Network Security: Firewalls MIS 5973 – Infrastructures Summer 2002
14 Slides646.50 KB

Network Security: Firewalls MIS 5973 – Infrastructures Summer 2002 – Kelly S. Nix
The only safe computer is a dead computer.

The Threats Denial-of-Service Unauthorized Access Execution of Unauthorized Commands Breaches of Confidentiality Destructive Behavior

Who Are These Guys? activists club initiates competitors consultants crackers for hire crackers customers cyber-gangs deranged people drug cartels economic rivals extortionists foreign agents and spies Fraudsters global coalitions government agencies hackers hoodlums Industrial espionage experts information warriors infrastructure warriors insiders maintenance people military organizations nation states nature organized crime paramilitary groups police private investigators professional thieves reporters terrorists tiger teams vandals vendors whistle blowers

Basic Security Backup, Backup, Backup Control Where Data Is Located Decentralize Your Security System Your Operating System May Not Be Your Friend

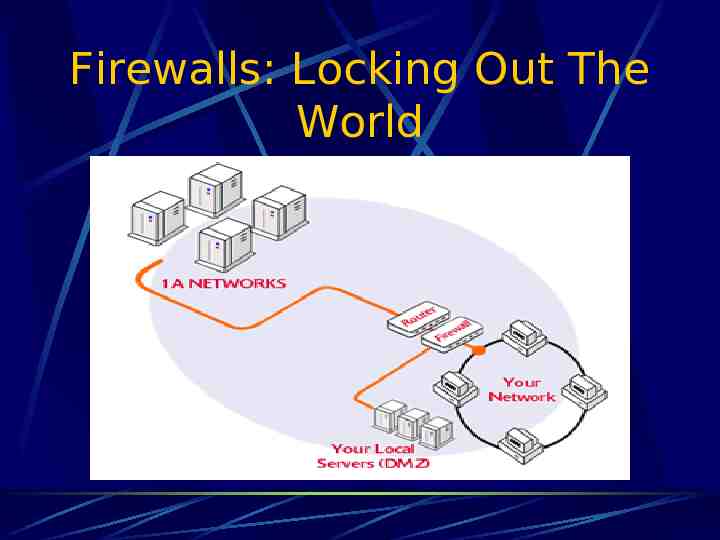
Firewalls: Locking Out The World

Firewall Terminology Bastion Host Router Access Control List (ACL) Demilitarized Zone (DMZ) Proxy Stateful Inspection Network Address Translation (NAT)
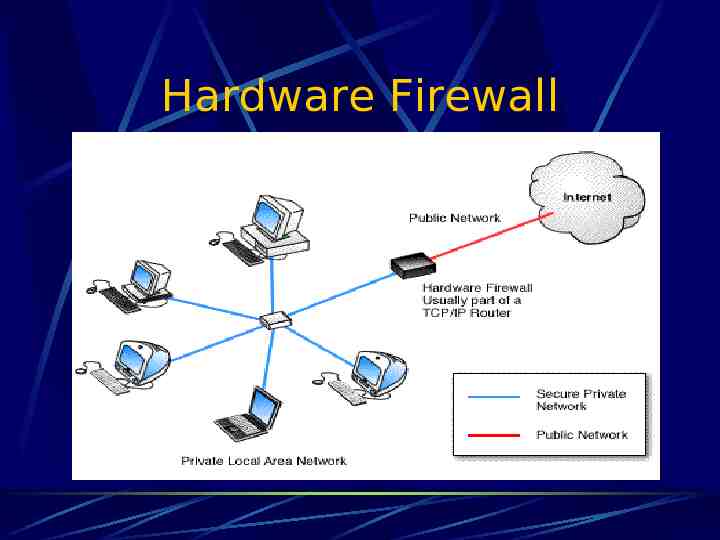
Hardware Firewall

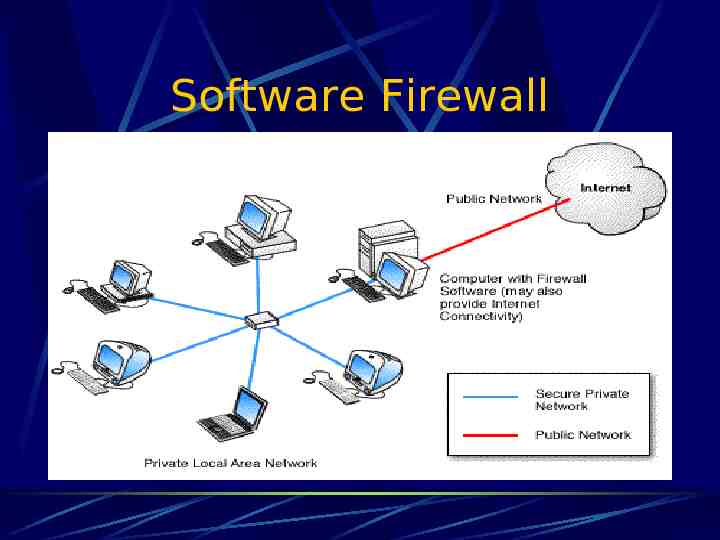
Software Firewall
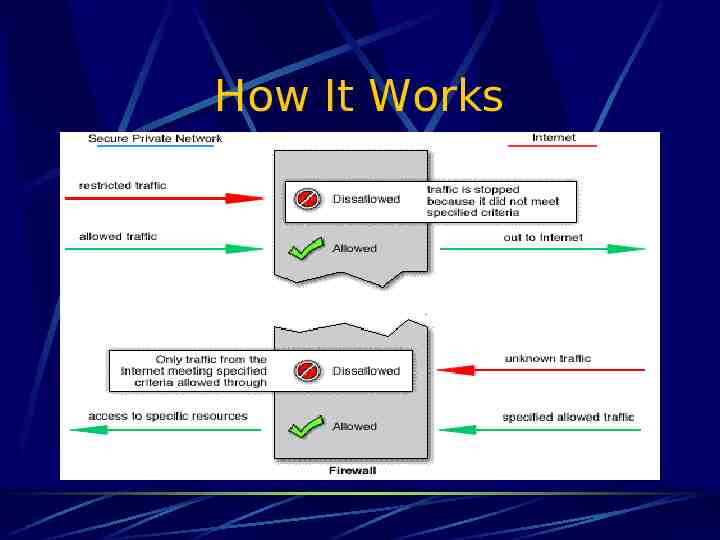
How It Works
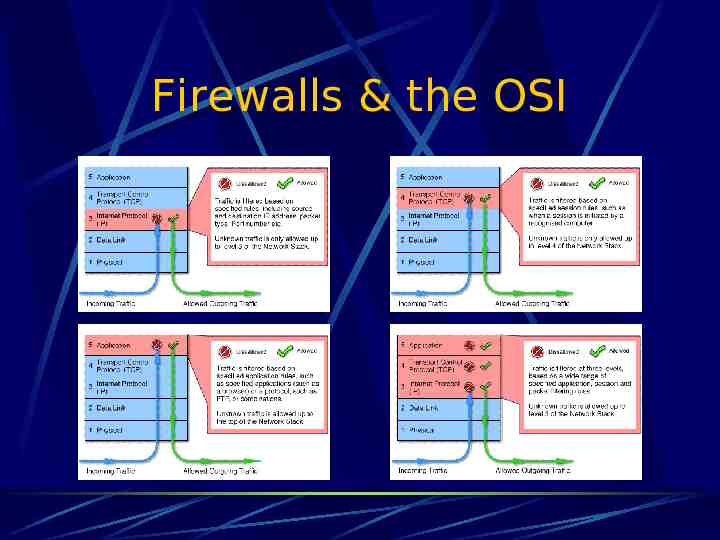
Firewalls & the OSI