Ethics in Violence Research with Vulnerable Populations April 24, 2006
75 Slides222.00 KB

Ethics in Violence Research with Vulnerable Populations April 24, 2006 Sponsored by: Interdisciplinary Center for Research on Violence Criminal Justice Department Office on Protection of Research Subjects University of Illinois at Chicago

Purposes of Seminar To present examples of sensitive practice in research and intervention with vulnerable populations To discuss ethical dilemmas and methods of resolving them To initiate a dialogue about these issues, especially in relation to violence research with vulnerable populations

Panelists Sarah Ullman, Ph.D., Professor of Criminal Justice: Overview of ethical practices & examples from sexual assault research Larry Bennett, Ph.D., Assoc. Professor of Social Work: Human subjects protection in research with domestic violence perpetrators Christine Helfrich, Ph.D., Asst. Professor of Occupational Therapy: Ethical issues in conducting research with domestic violence victims Carl Bell, M. D., Professor of Psychiatry and Public Health: Cultural sensitivity in studying populations exposed to violence Charles Hoehne, Assistant Director, Office for the Protection of Research Subjects: Safeguarding vulnerable populations in research – IRB viewpoints on certificates of confidentiality and mandatory reporting Margaret Luft, Director of Counseling, Life Span Center for Legal Services and Counseling: Research and Service Providers: Can we establish a balance when worlds collide?

Overview of Ethical Practices and Examples from Sexual Assault Research Sarah Ullman Department of Criminal Justice Principal Investigator, UIC Interdisciplinary Center for Research on Violence

What are Vulnerable Populations? Categories include: pregnant women children mentally ill prisoners economically disadvantaged mentally/physically challenged ** Also – victims, offenders, their families/social networks

Weighing Risks vs. Benefits Bias of researcher/IRB vs. those studied Assess Risks: inadequate informed consent, confidentiality, safety concerns for violence survivors, revictimization or retraumatization during the research due to the study Assess Benefits: private, safe disclosure of violence, community resource information, chance to help others, payment etc.

Minimizing Risks Recruitment tailored towards empowerment Consider participatory/collaborative research Going beyond paper/pencil survey methods Pilot testing instruments with victims Avoiding methods/populations that are more likely to retraumatize already vulnerable groups Using feedback from participants to improve sensitivity of research methods/assessments Responding to survivor’s requests if possible Giving back to participants & community

Other Methods to Protect Participants Include: certificates of confidentiality waiving parental consent for children in some cases flexibility in research protocols to maximize participant safety following up with participants to be sure they are safe/to give referrals/get consent on an ongoing basis if relevant

Collaborate with Community/Participants Consider qualitative research or a qualitative component Protect researchers, participants, collaborators – vicarious trauma risks Ask what community needs/wants Develop safety plans Give results back/collaborate in what is published/reported as appropriate Assume you don’t know everything – check in with yourself, your participants, co-researchers etc!

Securing Initial IRB Approval Be patient – IRB should help you to identify biases you may be unaware of and risks you can minimize in your research plans. Do a thorough and complete submission to the IRB of your research study plans. Educate the IRB about your research & population, study team expertise, context of the research, and any information from the field/research documenting your plans are ethical and safe. Get advice from others doing similar research and only do what you have the resources and experience to handle.

Oh No, Not Another Deferral! Violence research is almost always reviewed by the full board and should be. This protects you and your participants. Don’t feel badly when your research initially gets deferred – this is typical, so expect it. Communicate with the IRB and use them as allies. Call the OPRS with questions prior to and/or during the review process with questions, information to help the board etc. Realize sometimes you cannot do exactly what you had planned and try to find another way

Conclusions Research is a learning process and doing violence research is challenging, but important. Learn from your mistakes and those of others and try to do your best to be sure your work is both scientifically and ethically sound. Fully consider perspectives from outside academia, especially those who are and who work with victimized populations.

Human Subjects Protection in Research on Domestic Violence Perpetrators Larry Bennett Jane Addams College of Social Work

Consent, Privacy, & Harm Coercion of batterers and their partners Batterer program v. researchers standards of confidentiality Necessity of partner data v. partner safety Created and detected risks Follow-up v. stalking

Coercion of Batterers and Their Partners Prospect of return to court on a violation may subtly coerce batterers to participate When possible, integrate research tools into agency assessment protocol Partner may be coerced to participate by both batterer and by researcher Fears both participation and non-participation 50% of batterers not with index partner, 20% have new partners

Conflicting Standards of Confidentiality Batterer programs often request waiver of normal conditions of confidentiality Researcher must articulate the differences between programmatic confidentiality and research confidentiality To participants To program staff To advocates affiliated with batterer program

Safety of the Batterer’s Partner(s) Research on batterers usually requires data from partner for reliability Partners are rarely in shelter, therefore at very high risk when providing data Procedures to reduce risk: Establish privacy Funnel questions Debrief

Victim Contact: Always Assume Batterer has full access to her (e)mail Batterer is listening on another phone line Batterer is standing in the room during your phone conversation with victim Batterer will come home during your home interview Batterer will check all her phone logs (Sullivan & Cain, 2004)

Created and Detected Risk Created Risk: threat to victim from the research process research process parallels abuse n 465 women: 20% report partner was listening during a follow-up interview 10% report being questioned about the interview Detected Risk: suicide, threat to victim, child abuse Threat rate: 25 episodes/840 batterers (3%) (Gondolf, 2000)
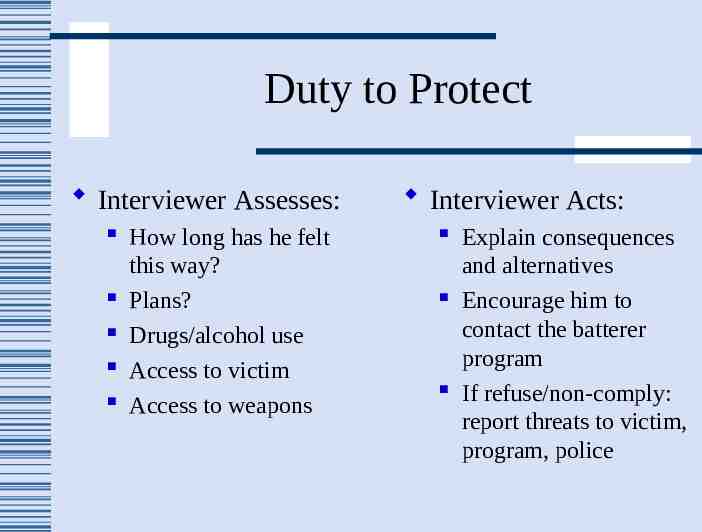
Duty to Protect Interviewer Assesses: How long has he felt this way? Plans? Drugs/alcohol use Access to victim Access to weapons Interviewer Acts: Explain consequences and alternatives Encourage him to contact the batterer program If refuse/non-comply: report threats to victim, program, police

When is Research Follow-up Like Stalking? Follow-up may replicate batterer’s stalking/abuse State coalitions of battered women’s services now train advocates on phone privacy techniques Tracking Protocol, Phone Protocol needed Do not use professional locators

Ethical Issues in Conducting Research with Domestic Violence Victims Christine Helfrich, PhD, OTR/L, FAOTA Department of Occupational Therapy College of Applied Health Sciences

Research Paradigm Principle of justice Need to consult victims and advocates to ascertain risks when designing study Emancipation Paradigm ensures beneficence and includes collaborative data collection methods to improve conditions for those studied

Study Design Study design must ensure safety and sometimes this means needing to alter desired study designs to do so. Sample recruitment and retention is affected by safety issues Abuser knowledge of study participation Abuser/legal system use of study information

Participation – Issues of Power and Coercion Informed Consent process needs to minimize issues of coercion and not re-victimize the participants Incentives should not be coercive and need to maintain confidentiality (ie. Cash or gift cards vs checks) Longitudinal Involvement is desirable; however, safety and dependency issues must be considered

Cultural Congruence Throughout the Research Process Researcher must have cultural competence to go into the community and conduct ethical and effective research. Recruitment and consent process must consider cultural aspects related to ethnicity and race, as well as the culture of the DV community. Issues of power and intimidation need to be carefully considered with this population. Data analyses must consider the biases of where and how data was collected. Dissemination process must carefully consider nonmalfeasance in reporting results.

Ensuring Safety When the Research Itself Engenders Danger Safeguards for physical safety Generic voice mail messages Not identifying study name Blocking caller ID Pre-established code words to determine if safe to talk Not leaving messages Not giving out specific information regarding study to unknown callers Resources for emotional/psychological safety Established relationships with DV agencies, Crises line phone numbers, Referral sources

Cultural Sensitivity in Studying Populations Exposed to Violence Carl C. Bell, M.D., F.A.P.A., F.A.C.Psych. C.E.O./President: Community Mental Health Council, Inc. Professor of Psychiatry, Professor of Public Health, University of Illinois [email protected]

Ethnocentric Multiculturalism This aspect of Euro-American culture makes it difficult to appreciate cultural differences between different ethnic groups. This aspect of Euro-American culture makes it difficult to appreciate diversity within racial groups.

Ethnocentric Monoculturalism An example is the food pyramid graphic recommended by the U. S. Department of Agriculture which has milk and dairy products as a consumer’s only source of calcium. Lactose intolerance occurs in: 70% of African Americans 90% of Asian Americans 74% of Native Americans 53% of Mexican Americans Only 15% of Whites are lactose intolerant

Racism Racism is the practice of racial discrimination, segregation, persecution, and domination based on a feeling of racial differences or antagonisms; especially with reference to supposed racial superiority, inferiority, or purity.

Oppressed/Oppressor Relationships In any effective and efficient submissiondominance system, it is critical for the oppressor to monopolize the perception of the victim. One is victimized in proportion to the quality of space, time, energy, and mobility that one must yield or has yielded to the oppressor. Conversely, the more one regains or commands control of these elements the less one is victimized.
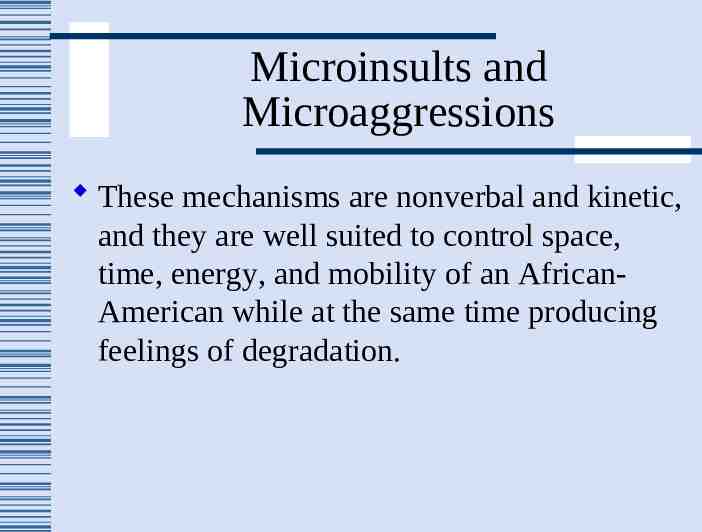
Microinsults and Microaggressions These mechanisms are nonverbal and kinetic, and they are well suited to control space, time, energy, and mobility of an AfricanAmerican while at the same time producing feelings of degradation.

Violence in Different Ethnic Groups - General In most murder cases involving a white or black victim, the offender was of the same race of the victim. Poverty and social infrastructure account for the vast differences in rates of violence between AfricanAmericans and Whites. African-American rates are six times & Latino rates are 2.3 times the Native America, Asian, & White rates of homicide.

Violence in Different Ethnic Groups - African-American Interpersonal Altercation violence is a major from of violence occurring in the AfricanAmerican community Domestic homicide continues to be a problem in the African American community, but African-American women are no longer killing more African American men than vice versa.

Violence in Different Ethnic Groups - Latino Gang-related violence is a major form of violence occurring in the Latino community Latino men are not known to perpetrate domestic homicide. Latino men tend to perpetuate violence in the street and, while gun violence predominates, there is a greater use of knifes.

Violence in Different Ethnic Groups - Native American Interpersonal altercation violence is a major form of violence in the Native American community. Forty percent of Native American murder victims were killed by an offender who was not Native American In 33% of the cases the offender was white.

Violence in Different Ethnic Groups – Euro-American Suicide is a major form of violence occurring in the Euro-American community Euro-Americans are the majority of offenders in Anger/revenge & Domestic/romantic related mass murder In Anger/revenge & Domestic/romantic related mass murder there is a significant suicide dynamic
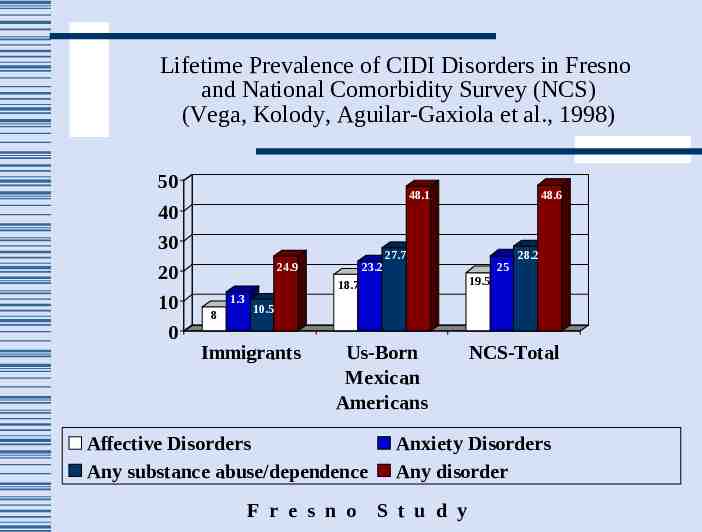
Lifetime Prevalence of CIDI Disorders in Fresno and National Comorbidity Survey (NCS) (Vega, Kolody, Aguilar-Gaxiola et al., 1998) 50 40 30 20 10 0 48.1 24.9 1.3 8 23.2 48.6 27.7 25 28.2 18.7 19.5 Us-Born Mexican Americans NCS-Total 10.5 Immigrants Affective Disorders Any substance abuse/dependence F r e s n o Anxiety Disorders Any disorder S t u d y
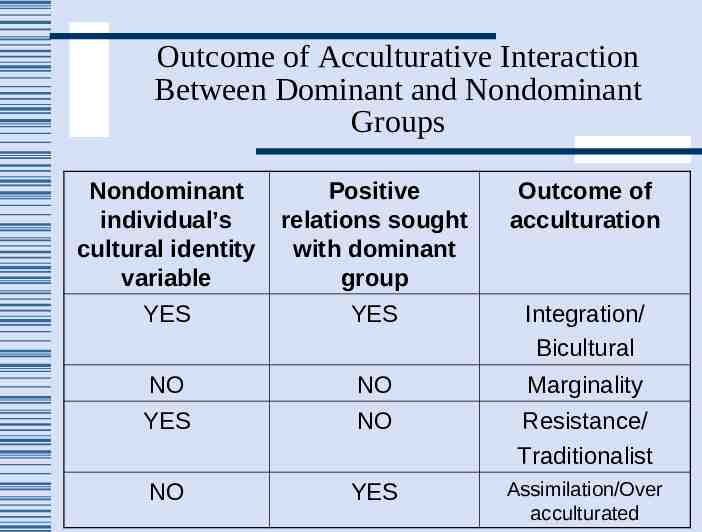
Outcome of Acculturative Interaction Between Dominant and Nondominant Groups Nondominant individual’s cultural identity variable Positive relations sought with dominant group Outcome of acculturation YES YES Integration/ Bicultural NO NO Marginality YES NO Resistance/ Traditionalist NO YES Assimilation/Over acculturated

African-Based Populations Pre-slavery Africans in America Africans in America subjected to various degrees of slavery Recent African Immigrants in America Recent African Refugees in America

Racism In Research The history of research efforts in disadvantaged communities provides sufficient evidence of the ways in which African Americans have been exploited by both medical and research interventionists.

Racism in Psychiatry G. Stanley Hall also declared that the medical treatment of the races was a different "as the application of veterinary medicine for horses is from that applied to the oxen".

Racism in Psychiatry Carl Gustav Jung noted "The different strata of the mind correspond to the history of the races" and that the Negro "has probably a whole historical layer less" than the white man.

Racism in Psychiatry Another example of the racist use of race in psychiatry can be found in Lauretta Bender's work on "Behavior Problems in Negro Children" (1939). She noted that the two most distinguishing characteristics of Negro children were their ability to dance and their capacity for laziness.

Safeguarding vulnerable populations in research – IRB viewpoints on certificates of confidentiality and mandatory reporting Charles Hoehne Assistant Director, Office for the Protection of Research Subjects

What Defines a “Vulnerable Population”? Belmont Report: “Respect for Persons” - Persons with diminished autonomy are entitled to protection Research implications: Acknowledge autonomy Protect those with diminished autonomy

What Defines a “Vulnerable Population”? Belmont Report: “Justice”: One special instance of injustice results from the involvement of vulnerable subjects. Certain groups, such as racial minorities, the economically disadvantaged, the very sick, and the institutionalized may continually be sought as research subjects, owing to their ready availability in settings where research is conducted. Given their dependent status and their frequently compromised capacity for free consent, they should be protected against the danger of being involved in research solely for administrative convenience, or because they are easy to manipulate as a result of their socioeconomic condition.

What Defines a “Vulnerable Population”? Examples of “vulnerable populations” commonly seen by the IRB: Students (UIC Psychology Subject Pool, Use of Classroom Time, Teachers recruiting their own students, for example) Employees Children Pregnant Women Wards Individuals with diminished/diminishing capacity Individuals with service needs (health, social services, etc) Economically disadvantaged Racial minorities Prisoners

Protection of Vulnerable Populations (as per 45 CFR 46) Subpart A: Basic Protection for all Human Subjects Subpart B: Additional Protections for Pregnant Women, Human Fetuses, and Neonates Subpart C: Additional Protections for Prisoners Subpart D: Additional Protections for Children

Protection of Vulnerable Populations (as per 45 CFR 46) Sometimes additional safeguards above and beyond Subparts A-D are required to satisfy 45 CFR 46.111(1): “Risk to subjects are minimized: (i) by using procedures which are consistent with sound research design and which do not unnecessarily expose subjects to risk, ” Example: Certificate of Confidentiality AKA: Section 301(d) of the Public Health Service Act [42 U.S.C. 241(d)]

Certificate of Confidentiality Issued by the National Institutes of Health (NIH) DHHS Secretary may authorize persons engaged in: a) b) Protects investigators and institutions from involuntary release of “identifying information” in any: a) b) c) d) Biomedical, Behavioral, Clinical, Other Research To protect the privacy of individuals who are the subjects of that research. Civil Criminal Administrative Federal, state or local legislative, or other proceeding Protection is not limited to federally supported research

Certificate of Confidentiality Research studies eligible for a Certificate must: Have IRB approval; Involve collection of identifying information; and Disclosure could have adverse consequences for subjects or damage their financial standing, employability, insurability, or reputation.

Certificate of Confidentiality NIH Requirements: Informed consent document must explain the Certificate’s protections, including a fair and clear explanation of the limitations and exceptions; PI must submit documentation of IRB approval PI must submit a copy of the IRB-approved informed consent document; PI and Institutional Official (Vice-Chancellor for Research, or his designee) must sign the application; cont.

Certificate of Confidentiality NIH Requirements (cont): PI must agree to protect against involuntary disclosure and to support and defend the authority of the Certificate against legal challenges; PI must agree to comply with federal regulations protecting human subjects; and PI must agree not to represent the Certificate as an endorsement of the research by DHHS or NIH.

Certificate of Confidentiality Boundaries of Protection: Goes into effect on date Certificate is granted Permanently protects identifiable data obtained during any time the Certificate is in effect Does not protect against voluntary disclosure: a) b) c) d) Child abuse Threat of harm to self or others Reportable communicable diseases Subjects own disclosure

Why don’t more PI’s obtain Certificates? Lack of familiarity Misconception that Certificates apply only to “criminal” behavior Perceived low risk-benefit ratio: a) b) What is likelihood of a subpoena? Takes too long (IRB process 30-45 days)

Mandated Reporting and the IRB RememberA Certificate of Confidentiality does not “trump” mandated reporting requirements!

Mandated Reporting and the IRB What is the IRB looking for?* PI should address mandated reporting in the application and informed consent document if there is a reasonably likelihood that abuse and/or neglect will be discovered. *Charles Hoehne does not speak for any or all of the UIC IRB’s.

Mandated Reporting and the IRB Assent and Parental Permission Issues PI’s want to consider/address in their applications for IRB review: a) b) c) d) Will a child understand the concept? Will a “warning” in the assent document decrease the likelihood that the child will report? Will a “warning” in the assent document increase the likelihood that the child will report? Will a “warning” in the parental permission document keep abusive parent from permitting the child to participate? If so, what are the implications? Question: Who are we trying to protect? The child? The parent? The Investigators? The IRB? The Institution? All?

Mandated Reporting and the IRB Question: Is the following language in the UIC Informed Consent Document template sufficient?: “No information about you, or provided by you during the research, will be disclosed to others without your written permission, except: a) if necessary to protect your rights or welfare , or b) if required by law.” Answer: No, not if revelation of abuse or neglect is likely. Suggestion: Please carefully review the assent/consent/parental permission documents to make sure there is no contradictory information regarding confidentiality.
References/Resources: Link to DHHS: http://www.hhs.gov/ohrp/ DHHS link to 45 CFR 46: Http://www.hhs.gov/ohrp/humansubjects/guidance/45cfr46.htm DHHS Guidance on Certificates of Confidentiality: http://www.hhs.gov/ohrp/humansubjects/guidance/certconf.htm NIH Certificates of Confidentiality Kiosk: http:// grants.nih.gov/grants/policy/coc/index.htm NIH Certificates of Confidentiality Slide Presentation: http://www.grants.nih.gov/grants/policy/coc/slides 020503/sld002.htm UIC Office for the Protection of Research Subjects: http://tigger.uic.edu/depts/ovcr/research/protocolreview/irb/index.shtml (Phone: 312-996-1711)
Template Language for Informed Consent Document if a Certificate will be obtained Required Language: To help us protect your privacy, we have obtained a Certificate of Confidentiality from the National Institutes of Health. With this Certificate, the researchers cannot be forced to disclose information that may identify you, even by a court subpoena, in any federal, state, or local civil, criminal, administrative, legislative, or other proceedings. The researchers will use the Certificate to resist any demands for information that would identify you, except as explained below. The Certificate cannot be used to resist a demand for information from personnel of the United States Government that is used for auditing or evaluation of Federally funded projects or for information that must be disclosed in order to meet the requirements of the federal Food and Drug Administration (FDA). You should understand that a Certificate of Confidentiality does not prevent you or a member of your family from voluntarily releasing information about yourself or your involvement in this research. If an insurer, employer, or other person obtains your written consent to receive research information, then the researchers may not use the Certificate to withhold that information. cont.

Template Language for Informed Consent Document if a Certificate will be obtained Required language (cont): Researchers should include language such as the following if they intend to make voluntary disclosure about things such as child abuse, intent to hurt self or others, or other voluntary disclosures The Certificate of Confidentiality does not prevent the researchers from disclosing voluntarily, without your consent, information that would identify you as a participant in the research project under the following circumstances: [The researchers should state here the conditions under which voluntary disclosure would be made. If no voluntary disclosures will be made, the researchers should so state.] cont.

Template Language for Informed Consent Document if a Certificate will be obtained Required language (cont): Certificates of Confidentiality protect subjects from compelled disclosure of identifying information but do not prevent the voluntary disclosure of identifying characteristics of research subjects. Researchers, therefore, are not prevented from voluntarily disclosing certain information about research subjects, such as evidence of child abuse or a subject's threatened violence to self or others. However, if a researcher intends to make such voluntary disclosures, the consent document must clearly indicate this. Furthermore, Certificates of Confidentiality do not prevent other types of intentional or unintentional breaches of confidentiality. As a result, investigators and IRBs must ensure that other appropriate mechanisms and procedures are in place to protect the confidentiality of the identifiable private information to be obtained in the proposed research.

Research and Service Providers: Can we Establish a Balance when Worlds Collide? Margaret Luft Director of Counseling, Life Span Center for Legal Services and Counseling

Everybody Wants to Know What Works (Efficacy) But success is defined differently depending on where people start, AND Research is often used to validate a belief about what is right rather than to discover what is true.

Identify Distinct Constituencies How you define success depends on who is asking the evaluative questions: Elected officials Private donors Corporate sponsors Service providers Client consumers

Elected Officials Accountable to the general public Stewards of the public purse Need to see progress now Balancing competing interests Money has to be renewed every year Efficacy Measurable outcomes

Private Donors Guided by specific mission Time limited commitments Concerned with sustainability Efficacy Measurable outcome Efficacy Legacy

Corporate Sponsors Want brand name to be associated with a “winner” Good Public relations in community Efficacy Improving image with customers and employees; Efficacy Spread the brand name.

Service Providers Guided by mission to help Need to find money continuously for operations Overwhelmed with volume and scope of client needs Barrage of demand from all funders to justify continuation of services Formal evaluations frequently validate what they already know Research money competes with services’ funding Efficacy continuing services, client satisfaction

Client Consumers Want relief in crisis Want future to be better than the past Know what works or does not work for them Have been told what they “should” do by everyone; (if it were that simple, they would already be doing it) Discouraged by the lack of tangible help Display cynicism about formal research, because it often fails to provide immediate relief or to produce the long term change necessary to improve the future Efficacy improvement in life circumstances and increase in personal sense of accomplishment

How can Research Balance these Different Definitions of Efficacy? Government vs Private “sustainability” Funders vs Clients “who pays? who consumes?” Providers vs Funders “Process/Product” Deliverables vs Impact “counting things vs. measuring outcomes” Big picture vs One-person-at-a-time “at what level does lasting change occur?”

Service Provider Perspective Push of funders “Do more with less” Pull of clients “Help me out of this mess”






