Strategies for Preventing a Breach and Assessing Your Cybersecurity
33 Slides1.64 MB

Strategies for Preventing a Breach and Assessing Your Cybersecurity Risk Management Program Colorado Society of Certified Public Accountants February 8, 2018 Troy Fine - Manager, Risk Advisory Services Dan Desko - Senior Manager, Risk Advisory Services

Who is Schneider Downs? One of the top 60 largest accounting and business advisory firms in the United States Established in 1956; headquartered in Pittsburgh, PA Largest regional independently owned, registered public accounting and business advisory firm in Western Pennsylvania, with an office in Columbus, Ohio Approximately 450 personnel in total, including 42 shareholders Registered with the PCAOB Risk Advisory Services – – – – Cybersecurity SOX Section 404 compliance Internal control outsourcing/co-sourcing SOC Reports 2

Troy Fine Manager, Risk Advisory Services CPA/CITP, CISA Joined Schneider Downs in 2011 Areas of expertise: – – – – – – SOC 1 and 2 assurance services SOC 2 assurance services (HITRUST) SOC for Cybersecurity assurance services SOX Section 404 compliance Internal control assessments HIPAA assessments Industry experience: Cloud Computing/Software-as-a-Service, Higher Ed, Banking, Financial Services, Healthcare, Manufacturing, Non-profit AICPA CITP Credential Committee Member 3

Dan Desko Senior Manager of IT Risk Advisory Services at Schneider Downs CISA (Certified Information Systems Auditor) CISSP (Certified Information Systems Security Professional) CTPRP (Certified Third Party Risk Professional) 14 years of experience; began career working in IT Current Outgoing ISACA Pittsburgh Chapter President Experience in delivering IT Audit, IT Security Services, Penetration Testing and Vendor Risk Management Services to a variety of industries Responsible for product delivery, client satisfaction and quality control 4

Agenda Current State of Cybersecurity Must-Ask Questions to Prevent Your Organization from Being Breached Methods for Assessing Your Organization’s Cybersecurity Risk Management Program Q&A 5
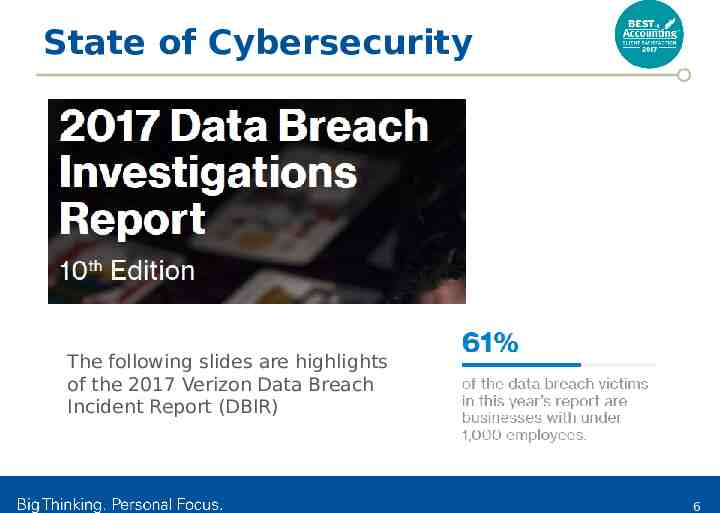
State of Cybersecurity The following slides are highlights of the 2017 Verizon Data Breach Incident Report (DBIR) 6

State of Cybersecurity The important thing to note on this slide is that the majority of breaches occur in one of two ways: 1. Human error 2. Outside hackers Bonus: Combination of the two! The other important takeaway is that the attackers are organized criminal groups; they’re run like businesses 7
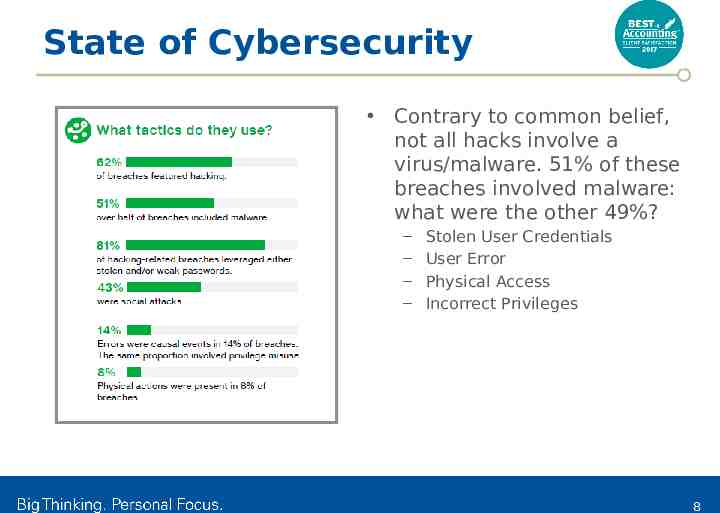
State of Cybersecurity Contrary to common belief, not all hacks involve a virus/malware. 51% of these breaches involved malware: what were the other 49%? – – – – Stolen User Credentials User Error Physical Access Incorrect Privileges 8
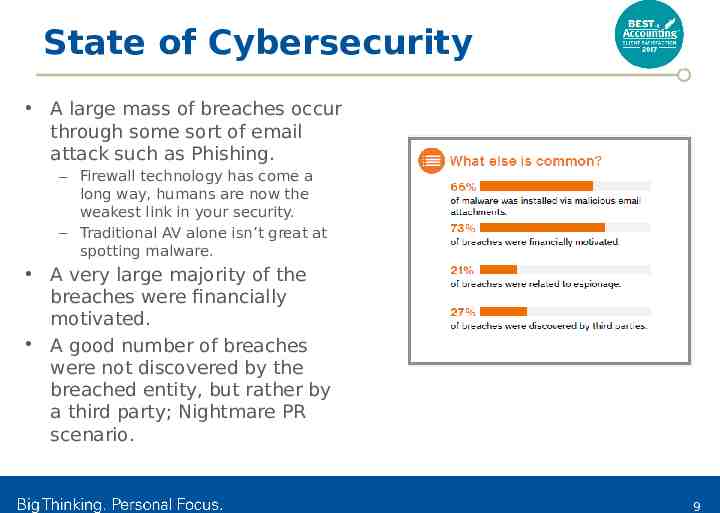
State of Cybersecurity A large mass of breaches occur through some sort of email attack such as Phishing. – Firewall technology has come a long way, humans are now the weakest link in your security. – Traditional AV alone isn’t great at spotting malware. A very large majority of the breaches were financially motivated. A good number of breaches were not discovered by the breached entity, but rather by a third party; Nightmare PR scenario. 9

State of Cybersecurity 10

State of Cybersecurity Phishing deservedly warrants some additional attention – It was found in over 90% of all incidents and breaches. – Once phished, a number of things can occur: Installation of software (e.g., ransomware, command and control systems, etc.) Influencing disclosure of sensitive data (e.g., business email compromise) Using the compromised computer or accounts as a foothold and pivot to other more interesting systems Using a compromised email account to then phish internally 11
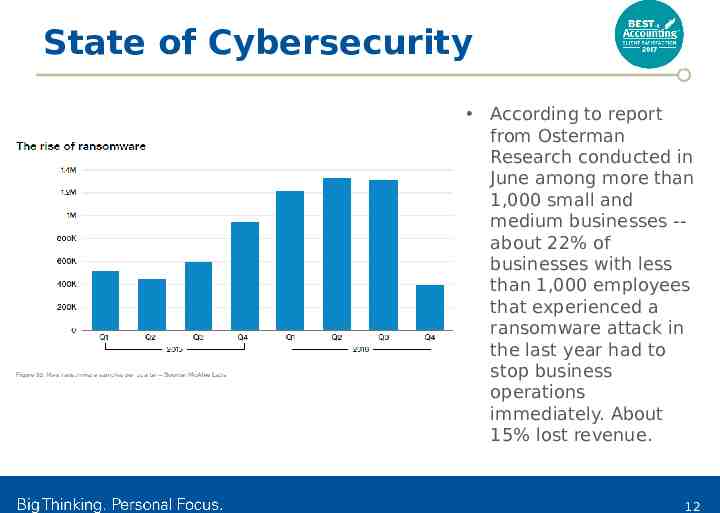
State of Cybersecurity According to report from Osterman Research conducted in June among more than 1,000 small and medium businesses -about 22% of businesses with less than 1,000 employees that experienced a ransomware attack in the last year had to stop business operations immediately. About 15% lost revenue. 12

Agenda Current State of Cybersecurity Must-Ask Questions to Prevent Your Organization from Being Breached Methods for Assessing Your Organization’s Cybersecurity Risk Management Program Q&A 13

Question One How well do you know your IT environment? – Accurate inventory of devices – Accurate inventory of software – Accurate inventory of Internet- facing systems 14

Question Two What data do the hackers want and where does it live? Look at not only structured data, but unstructured as well (e.g., spreadsheets, user reports, downloads from ERP or CRM systems) What data lives in your employee’s email accounts? 15

Question Three If you have identified critical systems and data, how do you further protect access to it? Do you require complex passwords? Do you require two-factor authentication to critical systems and the network? – Email – VPN – ERP – CRM 16

Question Four Are your employees susceptible to being phished? Statistics show the answer is likely “yes”. Have you tested/trained them? What technical controls have you put in place to stop it? – e.g., Advanced Email Protection 17

Question Five If phishing succeeds, do you have additional protection methods? Advanced endpoint protection complements traditional anti-virus Encryption of data Whitelisting of allowed applications 18

Question Six Does your IT staff concentrate more on security or operations? Management often believes that their IT staff focuses on security more than they actively do in reality. Reality is that security and IT operations often conflict with each other Having an independent security group or security consulting partner helps bridge the gap 19

Question Seven Do you know where you are vulnerable? A large amount of breaches take advantage of unpatched operating systems and application software. – e.g., Equifax breach leveraged vulnerability in Apache Struts software toolkit. How often does your IT team patch systems and software? Have you run vulnerability scans to test the effectiveness of the patching process? 20

Question Eight Have you simulated an external attack to determine how secure/vulnerable you really are? Penetration tests or ethical hacking exercises are valuable because they help identify issues before the bad guys do. 21

Question Nine How prepared are you for a breach? Its not a matter of “IF,” but, “WHEN” Having a solid incident response plan that is tested may not prevent a breach, but will surely limit the impact Practice common scenarios (e.g., phishing, ransomware, business email compromise, etc.) 22
Question Ten Have you adopted and assessed yourself against a standard security framework? Allows for continuous improvement Set a road map for long-term information security success 23

Extra Credit! Do you know what vendors have access to, or store, your data? You can outsource certain business operations, but you can’t outsource the risk. Ask business service providers for a SOC report or similar attestation report regarding their security controls to gain transparency. 24

Agenda Current State of Cybersecurity Must-Ask Questions to Prevent Your Organization from Being Breached Methods for Assessing Your Organization’s Cybersecurity Risk Management Program Q&A 25

Assessing Cybersecurity Risk SOC for Cybersecurity Examination – Assurance engagement performed by an independent CPA firm – Examined against suitable control criteria i.e., SOC 2 Trust Services Criteria – Results in a Cybersecurity Risk Management Examination Report that consists of: Management's description of the entity's cybersecurity risk management program Management’s assertion CPA’s opinion on the effectiveness of the entity’s cybersecurity risk management program – Report covers a specific time period 26

Assessing Cybersecurity Risk Cybersecurity Maturity Assessment – Evaluate your cybersecurity risk management program against industry best practices NIST Cybersecurity Framework ISO 27001 HITRUST PCI-DSS – Results in a Cybersecurity Maturity Assessment Report that consists of: Completed cybersecurity risk assessment report Prioritized list of control gaps with recommended plans of action 27

Assessing Cybersecurity Risk External Footprint Analysis – Use commonly available open source tools, scanners and databases to obtain a blueprint of the network and its Internet profile – Black box approach – Gather data about hosts – Results in a report that consists of: List of identified hosts, including operating systems, applications, domain names, IP ranges May discover hosts or applications that management was not aware existed 28

Assessing Cybersecurity Risk Vulnerability Assessment – Provides a comprehensive view of potential security flaws in an environment – Check for misconfigurations, unpatched services, open ports and other architectural mistakes – Results in a report that consists of: Summary of identified vulnerabilities Vulnerabilities ranked by criticality Remediation plans 29

Assessing Cybersecurity Risk Penetration Test – Builds on the external footprint analysis and vulnerability assessment – Simulate actions of an internal/external attacker and attempt to exploit vulnerabilities and misconfigurations – Attempt to use multiple attack vectors Expose unpatched systems “Phishing for compromise” Physical access USB flash drive drop – Results in a report that consists of: Summary of vulnerabilities Results of exploitation attempts Criticality rankings Remediation strategies 30

Assessing Cybersecurity Risk Phishing Assessments – Simulate realistic phishing campaigns – Results in a report that consists of: Summary of customized phishing campaign Results about user’s actions, including: – Percentage of employees who opened the email – Percentage of employees who clicked on the link/attachment – Percentage of employees who provided account details 31

CITP Credential A CITP is a CPA: – Credentialed by the AICPA – Recognized for the unique ability to provide business insight by leveraging knowledge of information relationships and supporting technologies – Specializing and demonstrating specific skills, expertise and experience in the following areas: IT Assurance IT Risk Data Analytics Security & Privacy Business Solutions Emerging IT Trends 32
Questions? Contact Information Troy Fine – [email protected] - 412-6975238 Dan Desko – [email protected] - 412697-5285 Visit our blog for more information on cybersecurity: https://www.schneiderdowns.com/our-thoughts-on 33






