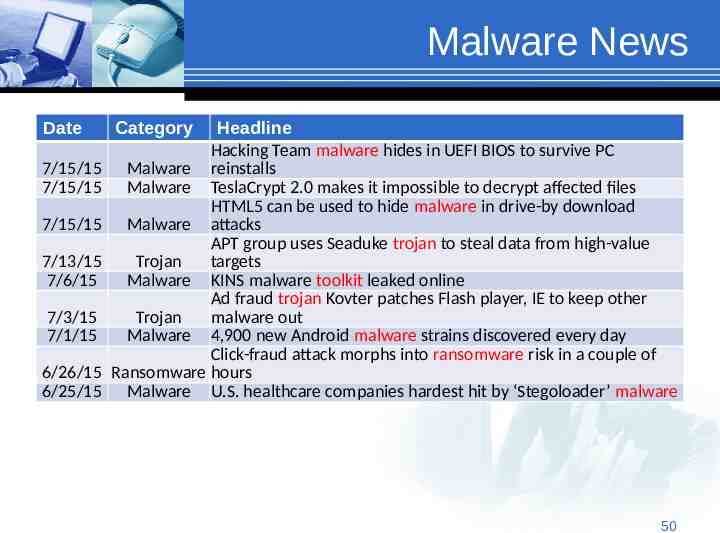
Malware News Date 7/15/15 7/15/15 7/15/15 7/13/15 7/6/15 7/3/15 7/1/15 6/26/15 6/25/15 Category Headline Hacking Team malware hides in UEFI BIOS to survive PC Malware reinstalls Malware TeslaCrypt 2.0 makes it impossible to decrypt affected files HTML5 can be used to hide malware in drive-by download Malware attacks APT group uses Seaduke trojan to steal data from high-value Trojan targets Malware KINS malware toolkit leaked online Ad fraud trojan Kovter patches Flash player, IE to keep other Trojan malware out Malware 4,900 new Android malware strains discovered every day Click-fraud attack morphs into ransomware risk in a couple of Ransomware hours Malware U.S. healthcare companies hardest hit by ‘Stegoloader’ malware 50
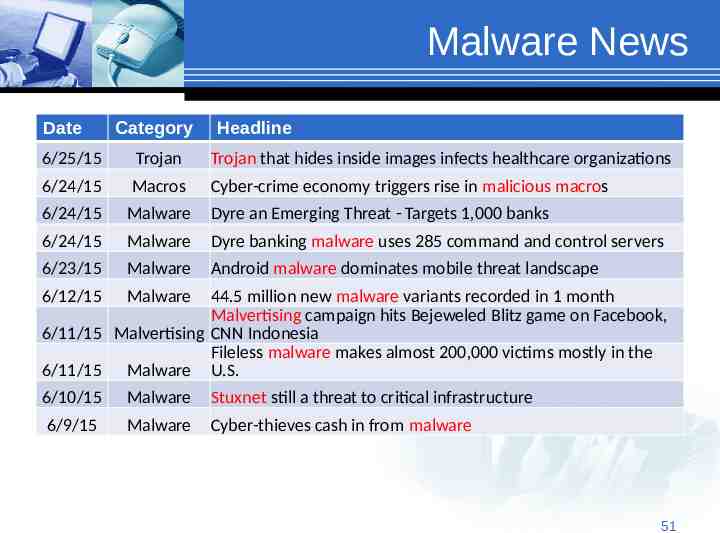
Malware News Date Category Headline 6/25/15 Trojan Trojan that hides inside images infects healthcare organizations 6/24/15 Macros Cyber-crime economy triggers rise in malicious macros 6/24/15 Malware Dyre an Emerging Threat - Targets 1,000 banks 6/24/15 Malware Dyre banking malware uses 285 command and control servers 6/23/15 Malware Android malware dominates mobile threat landscape 6/12/15 Malware 6/10/15 Malware Stuxnet still a threat to critical infrastructure 6/9/15 Malware Cyber-thieves cash in from malware 44.5 million new malware variants recorded in 1 month Malvertising campaign hits Bejeweled Blitz game on Facebook, 6/11/15 Malvertising CNN Indonesia Fileless malware makes almost 200,000 victims mostly in the 6/11/15 Malware U.S. 51

Malware News Date Category Headline 6/8/15 Malware Vawtrak banking malware found to use Tor2Web Point-of-sale (POS) malware (MalumPOS) can be configured to 6/8/15 Malware target nearly any POS system 6/5/15 Trojan Zeus banking trojan variant goes completely undetected 6/4/15 Botnet Adware-laden Skype botnet disrupted 6/3/15 Malware Cloud providers hit hard by DDoS attacks in Q1: VeriSign 6/3/15 Malware Russian crypto-malware encrypts files completely Angler Exploit Kit exploiting new Adobe vulnerability, dropping 5/29/15 Exploit Kit CryptoWall 3.0 Non-sophisticated malware steals thousands of credentials from 5/29/15 Malware targeted SMBs Amount of new malware strains more than doubled in second 5/20/15 Malware half of 2014 52

Malware News Date 5/4/15 4/28/15 4/26/15 4/22/15 4/21/15 4/21/15 4/21/15 4/20/15 4/20/15 4/20/15 Category Headline Malware known as Rombertik goes to great lengths to evade Malware analysis Malware delivered via malicious macro in Word document Malware embedded in PDF Botnets Banking botnets persist despite takedowns Malware Malware uses invisible command line argument in shortcut file Exploit Kit Fake antivirus delivered to users in the US via Fiesta exploit kit Malware New fileless malware (Phasebot) found in the wild Malvertising Zero-day malvertising attack went undetected for two months Ransomware New ransomware "Threat Finder" delivered by Angler exploit kit Botnet Pushdo spamming botnet gains strength again New variant of Upatre malware downloader integrates full SSL Malware encryption 53

Takedowns – Past Company LOGO 54
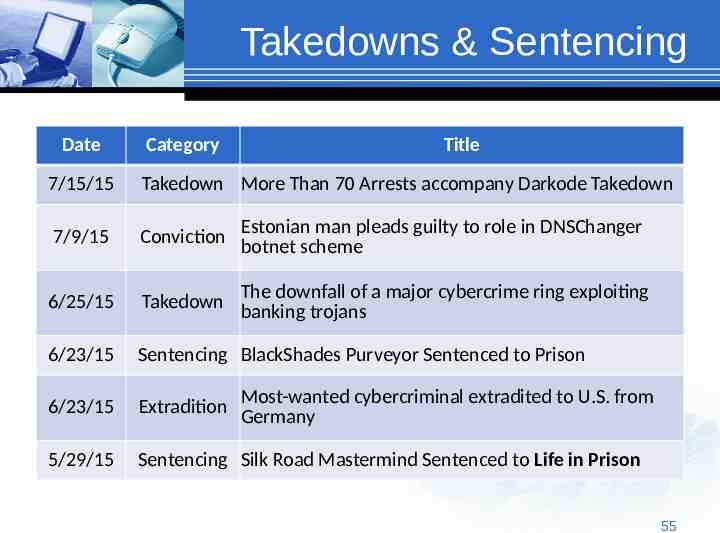
Takedowns & Sentencing Date Category Title 7/15/15 Takedown More Than 70 Arrests accompany Darkode Takedown 7/9/15 Conviction Estonian man pleads guilty to role in DNSChanger botnet scheme 6/25/15 downfall of a major cybercrime ring exploiting Takedown The banking trojans 6/23/15 Sentencing BlackShades Purveyor Sentenced to Prison 6/23/15 Extradition Most-wanted cybercriminal extradited to U.S. from Germany 5/29/15 Sentencing Silk Road Mastermind Sentenced to Life in Prison 55
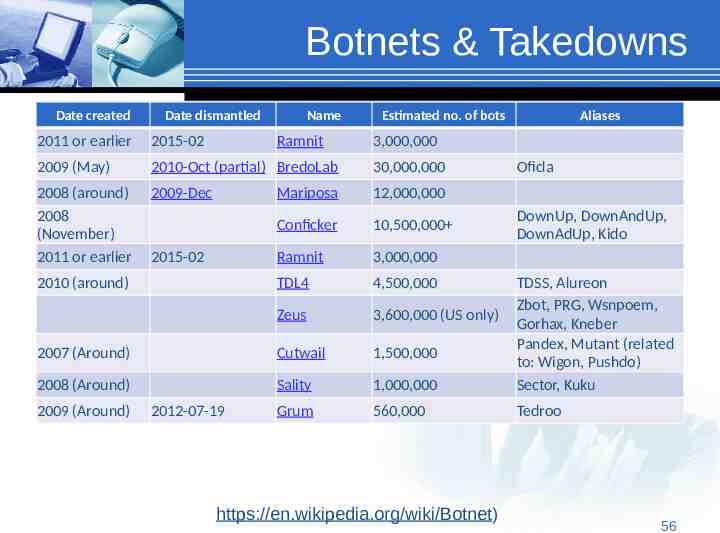
Botnets & Takedowns Date created Date dismantled Name Ramnit Estimated no. of bots Aliases 2011 or earlier 2015-02 2009 (May) 2010-Oct (partial) BredoLab 30,000,000 2008 (around) 2008 (November) 2011 or earlier 2009-Dec Mariposa 12,000,000 Conficker 10,500,000 Ramnit 3,000,000 TDL4 4,500,000 Zeus 3,600,000 (US only) 2007 (Around) Cutwail 1,500,000 2008 (Around) Sality 1,000,000 TDSS, Alureon Zbot, PRG, Wsnpoem, Gorhax, Kneber Pandex, Mutant (related to: Wigon, Pushdo) Sector, Kuku Grum 560,000 Tedroo 2015-02 2010 (around) 2009 (Around) 2012-07-19 3,000,000 https://en.wikipedia.org/wiki/Botnet) Oficla DownUp, DownAndUp, DownAdUp, Kido 56
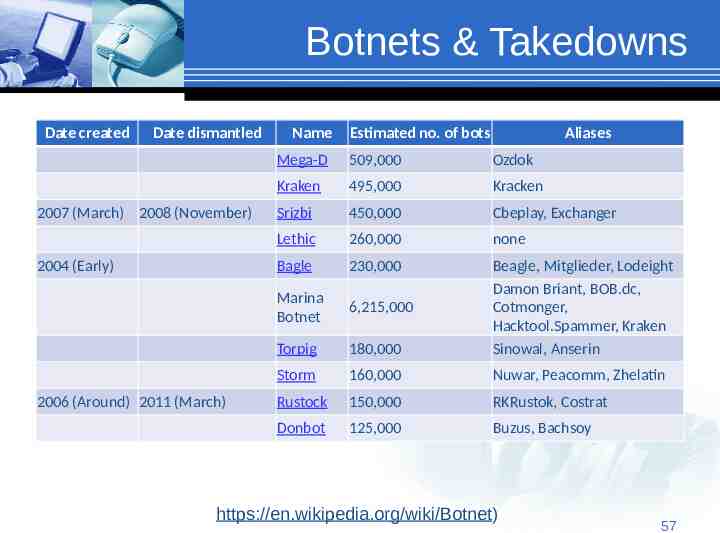
Botnets & Takedowns Date created Date dismantled 2007 (March) 2008 (November) 2004 (Early) 2006 (Around) 2011 (March) Name Estimated no. of bots Aliases Mega-D 509,000 Ozdok Kraken 495,000 Kracken Srizbi 450,000 Cbeplay, Exchanger Lethic 260,000 none Bagle 230,000 Marina Botnet 6,215,000 Torpig 180,000 Beagle, Mitglieder, Lodeight Damon Briant, BOB.dc, Cotmonger, Hacktool.Spammer, Kraken Sinowal, Anserin Storm 160,000 Nuwar, Peacomm, Zhelatin Rustock 150,000 RKRustok, Costrat Donbot 125,000 Buzus, Bachsoy https://en.wikipedia.org/wiki/Botnet) 57
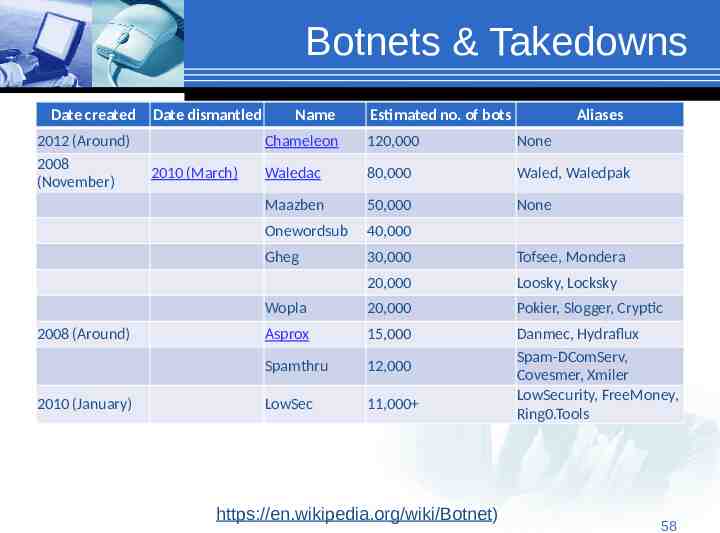
Botnets & Takedowns Date created 2012 (Around) 2008 (November) 2008 (Around) 2010 (January) Date dismantled 2010 (March) Name Estimated no. of bots Aliases Chameleon 120,000 None Waledac 80,000 Waled, Waledpak Maazben 50,000 None Onewordsub 40,000 Gheg 30,000 Tofsee, Mondera 20,000 Loosky, Locksky Wopla 20,000 Pokier, Slogger, Cryptic Asprox 15,000 Spamthru 12,000 LowSec 11,000 Danmec, Hydraflux Spam-DComServ, Covesmer, Xmiler LowSecurity, FreeMoney, Ring0.Tools https://en.wikipedia.org/wiki/Botnet) 58
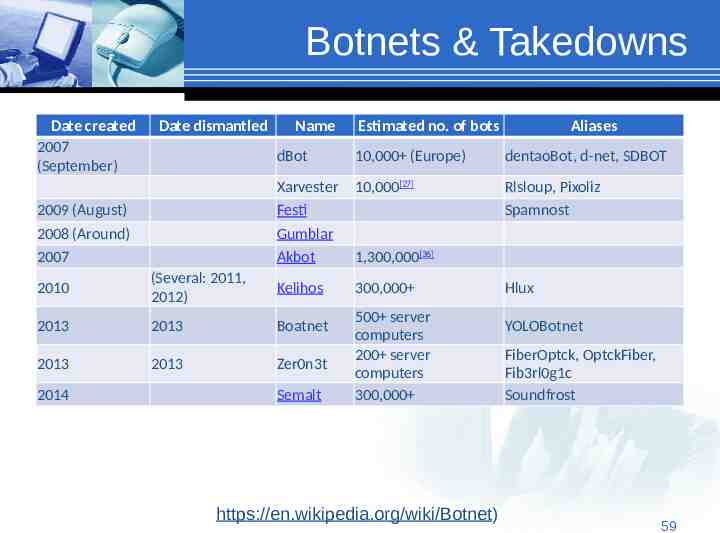
Botnets & Takedowns Date created 2007 (September) Date dismantled 2009 (August) 2008 (Around) 2007 Name Aliases dBot 10,000 (Europe) dentaoBot, d-net, SDBOT Xarvester Festi Gumblar Akbot 10,000[27] Rlsloup, Pixoliz Spamnost 300,000 2010 (Several: 2011, 2012) Kelihos 2013 2013 Boatnet 2013 2013 Zer0n3t 2014 Estimated no. of bots Semalt 1,300,000[36] 500 server computers 200 server computers 300,000 https://en.wikipedia.org/wiki/Botnet) Hlux YOLOBotnet FiberOptck, OptckFiber, Fib3rl0g1c Soundfrost 59

Trends & Predictions - Future Company LOGO 60

Point of Sale (POS) Point of Sale devices are essentially endpoints with virtually no embedded security. Most run Windows XP and outdated Antivirus software. They were sitting ducks for targeted malware likely developed by hacker groups in the former Soviet Union. While there isn’t an immediate silver bullet, these threats will slowly be mitigated and phased out over time. 61

Ransomware These attacks are very lucrative. Since higher infection rates mean more income -- attackers invested in and bolted-on very sophisticated evasion techniques to their core payloads. The advent of bitcoin has transformed ransomware into a stealthy money making machine anyone can use. This trend is here to stay - since there are no effective security measures against it today. 62

Targeted, Advanced Evasion Both Nation States and cyber criminals developed attacks that only execute on a specific machine or set up. Since they behave like a benign application on the way to the target machine these threats are able to evade layers of detection mechanisms. 63

Government Code Went Mainstream Government grade malware has been developed for espionage (Gyges) and is being bolted onto ransomware and financial Trojans. This code enables any type of malware to operate in stealth mode and be completely invisible to all security measures. 64
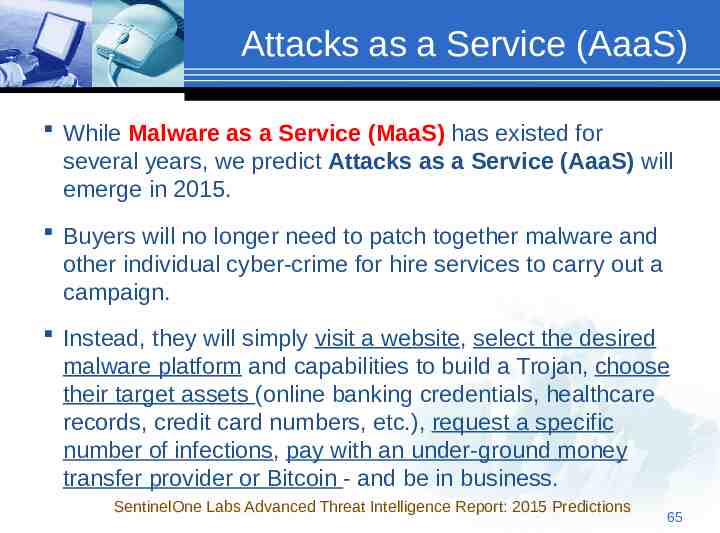
Attacks as a Service (AaaS) While Malware as a Service (MaaS) has existed for several years, we predict Attacks as a Service (AaaS) will emerge in 2015. Buyers will no longer need to patch together malware and other individual cyber-crime for hire services to carry out a campaign. Instead, they will simply visit a website, select the desired malware platform and capabilities to build a Trojan, choose their target assets (online banking credentials, healthcare records, credit card numbers, etc.), request a specific number of infections, pay with an under-ground money transfer provider or Bitcoin - and be in business. SentinelOne Labs Advanced Threat Intelligence Report: 2015 Predictions 65

Enterprise Hostageware The runaway success of ransomware campaigns will emboldened attackers to devise new and even more lucrative attacks. Ransomware will be used to coordinate a “time bomb” attack on an enterprise. By simultaneously holding hostage multiple resources within an organization, an attacker could temporarily halt operations. The devastating effects of such an attack on a small enterprise, would force most companies to pay a high price for the release of their systems. One successful attack of this nature will produce many more copycat incidents. SentinelOne Labs Advanced Threat Intelligence Report: 2015 Predictions 66

Critical Infrastructure Shut Downs There have been a few “first spark” attacks on critical infrastructure, including some that shut down power grids for short periods of time (but were not were never publicly disclosed). The dangerous combination of old, unmaintained technologies and a large attack surface make critical infrastructure especially vulnerable to attacks. Nation States are building weaponized capabilities to remotely take control of an adversary’s SCADA and other critical infrastructure operational systems. It is predicted that cyber inflicted power outages and irregularities in assembly operations at large manufacturing facilities will result from attacks on SCADA and ICS systems. SentinelOne Labs Advanced Threat Intelligence Report: 2015 Predictions 67

New Nation State Threats Predict that Russia will continue to use cyber-attacks as a political retaliation tool, as it is believed they did in the Home Depot POS attack and numerous attacks on US-based financial institutions. Expect China to continue to carry out brute force cyber-attacks and espionage campaigns, primarily against the US, Japan, other APAC countries and human rights activists. Even though their methods are not very stealth and often traceable, law enforcement agencies and governments will not be able to do very much to mitigate Chinese attacks. Primarily because of entangled diplomacy efforts and lack of accountability inside the Chinese regime. It is believed that Pakistan, will expand its activities, mostly against India, by outsourcing malware creation and using contractors to build out attacks. SentinelOne Labs Advanced Threat Intelligence Report: 2015 Predictions 68

OS X, Linux in the Cross Hairs Until now, these two platforms have been relatively “neglected” by attackers. We predict this is about to change. The massive adoption of Linux in enterprise datacenters and the recent uptick in revived variants of Linux malware (i.e. “cdorked”) all indicate that this OS will be targeted. We view the “cdorked” attacks as a proof of concept designed to test the resilience of Linux and the security products used to defend it. As for Mac OS X, it has experienced a long and slow rise in malware attacks -- if we exclude the enormous “Flashback” campaign a few years ago. However, the recent emergence of zero-day vulnerabilities combined with the platform’s increasing enterprise market share, especially among executives, leads us to believe this will change. The biggest cause for concern is that because these platforms are generally considered “safe”, there are very few security products available to protect them from advanced attacks. SentinelOne Labs Advanced Threat Intelligence Report: 2015 Predictions 69

Amazon Amazon is a Hornet’s Nest of Malware (1/16/14)* Of the 10 sites that pump out malware most frequently, four are hosted on Amazon Web Services (AWS) — including the number one site, download-instantly.com, according to a threat report published Wednesday by the IT security firm Solutionary. The report comes a week after we learned that hackers allegedly used Amazon's cloud hosting solution as a platform for a botnet that scraped personal information from potentially millions of LinkedIn subscribers. AWS was found to be hosting SpyEye, a trojan that let hackers gain access to the online accounts of banking customers. Amazon Vulnerability Reporting web page https://aws.amazon.com/security/vulnerability-reporting/ *https://www.washingtonpost.com/blogs/the-switch/wp/2014/01/16/amazon-is-a-h ornets-nest-of-malware 70

Malware Trends Malware is becoming increasingly aggressive and evasive Two-factor authentication is vulnerable Targeted attacks will give way to mass exploit customization More consumer and enterprise data leaks via cloud apps Your refrigerator is running exploits http://www.tripwire.com/state-of-security/security-data-protection/cyber-security /top-5-malware-trends-on-the-horizon/ 71

Threats and Countermeasures STRIDE Network Threats Host Threats Company LOGO 72
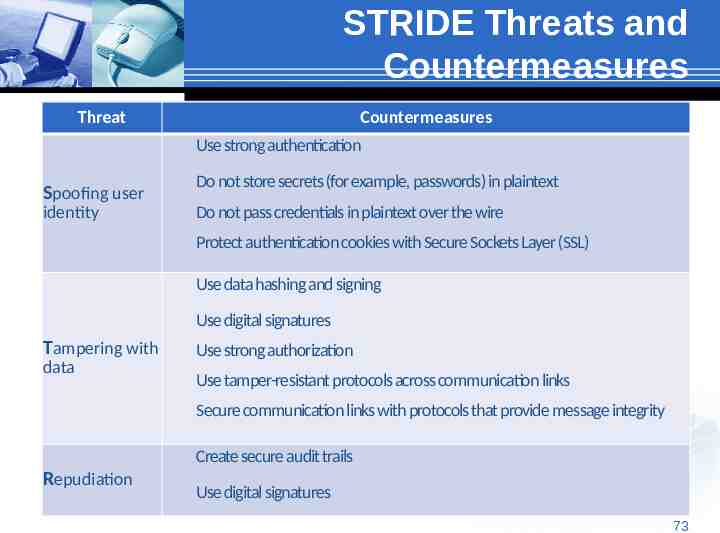
STRIDE Threats and Countermeasures Threat Countermeasures Use strong authentication Spoofing user identity Do not store secrets (for example, passwords) in plaintext Do not pass credentials in plaintext over the wire Protect authentication cookies with Secure Sockets Layer (SSL) Use data hashing and signing Use digital signatures Tampering with Use strong authorization data Use tamper-resistant protocols across communication links Secure communication links with protocols that provide message integrity Create secure audit trails Repudiation Use digital signatures 73
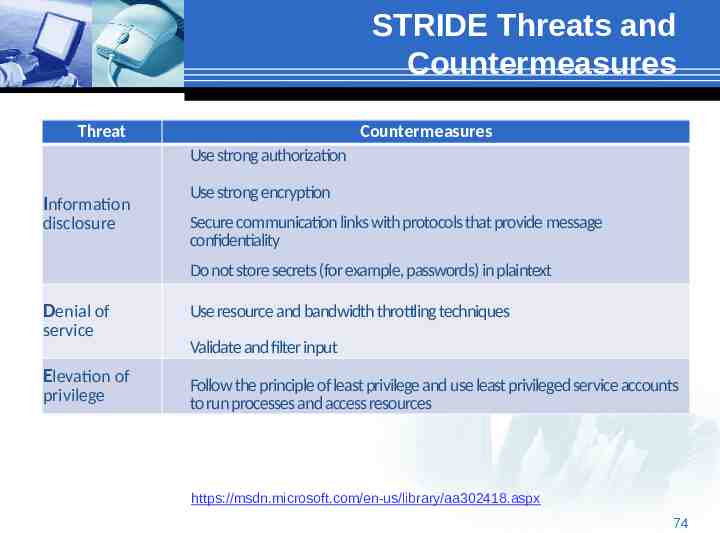
STRIDE Threats and Countermeasures Threat Countermeasures Use strong authorization Information disclosure Use strong encryption Secure communication links with protocols that provide message confidentiality Do not store secrets (for example, passwords) in plaintext Denial of service Elevation of privilege Use resource and bandwidth throttling techniques Validate and filter input Follow the principle of least privilege and use least privileged service accounts to run processes and access resources https://msdn.microsoft.com/en-us/library/aa302418.aspx 74
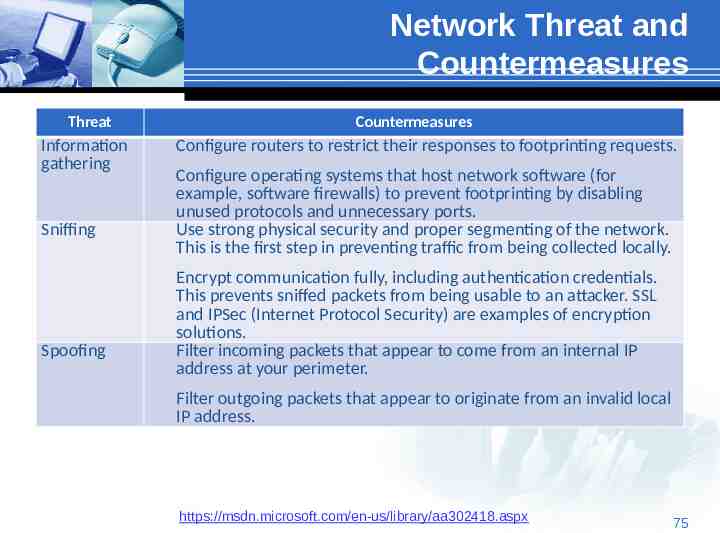
Network Threat and Countermeasures Threat Information gathering Sniffing Spoofing Countermeasures Configure routers to restrict their responses to footprinting requests. Configure operating systems that host network software (for example, software firewalls) to prevent footprinting by disabling unused protocols and unnecessary ports. Use strong physical security and proper segmenting of the network. This is the first step in preventing traffic from being collected locally. Encrypt communication fully, including authentication credentials. This prevents sniffed packets from being usable to an attacker. SSL and IPSec (Internet Protocol Security) are examples of encryption solutions. Filter incoming packets that appear to come from an internal IP address at your perimeter. Filter outgoing packets that appear to originate from an invalid local IP address. https://msdn.microsoft.com/en-us/library/aa302418.aspx 75

Network Threat and Countermeasures Threat Session Hijacking Denial of Service Countermeasures Use encrypted session negotiation. Use encrypted communication channels. Stay informed of platform patches to fix TCP/IP vulnerabilities, such as predictable packet sequences. Apply the latest service packs. Harden the TCP/IP stack by applying the appropriate registry settings to increase the size of the TCP connection queue, decrease the connection establishment period, and employ dynamic backlog mechanisms to ensure that the connection queue is never exhausted. Use a network Intrusion Detection System (IDS) because these can automatically detect and respond to SYN attacks. https://msdn.microsoft.com/en-us/library/aa302418.aspx 76

Host Threats and Countermeasures Threats Countermeasures Viruses, Trojan Stay current with the latest operating system service packs and horses, and software patches. worms Block all unnecessary ports at the firewall and host. Disable unused functionality including protocols and services. Footprinting Harden weak, default configuration settings. Disable unnecessary protocols. Lock down ports with the appropriate firewall configuration. Use TCP/IP and IPSec filters for defense in depth. Configure IIS to prevent information disclosure through banner grabbing. Use an IDS that can be configured to pick up footprinting patterns and reject suspicious traffic. https://msdn.microsoft.com/en-us/library/aa302418.aspx 77

Host Threats and Countermeasures Threats Password Cracking Countermeasures Use strong passwords for all account types Apply lockout policies to end-user accounts to limit the number of retry attempts that can be used to guess the password Do not use default account names, and rename standard accounts such as the administrator's account and the anonymous Internet user account used by many Web applications Audit failed logins for patterns of password hacking attempts Arbitrary code Configure IIS to reject URLs with "./" to prevent path traversal execution Lock down system commands and utilities with restricted ACLs Stay current with patches and updates to ensure that newly discovered buffer overflows are speedily patched https://msdn.microsoft.com/en-us/library/aa302418.aspx 78

Host Threats and Countermeasures Threats Denial of Service Countermeasures Configure your applications, services, and operating system with denial of service in mind Stay current with patches and security updates Harden the TCP/IP stack against denial of service Make sure your account lockout policies cannot be exploited to lock out well known service accounts Make sure your application is capable of handling high volumes of traffic and that thresholds are in place to handle abnormally high loads Review your application's failover functionality Use an IDS that can detect potential denial of service attacks https://msdn.microsoft.com/en-us/library/aa302418.aspx 79

Future? Malware as a Service (MaaS) Company LOGO 80
Professional DDOS Services From Arbor Networks 8181
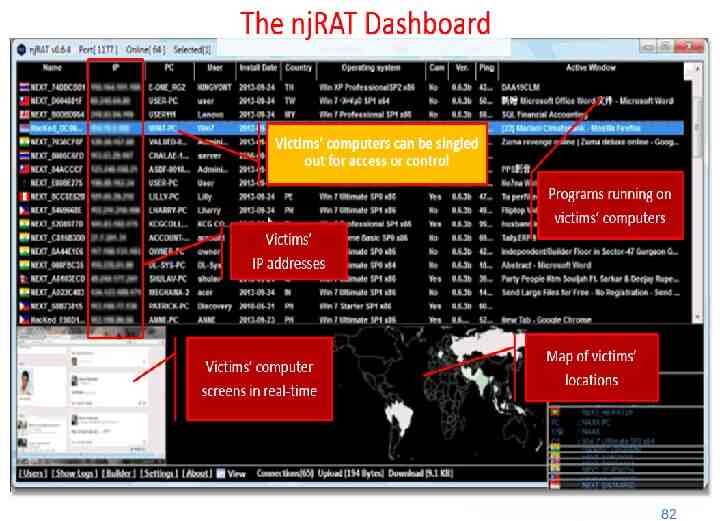
82
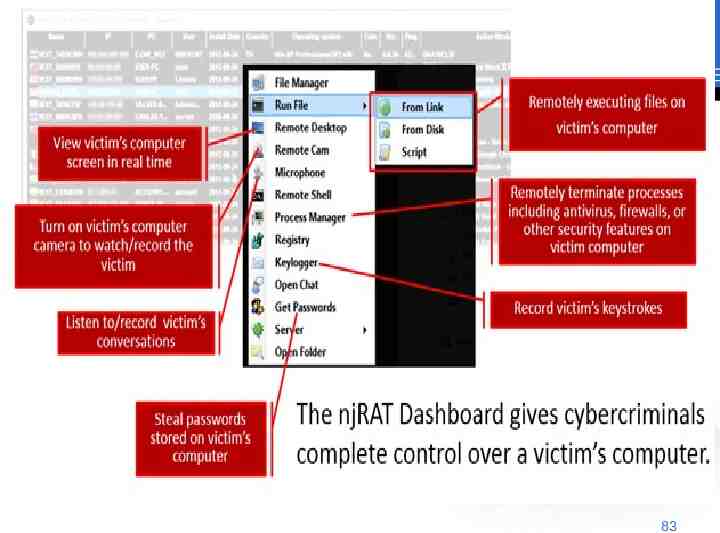
83
Malware”R”Us.com Malware Selection Menu: O/S: Windows, UNIX, Linux, Apple, etc. O/S Version(s) – xx.x Target Device(s): Firewall, Gateway, Router, Server, Desktop, Laptop, Tablet, PDA, IoT, etc. Browser (IE, Firefox, Safari, etc.) Application (e.g., SaaS, Office Suite, Adobe, WordPress) Select Target(s) by IP, IP Range, Phone Number(s) Type of Malware(s): Virus, Worm, Trojan Horse, DDoS, C&C, Botnet, Macro, Keylogger, Spam, Spyware, Rootkit, Adware, etc. For Custom Work contact 800 number 84
Questions 85






