Cyber Threat to Critical Infrastructure Mike Lettman Chief
36 Slides4.36 MB

Cyber Threat to Critical Infrastructure Mike Lettman Chief Information Security Officer State of Arizona

Why Cyber? “There is no such thing as a cyber emergency, there are only emergencies caused by many things. In order to declare a state of emergency you need to have kinetic affects, threats to health and public safety” Many things can cause an emergency: nature, man made, cyber, accident, malfunction Major General Michael McGuire TAG State of Arizona

Headlines Ukraine says Russian cyber attacks targeted its main airport Jihadists in the West are taught to DERAIL trains and target stations in chilling new al-Qaeda terror guide that includes lists of 'vulnerable' US rail routes FBI and Homeland Security launch probe as foreign cyber attackers target U.S. water supply

What Could Go Wrong? What if? Road Energy Sirens Water Telecom Transportation Dams

What did go Wrong? History of cyber and physical Sept 2007 Nov 2007 Jan 2014 Dec 2015 Oct 2016 April 2017 May 2017 June 2017 DHS Generator Natanz nuclear power North Carolina Ukraine power grid IOT attack on DYN Dallas sirens WannaCry ransomware Notpetya ransomware Maersk

Who and How Who Hacktivists – Anonymous, WikiLeaks Insiders – Snowden Criminals – Individuals, gangs, groups Terrorist – ISIL, al-Queda Nations – US, China, Russia, Israel, Iran How SQL injection BotNet Phishing Social Media Infected Websites

Why is there concern? Why - Attacks Cyber Investigations 15/Day Trojan Attempts 3000/Day SQL Injection 50/Day SPAM 100K/Day Web Activity 8.3M/Month Why - Cost 2016 there was 1093 breaches 36,601,939 records 19,699,094 ssns 7,472,540 credit cards @ 250 9,150,484,750 cost to organizations
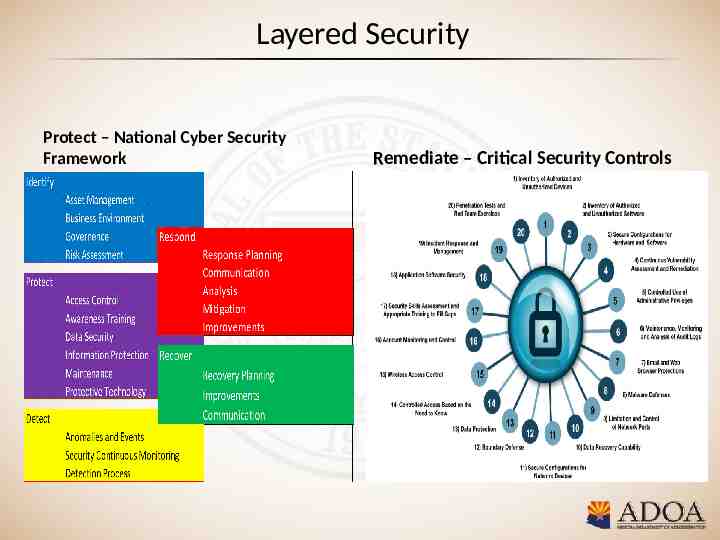
Layered Security Protect – National Cyber Security Framework Remediate – Critical Security Controls

Municipal and Small Business Cyber Impacts Tina Slankas Deputy Director, City of Phoenix Office of Homeland Security & Emergency Management

Community Impact of Cyber Click to add text
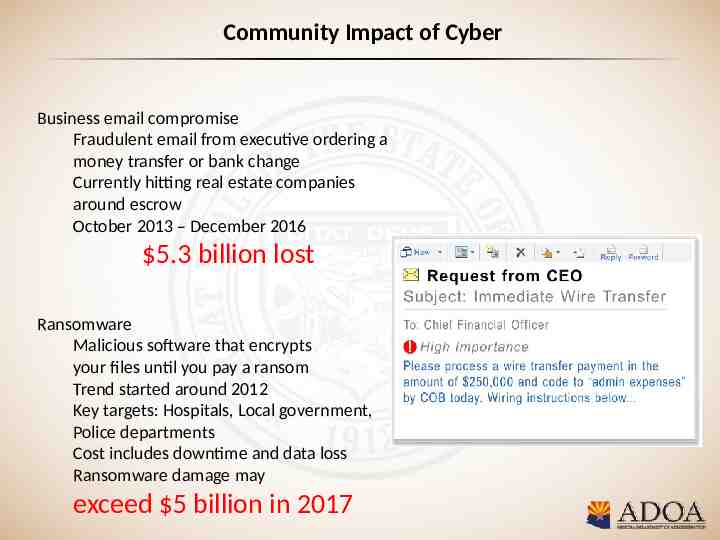
Community Impact of Cyber Business email compromise Fraudulent email from executive ordering a money transfer or bank change Currently hitting real estate companies around escrow October 2013 – December 2016 5.3 billion lost Ransomware Malicious software that encrypts your files until you pay a ransom Trend started around 2012 Key targets: Hospitals, Local government, Police departments Cost includes downtime and data loss Ransomware damage may exceed 5 billion in 2017
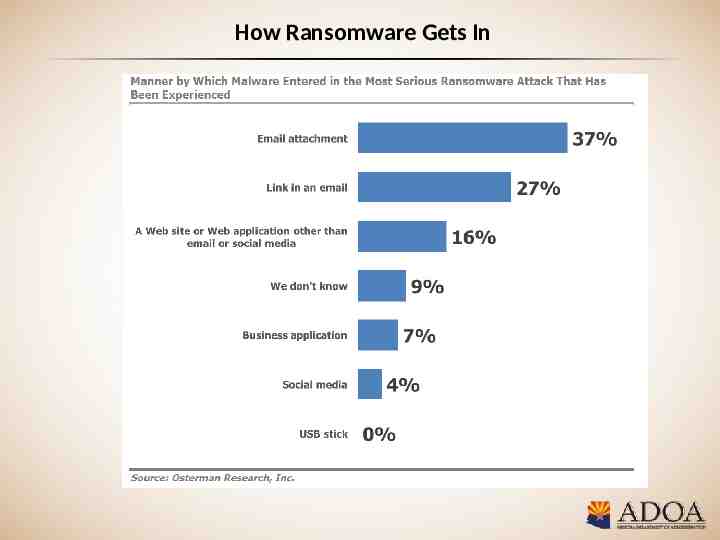
How Ransomware Gets In
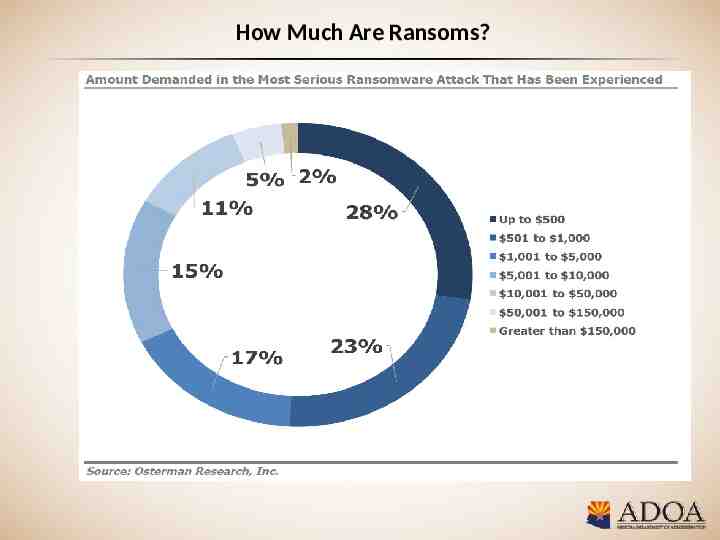
How Much Are Ransoms?

Impacts to Small Business The World Economic Forum classifies cybercrime as a “Top Global Risk”. 85% of business assets are in digital form Small businesses are a target. – Easy target for cybercriminals. – Systems as a secret doorway into their corporate partners’ networks. – Experience a higher proportion of cybercrime costs – Experience the disruptive effects of data breaches both immediately and in the long term Last year alone over 430 million new versions of malware launched on the open web Any device connected to the Internet can be hacked. – – – – Devices offer hackers quick access to businesses’ data through unsecured Wi-Fi networks Compromised IoT devices and turn them into “bots” to use in future attacks Adequate security protocols do not yet exist Over 75% of all cyberattacks target known vulnerabilities

Costs of Cybercrime In 2015 cyber attacks cost businesses as much as 400 billion a year From 2013 to 2015 the cyber crime costs quadrupled Projected to quadruple from 2015 to 2019 Cost of data breaches will increase to 2.1 trillion globally by 2019 The average cost of one cyber breach – – 4 million globally 7 million in the United States One cyberattack can result in millions of dollars in expenses: – – 30 days to contain a cyberattack, the average cost is 7.7 million 90 days, the average cost is 12.2 million Immediate costs: Customer breach notifications Post breach customer protection Regulatory compliance fines Public relations/crisis communications Attorney fees and litigation Technical investigations Loss of customer trust Disruption of normal business operations Immediate financial losses Long term costs: Increase in insurance premiums Operational disruptions Lost value in customer relationships Value of lost contract revenue Devaluation of trade name Loss of intellectual property Loss of future business contracts and relationships

Cyber Threats to Private Industry Financial Services Michael Kirby II Head of FIS Risk and Cybersecurity Product Strategy 9/11/2017
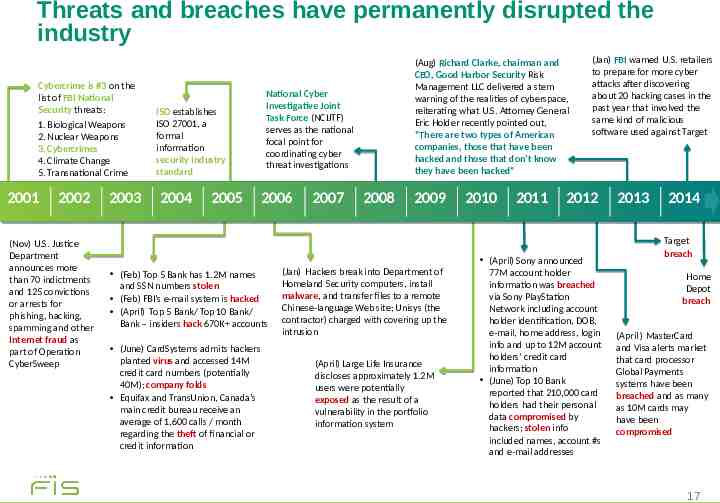
Threats and breaches have permanently disrupted the industry Cybercrime is #3 on the list of FBI National Security threats: 1. Biological Weapons 2. Nuclear Weapons 3. Cybercrimes 4. Climate Change 5. Transnational Crime 2001 2002 (Nov) U.S. Justice Department announces more than 70 indictments and 125 convictions or arrests for phishing, hacking, spamming and other Internet fraud as part of Operation CyberSweep 2003 ISO establishes ISO 27001, a formal information security industry standard 2004 2005 National Cyber Investigative Joint Task Force (NCIJTF) serves as the national focal point for coordinating cyber threat investigations 2006 (Feb) Top 5 Bank has 1.2M names and SSN numbers stolen (Feb) FBI's e-mail system is hacked (April) Top 5 Bank/ Top 10 Bank/ Bank – insiders hack 670K accounts (June) CardSystems admits hackers planted virus and accessed 14M credit card numbers (potentially 40M); company folds Equifax and TransUnion, Canada’s main credit bureau receive an average of 1,600 calls / month regarding the theft of financial or credit information (Aug) Richard Clarke, chairman and CEO, Good Harbor Security Risk Management LLC delivered a stern warning of the realities of cyberspace, reiterating what U.S. Attorney General Eric Holder recently pointed out, “There are two types of American companies, those that have been hacked and those that don’t know they have been hacked” 2007 2008 2009 (Jan) Hackers break into Department of Homeland Security computers, install malware, and transfer files to a remote Chinese-language Web site; Unisys (the contractor) charged with covering up the intrusion (April) Large Life Insurance discloses approximately 1.2M users were potentially exposed as the result of a vulnerability in the portfolio information system 2010 2011 (Jan) FBI warned U.S. retailers to prepare for more cyber attacks after discovering about 20 hacking cases in the past year that involved the same kind of malicious software used against Target 2012 (April) Sony announced 77M account holder information was breached via Sony PlayStation Network including account holder identification, DOB, e-mail, home address, login info and up to 12M account holders’ credit card information (June) Top 10 Bank reported that 210,000 card holders had their personal data compromised by hackers; stolen info included names, account #s and e-mail addresses 2013 2014 Target breach Home Depot breach (April ) MasterCard and Visa alerts market that card processor Global Payments systems have been breached and as many as 10M cards may have been compromised 17

2016 Community analysis IBM: Security trends in the financial services sector – Financial Services customers had 65% more events than other industries · up 29% from 2015 – Threat actors 94% External, 6% Internal – Data compromised 71% Credentials, 12% Payment, 9% Personal VZN DBIR – 75% “Outsiders”, 25% “Internal actors”. – Focus: Vulnerabilities, Phishing, Credentials Dimension Data (2016 report) – Spear-phishing 17% of 2015 incidents, up from 2% in 2014 · Brute Force up (2% 7%), DDoS down (4% 3%), Malware up (2% 5%) – Geographical shift: more US now – End-point security remains a key weakness 18

2016 Cybersecurity Trends Motivations and attacks Denial of Service (DoS/DDoS): Extortion, Fun, Punishment, Competition Ransomware: Extortion, some Punishment Data Theft: Sales, Espionage, Identity Theft, Fun, Embarrassment Credential Theft: Sales of credentials, credential reuse, password list aggregation Botnets: DDoS, Bitcoin mining, Spam, illegal storage 19

Defense Challenges Endpoint control weak (patch, behavioral) – Polymorphism and the demise of signature-based defense – SWIFT: weak banks, long-term recon No silver bullets – Each layer has weaknesses IOCs growing at alarming rate – High volume of threat data and indicators is difficult to manage Credentials (reused, weak) – Cannot alert on password attacks if they use the right password Strategic challenges – Bigger, more complex customers need bigger, more complex solutions – Regulatory and industry standard changes – Changing threat landscape (Ransomware changes) 20

Aggregated Defense Recommendations Community analysis IBM – Training and employee awareness – Proprietary Email and IAM solutions – Augmented cyber security intelligence VZN DBIR – (Vulnerabilities) Targeted methodical patching, mitigation, scanning – (Phishing) Filter email, awareness training, segmentation, strong AAA, Monitor outbound traffic – (Credentials) Strong unique passwords – (Web App) MFA for critical apps, validate input, patch platforms and third party plugins · interesting. focus on the web app, not how to protect from the web app Dimension Data – Effective patch management – Social engineering (phishing) training – Endpoint protection / detection – Threat intelligence – Ad-blocking software – IP reputation 21
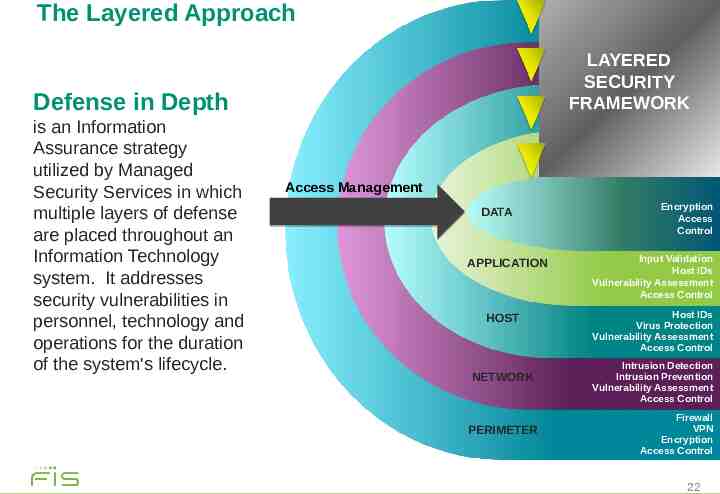
The Layered Approach LAYERED SECURITY FRAMEWORK Defense in Depth is an Information Assurance strategy utilized by Managed Security Services in which multiple layers of defense are placed throughout an Information Technology system. It addresses security vulnerabilities in personnel, technology and operations for the duration of the system's lifecycle. Access Management DATA APPLICATION HOST NETWORK PERIMETER Encryption Access Control Input Validation Host IDs Vulnerability Assessment Access Control Host IDs Virus Protection Vulnerability Assessment Access Control Intrusion Detection Intrusion Prevention Vulnerability Assessment Access Control Firewall VPN Encryption Access Control 22

Example: Defense in Depth More recent trending Google OATH Phishing Campaign (May 2017) – Phishing attack, appeared to be Google Docs sharing from known Google contacts – Sent to 736 customers 702 blocked by Email Gateway due to invalid recipients, SPAM, or trending SPAM. · 30 delivered but ignored/deleted by users · 4 users clicked the bait but denied access due to “Unclassified” blocking. · 0 infected endpoints found · Google took immediate action to protect users, including removing the fake Google Docs pages and disabling the offending accounts.
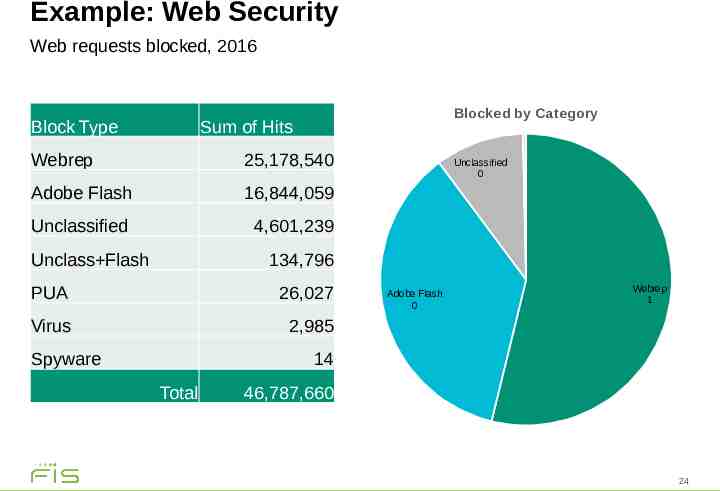
Example: Web Security Web requests blocked, 2016 Block Type Blocked by Category Sum of Hits Webrep 25,178,540 Adobe Flash 16,844,059 Unclassified 4,601,239 Unclass Flash Unclassified 0 134,796 PUA 26,027 Virus 2,985 Spyware Adobe Flash 0 Webrep 1 14 Total 46,787,660 24

2016 FIS and/or its subsidiaries. All Rights Reserved. FIS confidential and proprietary information.

Cyber Resources Owen Zorge State Compliance and Privacy Officer

Federal Cyber Resources US Department of Homeland Security – Stop. Think. Connect. www.dhs.gov/stopthinkconnect October is National Cyber Security Awareness Month – Weekly Themes Toolkits: Students, Parents and Educators, Professionals, Older Americans, Government, Industry, Small Business, Law Enforcement – US Computer Emergency Readiness Team (US-CERT) www.us-cert.gov Strives for safer, stronger Internet for all Americans by responding to major incidents, analyzing threats, and exchanging critical cybersecurity information with trusted partners. – Ready.Gov Planning Ahead for Disasters

National Cyber Resources Information Sharing and Analysis Centers (ISAC) – National Council of ISACs www.nationalisacs.org – Sector-based ISACs that collaborate with each other across private and public sector critical infrastructure. Automotive, Aviation, Communications, Defense Industrial Base, Electricity, Emergency Management, Financial, Healthcare, Multi-State, Transportation, Water, and others.

Local Cyber Resources Arizona Infragard – http://azinfragard.org – Mission: to help protect Arizona’s infrastructure by supporting the priorities of the FBI; to cultivate partnerships with public and private sectors through bi-directional sharing of actionable information, training and educational events. Arizona Cyber Threat Response Alliance (ACTRA) – http://azinfragard.org/?page id 8 – Mission: The hub for collaborative cyber information sharing in a neutral environment of trust where partners from industry, academia, law enforcement, and intelligence come together Arizona Counter Terrorism Information Center (ACTIC) – www.azactic.gov , 1-877-2-SAVE-AZ – The ACTIC is a joint effort between the Arizona Department of Public Safety, Arizona Department of Homeland Security , Federal Bureau of Investigation, and other participating agencies providing both intelligence, investigative and technical support to state, local, tribal and federal law enforcement agencies as well as other agencies critical to Arizona and the country’s homeland security efforts.

Cyber Resources – Best Practices National Institute of Standards and Technology (NIST) – www.nist.gov – NIST Cybersecurity Framework www.nist.gov/cyberframework Identify, Protect, Detect, Respond, Recover NIST Special Publications (SP) – 800-53 Rev 4, Security and Privacy Controls Other Cybersecurity Frameworks – International Standards Organization (ISO) 27001 / 27002 www.iso.org/isoiec-27001-information-security.html – Control Objectives for Information and Related Technology (COBIT) www.isaca.org/Cobit

Information Privacy Health Insurance Portability and Accountability Act (HIPAA) – www.hhs.gov/hipaa/index.html – Do you process any Protected Health Information (PHI)? Payment Card Industry Data Security Standard (PCI DSS) – www.pcisecuritystandards.org – Do you process or store any Payment Card information? Personally Identifiable Information (PII) – NIST SP 800-122 www.nist.gov/publications/guide-protecting-confidentiality-personally-identifiable-i nformation-pii – Do you process or store SSNs, Date of Birth, etc.?

What You Can Do – As Leaders Demonstrate active support for cybersecurity – – – – Create a culture of cyber security Emphasize its importance (tone at the top) Resource it appropriately (budget and people) Chat regularly with your CISO Discuss the organization’s current security posture, threats and risks, and needs Follow processes and security safeguards – Be a good example Don’t circumvent processes (that’s how business email compromises occur) Don’t post/share passwords

Call to Action Complete Cyber Security Awareness Training Identify Essential Functions? – – – – – What are the core functions under normal conditions? What is your processes for providing your services? Are functions documented and written in a clear description for readers? Estimation of personnel and Vital Records or Resources for each function? Have the functions been sorted by Tiers and Prioritized? Do you have a plan? – What are you going to do? – Who are you going to call? – What resources do you have available? Monthly Exercises – Can organization function for 1 hour without tech? No computers No internet No databases

Top Ways to Prevent Cyber Attacks Don’t click – on ANYTHING – Unexpected email attachments – Links in email messages – even if they promise tantalizing pictures! – Ads on websites (banner ads, ones on the sides of pages ) Ensure your anti-malware software is running and up-to-date – Set it to automatically update Apply all software updates/security patches when released – Set your PC to automatically update Use a strong, unique password

Questions Owen Zorge State Compliance Officer Mike Lettman Chief Information Security Officer Arizona Department of Administration [email protected] ADOA.az.gov Tina Slankas Deputy Director, Office of Homeland Security & Emergency Management Michael Kirby Head of FIS Risk and Cybersecurity Product Strategy, FIS 36