The Bytes Stop Here: Duty and Liability for Negligent Security Erin
55 Slides5.72 MB

The Bytes Stop Here: Duty and Liability for Negligent Security Erin E. Kenneally San Diego Supercomputer Center University of California San Diego [email protected]
1 (C) 2000-2004 Kenneally
1 (C) 2000-2004 Kenneally
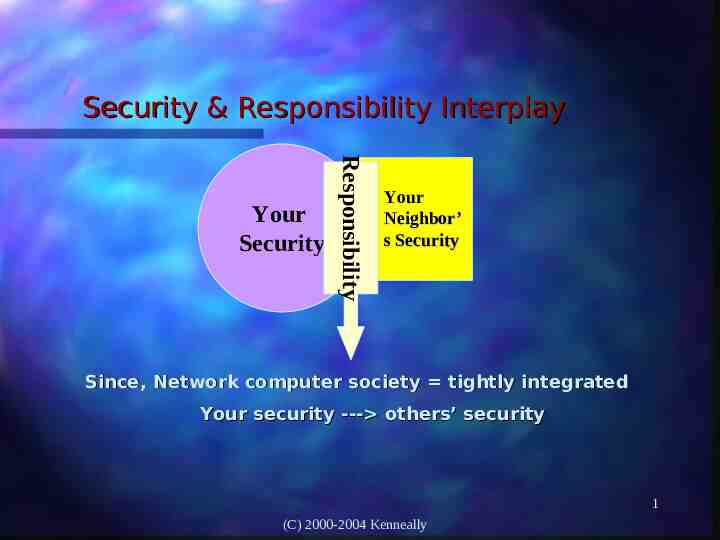
Security & Responsibility Interplay Responsibility Your Security Your Neighbor’ s Security Since, Network computer society tightly integrated Your security --- others’ security 1 (C) 2000-2004 Kenneally

OVERVIEW Why should there be a Duty to Secure Computer Systems? Technical ; Legal forces What does it mean to have a Duty to Secure Computer Systems? Enter Negligence Liability Basis for imposing a Duty to Secure Knowledge Ability to Control Assumption of Duty Socioeconomic Policies 1 (C) 2000-2004 Kenneally
(OVERVIEW) Who does the Duty apply to? What is the scope of the Duty? Software Vendor (SWV)? Internet Service Provider (ISP)? Web Co.? Individual User? Liability Defenses 1 (C) 2000-2004 Kenneally

The Fine Line: Are you a Victimsymptom or Liable -cause? Take this test: test 1st: draw lines connecting the consequence to every possible cause 2nd: connect each cause to every actor that may affect the cause 3rd: determine which category of actor you qualify 4th: trace back-up the chart 5th: Analysis - unable to link actor to event - able to trace actor to damaging event 1 (C) 2000-2004 Kenneally
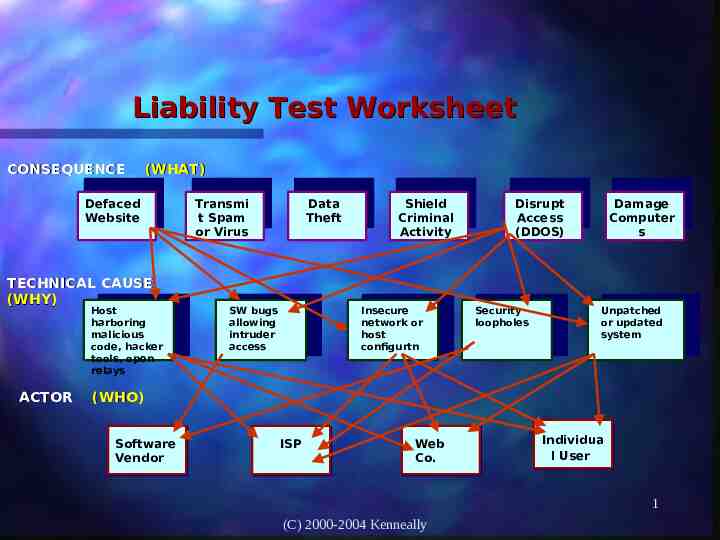
Liability Test Worksheet CONSEQUENCE (WHAT) Defaced Website TECHNICAL CAUSE (WHY) Host harboring malicious code, hacker tools, open relays ACTOR Data Theft Transmi t Spam or Virus SW bugs allowing intruder access Shield Criminal Activity Insecure network or host configurtn Disrupt Access (DDOS) Security loopholes Damage Computer s Unpatched or updated system (WHO) Software Vendor ISP Web Co. Individua l User 1 (C) 2000-2004 Kenneally

Why should there be a Duty to Secure Computer Systems? Technical environment Information processing, storage, and security are different in computer networked society Physical society: V. Internet society: Standards emerging 1 (C) 2000-2004 Kenneally

(Technical environment, con’t) So, what? Social ramifications demand responsibilities Every other major industry/technology has become important enough to affect people outside its sphere Currently: Complexity Boundary-less unregulated automated *mutable responsibilities *blame-shifting encouraged *human accountability confused with computer errors 1 (C) 2000-2004 Kenneally

Why should there be a Duty to Secure Computer Systems? Legal environment Criminal law purpose: enforce State’s interests – deterrence – punishment victim of computer invasion not compensated – limits: identifying, prosecuting, no reluctance to involve LE 1 (C) 2000-2004 Kenneally

(Legal environment con’t) Contract Law purpose: redress injuries between 2 bargaining parties Imagine: ‘.ACME HEREBY ASSUMES RESPONSIBILITY FOR ANY/ALL DAMAGES THAT MAY RESULT WHEN AN INSECURITY IN ACME’S COMPUTER SYSTEMS RESULTS IN AN UNKNOWN 3RD PARTY USING IT TO CAUSE DAMAGE TO WIDGETS, INC.’ No cover third party liability 1 (C) 2000-2004 Kenneally

(Legal environment con’t) Civil law purpose: encourage socially responsible behavior by addressing disputes between citizens and compensating aggrieved party Benefits: – no need to ID perp – more deep-pockets – prior contract unnecessary 1 (C) 2000-2004 Kenneally

Tort Liability Tort “[A] civil wrong, other than a breach of contract, for which the law provides a remedy.” Prosser Intentional Negligence – Duty – Breach (of standard of care) – Causation – Damages 1 (C) 2000-2004 Kenneally

Torts and Infosec: What does it mean to have a Duty to Secure Computer Systems? Issue should we allow the recovery of damages from a party whose failure to secure his computer system(s) enabled a third party to exact harm If “YES” reasonable care must be used in securing one’s computer(s) for the protection of others against unreasonable risks 1 (C) 2000-2004 Kenneally

(What does it mean to have a Duty to Secure Computer Systems?) Enter Negligence Liability Elements: Victim must show that the “insecure” party: (1) owed a duty to use reasonable care in securing its computer(s); (2) breached duty by failing to implement/maintain adequate security; and (3) was reasonable cause of actual damages that resulted from insecure computer(s) 1 (C) 2000-2004 Kenneally

(What does it mean to have a Duty to Secure Computer Systems?) Legal mumbo-jumbo Duty - general duty to act reasonably so as to not cause harm to others “Reasonable Care”- the attention, knowledge, intelligence and judgement as defined by society for its protection Defined and applied: what technologies available to prevent – industry standards / best practices – market competition pressure and quality of service – insurance prereq’s set standard of care/expectations Statutes (e.g.(C)HIPAA, GLBA, SOX, SB 1386) 2000-2004 Kenneally 1
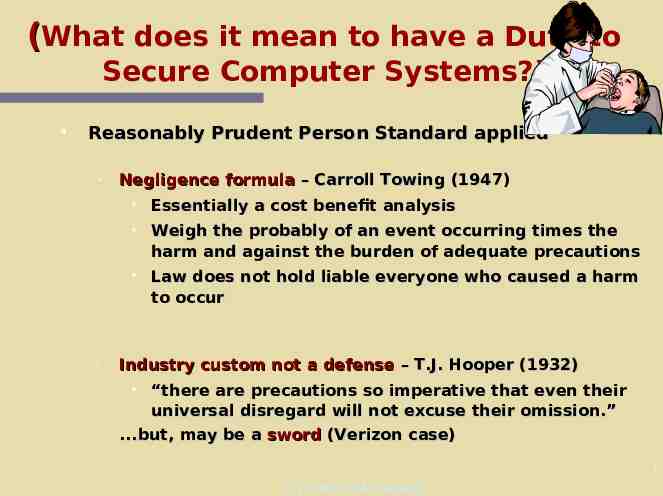
(What does it mean to have a Duty to Secure Computer Systems?) Reasonably Prudent Person Standard applied Negligence formula – Carroll Towing (1947) Essentially a cost benefit analysis Weigh the probably of an event occurring times the harm and against the burden of adequate precautions Law does not hold liable everyone who caused a harm to occur Industry custom not a defense – T.J. Hooper (1932) “there are precautions so imperative that even their universal disregard will not excuse their omission.” .but, may be a sword (Verizon case) 1 (C) 2000-2004 Kenneally

Basis for imposing a Duty to Secure (4) 1. Knowledge: Foreseeability of Harm Foreseeability of Party harmed (Plaintiff) Problem: pool of foreseeable Plaintiffs on Internet boundless? case compare: – – doctors, hospital, drug maker -- passenger SWV, ISP, Web Master, -- Inet passenger 1 (C) 2000-2004 Kenneally

(Basis for imposing Duty, con’t) 2. Ability to Control: nature of authority some parties in better position to control security implementations nature of relationship self-protection dependent on others’ security expectation of care owed reliance 1 (C) 2000-2004 Kenneally

(Basis for imposing Duty, con’t) 2. Ability to Control: /e.g./ Maine Public Utilities Commission v. Verizon Verizon-Maine provides wholesale Internet access to local telecommunications companies--Competitive Local Exchange Carriers (CLECs). 1/03 Slammer hit Verizon network To contain spread, Verizon shut down interfaces with CLECs No Inet access for one day Ruling: Verizon could've easily avoided the damage to CLECs – MSFT warn and release patch 6 months prior – Award CLECs 62K compensation as result of harm incurred by Verizon's (C) 2000-2004failure Kenneallyto patch 1

(Basis for imposing Duty, con’t) 3. Assumption of Duty party that voluntarily undertakes security measures, required to act reasonably liable for foreseeable, harmful results question: do self-imposed duties arise from implementing security policies & procedures? 1 (C) 2000-2004 Kenneally

(Basis for imposing Duty, con’t) 3. Assumption of Duty Privacy Policies Many privacy policy contain broad data security commitments /e.g/ www.cnn.com “We have put in place appropriate physical, electronic, and managerial procedures to safeguard and help prevent unauthorized access, maintain data security, and correctly use the information we collect online” 1 (C) 2000-2004 Kenneally

(Basis for imposing Duty, con’t) 3. Assumption of Duty Privacy Policies Enforcement Actions Based Upon Security Statements in Privacy Policies Eli Lilly Promised that it employed measures and takes steps appropriate under the circumstances to maintain and protect the confidentiality of personal information through its web sites 1 (C) 2000-2004 Kenneally

(Basis for imposing Duty, con’t) 3. Assumption of Duty – Privacy Policies PETCO (11/04) Consent order with FTC for violating website privacy policy Flaws allow hacker access to consumer records, cc's FTC alleges no implement reasonable and appropriate security measures to secure and protect sensitive consumer information – including simple, readily available defenses (patch for sql injection attack) – No encrypt sensitive info in storage 1 (C) 2000-2004 Kenneally
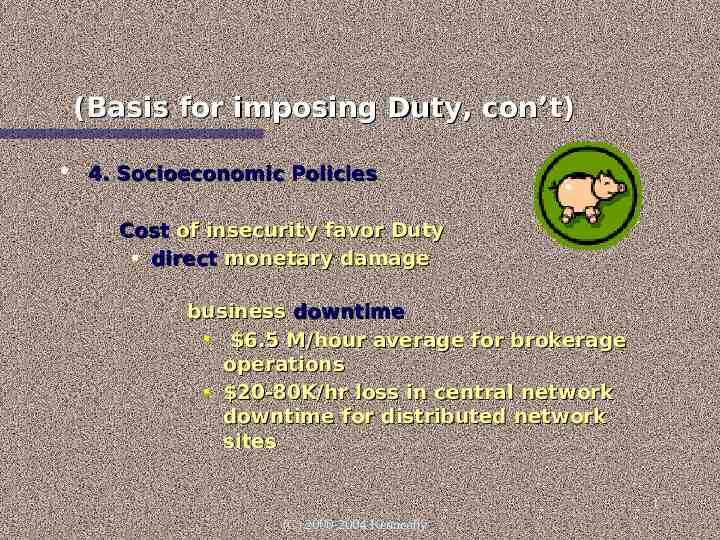
(Basis for imposing Duty, con’t) 4. Socioeconomic Policies Cost of insecurity favor Duty direct monetary damage – business downtime 6.5 M/hour average for brokerage operations 20-80K/hr loss in central network downtime for distributed network sites 1 (C) 2000-2004 Kenneally

(Socioeconomic policies, con’t) indirect monetary damage – loss of customer base, damage to business reputation & public image, destruction of potential partnerships, delays to market – /i.e./ DDoS (2/00) 1B capitalization losses 100M lost sales and advertising (Yankee Group) 1 (C) 2000-2004 Kenneally

(Socioeconomic policies, con’t) Economic incentive no quality incentive Ecommerce & technology growth duty reflects policy that Internet users entitled to some modicum of security foster business 1 (C) 2000-2004 Kenneally

(Socioeconomic policies, con’t) Holding wrongdoer responsible futile insolvent inability to ID prosecution problems traceback difficult 1 (C) 2000-2004 Kenneally

(Socioeconomic policies, con’t) Causation loopholes inapplicable in Networked society Web servers can be operated by any cable modem hosts targeted as launch pads for attack attack tools (DDoS- Trinoo, TFN, Stachledraht)no longer platform specific attacks automated 1 (C) 2000-2004 Kenneally

(Socioeconomic policies, con’t) need to secure info will persist danger of false victimization claims Anti-government regulation distribute risk of loss Physical harm- TBD (911 virus) SQL Slammer (03') 1 (C) 2000-2004 Kenneally

Who Owes a Duty to Secure Computers? What is the Scope? Someone has intruded into your computer and stolen data and brought down your system. Who ya gonna blame? Software vendor - time to market pressure, neglects to code against buffer overflows ISP - failed to patch servers; no warn customers of problems; set inappropriate permissions Web Co. - did not install firewall, IDS, or scan for network vulnerabilities; did not log or review traffic denied at firewall User of Internet- bypass installation instructions, did not upgrade or use AV software 1 (C) 2000-2004 Kenneally

"Every American relies upon cyberspace and every American has to do something to secure their part of cyberspace." - Richard Clarke, former Security Advisor to the President 1 (C) 2000-2004 Kenneally

Downstream Liability Analogous to suing auto manufacturer when its defective vehicle injures someone other than the driver Theory in information security context is largely untested Allows third parties to file tort claims against software manufacturers, ISPs, and others that would be contractually barred if filed by the user of the software or service 1 (C) 2000-2004 Kenneally
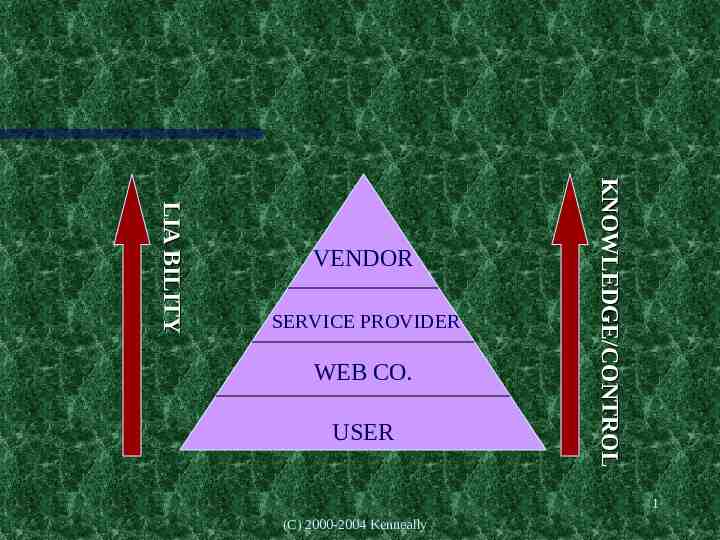
SERVICE PROVIDER WEB CO. USER KNOWLEDGE/CONTROL LIA BILITY VENDOR 1 (C) 2000-2004 Kenneally

SWV/Developer Duty Issue: should a SWV be liable for failure to secure when his defective security design in product allows intruder to harm ISP, Web Co., user? Compare: architect liability to contractor for defective building design Basis Knowledge ; Control ; Best Position imputed knowledge-widespread news ; specific class victims patent knowledge- patch posting, warnings in response to security watchdog alerts (CERT) and INDEPENDENTLY (C) 2000-2004 Kenneally 1

Blame Game 1 (C) 2000-2004 Kenneally

ISP Duty Compare: Landlord ---------- ISP Tenant ----------- Web Co/User UTP criminal ------ UTP criminal Landlord liable for failure to provide adequate security from criminal invasions against their tenants 1 (C) 2000-2004 Kenneally
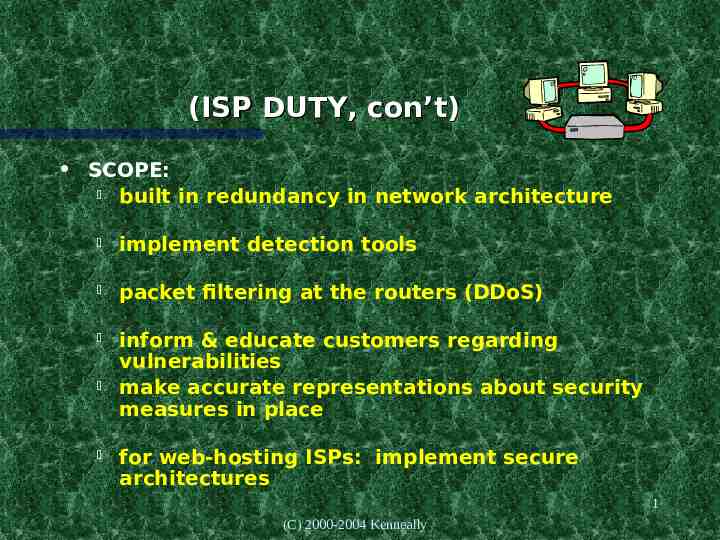
(ISP DUTY, con’t) SCOPE: built in redundancy in network architecture implement detection tools packet filtering at the routers (DDoS) inform & educate customers regarding vulnerabilities make accurate representations about security measures in place for web-hosting ISPs: implement secure architectures 1 (C) 2000-2004 Kenneally

(ISP Duty, con’t) Case hypothetical DDoS vs. online brokerage (Ameritrade) attack relay thru hosting service (Digex) .no access big loss possible claims 1. Customers v. brokerage 2. Brokerage v. ISP 3. Customers v. ISP 1 (C) 2000-2004 Kenneally
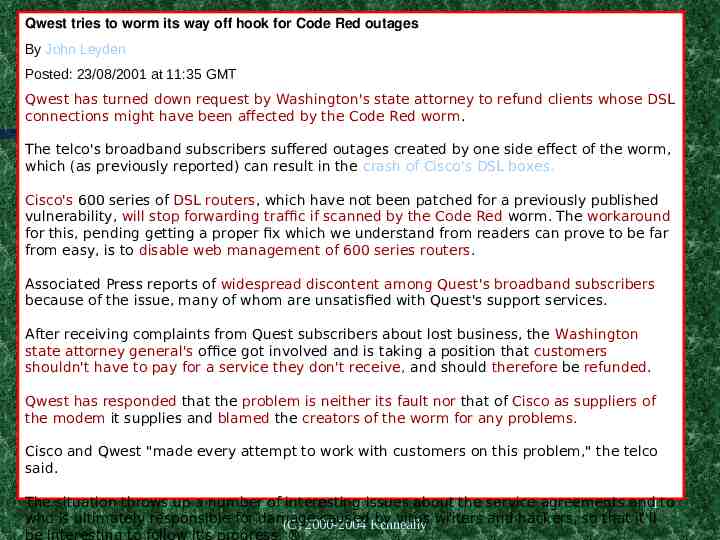
Qwest tries to worm its way off hook for Code Red outages By John Leyden Posted: 23/08/2001 at 11:35 GMT Qwest has turned down request by Washington's state attorney to refund clients whose DSL connections might have been affected by the Code Red worm. The telco's broadband subscribers suffered outages created by one side effect of the worm, which (as previously reported) can result in the crash of Cisco's DSL boxes. Cisco's 600 series of DSL routers, which have not been patched for a previously published vulnerability, will stop forwarding traffic if scanned by the Code Red worm. The workaround for this, pending getting a proper fix which we understand from readers can prove to be far from easy, is to disable web management of 600 series routers. Associated Press reports of widespread discontent among Quest's broadband subscribers because of the issue, many of whom are unsatisfied with Quest's support services. After receiving complaints from Quest subscribers about lost business, the Washington state attorney general's office got involved and is taking a position that customers shouldn't have to pay for a service they don't receive, and should therefore be refunded. Qwest has responded that the problem is neither its fault nor that of Cisco as suppliers of the modem it supplies and blamed the creators of the worm for any problems. Cisco and Qwest "made every attempt to work with customers on this problem," the telco said. The situation throws up a number of interesting issues about the service agreements and1 to who is ultimately responsible for damage causedKenneally by virus writers and hackers, so that it'll (C) 2000-2004

Web Co. Duty to Secure Downstream liability Issue: Should a Web Co. be liable when its insecure computer(s) was used by an intruder to damage a third party? Legal basis Causation in networked society how far down chain of connected events leading to injury is society willing to ascribe liability? Environet (Internet environment) challenges meaning of “downstream” 1 (C) 2000-2004 Kenneally

Web Co. Duty to Secure Socioeconomic PoliciesPolicies economic burden Cost-benefit analysis Judge Learned Hand formula for negligence – Negligence B PL (US v. Carroll Towing, 1947) Reality - end-user may bear costs 1 (C) 2000-2004 Kenneally
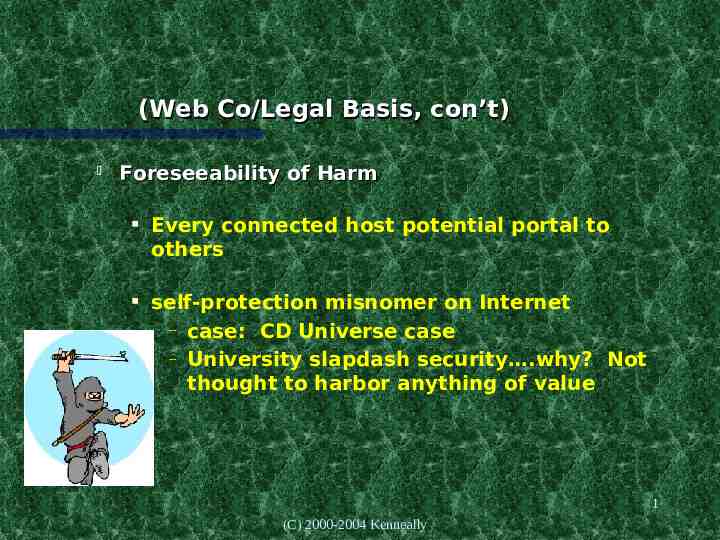
(Web Co/Legal Basis, con’t) Foreseeability of Harm Every connected host potential portal to others self-protection misnomer on Internet – case: CD Universe case – University slapdash security .why? Not thought to harbor anything of value 1 (C) 2000-2004 Kenneally

(Web Co/Legal Basis, con’t) Ability to Control Consensus? IT admins can reasonably be expected to take technical protective measures: – – – knowledge of programs running patch updates, egress filters – monitor bandwidth & type packets on network – awareness of attack sigs 1 (C) 2000-2004 Kenneally
(Web Co/Legal Basis, con’t) – – – – – – – – perimeter security plan disable unused services & assess network protocols firewall logging & review secure remote connections knowledge of latest exploits .monitor alert sites proper sw config network load balancing DISCLOSURE: no misrepresent 1 (C) 2000-2004 Kenneally

Downstream Victim- Causation Causation comparison: Downstream Victim of Computer Insecurity v. Medical Exposure Victim Similarities: complicated causation issues /ex./ Exposure to 1 chemicals, multiple manufacturers, can’t prove which caused – Current standard: “risk-based” causation theory: Significance: difficulty showing what actually allow system exploitation – Juries asked: WHETHER Def. ENHANCED THE RISK OF THE HARM 1 (C) 2000-2004 Kenneally
User Duty to Secure Issue: Issue should a User be liable when his insecure computer is used to damage another party on the Internet? Scope of duty may be different Why: Legal basis Knowledge, Control, burden Postulated duty: duty read instructions, update AV 1 (C) 2000-2004 Kenneally

‘This assault also demonstrates that machines operated by home users or small businesses (hosts less likely to be maintained by a professional sysadmin) are integral to the robustness of the global Internet. As is the case with biologically active pathogens, vulnerable hosts can and do put everyone at risk, regardless of the significance of their role in the population.’ (C) 2000-2004 Kenneally 1
Avoiding Liability Negligence Liability-Defenses No Duty: Learned Hand- unreasonable burdens vagueness of standrd Historical Rule: Good Samaritan? no liablty for LL for injuries to tenant by 3rd ptys Kline Socioeconomics ‘if finding liab will cost too much , or have potential to ruin an entity that is vital to public intersts, such as pub utility or municipal corp, scope of the duty will be carefully circumscribed ‘ Milliken v. Consolidated Edison 1 (C) 2000-2004 Kenneally

(Avoiding Liability) (Negligence Liability/Defenses) 3rd party liability limits Exclude mere “economic” loss Counter: case law accepting digital damage as property damage – ebay v. bidder’s edge, etc. Assumption of Risk (Let the Netizen Beware) Duty to Mitigate/Contributory Negligence Superceding cause foreseeability of criminal acts 1 (C) 2000-2004 Kenneally

(Avoiding Liability) (Negligence Liability/Defenses) Immunity ISPs defense: mere conduits of data defamation & copyright under common carrier doctrine; safe harbor in CDA & DMCA Counter: Counter ISPs may not be common carriers entitled to disclaim liability defamation & no necessarily extend to computer attacks If are common carriers: Statutes that historically void: garages & parking lots, pools, public rec 1 (C) 2000-2004 Kenneally Counter: not be cost-effective Counter may

Liability Defenses Contract Liability Defenses Disclaimers Counter: no viable against 3rd parties Counter: disclaimer may be invalid or unenforceable (void exculpatory clauses) 1 (C) 2000-2004 Kenneally

Erin E. Kenneally San Diego Supercomputer Center University of California San Diego erin @ sdsc.edu