Perkins Innovation and Modernization Grant Program Project:
28 Slides4.34 MB

Perkins Innovation and Modernization Grant Program Project: Computer Science Principles and Cybersecurity Pathway for Career and Technical Education Exploring Cybersecurity Fundamentals TASK 39-49

TASK 39-44 [39] Describe cybersecurity. [40] Define information assurance. [41] Describe the critical factors of information security. [42] Explain cybersecurity services as they relate to intrusion prevention capabilities that protect systems against unauthorized access, exploitation, and data exfiltration. [43] Define risk.

TASK 45-49 [44] Identify the concepts of cybersecurity risk management. [45] Describe cybersecurity threats to an organization. [46] Explain why organizations need to manage risk. [47] Discuss national or industry standards/regulations that relate to cybersecurity. [48] Describe the cyberattack surface of various organizations. [49] Analyze risks affecting critical infrastructure.

[39] Describe Cybersecurity Cybersecurity: A set of principles and practices designed to safeguard the computing assets and online information against digital threats. Practice of protecting computers, servers, cell phones, networks from harmful attacks to their software, hardware or electronic data, as well as to the services they provide. Protects sensitive data from theft and damage.

[40]Define information assurance Information assurance: Steps involved in protecting and managing risks related to the use, storage, and transmission of data and information systems. Done by focusing on ensuring that a user is who they say they are. Ensures that only authorized users can view/modify specific files or information.
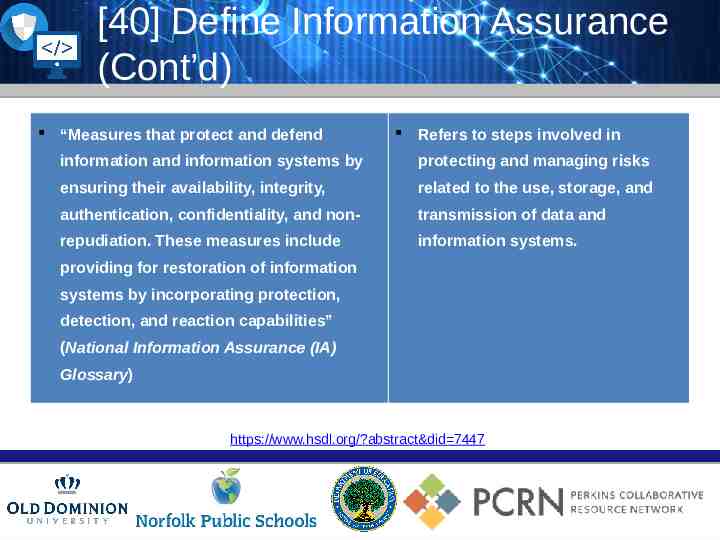
[40] Define Information Assurance (Cont’d) “Measures that protect and defend Refers to steps involved in information and information systems by protecting and managing risks ensuring their availability, integrity, related to the use, storage, and authentication, confidentiality, and non- transmission of data and repudiation. These measures include information systems. providing for restoration of information systems by incorporating protection, detection, and reaction capabilities” (National Information Assurance (IA) Glossary) https://www.hsdl.org/?abstract&did 7447
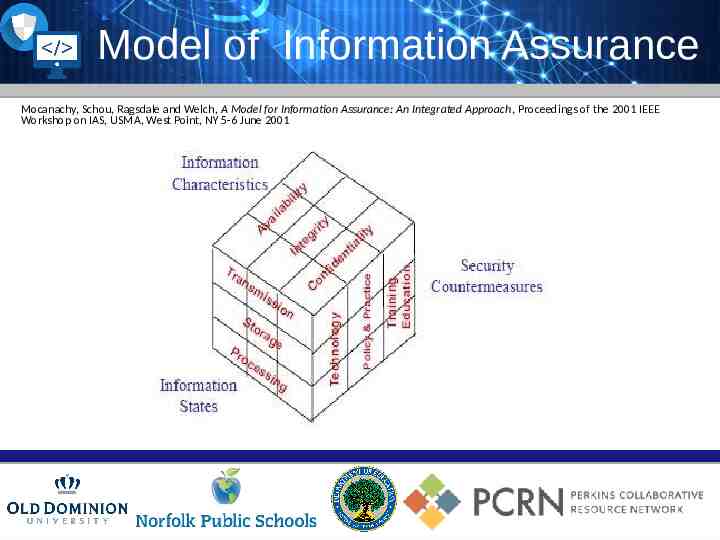
Model of Information Assurance Mocanachy, Schou, Ragsdale and Welch, A Model for Information Assurance: An Integrated Approach, Proceedings of the 2001 IEEE Workshop on IAS, USMA, West Point, NY 5-6 June 2001

[41] Describe the Critical Factors of Information Security Information security: Critical Factors: Protection of information and information Protects organization's ability to function systems from: unauthorized access use disclosure disruption modification destruction in order to provide confidentiality, integrity, and availability. Enables safe operation of applications downloaded on organization’s IT systems Protects data the organization collects and uses Safeguards technology the organization uses

Thoughts . What do you think are some Critical Factors of Information Security?
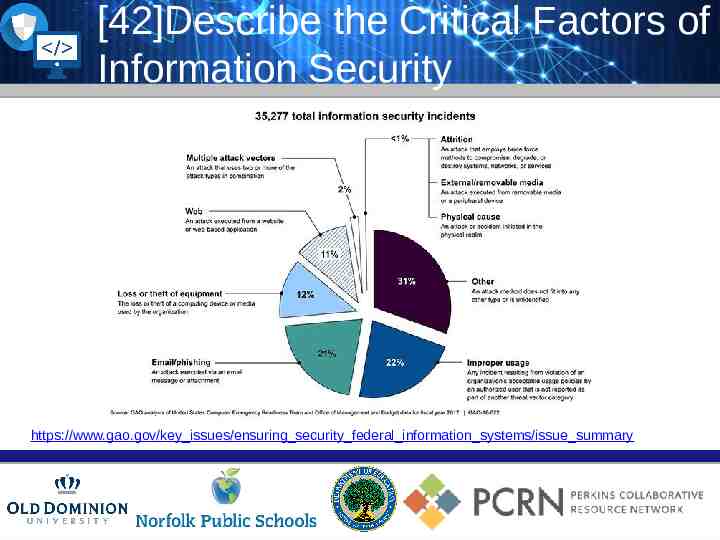
[42]Describe the Critical Factors of Information Security https://www.gao.gov/key issues/ensuring security federal information systems/issue summary

[43] Define Cyber Risk Cybersecurity RISK threat vulnerability consequence Cyber Risk: Potential exposure to harm or loss resulting from breaches of or attacks on information systems.

[44] Identify the Concepts of Cybersecurity Risk Management Identifying, Assessing and Controlling threats to an organization's capital and earnings.

Thoughts . Why do you think organization's need to manage risks?

[45] Describe Cybersecurity Threats to an Organization Cybersecurity threats to an organization Phishing Malware (Virus, Worm, Trojan Horse) Spyware Ransomware Algorithm Manipulation Password Attacks Distributed Denial of Service Spam

Thoughts . What do you think are some Cybersecurity threats to an organization?

[46] Explain Why Organizations Need to Manage Risk Organization's need to manage risk because: Private data can be compromised or altered Recovery expenses are costly o new IT training, new software, or restoring lost data Clients trust for the organization will likely weaken and the company can lose business https://www.coso.org/Documents/COSO-Deloitte-Managing-Cyber-Risk-in-a-Digital-Age.pdf

Cybersecurity Measures Firewalls Anti-virus software Intrusion detection and prevention systems Encryption Login passwords Government and private sector regulations

Activity: Cybersecurity Threats & Measures Define and Give an example (Text or Graphic) of the following: Algorithm Manipulation Anti-virus software Distributed Denial of Service Password Attacks Encryption Phishing Firewalls Ransomware Intrusion detection and Spam prevention systems Spyware Login passwords Malware (Virus, Worm, Trojan Horse)

[47] Discuss national or industry standards/regulations that relate to cybersecurity. Three main cybersecurity regulations are: 1996 Health Insurance Portability and Accountability Act (HIPAA) 1999 Gramm-Leach-Bliley Act 2002 Homeland Security Act which included the Federal Information Security Management Act (FISMA). https://en.wikipedia.org/wiki/Cyber-security regulation

[48] Describe Cyber Attack Surface of an Organization Inside attackers an organization Outside attackers to an organization Disgruntled employee Business competitors Contract worker that was trusted Hackers with network access Foreign governments Terrorists

[49] Analyze Risks Affecting Critical Infrastructure Part 1 Critical infrastructure: Energy, Water, Transportation and Communication systems Includes items that society relies Our country’s critical lifeline functions upon to maintain: which are constantly under threat. - national security, economic vitality and public health & safety. - Examples: assets, systems, facilities, networks, other elements. https://www.cisa.gov/sites/default/files/publi cations/Guide-Critical-Infrastructure-Securit y-Resilience-110819-508v2.pdf

Analyze Risks Affecting Critical Infrastructure Part 2 Sectors at risk of physical or cyber attacks, due to natural causes or accidents as well as malicious actors, include: – healthcare – nuclear and chemical facilities – the food chain – dams and power stations – government and financial facilities – water treatment and sewer systems – critical manufacturing and more. https://www.hstoday.us/subjectmatter-areas/infrastructure-secur ity/cisa-confronts-2020s-top-criti cal-infrastructure-threats/

Thouhgt . What do you think are Risks Affecting an organization’s Critical Infrastructure?

Analyze Risks Affecting Critical Infrastructure. Threats include – extreme weather – hacking – other natural disasters – pandemics – malfunctions and industrial accidents – terror attacks, active shooters – foreign influence operations and the investment of potentially hostile foreign powers in segments of American infrastructure. https://www.hstoday.us/subject-matter-areas/infrastructure-security/cisa-confronts-2020s-top-critical-infrastructure-threats/
Activity Review a hacking case study https://www.csid.com/wp-content/uploads/2015/04/CSI D Whitepaper Jomoco.pdf

References Part 1 https://www.hsdl.org/?abstract&did 7447 https://www.ceocomputers.com/what-to-do-to-defend-against-cyber-security-threats/ Mocanachy, Schou, Ragsdale and Welch, A Model for Information Assurance: An Integrated Approach, Proceedings of the 2001 IEEE Workshop on IAS, USMA, West Point, NY 5-6 June 2001 https://www.gao.gov/key issues/ensuring security federal information systems/issue sum mary https://cybersecop.com/services/cybersecurity-services https://www.bitsight.com/blog/cybersecurity-risk-thorough-definition https://www.coso.org/Documents/COSO-Deloitte-Managing-Cyber-Risk-in-a-Digital-Age.pdf

References Part 2 https://www.baesystems.com/en/cybersecurity/article/bae-systems--research-reveals-40--of-u -s--executives-are-unsure-of-the-cyber-security-measures-their-companies-have-in-place https://en.wikipedia.org/wiki/Cyber-security regulation https://www.channelnews.com.au/commenttelstra-cyber-attack-shows-how-easy-australia-can -be-attacked/ https://www.cisa.gov/sites/default/files/publications/Guide-Critical-Infrastructure-Security-Resil ience-110819-508v2.pdf https://www.forbes.com/sites/brighammccown/2018/07/11/senate-to-probe-growing-cybersecu rity-threats-is-energy-infrastructure-safe

Acknowledgements The project team wishes to acknowledge funding received by the U.S. Department of Education, Office of Career, Technical, and Adult Education, Division of Academic and Technical Education, Innovation and Modernization Program, award # V051F190072, grant #12882683, funded by the Perkins V statute, U.S. Congress.