Information Security Challenges & Best Practices Meng-Chow Kang,
32 Slides3.01 MB

Information Security Challenges & Best Practices Meng-Chow Kang, CISA, CISSP Chief Security & Privacy Advisor Microsoft Asia Pacific
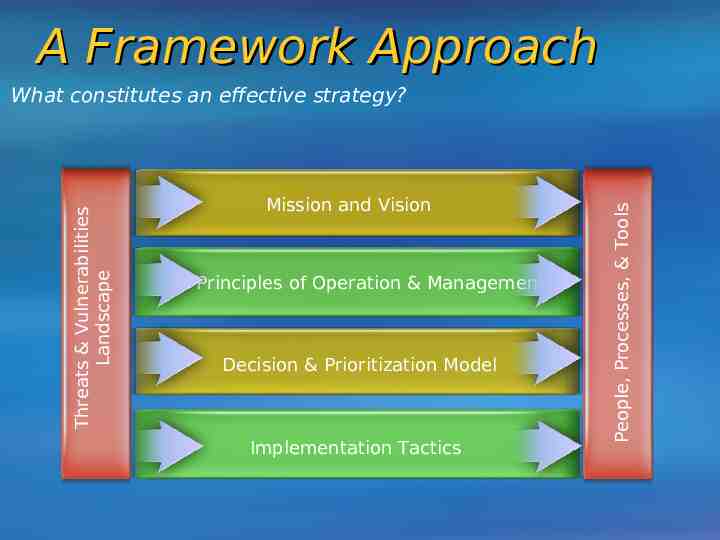
A Framework Approach Mission and Vision Principles of Operation & Management Decision & Prioritization Model Implementation Tactics People, Processes, & Tools Threats & Vulnerabilities Landscape What constitutes an effective strategy?
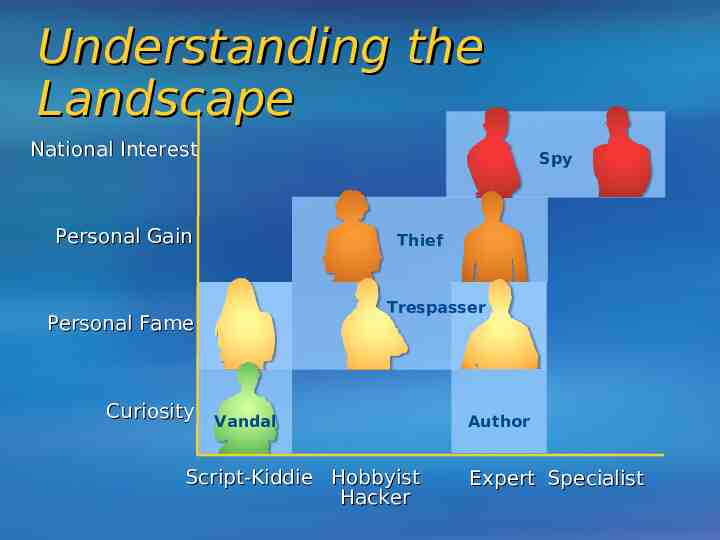
Understanding the Landscape National Interest Spy Personal Gain Thief Trespasser Personal Fame Curiosity Vandal Script-Kiddie Hobbyist Hacker Author Expert Specialist
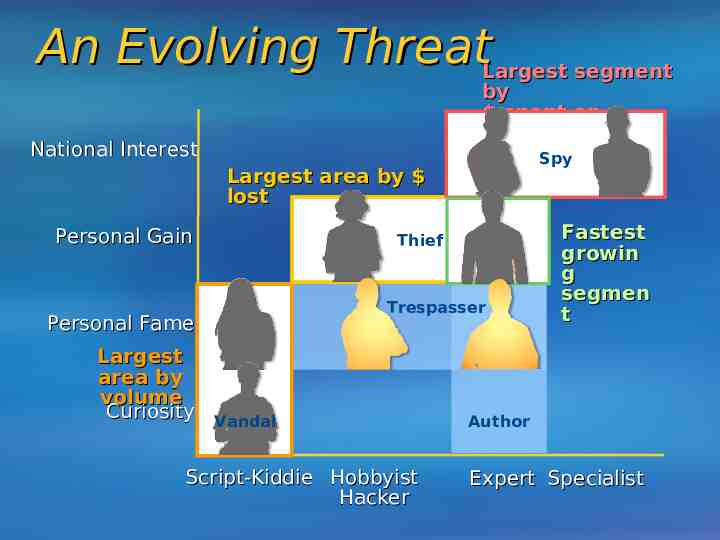
An Evolving ThreatLargest segment by spent on defense National Interest Spy Largest area by lost Personal Gain Thief Trespasser Personal Fame Largest area by volume Curiosity Vandal Script-Kiddie Hobbyist Hacker Fastest growin g segmen t Author Expert Specialist
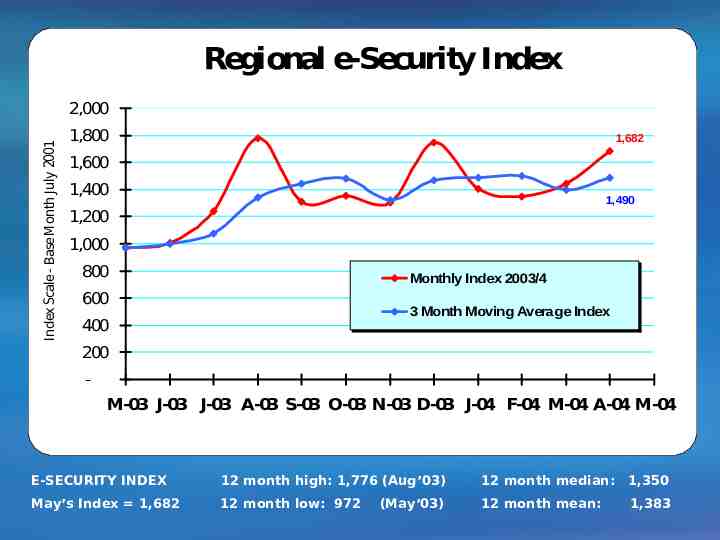
Regional e-Security Index Index Scale - Base Month July 2001 2,000 1,800 1,682 1,600 1,400 1,490 1,200 1,000 800 Monthly Index 2003/4 600 3 Month Moving Average Index 400 200 - M-03 J-03 J-03 A-03 S-03 O-03 N-03 D-03 J-04 F-04 M-04 A-04 M-04 E-SECURITY INDEX 12 month high: 1,776 (Aug’03) 12 month median: 1,350 May’s Index 1,682 12 month low: 972 12 month mean: 1,383 (May’03)
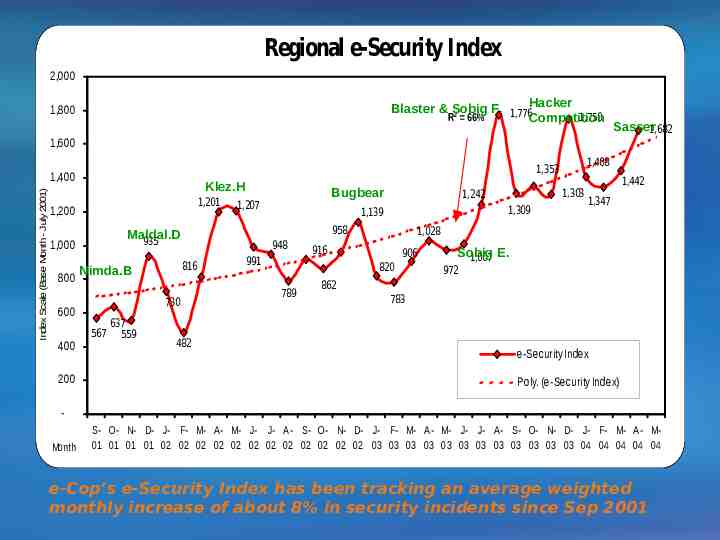
Regional e-Security Index 2,000 Blaster & Sobig F. 1,776Hacker 2 R 66% 1,750 Competition 1,800 Sasser1,682 1,600 Index Scale (Base Month - July 2001) 1,400 Klez.H 1,201 1,200 730 600 400 200 567 637 559 1,309 1,139 948 482 Source: e-Cop 991 1,442 1,347 1,028 916 906 820 789 1,303 1,242 958 816 Nimda.B Bugbear 1,207 Maldal.D 935 1,000 800 1,408 1,353 Sobig 1,007 E. 972 862 783 e-Security Index Poly. (e-Security Index) Month S- O- N- D- J- F- M- A- M- J- J- A- S- O- N- D- J- F- M- A- M- J- J- A- S- O- N- D- J- F- M- A- M01 01 01 01 02 02 02 02 02 02 02 02 02 02 02 02 03 03 03 03 03 03 03 03 03 03 03 03 04 04 04 04 04 e-Cop’s e-Security Index has been tracking an average weighted monthly increase of about 8% in security incidents since Sep 2001
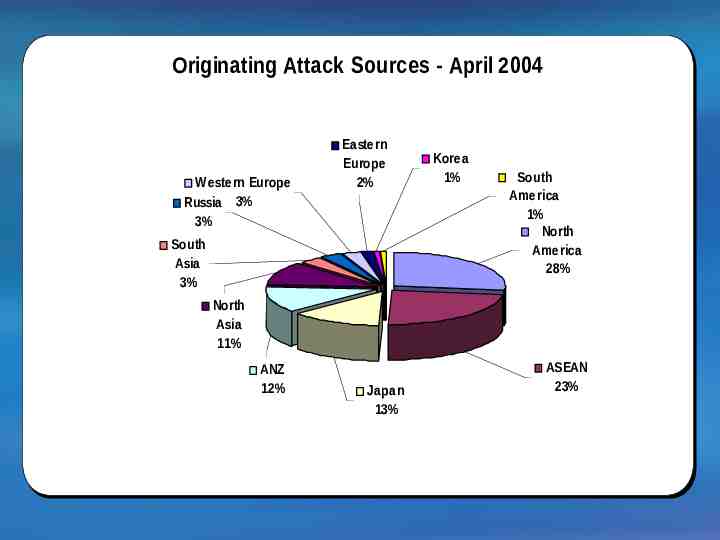
Originating Attack Sources - April 2004 Western Europe Russia 3% 3% Eastern Europe 2% South Asia 3% Korea 1% South America 1% North America 28% North Asia 11% ANZ 12% Japan 13% * North Asia excludes Japan & South Korea ASEAN 23% Source: e-Cop
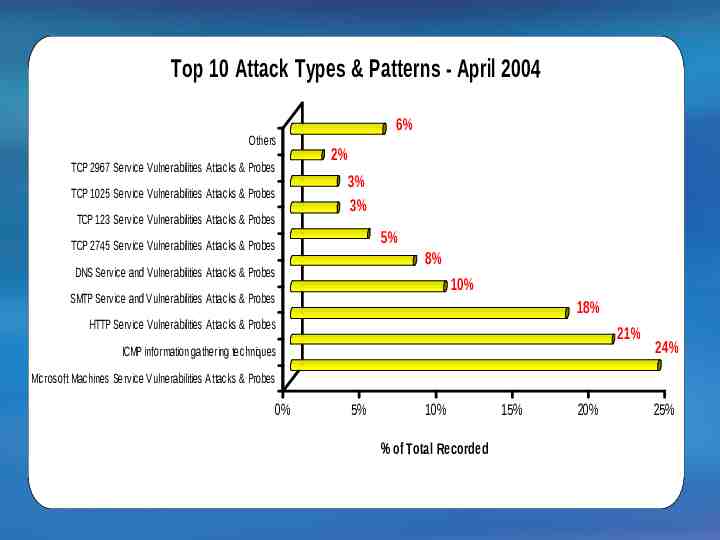
Top 10 Attack Types & Patterns - April 2004 Others TCP 2967 Service Vulnerabilities Attacks & Probes TCP 1025 Service Vulnerabilities Attacks & Probes TCP 123 Service Vulnerabilities Attacks & Probes 6% 2% 3% 3% 5% TCP 2745 Service Vulnerabilities Attacks & Probes 8% DNS Service and Vulnerabilities Attacks & Probes 10% SMTP Service and Vulnerabilities Attacks & Probes 18% HTTP Service Vulnerabilities Attacks & Probes 21% ICMP information gathering techniques 24% Microsoft Machines Service Vulnerabilities Attacks & Probes 0% 5% 10% 15% 20% 25% % of Total Recorded Source: e-Cop

Situation Hackers rely on patches to develop exploits Some security researchers are still disclosing vulnerabilities irresponsibly Why Mostdoes attacks this occur gap exist? here Product ship Vulnerability discovered Component modified Patch released Patch deployed at customer site Lack-of or ineffective patch management process Lack-of defense-in-depth and configuration management in infrastructure security

Exploit Timeline Process, Guidance, Tools Critical exploit patch code Why does this gap exist? Days between patch & exploit I Product ship I Vulnerability discovered 331 180 Days FromI Patch To Exploit I I Vulnerability Fix Fix Have decreased sodeployed that made public/ deployed customer in patching is not aatdefense Component fixed large organizationssite 151 25 Nimda SQL Slammer Welchia/ Nachi Blaster Average 9 days for patch to be reverse engineered to identify vulnerability
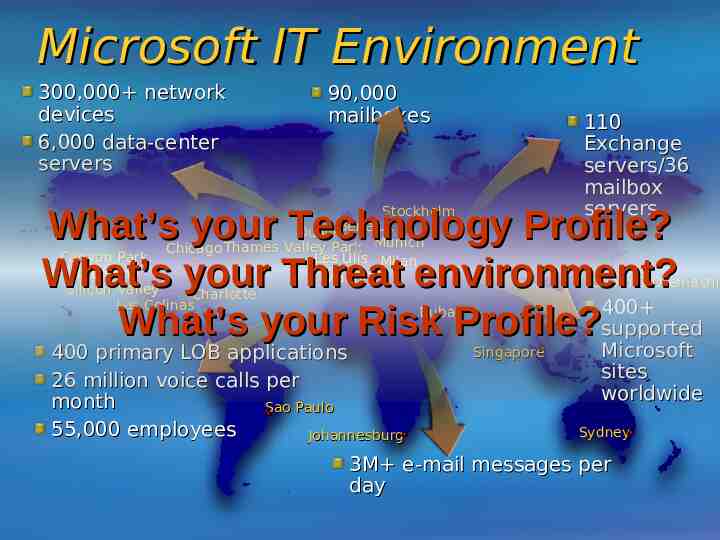
Microsoft IT Environment 300,000 network devices 6,000 data-center servers 90,000 mailboxes 110 Exchange servers/36 mailbox servers What’s your Technology Profile? What’s your Threat environment? 400 What’s your Risk Profile?supported Stockholm DublinBenelux Chicago Thames Valley Park Munich Canyon Park, Les Ulis Milan Redmond Madrid Silicon Valley Charlotte Las Colinas Dubai 400 primary LOB applications 26 million voice calls per month Sao Paulo 55,000 employees Johannesburg Chofu & Otemachi Singapore Microsoft sites worldwide Sydney 3M e-mail messages per day
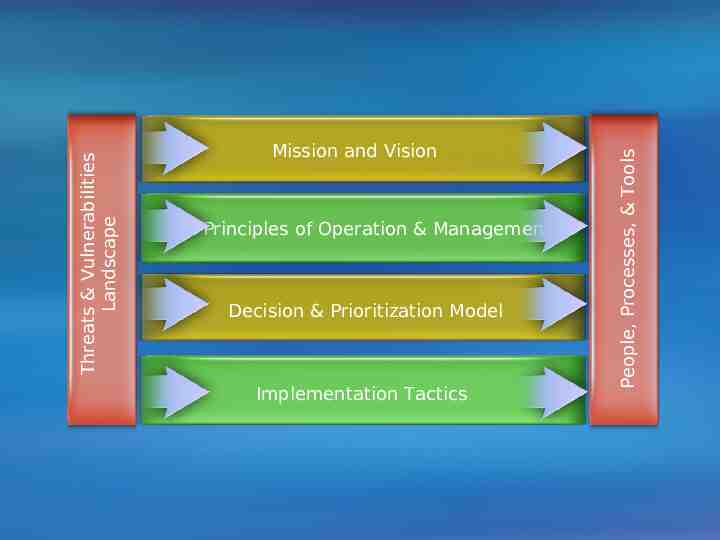
Principles of Operation & Management Decision & Prioritization Model Implementation Tactics People, Processes, & Tools Threats & Vulnerabilities Landscape Mission and Vision
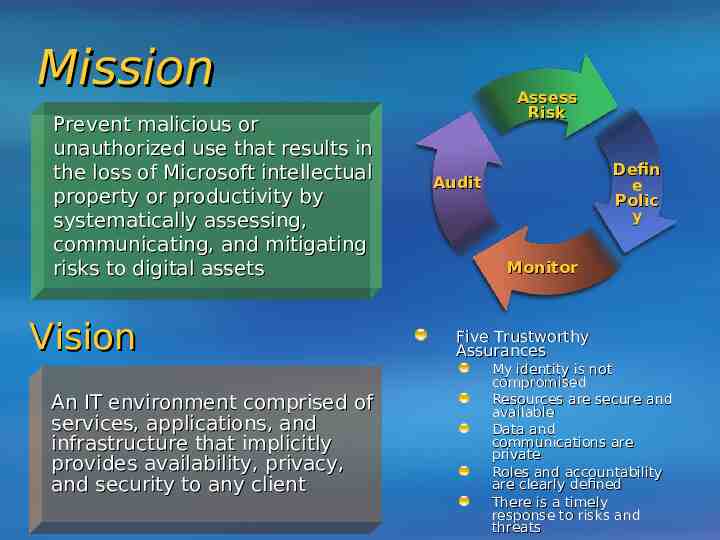
Mission Prevent malicious or unauthorized use that results in the loss of Microsoft intellectual property or productivity by systematically assessing, communicating, and mitigating risks to digital assets Vision An IT environment comprised of services, applications, and infrastructure that implicitly provides availability, privacy, and security to any client Assess Risk Defin e Polic y Audit Monitor Five Trustworthy Assurances My identity is not compromised Resources are secure and available Data and communications are private Roles and accountability are clearly defined There is a timely response to risks and threats

Other Business Drivers Security Risk Management Reducing Reducing exposures exposures to to technology technology threats threats Preventing Preventing computer-related computer-related frauds frauds Enforce Enforce policies policies and and improve improve audit audit capability capability Regulatory Compliance HIPAA HIPAA Gramm-Leach-Bliley Gramm-Leach-Bliley Sarbane-Oxley Sarbane-Oxley Act Act Reducing Operational Online Business Reducing Reducing cost cost of of unexpected unexpected security security Costs events events Reducing Reducing losses losses from from frauds frauds and and security security failures failures Integrate Integrate Partners Partners in in Supply Supply Chain Chain EnablementConnect Connect with with Customers Customers Empower the the information information workers workers
Principles of Operation & Management Decision & Prioritization Model Implementation Tactics People, Processes, & Tools Threats & Vulnerabilities Landscape Mission and Vision

Security Principles Management commitment Manage risk according to business objectives Define organizational roles and responsibilities Users and data Manage to practice of least privilege Strictly enforce privacy and privacy rules Application and system development Build security into development life cycle (Microsoft SD3 C Framework) Create layered defense and reduce attack surface (Defense-indepth) Operations and maintenance Integrate security into operations framework Align monitor, audit, and response functions to operational functions Watchful, constant vigilance, readiness, and responsiveness

Strategies for Security Policies Root your security policy in well-known industry standards or regulations ISO 17799 – Security Management Best Practices ISC2 Common Book of Knowledge RFC 2196 – Site Security Handbook Security policies have to start from the top down Illustrate the value of security policy to management Get corporate legal and HR departments to assist you

Environment conducive for protection Protection ready versus attackers’ friendly Laws and regulations Enforcements Rewards and penalties Think and do security
Principles of Operation & Management Decision & Prioritization Model Implementation Tactics People, Processes, & Tools Threats & Vulnerabilities Landscape Mission and Vision
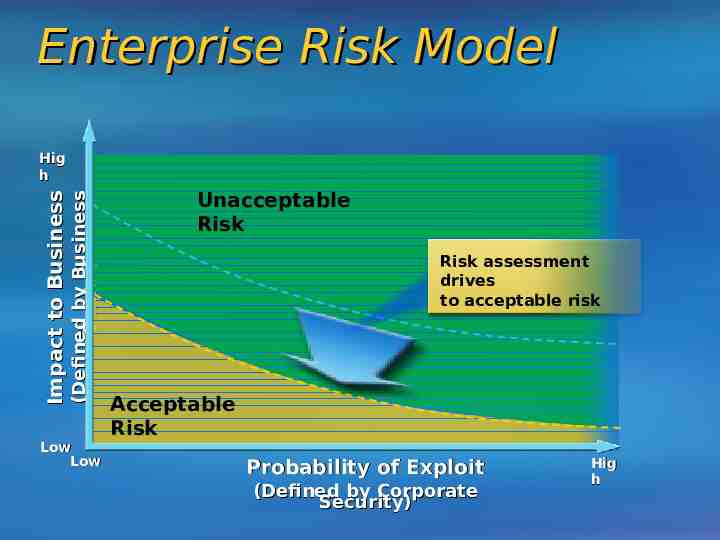
Enterprise Risk Model (Defined by Business Owner) Impact to Business Hig h Low Low Unacceptable Risk Risk assessment drives to acceptable risk Acceptable Risk Probability of Exploit (Defined by Corporate Security) Hig h
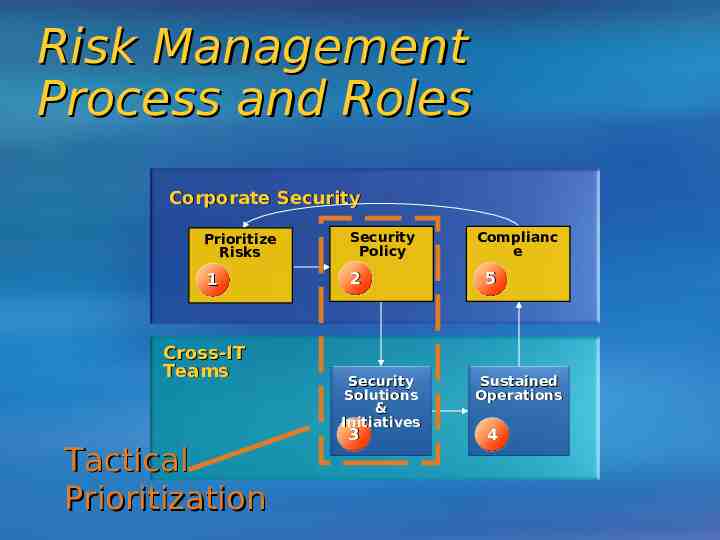
Risk Management Process and Roles Corporate Security Prioritize Risks Security Policy 1 2 Cross-IT Teams Tactical Prioritization Security Solutions & Initiatives 3 Complianc e 5 Sustained Operations 4
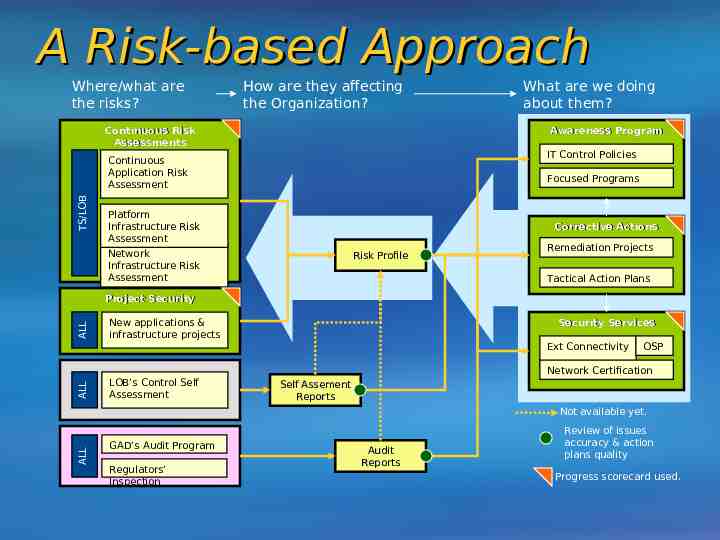
A Risk-based Approach Where/what are the risks? How are they affecting the Organization? Continuous Risk Assessments Awareness Program IT Control Policies Continuous Application Risk Assessment TS/LOB What are we doing about them? Focused Programs Platform Infrastructure Risk Assessment Corrective Actions Network Infrastructure Risk Assessment Risk Profile Remediation Projects Tactical Action Plans ALL Project Security New applications & infrastructure projects Security Services Ext Connectivity OSP ALL Network Certification LOB’s Control Self Assessment Self Assement Reports ALL Not available yet. GAD’s Audit Program Regulators’ Inspection Audit Reports Review of issues accuracy & action plans quality Progress scorecard used.
Principles of Operation & Management Decision & Prioritization Model Implementation Tactics People, Processes, & Tools Threats & Vulnerabilities Landscape Mission and Vision
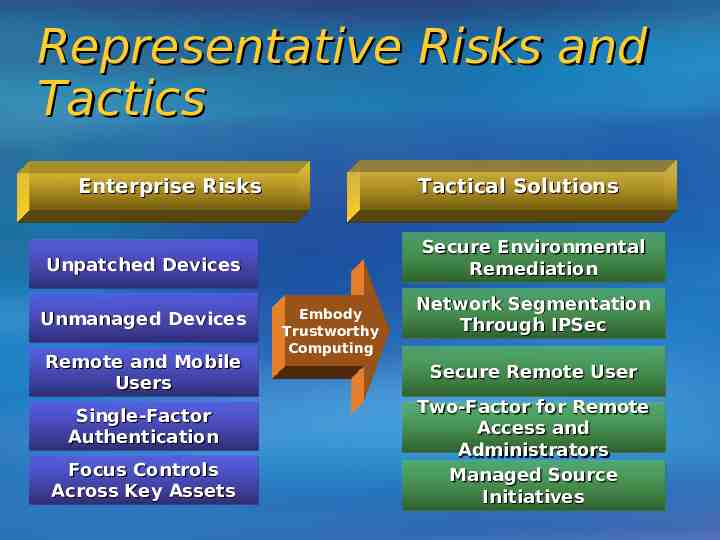
Representative Risks and Tactics Tactical Solutions Enterprise Risks Secure Environmental Environmental Remediation Unpatched Devices Devices Unmanaged Unmanaged Devices Devices Remote Remote and Mobile Users Users Single-Factor Single-Factor Authentication Authentication Focus Focus Controls Controls Across Across Key Key Assets Assets Embody Trustworthy Computing Network Segmentation Segmentation Through Through IPSec IPSec Secure Secure Remote Remote User User Two-Factor Two-Factor for for Remote Remote Access and Administrators Managed Managed Source Source Initiatives Initiatives
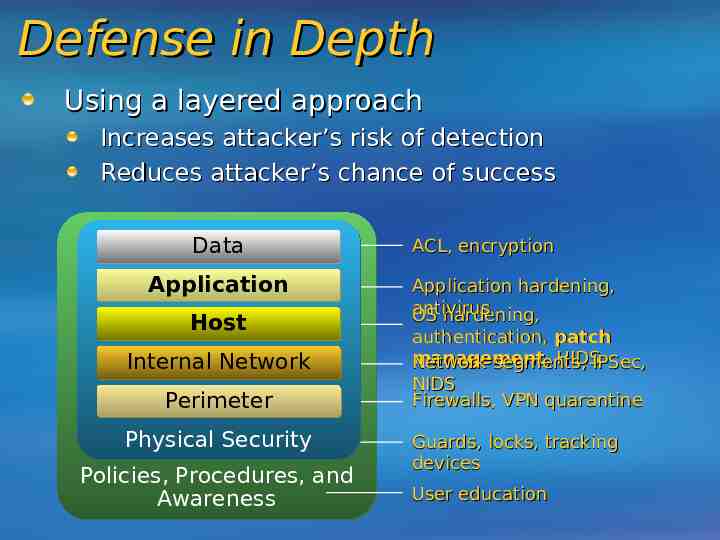
Defense in Depth Using a layered approach Increases attacker’s risk of detection Reduces attacker’s chance of success Data Application Host Internal Network Perimeter Physical Security Policies, Procedures, and Awareness ACL, encryption Application hardening, antivirus OS hardening, authentication, patch management , HIDSIPSec, Network segments, NIDS Firewalls, VPN quarantine Guards, locks, tracking devices User education
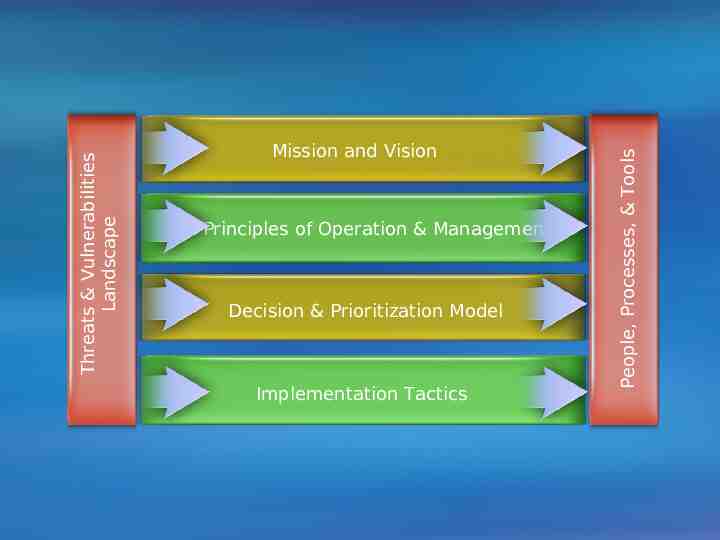
Principles of Operation & Management Decision & Prioritization Model Implementation Tactics People, Processes, & Tools Threats & Vulnerabilities Landscape Mission and Vision
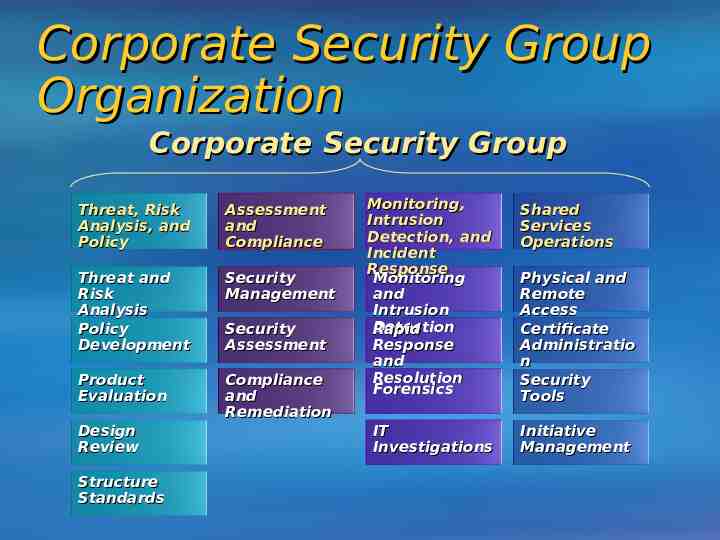
Corporate Security Group Organization Corporate Security Group Threat, Risk Analysis, and Policy Assessment and Compliance Threat and Risk Analysis Policy Development Security Management Product Evaluation Compliance and Remediation Design Review Structure Standards Security Assessment Monitoring, Intrusion Detection, and Incident Response Monitoring and Intrusion Detection Rapid Response and Resolution Forensics IT Investigations Shared Services Operations Physical and Remote Access Certificate Administratio n Security Tools Initiative Management

Processes and Tools Driven (influenced) largely by policies and strategy Common challenges Information security/risk budget normally not covering cost of devising and implementing security processes and tools, in particular, tools required for risk analysis and performance measurement Spreadsheets as database of control status Checklist remains predominantly tool of choice Quality of answers vs completion of checklist questions No linkages to organization’s

Security Readiness Risk management does not guarantee risk elimination Exploits increasingly sophisticated Ready to act, ready to change Education and training Scenarios planning Drills, drills, drills
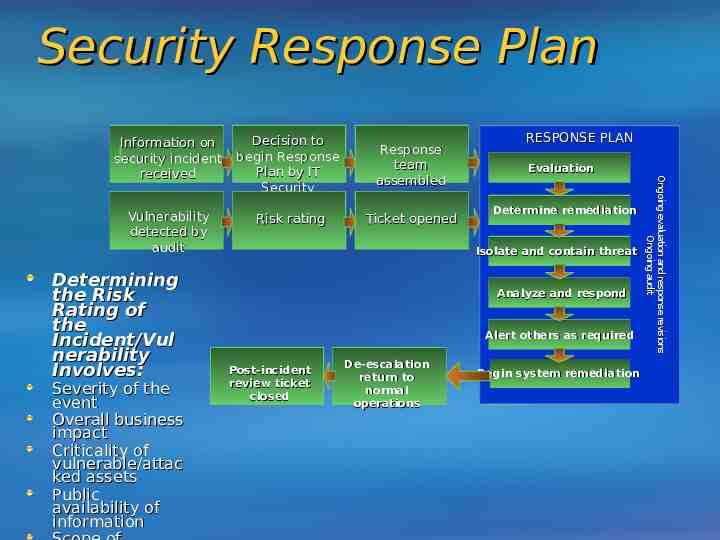
Security Response Plan Decision to begin Response Plan by IT Security Response team assembled Vulnerability detected by audit Risk rating Ticket opened Determining the Risk Rating of the Incident/Vul nerability Involves: Severity of the event Overall business impact Criticality of vulnerable/attac ked assets Public availability of information RESPONSE PLAN Evaluation Determine remediation Isolate and contain threat Analyze and respond Alert others as required Post-incident review ticket closed De-escalation return to normal operations Begin system remediation Ongoing evaluation and response revis ions Ongoing audit Information on security incident received
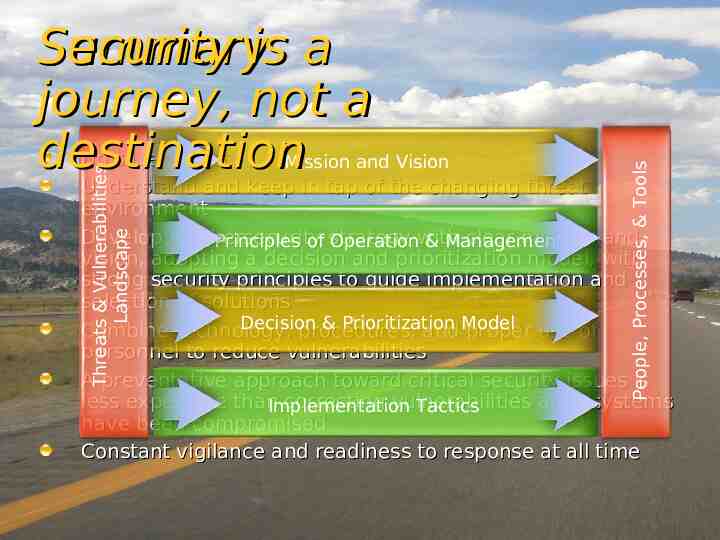
Mission and Vision People, Processes, & Tools Threats & Vulnerabilities Landscape Security is a Summary journey, not a No silver bullet destination Understand and keep in tap of the changing threat environment Develop a cybersecurity clear mission and Principles of strategy Operationwith & Management vision, adopting a decision and prioritization model, with strong security principles to guide implementation and selection of solutions Decision & Prioritization Combine technology, procedures, and Model proper use of personnel to reduce vulnerabilities A preventative approach toward critical security issues is less expensive than correcting vulnerabilities after systems Implementation Tactics have been compromised Constant vigilance and readiness to response at all time

2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.






