Simple Mail Transfer Protocol (SMTP) Team: Zealous Presented By:
22 Slides1.05 MB

Simple Mail Transfer Protocol (SMTP) Team: Zealous Presented By: Vishal Parikh (003749955) Ribhu Pathria(004698318) Deval Dudhia(004692975) Vaibhav Patel(004413124) Jainip Desai (004677635)

Agenda Introduction Format of E-mail Basic SMTP architecture SMTP Communication model Commands of SMTP Session Establishment and Termination SMTP mail transaction process Security Basics PGP-SMIME-PEM Server Authentication Advantages Limitations Special Features Conclusion References
Introduction SMTP stands for Simple Mail Transfer Protocol. MTP preceded SMTP. The Commands of MTP are based directly on those of FTP. What is the need of SMTP ? Came into existence in 1981 (RFC 780) SMTP is simpler than MTP it replaced. When an e-mail is sent from the sender to receiver, in most cases this involves, the sender machine sends the email to local SMTP sever, which in then sends mail to recipients local SMTP sever, and finally to recipients local machine.
How messages are sent to SMTP server? E-mail communication using Relaying Used during initial days of SMTP. SMTP routing information is included along with Email address. Problem with this method. Using DNS This method is used at present. The senders SMTP server makes the use of DNS to find MX record of the domain to which the E-mail is to be sent.
Format of an e-mail Mail is a Text File. Envelope: It contains with sender address, receiver address and other information. Message: It contains Mail Header and Mail Body. Mail Header: It defines the sender, the receiver, the subject of the message and other information Mail Body: It contains the actual information in the message Why to use an envelope if sender and recipient’s email address is already contained in the headers of the message itself?
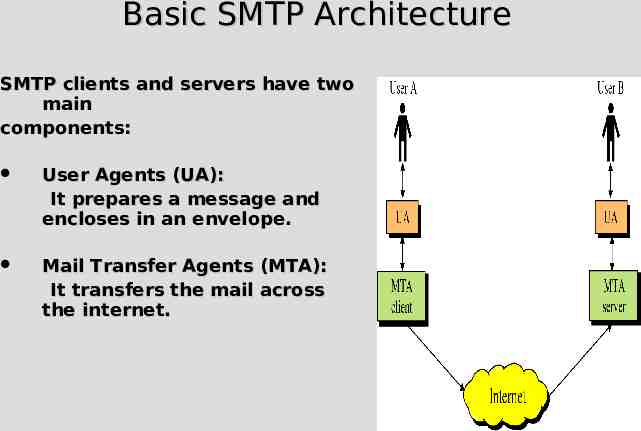
Basic SMTP Architecture SMTP clients and servers have two main components: User Agents (UA): It prepares a message and encloses in an envelope. Mail Transfer Agents It transfers the mail the internet. (MTA): across
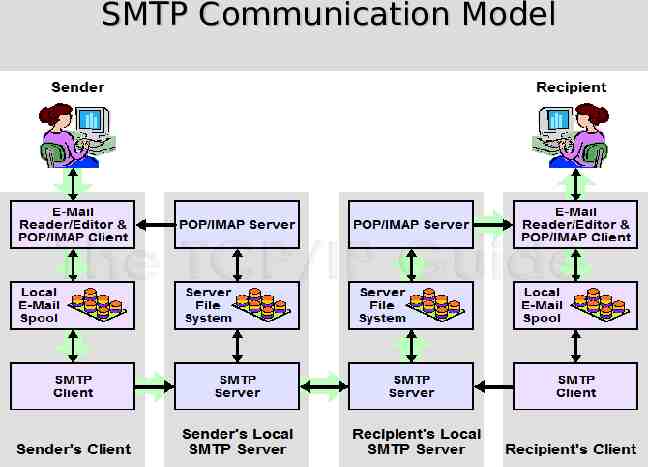
SMTP Communication Model

Commands of SMTP HELO : Request to initiate SMTP session MAIL FROM : Sender’s E-Mail address RCPT TO : Receiver’s E-Mail address DATA : Body of message QUIT : Terminates SMTP connection RSET : Aborts mail transaction VRFY : Asks receiver to verify the validity of the mailbox EXPN : Asks receiver to identify mailing list HELP : Causes receiver to send help information NOOP : Forces server to verify the communication with SMTP receiver
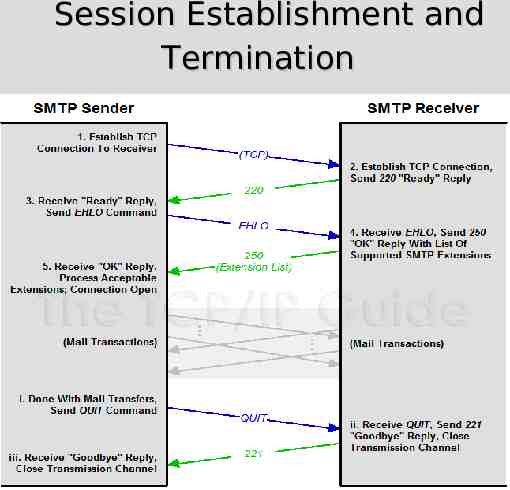
Session Establishment and Termination
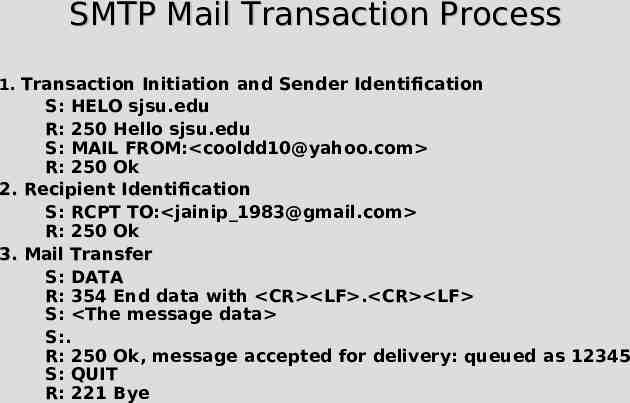
SMTP Mail Transaction Process 1. Transaction Initiation and Sender Identification S: HELO sjsu.edu R: 250 Hello sjsu.edu S: MAIL FROM: [email protected] R: 250 Ok 2. Recipient Identification S: RCPT TO: jainip [email protected] R: 250 Ok 3. Mail Transfer S: DATA R: 354 End data with CR LF . CR LF S: The message data S:. R: 250 Ok, message accepted for delivery: queued as 12345 S: QUIT R: 221 Bye

Status Codes The Server responds with a three digit code that may be followed by the text info. 2XX – The SMTP server has accepted the command and has completed the request. 3XX - Command is accepted and more information follows. 4XX - Try again later as there was a temporary failure with the command or the server. 5XX – The requested operation will never be completed due to permanent error.
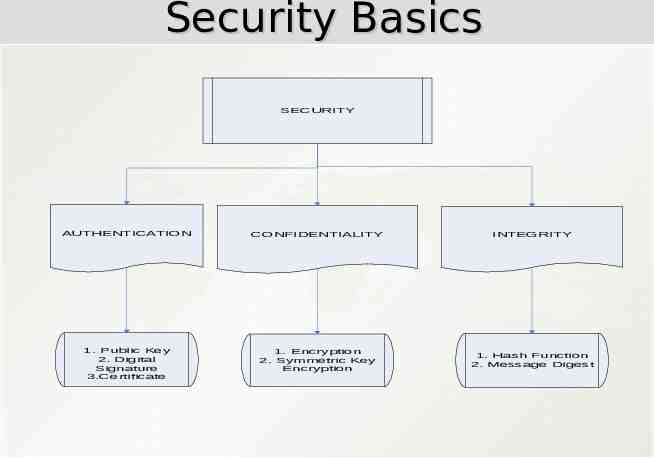
Security Basics SECURITY AUTHENTICATION CONFIDENTIALITY INTEGRITY 1. Public Key 2. Digital Signature 3.Certificate 1. Encryption 2. Symmetric Key Encryption 1. Hash Function 2. Message Digest
SMTP SECURITY FEATURES ?
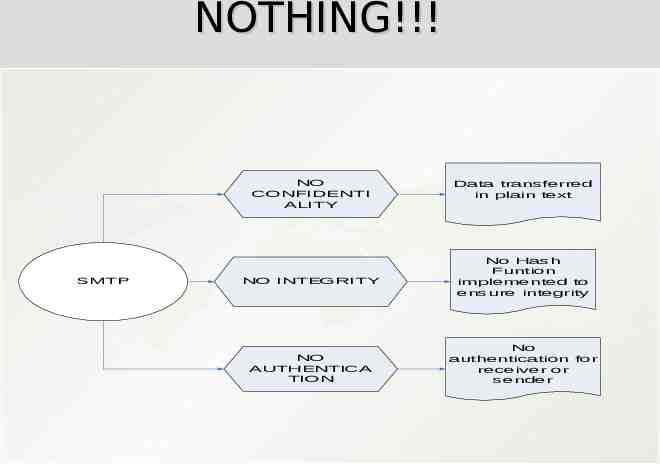
NOTHING!!! NO CONFIDENTI ALITY SMTP NO INTEGRITY NO AUTHENTICA TION Data transferred in plain text No Hash Funtion implemented to ensure integrity No authentication for receiver or sender
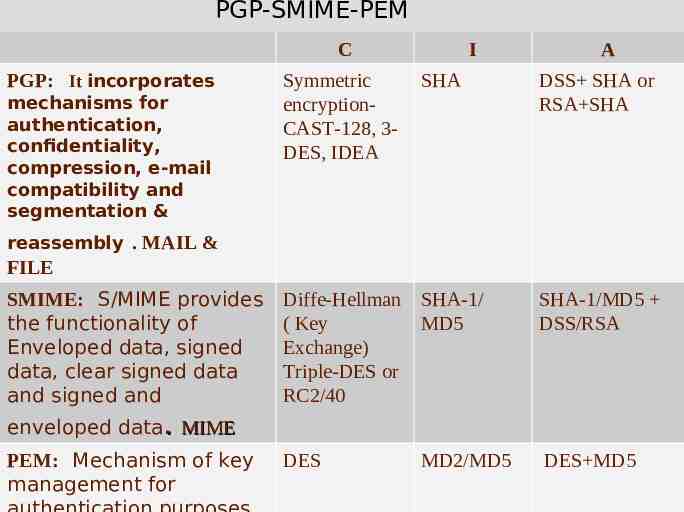
PGP-SMIME-PEM C PGP: It incorporates mechanisms for authentication, confidentiality, compression, e-mail compatibility and segmentation & I A Symmetric encryptionCAST-128, 3DES, IDEA SHA DSS SHA or RSA SHA Diffe-Hellman ( Key Exchange) Triple-DES or RC2/40 SHA-1/ MD5 SHA-1/MD5 DSS/RSA DES MD2/MD5 DES MD5 reassembly . MAIL & FILE SMIME: S/MIME provides the functionality of Enveloped data, signed data, clear signed data and signed and enveloped data. MIME PEM: Mechanism of key management for
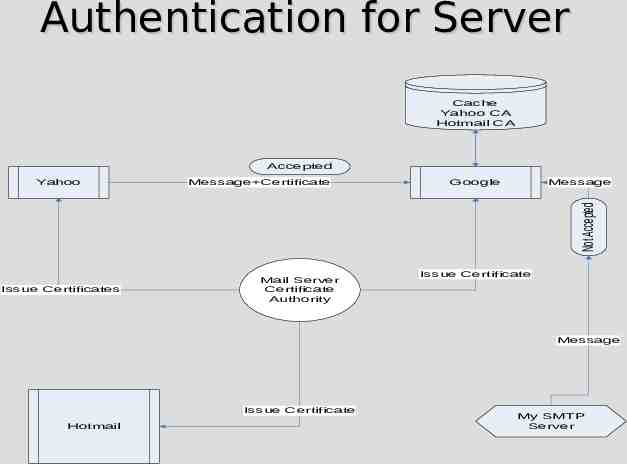
Authentication for Server Cache Yahoo CA Hotmail CA Accepted Message Certificate Google Message Not Accepted Yahoo Issue Certificates Mail Server Certificate Authority Issue Certificate Message Issue Certificate Hotmail My SMTP Server

Advantages Very Popular Supported on many platforms Low administration and implementation costs Simple addressing scheme

Limitations Security matters for SMTP are worse. Its usefulness is limited by its simplicity. Transmission of executable files and binary files using SMTP is not possible without converting into text files. Use MIME to send mail in other format. It cannot transmit text data that contains national language characters. These national language characters use 8-bit codes with values of 128 decimal or more. It is limited to 7-bit ASCII characters only. SMTP servers may reject mail messages beyond some specific length.

Special Features Mail Forwarding: SMTP server may agree to accept e-mail for nonlocal mailbox and forward it to the appropriate destination. Mail Gatewaying: SMTP servers can be implemented as e-mail gateways which can translate TCP/IP email in a suitable form for some another e-mail system and vice-versa. Mail Relaying: SMTP includes the ability to relay mail from one server to another, as explained earlier, provided certain conditions are met. Address Debugging: VRFY command allows the client to ask the sender to verify address of recipient without sending mail to recipient. Mailing List Expansion: EXPN command allows to expand mailing list.

Conclusion SMTP is one of the most widely used and implemented application. With the explosively growing reliance on electronic mail for commercial and personal services, there grows the demand of authentication and confidentiality. To complement the weak security feature of SMTP industry use PGP-SMIME-PEM. Still there is need of implementing the measures to eliminate spam and other security breaches.

References Web Sites: http://www.faqs.org/rfcs/rfc821.html (RFC 821). http://www.faqs.org/rfcs/rfc2821.html (RFC 2821) http://www.tcpipguide.com/free/ t SMTPSpecialFeaturesCapabilitiesandExtensions.html http://cns.utoronto.ca/usg/technotes/smtp-intro.html http://computer.howstuffworks.com/email5.htm Books: Programmer's Guide to Internet Mail by John Rhoton TCP/IP Illustrated Volume 1 by Richard Stevens

QUESTIONS SUGGESTIONS COMMENTS THANK YOU






