Information System Security AABFS-Jordan Summer 2006 Mobile
36 Slides254.00 KB

Information System Security AABFS-Jordan Summer 2006 Mobile Code Security Prepared by: Mossab Al Hunaity Supervised by: Dr. Lo’ai Tawalbeh

Outline Introduction (5 minutes) Advantages of Mobile codes (Agents) Mobile Code (Agent) Applications Mobile Code Security (20 minutes) Protecting the Host Protecting the Agent Mobile Code Security in Practice (10 minutes) Conclusions (5 minutes) Questions
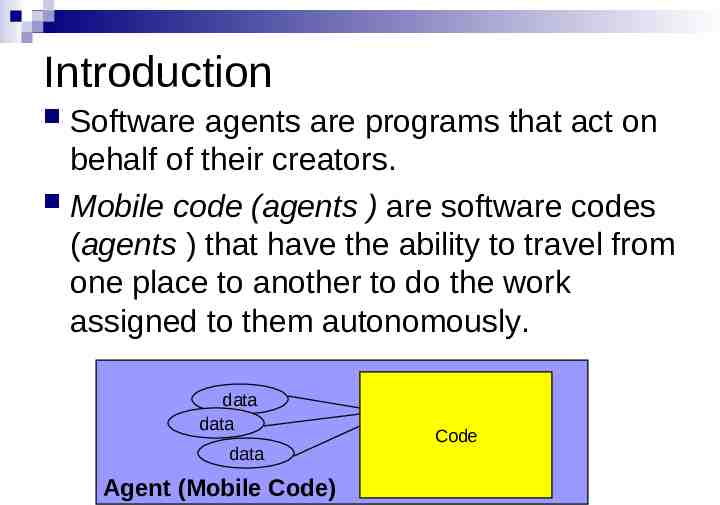
Introduction Software agents are programs that act on behalf of their creators. Mobile code (agents ) are software codes (agents ) that have the ability to travel from one place to another to do the work assigned to them autonomously. data data data Agent (Mobile Code) Code

Advantages of Mobile codes (Agents) Better network performance and Utilization Automation of a sequence of tasks on different locations Distribution and Update of software packages.

Mobile Code (Agent) Applications Data collection from many place implement a network backup tool Searching and filtering visit many sites, search through the information available at each site to match a search criterion Monitoring E.g. in a stock market host, wait for a certain stock to hit a certain price, notify its user or even buy some of the stocks on behalf of them . Targeted information dissemination Distribute interactive news or advertisements

Mobile Agent Applications / cont. Parallel processing distribute processes easily over many computers in the network E-Commerce A mobile agent could do your shopping, including making orders and even paying Entertainment Games , players Negotiating negotiate to establish a meeting time, get a reasonable price for a deal

Mobile Code Security In the past, mobile code was machine dependent and could only run on very specific machine architectures, today this is not the case we are becoming increasingly vulnerable to malicious attacks and defective software roaming the internet security of mobile code is emerging as one of the most important challenges facing computer research today

Basic Concepts Trust Security is based on the notion of trust. Basically, software can be divided into two categories, trusted software (All software from our side) and un trusted software (All software not from our side) Safety Policy A code is safe if it follows Control Flow, Memory, and Stack Safety

Mobile Code Security Dimensions Protecting the host from a malicious Mobile Code. Sandboxing Code Signing Firewalling Proof-carrying code Protecting Mobile Code from the Execution Environment Active and Passive attacks

Protecting the Host There are various ways by which a malicious agent can harm the host. An agent may steal or manage to get illegal access to some private data, e.g. the financial data of a company from a database residing on the host. An agent may damage or consume the host resources like deleting some files, consume a lot of processing power or network bandwidth or cause denial of services as well

How to Protect The Host Sandboxing Code Signing Firewalling Proof-carrying code

Sandboxing The basic idea behind sandboxing is to make the foreign mobile code to be executed within a sandbox in the host operating system. Then the mobile code can be controlled efficiently by allowing monitored access to local host resources like CPU time, memory, etc. so that denial of service attacks by the mobile code like over consuming resources do not occur. One of the most known examples of sandboxing technology is the Security Manager of Java and Code Access Security in dot net.
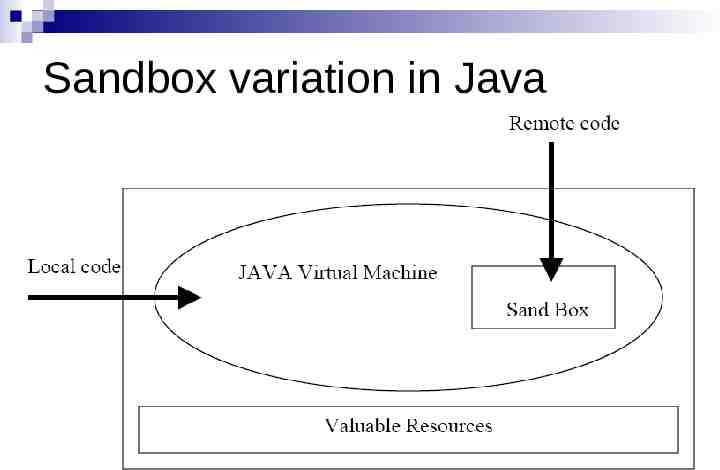
Sandbox variation in Java
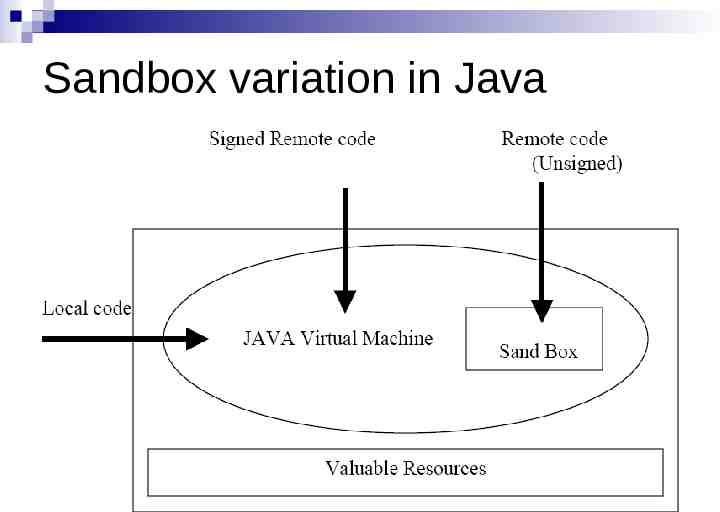
Sandbox variation in Java

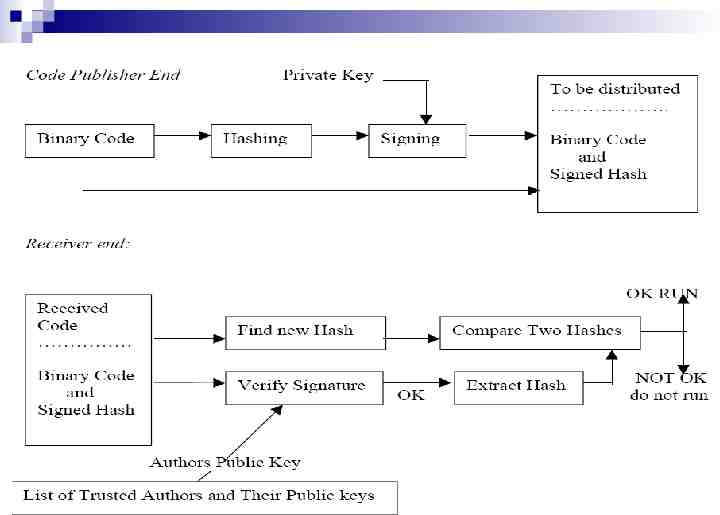
Code Signing Idea is to authenticate the mobile code before it is actually executed . The producer of the code is required to sign it. And the code consumer verifies the signature of the producer before using it Digital signatures are created using RSA

Code Signing Details RSA takes longer time for signing long documents. So the usual practice is to sign the hash of code and distribute it along with the code. This method saves time and insure integrity Changing original code at one bit will result in complete change of hash of message. At the receiver end the client computes the hash of mobile code it received and compares it with that sent by the user to ensure data integrity.
Firewalling Selectively choose whether or not to run a program at the very point where it enters the client domain. For example, if an organization is running a firewall or web proxy, it identify Java applets, examine them, and decide whether or not to serve them to the client. Research Usually it hard to implement.

Proof-Carrying Code Enables a host to determine that a program code provided by another system is safe to install and execute. The basic idea of PCC is that the code producer is required to provide an encoding of a proof that his/her code adheres to the security policy specified by the code consumer. The proof is encoded in a form that can be transmitted digitally. Therefore, the code consumer can quickly validate the code using a simple, automatic, and reliable proofchecking process

PCC process Step 1: the producer prepare the un trusted code he adds annotations to the code, which helps the code consumer to understand the safety-relevant properties of the code. then he sends the annotated code to the code consumer to execute it. Step 2: The code consumer performs a fast but detailed inspection of the annotated code. This I accomplished using a program, called VCGen and produce safety predicate

PCC process / cont. Step 3: Upon receiving the safety predicate, the producer attempts to prove it, and sends a formal proof back to the code consumer. Step 4: The code consumer performs a proof validation Step 5: after the executable code has passed both the VCGen checks and the proof check, it is trusted not to violate the safety policy and It can be safely installed for execution, without any further need for run-time checking

Protecting the Agent Protecting the Agent during the Transfer Protecting the Agent during the Execution

Protecting the Agent during the Transfer As a mobile agent moves around the network, its code as well as its data is vulnerable to various security threats. There are two known types of attacks passive attacks and active attacks

Passive Attacks Passive Attacks An adversary attempts to extract some information from messages exchanged between two Agents without modifying the contents of the messages (eavesdropping). Usually cryptographic mechanisms, such as RSA and ElGamal cryptosystems are used to protect against this kind of attacks

Active Attacks Attacker in this case is able to modify the data or the code of a mobile agent to benefit from them or impersonate a legitimate principal in the system and intercept messages intended for that principal Data integrity mechanisms can be used to protect against tampering (message digest technique ) Collision-Free Hash Functions MD5 Authentication mechanisms can be used to protect against impersonation.

Protecting The Agent during the Execution In general, it is very difficult to protect an Agent from the environment that is responsible for its execution. Therefore, protecting an agent is more difficult and challenging than protecting the host resources from a malicious agent

Dangers to Agents A host may simply destroy the agent and hence impede the function of its parent application. A host may steal sensitive information carried by the agent such as a private key of the agent’s owner. A host may modify the data carried by the agent for its favor. For instance, it might change the price quoted by another competitor. Or modify the agent’s code to perform some dangerous actions when it returns to its home site.

How to Protect the Agent during the Execution Limited blackbox security Computing with encrypted functions. Cryptographic traces

Limited blackbox security The key idea of blackbox security is to generate an executable code from a given agent specification. This generated code is executed as a “blackbox” by the host, i.e. the host can not modify or read it but it only can execute it as is.

Computing with encrypted functions. The Key idea is that there is no intrinsic reason why a program must be executed in a plaintext form Therefore, one can have a computer executes a cipher program without understanding it.

Cryptographic traces The mechanism is based on post-mortem analysis of data (called traces) that are collected during the execution of an agent. The traces are then used as a basis for code execution verification, i.e. has the code executed its designated tasks properly or not?

Conclusion Mobile code security is a very important research topic. There are many models for achieving Mobile code security but we still need more secure and fast approches.

Mobile Code Security in Practice We are going to see how to implement some of those principles using the Dot Net technology.

Questions

References Papers: M. Abadi and B. Bhargava, “On Mobile Code Security,” CERIAS Tech Report,2001. S. Ramdous and G. Kannan, “SECURITY OF MOBILE CODE,” Journal of Cryptology, 2(1),2002, pp.1-12. Alfonso Fuggetta et al, Understanding Code mobility, IEEE Transactions on Software Engineering. 1998. Wayne A. Jansen, Countermeasures for Mobile Agent Security, National Institute of Standards and technology. http://java.sun.com/products/jdk/1.2/docs/guide/ security/CryptoSpec.html.

Thank You ! Mossab Al Hunaity Dr. Lo’ai Tawalbeh







