KMIP Key Management with Vormetric Data Security Manager Controlling
17 Slides6.66 MB

KMIP Key Management with Vormetric Data Security Manager Controlling your keys with Thales eSecurity www.thalesesecurity.com
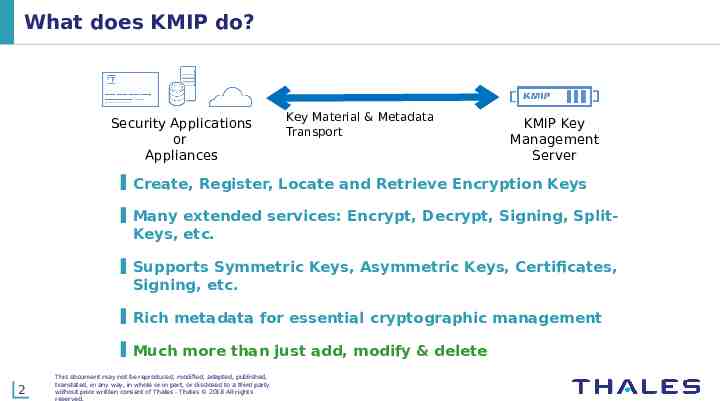
What does KMIP do? Security Applications or Appliances Key Material & Metadata Transport KMIP Key Management Server Create, Register, Locate and Retrieve Encryption Keys Many extended services: Encrypt, Decrypt, Signing, Split- Keys, etc. Supports Symmetric Keys, Asymmetric Keys, Certificates, Signing, etc. Rich metadata for essential cryptographic management Much more than just add, modify & delete 2 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.
KMIP Deployed in Solutions 4 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.
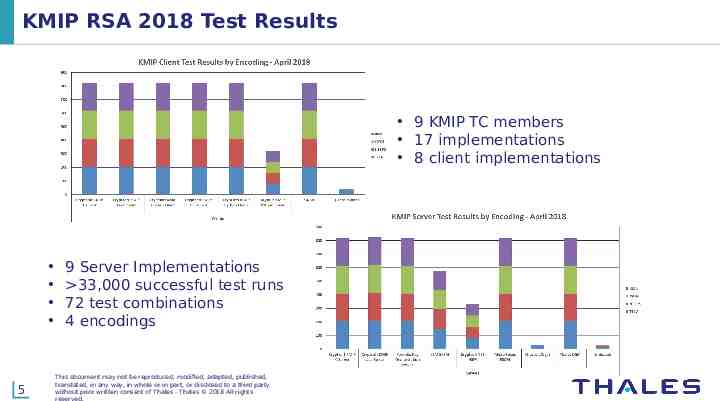
KMIP RSA 2018 Test Results 9 KMIP TC members 17 implementations 8 client implementations 5 9 Server Implementations 33,000 successful test runs 72 test combinations 4 encodings This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.

About Thales www.thalesesecurity.com

Thales Group – global leadership N 1 worldwid e N 2 worldwid Payloads for telecom satellites Air traffic manageme nt Sonars Rail signalling systems In-flight entertainm ent Military tactical radio comms e N 3 15 billion in revenues worldwid e 9 Security for interbank transactions This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved. Commercial avionics Civil satellites Military radars

Thales eSecurity – world leader in data protection 9 40 Years of securing the world’s most sensitive data Deep expertise and track record in applied cryptography Long-standing history of industry certifications and validation 10 Security for 20 19 Customers of Fortune 10 of the largest banks Security for 4 of the 5 largest energy companies This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved. 80% Protection of the world’s POS transactions 130 Partnerships with leading technology providers of cloud computing, digital payments and more
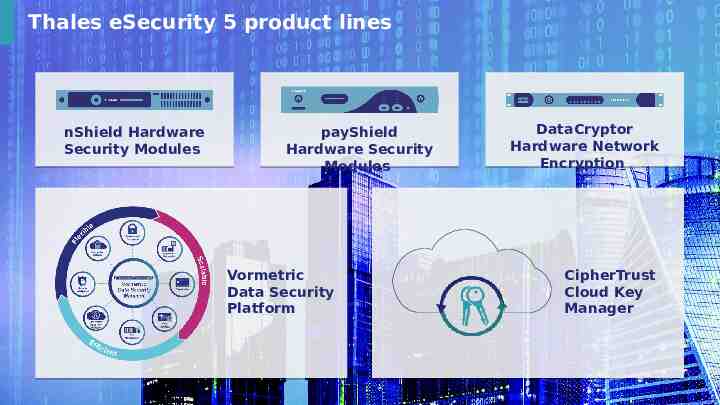
Thales eSecurity 5 product lines nShield Hardware Security Modules payShield Hardware Security Modules Vormetric Data Security Platform 11 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved. DataCryptor Hardware Network Encryption CipherTrust Cloud Key Manager

Vormetric DSM KMIP Key Management www.thalesesecurity.com

Vormetric Data Security Manager Available as: Virtual Appliance, FIPS 140-2 Level 1 V6000, FIPS 140-2 Level 2 hardware appliance V6100, FIPS 140-2 Level 3 Includes nShield Solo PCIe card 13 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.
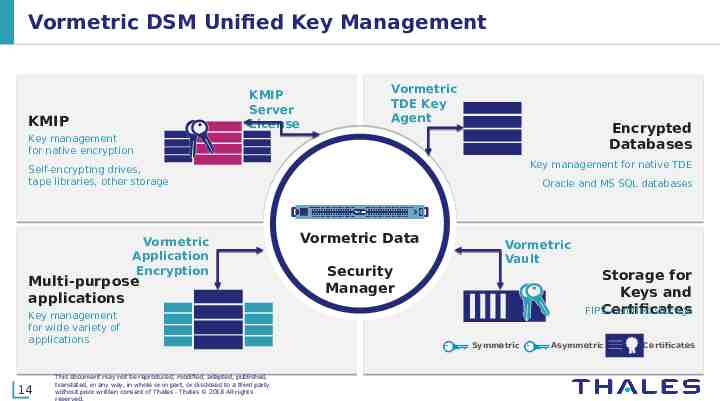
Vormetric DSM Unified Key Management KMIP Server License KMIP Vormetric TDE Key Agent Encrypted Databases Key management for native encryption Key management for native TDE Self-encrypting drives, tape libraries, other storage Vormetric Application Encryption Multi-purpose applications Key management for wide variety of applications 14 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved. Oracle and MS SQL databases Vormetric Data Security Manager Vormetric Vault Storage for Keys and FIPS-certified Certificates storage Symmetric Asymmetric Certificates
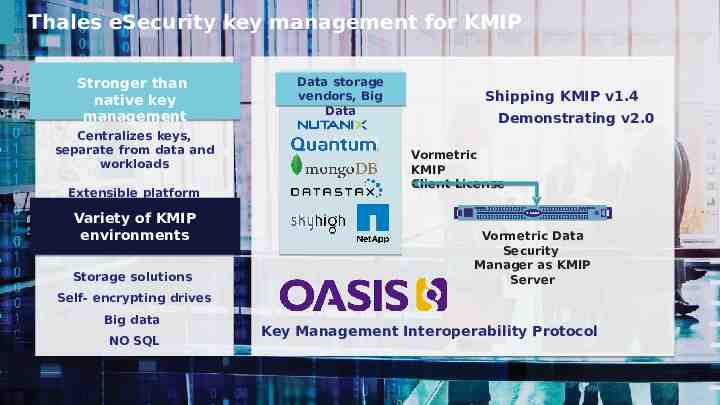
Thales eSecurity key management for KMIP Stronger than native key management Data storage vendors, Big Data Centralizes keys, separate from data and workloads Shipping KMIP v1.4 Demonstrating v2.0 Vormetric KMIP Client License Extensible platform solution Variety of KMIP environments Vormetric Data Security Manager as KMIP Server Storage solutions Self- encrypting drives Big data NO SQL 15 Key Management Interoperability Protocol This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.
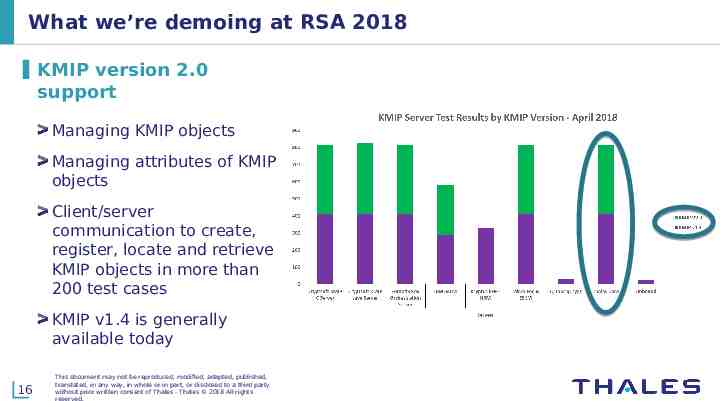
What we’re demoing at RSA 2018 KMIP version 2.0 support Managing KMIP objects Managing attributes of KMIP objects Client/server communication to create, register, locate and retrieve KMIP objects in more than 200 test cases KMIP v1.4 is generally available today 16 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.

Thales eSecurity KMIP Partners Partial list of qualified and in-flight partners 17 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.

Thank You www.thalesesecurity.com
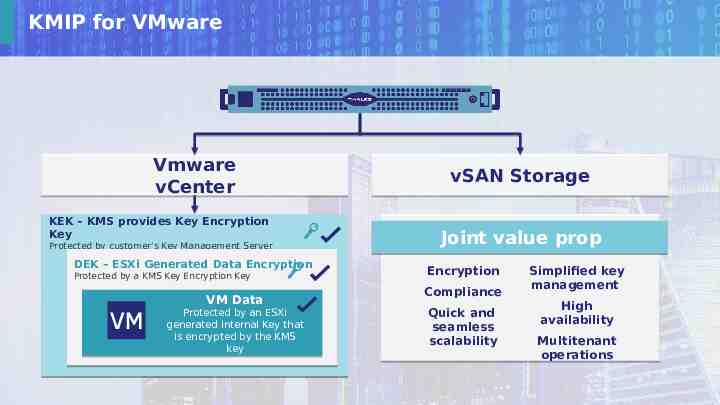
KMIP for VMware Vmware vCenter KEK – KMS provides Key Encryption Key Protected by customer’s Key Management Server DEK – ESXi Generated Data Encryption Protected by a KMS Key Encryption Key VM Data Protected by an ESXi generated internal Key that is encrypted by the KMS key 19 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved. vSAN Storage Joint value prop Encryption Compliance Quick and seamless scalability Simplified key management High availability Multitenant operations
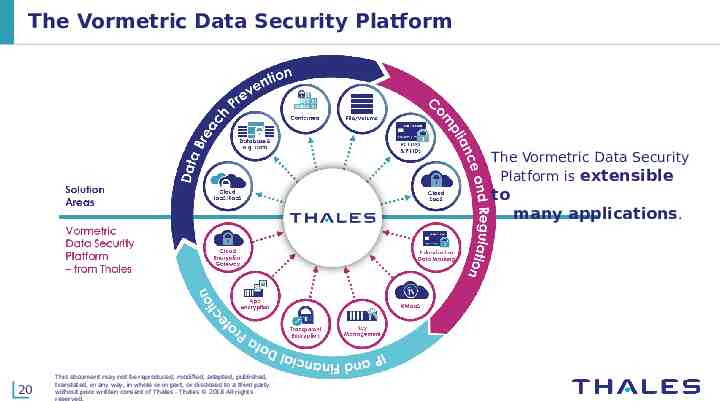
The Vormetric Data Security Platform The Vormetric Data Security Platform is extensible to many applications. 20 This document may not be reproduced, modified, adapted, published, translated, in any way, in whole or in part, or disclosed to a third party without prior written consent of Thales - Thales 2018 All rights reserved.






