An NFV Orchestration Framework for Interference-free Policy
25 Slides1.26 MB

An NFV Orchestration Framework for Interference-free Policy Enforcement Xin Li, Chen Qian University of Kentucky

Network Function Network Function A.k.a. Middlebox Networking device that perform functions other than packet forwarding Build in proprietary hardware

Network Function Security Network Function Firewall IDS Acceleration Network Function WAN Optimizer Proxy

Policy Chain Http Firewall IDS Proxy Non http Firewall Correctness: sequential order Efficiency: not traverse unnecessary ones

Network Functions Placement Policy chain Http Firewall Proxy IDS Placement not easy to re-deploy Firewall Proxy S2 S1 S3 S4

Placement: Hardware Network Functions Traffic Steering Simple [Sigcomm’13] Firewall IDS Policy Chain: Http Firewall S1 IDS Proxy S2 Dst Image from https://users.ece.cmu.edu/ vsekar/slides/sigcomm13 simple.pptx Proxy

Drawbacks of Traffic Steering Modified routing path Conflicting with other applications e.g. Traffic engineering Additional path length more latency, bandwidth Complex routing rules More forwarding table entries Loop Additional mechanism (e.g. tag)

Network Functions Virtualizaiton IDS WAN Optimizer Hardware Software More flexible and cheaper New opportunity: interference-free policy enforcement Virtual Network Function (VNF) Proxy

NFV Orchestration Framework Core idea Network Functions are contained in VMs for isolation. Places the required VNFs on the path of each traffic flow o Not changing routing path

Challenges Resource-efficient way to place VNFs while enforcing policies. Optimization problem Traffic is highly dynamic. Fast failover Scale in/out

Framework Overview Policy Traffic 1k 0.5 k Path . 1k http FW Proxy 0.5 k SDN controller Resource Orchestrator Optimization Engine Dynamic Handler App1 App2 . Rule Generator vSwitch Opt Engine output asas input outputs from diffEngine: apps input Core. Co-exist with other apps Inputs to Opt Hosts VNFs Take Take Fast failover if overloaded Install VNFs& inavailable APPLE hosts Generate routing rules & vsw) normal appspec. from SDN controller’s view Flow rsc. Once overloaded, send ntf.(sw to Dyn. Hdl.

Framework Overview Policy Traffic 1k 0.5 k . 1k http FW Proxy 0.5 k Resource Orchestrator SDN controller Optimization Engine Dynamic Handler vSwitch Path App1 Rule Generator App2 .
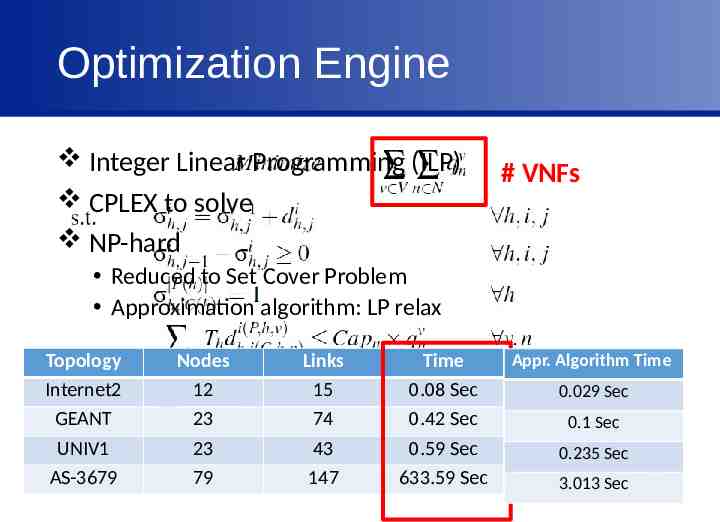
Optimization Engine Integer Linear Programming (ILP) CPLEX to solve NP-hard # VNFs Reduced to Set Cover Problem Approximation algorithm: LP relax Topology Internet2 GEANT UNIV1 AS-3679 Nodes 12 23 23 79 Links 15 74 43 147 Time 0.08 Sec 0.42 Sec 0.59 Sec 633.59 Sec Appr. Algorithm Time 0.029 Sec 0.1 Sec 0.235 Sec 3.013 Sec

Framework Overview Policy Traffic 1k 0.5 k . 1k http FW Proxy 0.5 k Resource Orchestrator SDN controller Optimization Engine Dynamic Handler vSwitch Path App1 Rule Generator App2 .

Dynamic Handler Firewall IDS Policy Chain: Dynamic Handler New FW IDS FW IDS Install new Initiate new VM forwarding rules 2 vSwitch 1 2 3 2 3 vSwitch 1 Using ClickOS: lightweight S1 ingress S2 S3 S4 egress Overload notification

Implementation Core: Stand-alone REST API XEN VMs can’t be connected to OpenVswitch directly Resource Orchestrator ClickOS Linux-br ClickOS Network Controller

Prototype Emulation Dynamic Handler overload roll back New FW Failover IDS 2 vSwitch 1 FW 2 3 Mater IDS 2 3 vSwitch 1 Orginal Path S1 ingress S2 S3 S4 egress Failover Path

Simulation Evaluation Methodology The input to Optimization Engine is the average traffic matrix. See the performance of APPLE with time-varying traffic matrix.

Simulation Evaluation Topologies Campus network, enterprise network, data center Network Functions Each host have 64 cores 4 network functions (FW, IDS, Proxy, IDS) Different core # requirement and capacity Policy Synthesize network policy chains
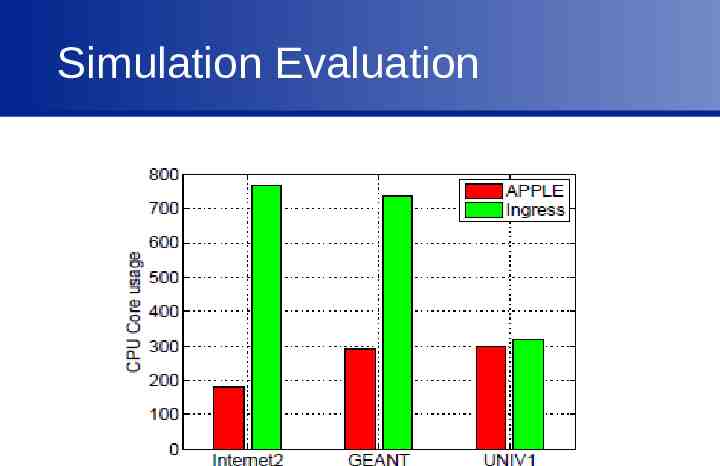
Simulation Evaluation

Simulation Evaluation Less packet loss

Conclusion We design and implement an interference-free NFV Orchestraton Framework Resource efficient Incorporate network dynamics Integrate ClickOS and OpenStack

Thank you!

Backup slides

Optimization Engine: Policy enforcement Policy enforcement. To enforce policies, the requirements are two-folded for each flow. For each network function specified by the policy for a flow, at least one instance is on the network path. For any VNF instance n, there should be at lease one instance of the VNFs succeeding n on the same switch of n or the downstream switches on the path. (recursive)