Mobile Edge Security Third Party App Edge Cloud Police/ EMS
9 Slides9.55 MB
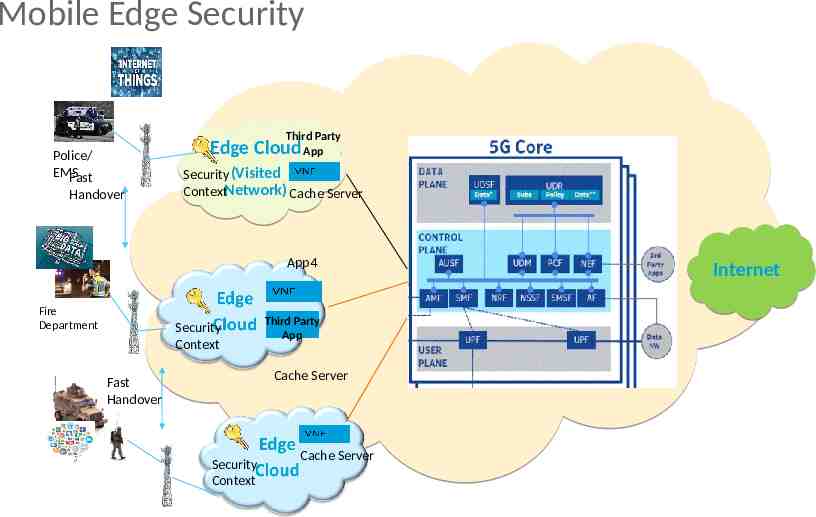
Mobile Edge Security Third Party App Edge Cloud Police/ EMS Fast Handover Security (Visited ContextNetwork) Cache Server App4 Fire Department Security Context Third Party App Cache Server Fast Handover Security Context Cache Server Internet
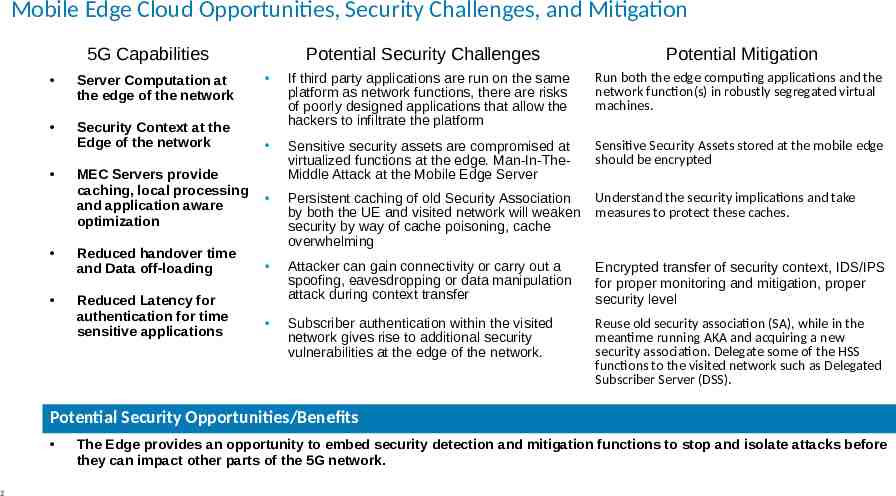
Mobile Edge Cloud Opportunities, Security Challenges, and Mitigation 5G Capabilities Potential Security Challenges Potential Mitigation If third party applications are run on the same platform as network functions, there are risks of poorly designed applications that allow the hackers to infiltrate the platform Run both the edge computing applications and the network function(s) in robustly segregated virtual machines. MEC Servers provide caching, local processing and application aware optimization Sensitive security assets are compromised at virtualized functions at the edge. Man-In-TheMiddle Attack at the Mobile Edge Server Sensitive Security Assets stored at the mobile edge should be encrypted Understand the security implications and take measures to protect these caches. Reduced handover time and Data off-loading Persistent caching of old Security Association by both the UE and visited network will weaken security by way of cache poisoning, cache overwhelming Reduced Latency for authentication for time sensitive applications Attacker can gain connectivity or carry out a spoofing, eavesdropping or data manipulation attack during context transfer Encrypted transfer of security context, IDS/IPS for proper monitoring and mitigation, proper security level Subscriber authentication within the visited network gives rise to additional security vulnerabilities at the edge of the network. Reuse old security association (SA), while in the meantime running AKA and acquiring a new security association. Delegate some of the HSS functions to the visited network such as Delegated Subscriber Server (DSS). Server Computation at the edge of the network Security Context at the Edge of the network Potential Security Opportunities/Benefits 2 The Edge provides an opportunity to embed security detection and mitigation functions to stop and isolate attacks before they can impact other parts of the 5G network.
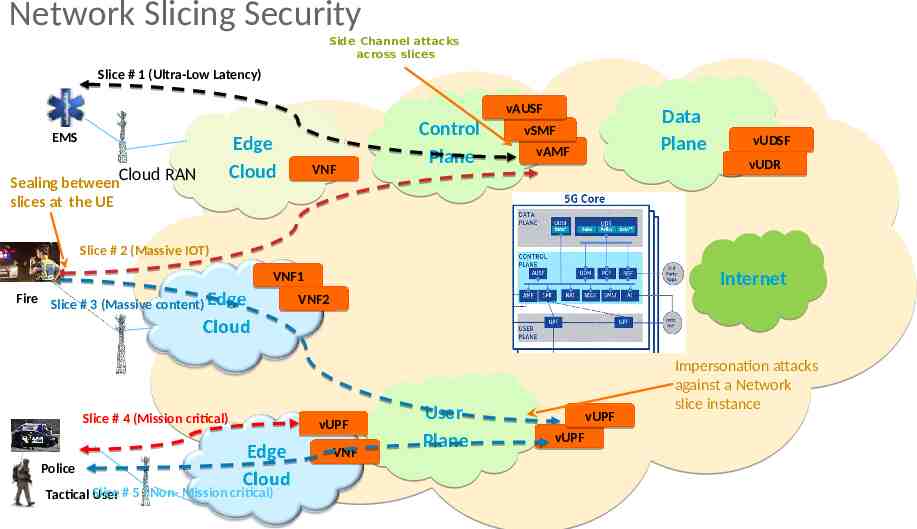
Network Slicing Security Side Channel attacks across slices Slice # 1 (Ultra-Low Latency) EMS Sealing betweenCloud RAN Edge Cloud VNF Control Plane vAUSF vSMF Data Plane vAMF vUDSF vUDR slices at the UE Slice # 2 (Massive IOT) Internet VNF1 Fire Slice # 3 (Massive content) Slice # 4 (Mission critical) VNF2 vUPF VNF Police Slice # 5 ( Non- Mission critical) Tactical User User Plane vUPF vUPF Impersonation attacks against a Network slice instance
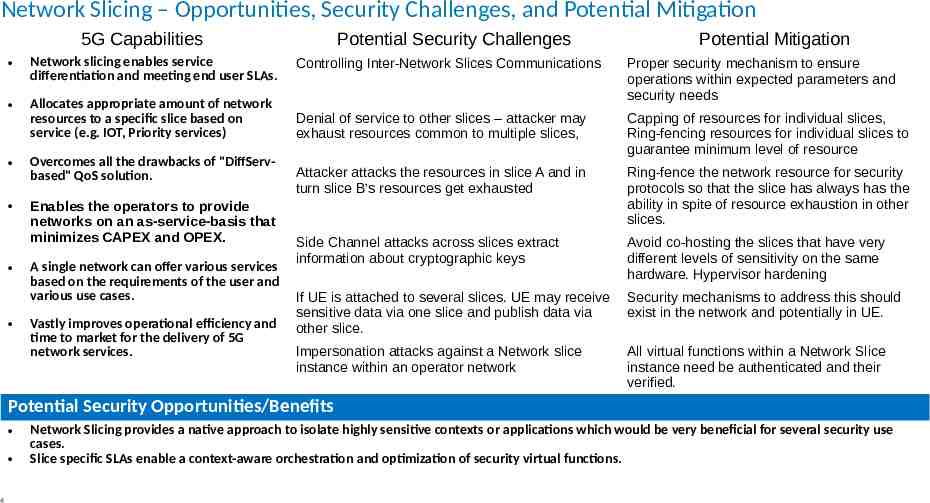
Network Slicing – Opportunities, Security Challenges, and Potential Mitigation 5G Capabilities Potential Security Challenges Potential Mitigation Network slicing enables service differentiation and meeting end user SLAs. Controlling Inter-Network Slices Communications Allocates appropriate amount of network resources to a specific slice based on service (e.g. IOT, Priority services) Proper security mechanism to ensure operations within expected parameters and security needs Denial of service to other slices – attacker may exhaust resources common to multiple slices, Overcomes all the drawbacks of "DiffServbased" QoS solution. Capping of resources for individual slices, Ring-fencing resources for individual slices to guarantee minimum level of resource Attacker attacks the resources in slice A and in turn slice B’s resources get exhausted Enables the operators to provide networks on an as-service-basis that minimizes CAPEX and OPEX. Ring-fence the network resource for security protocols so that the slice has always has the ability in spite of resource exhaustion in other slices. Side Channel attacks across slices extract information about cryptographic keys Avoid co-hosting the slices that have very different levels of sensitivity on the same hardware. Hypervisor hardening If UE is attached to several slices. UE may receive sensitive data via one slice and publish data via other slice. Security mechanisms to address this should exist in the network and potentially in UE. Impersonation attacks against a Network slice instance within an operator network All virtual functions within a Network Slice instance need be authenticated and their verified. A single network can offer various services based on the requirements of the user and various use cases. Vastly improves operational efficiency and time to market for the delivery of 5G network services. Potential Security Opportunities/Benefits 4 Network Slicing provides a native approach to isolate highly sensitive contexts or applications which would be very beneficial for several security use cases. Slice specific SLAs enable a context-aware orchestration and optimization of security virtual functions.
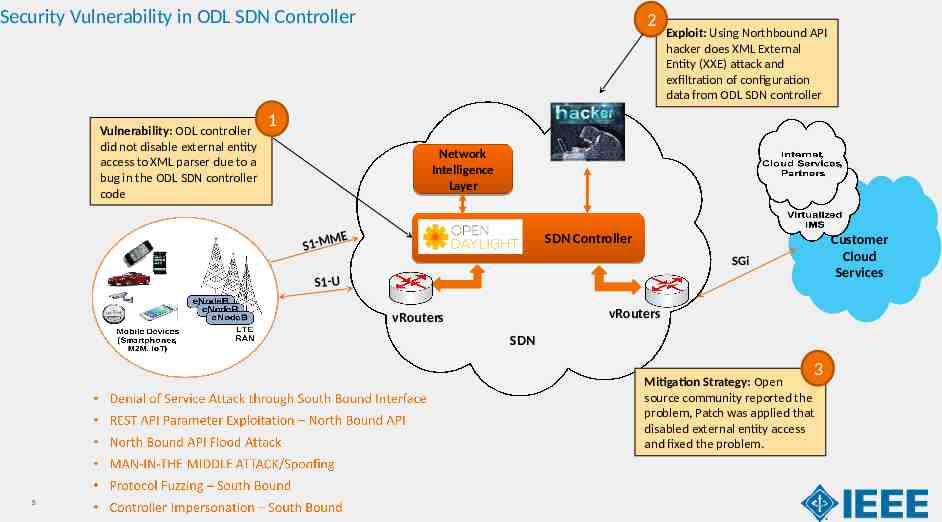
Security Vulnerability in ODL SDN Controller Vulnerability: ODL controller did not disable external entity access to XML parser due to a bug in the ODL SDN controller code 2 Exploit: Using Northbound API hacker does XML External Entity (XXE) attack and exfiltration of configuration data from ODL SDN controller 1 Network Intelligence Layer ME S1-M SDN Controller Customer Cloud Services SGi S1-U vRouters vRouters SDN 3 Mitigation Strategy: Open source community reported the problem, Patch was applied that disabled external entity access and fixed the problem. 5
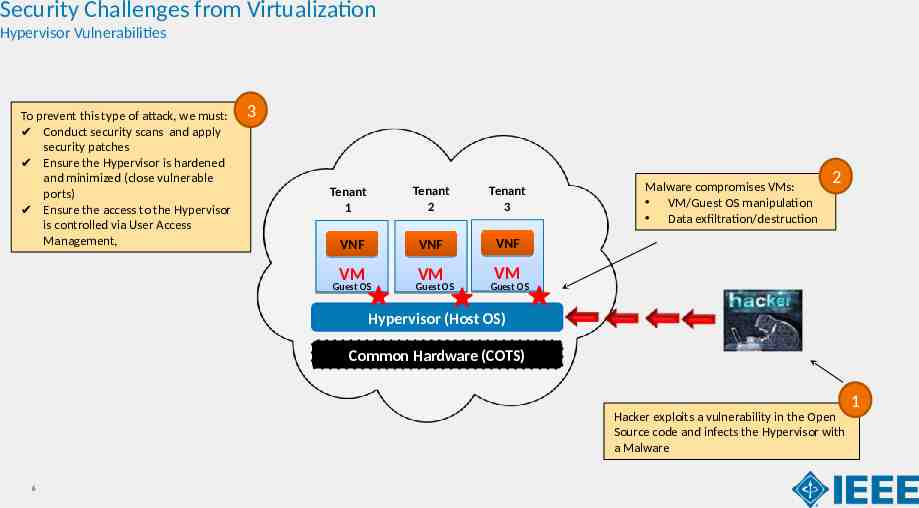
Security Challenges from Virtualization Hypervisor Vulnerabilities To prevent this type of attack, we must: Conduct security scans and apply security patches Ensure the Hypervisor is hardened and minimized (close vulnerable ports) Ensure the access to the Hypervisor is controlled via User Access Management, 3 Tenant 1 Tenant 2 Tenant 3 VNF VNF VNF VM Guest OS VM Guest OS Malware compromises VMs: VM/Guest OS manipulation Data exfiltration/destruction 2 VM Guest OS Hypervisor (Host OS) Common Hardware (COTS) Hacker exploits a vulnerability in the Open Source code and infects the Hypervisor with a Malware 6 1
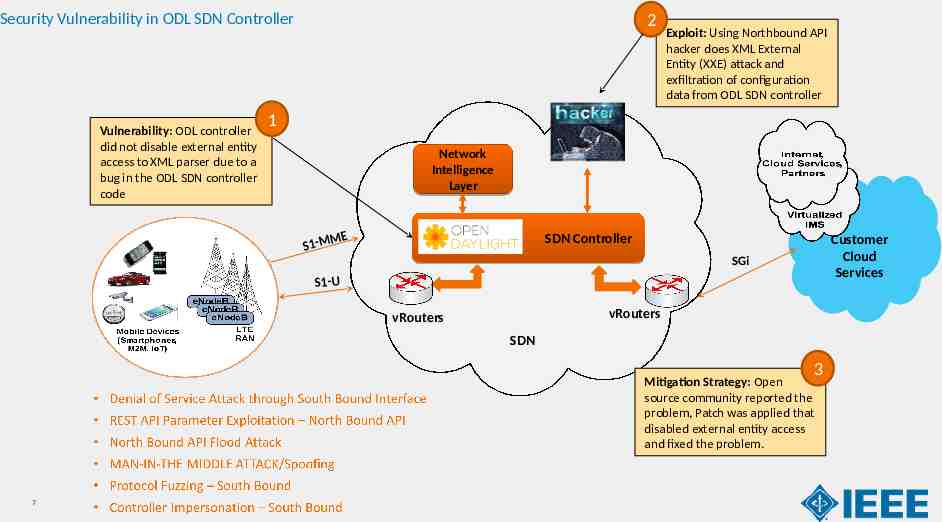
Security Vulnerability in ODL SDN Controller Vulnerability: ODL controller did not disable external entity access to XML parser due to a bug in the ODL SDN controller code 2 Exploit: Using Northbound API hacker does XML External Entity (XXE) attack and exfiltration of configuration data from ODL SDN controller 1 Network Intelligence Layer ME S1-M SDN Controller Customer Cloud Services SGi S1-U vRouters vRouters SDN 3 Mitigation Strategy: Open source community reported the problem, Patch was applied that disabled external entity access and fixed the problem. 7
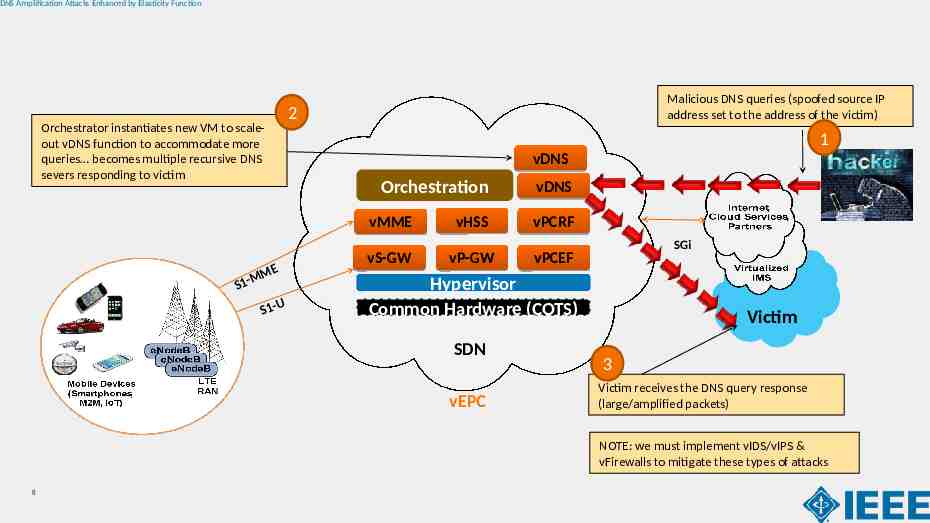
DNS Amplification Attacks Enhanced by Elasticity Function Orchestrator instantiates new VM to scaleout vDNS function to accommodate more queries becomes multiple recursive DNS severs responding to victim Malicious DNS queries (spoofed source IP address set to the address of the victim) 2 1 vDNS Orchestration vDNS vHSS vPCRF vMME S ME M 1 S1-U vS-GW vP-GW SGi vPCEF Hypervisor Common Hardware (COTS) SDN vEPC Victim 3 Victim receives the DNS query response (large/amplified packets) NOTE: we must implement vIDS/vIPS & vFirewalls to mitigate these types of attacks 8
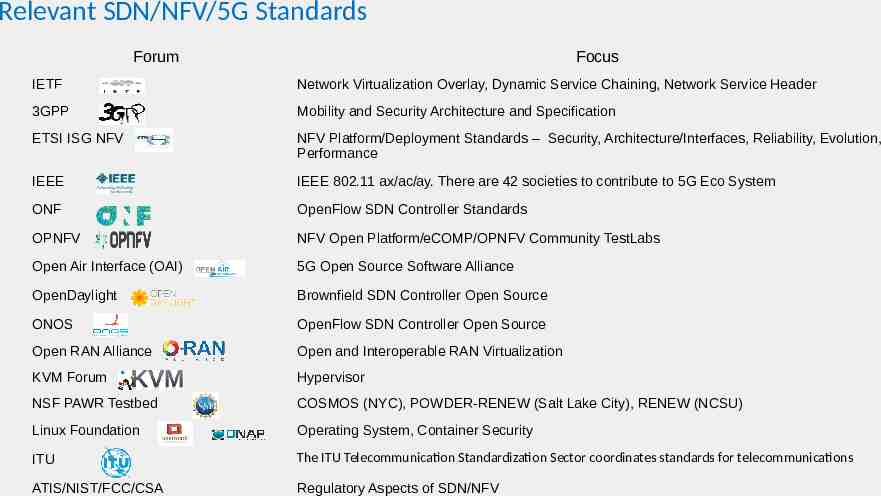
Relevant SDN/NFV/5G Standards Forum Focus IETF Network Virtualization Overlay, Dynamic Service Chaining, Network Service Header 3GPP Mobility and Security Architecture and Specification ETSI ISG NFV NFV Platform/Deployment Standards – Security, Architecture/Interfaces, Reliability, Evolution, Performance IEEE IEEE 802.11 ax/ac/ay. There are 42 societies to contribute to 5G Eco System ONF OpenFlow SDN Controller Standards OPNFV NFV Open Platform/eCOMP/OPNFV Community TestLabs Open Air Interface (OAI) 5G Open Source Software Alliance OpenDaylight Brownfield SDN Controller Open Source ONOS OpenFlow SDN Controller Open Source Open RAN Alliance Open and Interoperable RAN Virtualization KVM Forum Hypervisor NSF PAWR Testbed COSMOS (NYC), POWDER-RENEW (Salt Lake City), RENEW (NCSU) Linux Foundation Operating System, Container Security ITU The ITU Telecommunication Standardization Sector coordinates standards for telecommunications ATIS/NIST/FCC/CSA Regulatory Aspects of SDN/NFV






