Secure Your Cloud with Confidence Deep Dive into Azure Security
64 Slides9.94 MB

Secure Your Cloud with Confidence Deep Dive into Azure Security Management David Branscome [email protected]

Agenda Newest additions to Defender for Cloud: Defender CSPM and Defender for DevOps Defender for Containers and Kubernetes Attack Matrix Automating Security with Defender for Cloud and Logic Apps Database and Storage Protection with Microsoft Defender for Storage

Newest additions to Defender for Cloud: Defender CSPM Defender for DevOps

Defender for Cloud: Cloud Security Posture Management
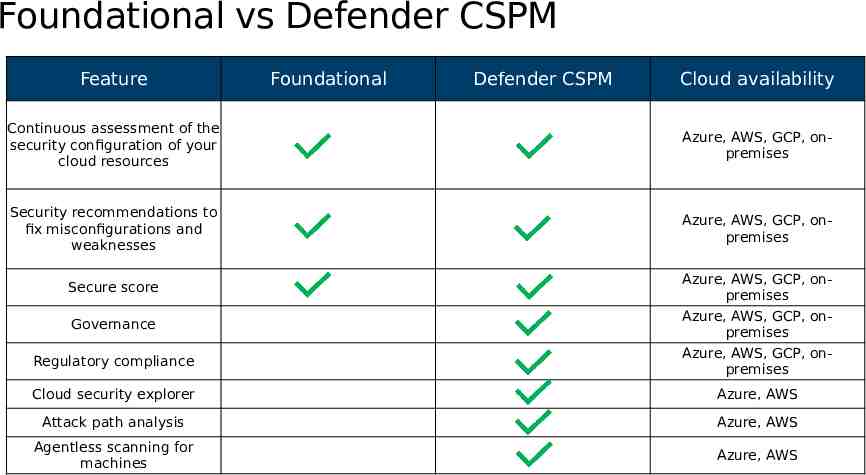
Foundational vs Defender CSPM Feature Foundational Defender CSPM Cloud availability Continuous assessment of the security configuration of your cloud resources Azure, AWS, GCP, onpremises Security recommendations to fix misconfigurations and weaknesses Azure, AWS, GCP, onpremises Secure score Governance Regulatory compliance Azure, AWS, GCP, onpremises Azure, AWS, GCP, onpremises Azure, AWS, GCP, onpremises Cloud security explorer Azure, AWS Attack path analysis Azure, AWS Agentless scanning for machines Azure, AWS
Security governance and regulatory compliance Policies ensure organizational compliance with laws and regulations established by external bodies (e.g, government) Continuously assesses hybrid cloud for risk factors based on controls and best practices
Cloud Security Explorer Collects data from multicloud environment and other data sources Helps you identify weaknesses, vulnerabilities and misconfigurations in deployed assets Feeds Attack Path Analysis
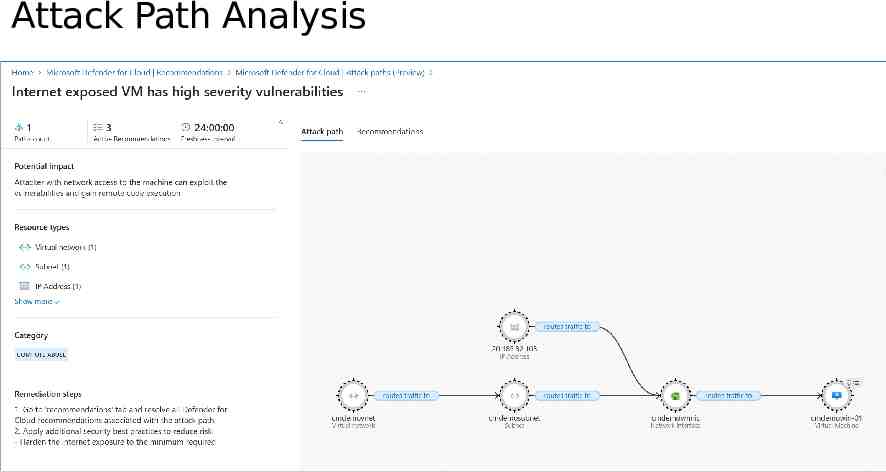
Attack Path Analysis

DEMO

Defender for DevOps
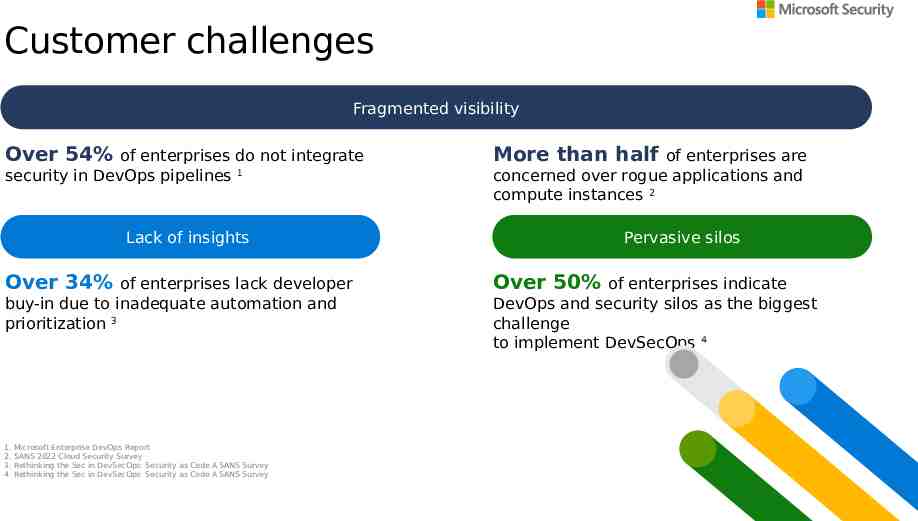
Customer challenges Fragmented visibility Over 54% of enterprises do not integrate security in DevOps pipelines 1 More than half of enterprises are concerned over rogue applications and compute instances 2 Lack of insights Over 34% of enterprises lack developer buy-in due to inadequate automation and prioritization 3 1. 2. 3. 4. Microsoft Enterprise DevOps Report SANS 2022 Cloud Security Survey Rethinking the Sec in DevSecOps: Security as Code A SANS Survey Rethinking the Sec in DevSecOps: Security as Code A SANS Survey Pervasive silos Over 50% of enterprises indicate DevOps and security silos as the biggest challenge to implement DevSecOps 4
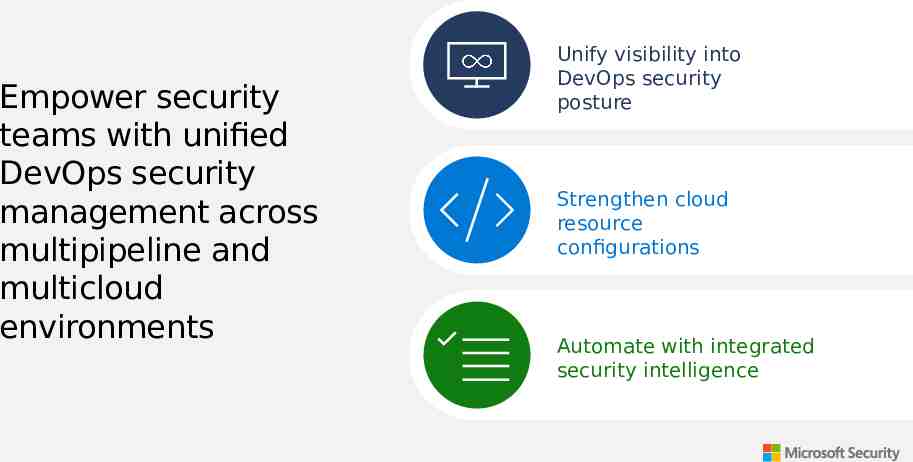
Empower security teams with unified DevOps security management across multipipeline and multicloud environments Unify visibility into DevOps security posture Strengthen cloud resource configurations Automate with integrated security intelligence
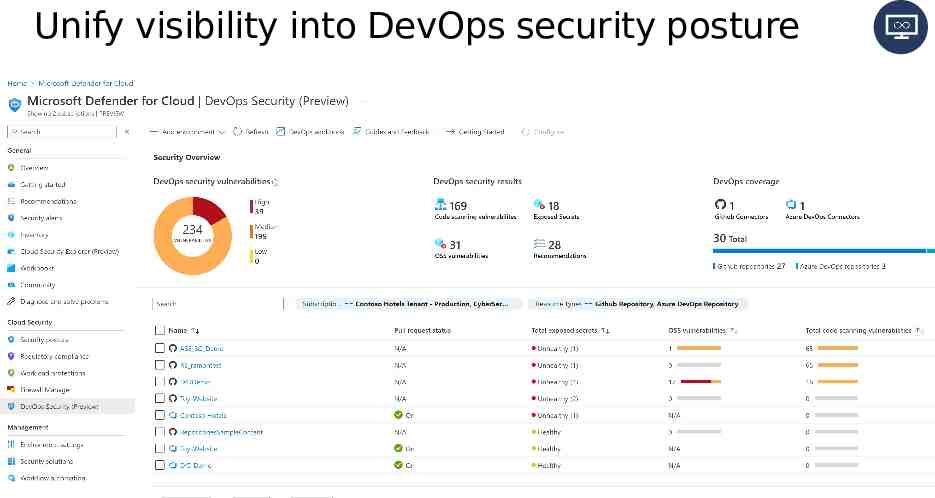
Unify visibility into DevOps security posture
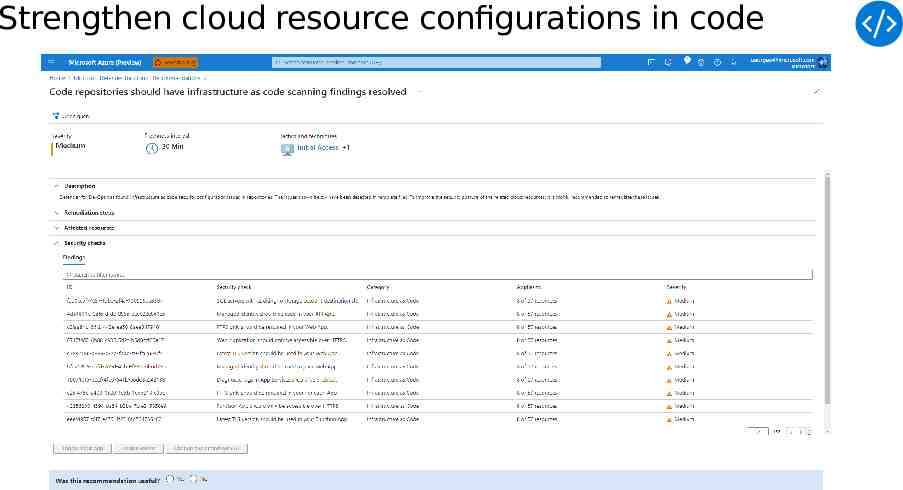
Strengthen cloud resource configurations in code
Automate with integrated security intelligence

DEMO

Defender for Containers

Containers and Kubernetes 101
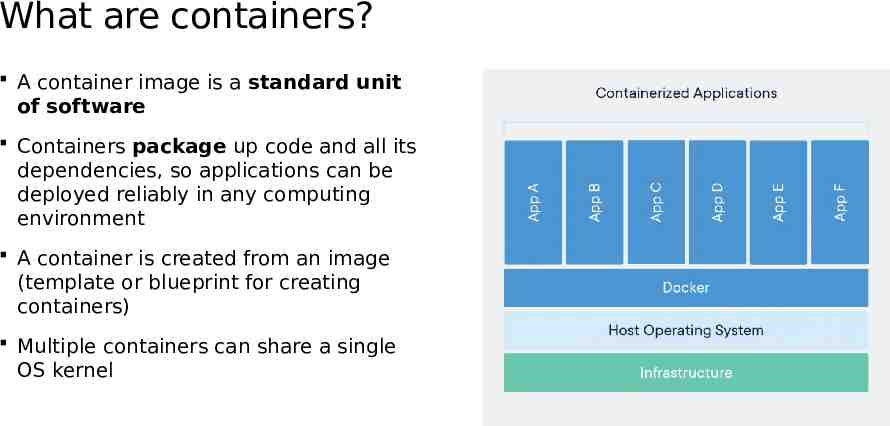
What are containers? A container image is a standard unit of software Containers package up code and all its dependencies, so applications can be deployed reliably in any computing environment A container is created from an image (template or blueprint for creating containers) Multiple containers can share a single OS kernel

Why containers? “Works on my machine” Every environment looks the same Increased velocity Runs anywhere

What is a container registry? A repository for storing container images Public registries i.e., Docker Hub are free & easy Private registries allow for efficient and secure storage

Why Kubernetes? Cluster Managemen t: deploy and manage cluster resources Scaling: make sets of containers elastic in number Scheduling: where containers run Lifecycle and Health: keep containers running despite failure Naming and Discovery: where are my containers and workflow happening in containers and cluster Load Balancing: evenly distribute traffic At the end of the day, we need something to help us with all the Image Continuous Logging and Storage orchestration. repository: Delivery: Monitoring: volumes: centralized, An orchestrator! CI/CD pipeline track what’s persistent secure Docker container images data for containers
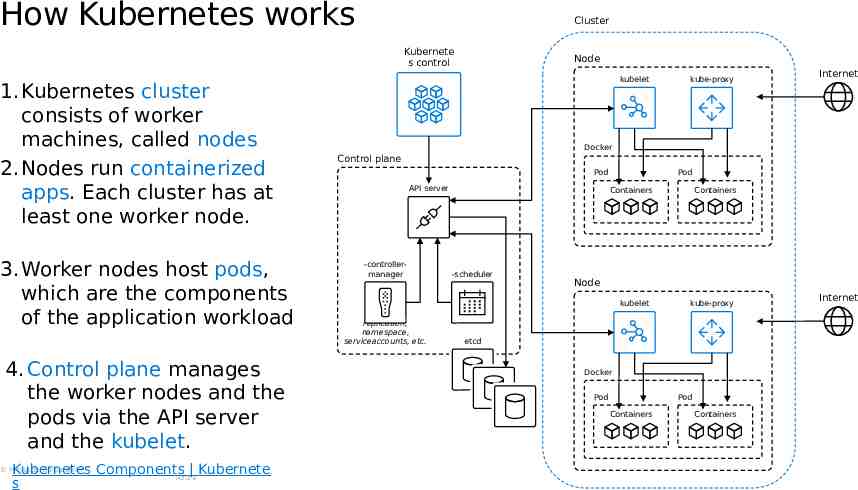
How Kubernetes works Cluster Kubernete s control 1. Kubernetes cluster consists of worker machines, called nodes 2. Nodes run containerized apps. Each cluster has at least one worker node. 3. Worker nodes host pods, which are the components of the application workload 4. Control plane manages the worker nodes and the pods via the API server and the kubelet. Kubernetes Components Kubernete Azure s Microsoft Corporation Node kubelet kube-proxy Internet Docker Control plane Pod API server -controllermanager Pod Containers -scheduler Node kubelet replication, namespace, serviceaccounts, etc. Containers kube-proxy etcd Docker Pod Pod Containers Containers Internet

Securing Containers

Container security is different Ephemeral environment Applications are elastic, containers are short lived, spawn and re-size rapidly Container images are immutable, software updates require creation of new images High demand for visibility and control Containers traffic flows are difficult to track with traditional tools Runtime environment includes rich data and controls, with different configuration layers Unique expertise needed A shortage of skilled labor Steep learning curves for open-source container tools and platforms 50% of container images get replaced in one week or less1 44% of containers live less than five minutes!1 1 2022-cloud-native-security-and-usagereport
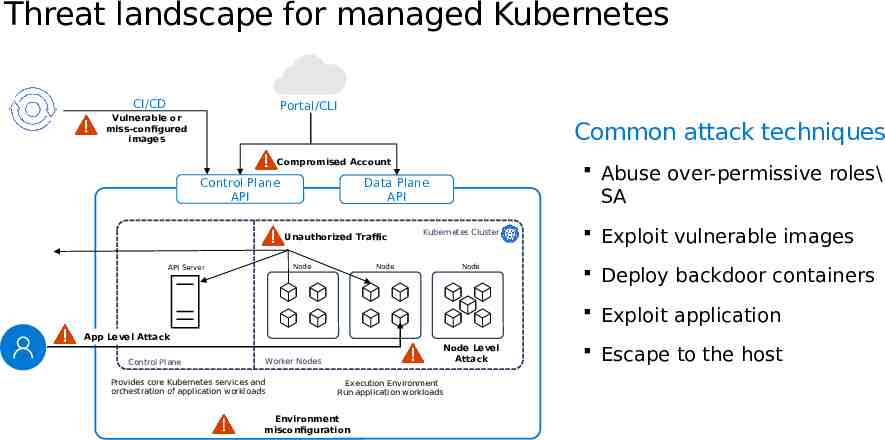
Threat landscape for managed Kubernetes CI/CD Portal/CLI Vulnerable or miss-configured images Common attack techniques Compromised Account Control Plane API Unauthorized Traffic SA Kubernetes Cluster Node Node API Server Abuse over-permissive roles\ Data Plane API Node Exploit vulnerable images Deploy backdoor containers Exploit application App Level Attack Node Level Attack Worker Nodes Control Plane Provides core Kubernetes services and orchestration of application workloads Execution Environment Run application workloads Environment misconfiguration Escape to the host
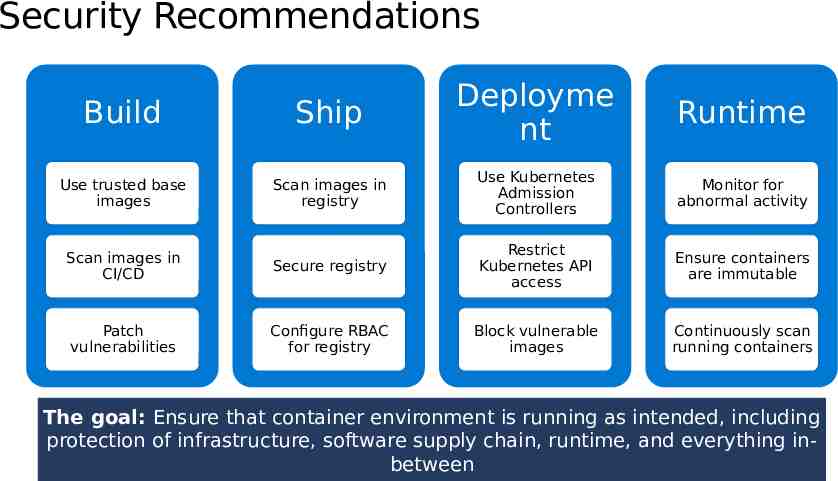
Security Recommendations Build Ship Deployme nt Use trusted base images Scan images in registry Use Kubernetes Admission Controllers Monitor for abnormal activity Scan images in CI/CD Secure registry Restrict Kubernetes API access Ensure containers are immutable Patch vulnerabilities Configure RBAC for registry Block vulnerable images Continuously scan running containers Runtime The goal: Ensure that container environment is running as intended, including protection of infrastructure, software supply chain, runtime, and everything inbetween

Defender for Containers
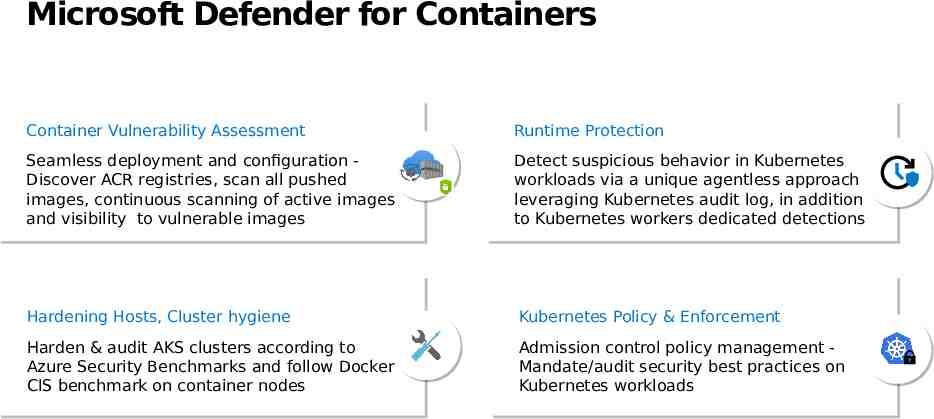
Microsoft Defender for Containers Container Container Vulnerability Vulnerability Assessment Assessment Runtime Runtime Protection Protection Seamless Seamless deployment deployment and and configuration configuration -Discover Discover ACR ACR registries, registries, scan scan all all pushed pushed images, images, continuous continuous scanning scanning of of active active images images and and visibility visibility to to vulnerable vulnerable images images Detect Detect suspicious suspicious behavior behavior in in Kubernetes Kubernetes workloads workloads via via aa unique unique agentless agentless approach approach leveraging leveraging Kubernetes Kubernetes audit audit log, log, in in addition addition to to Kubernetes Kubernetes workers workers dedicated dedicated detections detections Hardening Hardening Hosts, Hosts, Cluster Cluster hygiene hygiene Kubernetes Kubernetes Policy Policy & & Enforcement Enforcement Harden Harden & & audit audit AKS AKS clusters clusters according according to to Azure Azure Security Security Benchmarks Benchmarks and and follow follow Docker Docker CIS CIS benchmark benchmark on on container container nodes nodes Admission Admission control control policy policy management management -Mandate/audit Mandate/audit security security best best practices practices on on Kubernetes Kubernetes workloads workloads
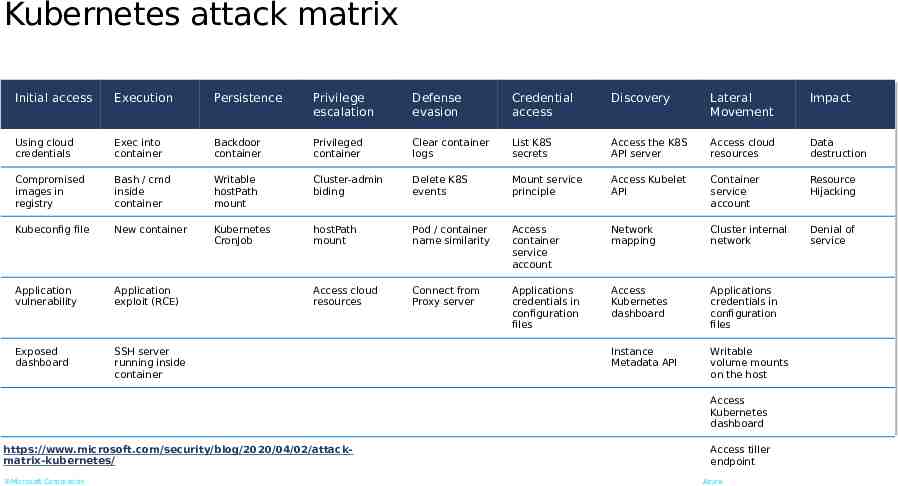
Kubernetes attack matrix Initial access Execution Persistence Privilege escalation Defense evasion Credential access Discovery Lateral Movement Impact Using cloud credentials Exec into container Backdoor container Privileged container Clear container logs List K8S secrets Access the K8S API server Access cloud resources Data destruction Compromised images in registry Bash / cmd inside container Writable hostPath mount Cluster-admin biding Delete K8S events Mount service principle Access Kubelet API Container service account Resource Hijacking Kubeconfig file New container Kubernetes CronJob hostPath mount Pod / container name similarity Access container service account Network mapping Cluster internal network Denial of service Application vulnerability Application exploit (RCE) Access cloud resources Connect from Proxy server Applications credentials in configuration files Access Kubernetes dashboard Applications credentials in configuration files Exposed dashboard SSH server running inside container Instance Metadata API Writable volume mounts on the host Access Kubernetes dashboard https://www.microsoft.com/security/blog/2020/04/02/attackmatrix-kubernetes/ Microsoft Corporation Access tiller endpoint Azure
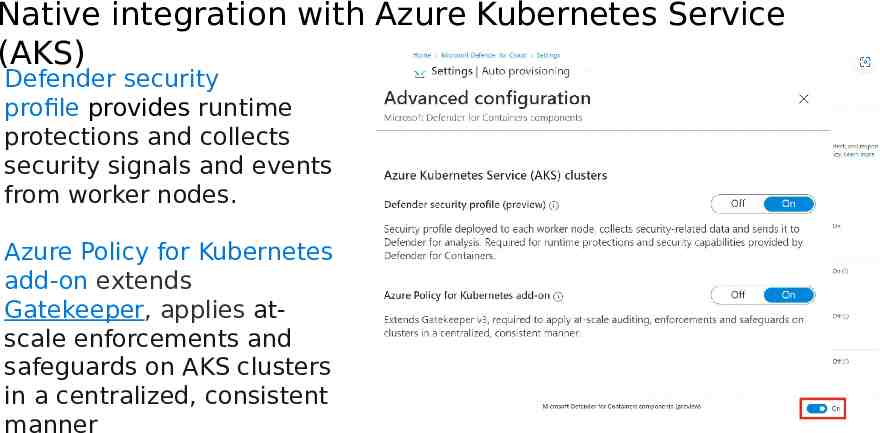
Native integration with Azure Kubernetes Service (AKS) Defender security profile provides runtime protections and collects security signals and events from worker nodes. Azure Policy for Kubernetes add-on extends Gatekeeper, applies atscale enforcements and safeguards on AKS clusters in a centralized, consistent manner
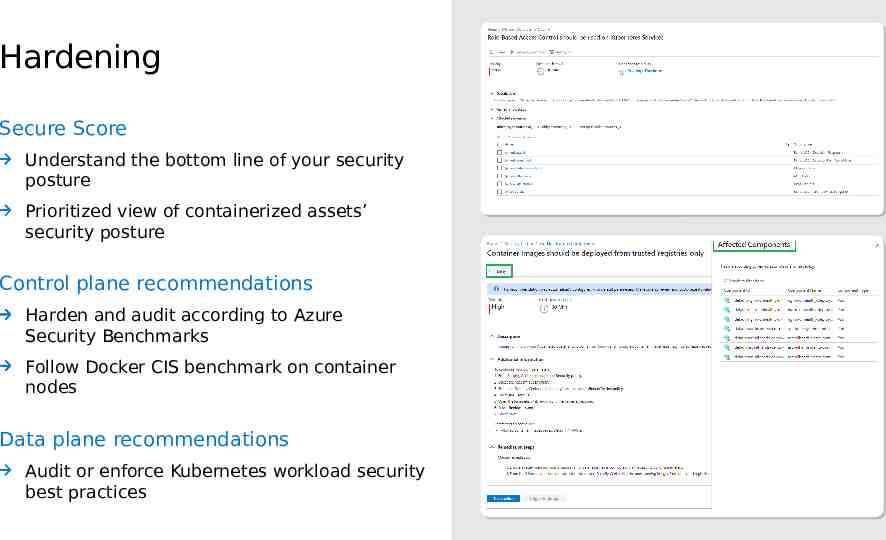
Hardening Secure Score Understand the bottom line of your security posture Prioritized view of containerized assets’ security posture Control plane recommendations Harden and audit according to Azure Security Benchmarks Follow Docker CIS benchmark on container nodes Data plane recommendations Audit or enforce Kubernetes workload security best practices
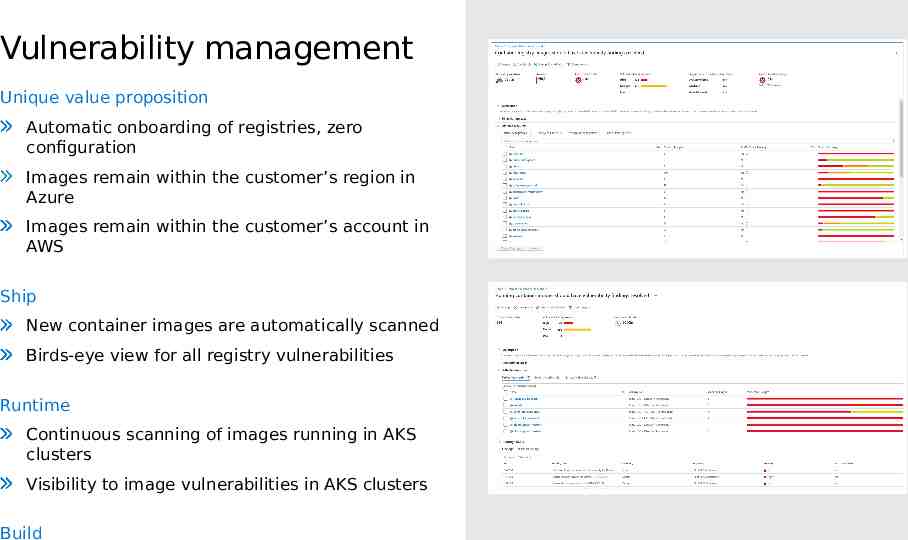
Vulnerability management Unique value proposition Automatic onboarding of registries, zero configuration Images remain within the customer’s region in Azure Images remain within the customer’s account in AWS Ship New container images are automatically scanned Birds-eye view for all registry vulnerabilities Runtime Continuous scanning of images running in AKS clusters Visibility to image vulnerabilities in AKS clusters Build
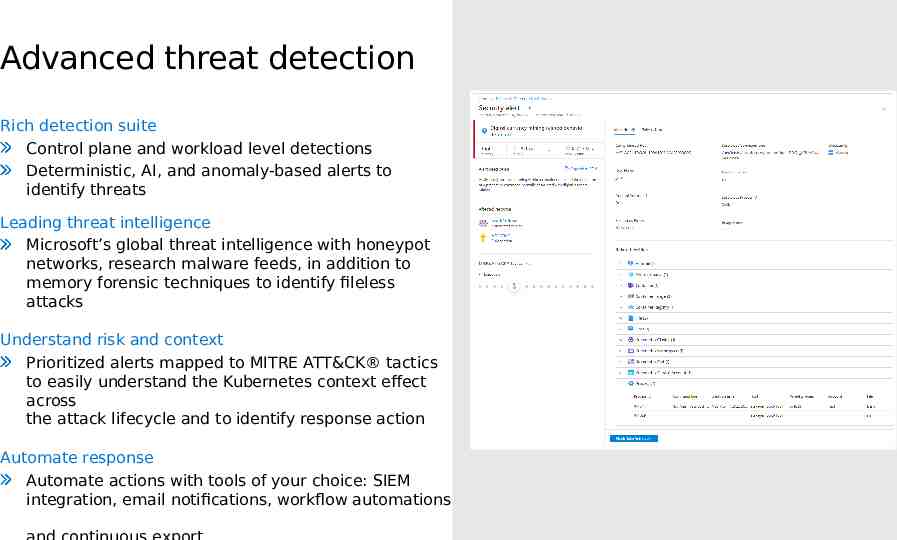
Advanced threat detection Rich detection suite Control plane and workload level detections Deterministic, AI, and anomaly-based alerts to identify threats Leading threat intelligence Microsoft’s global threat intelligence with honeypot networks, research malware feeds, in addition to memory forensic techniques to identify fileless attacks Understand risk and context Prioritized alerts mapped to MITRE ATT&CK tactics to easily understand the Kubernetes context effect across the attack lifecycle and to identify response action Automate response Automate actions with tools of your choice: SIEM integration, email notifications, workflow automations

Automating Security with Defender for Cloud and Logic Apps
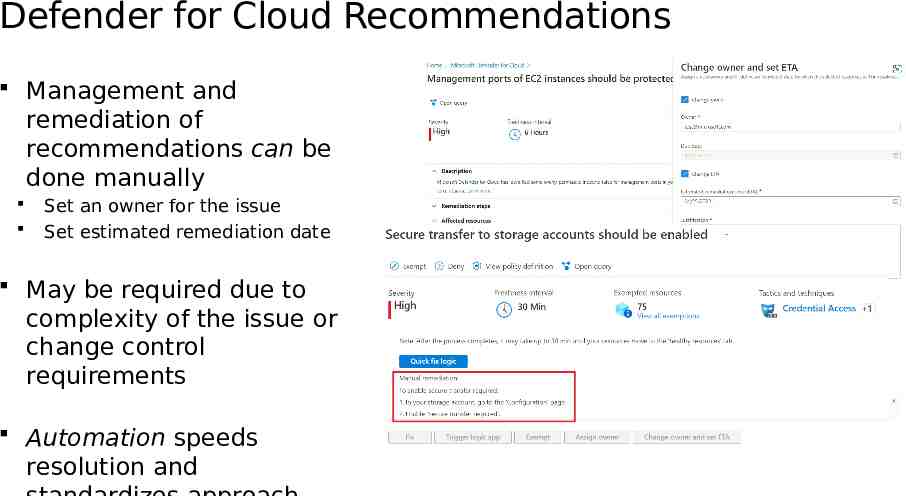
Defender for Cloud Recommendations Management and remediation of recommendations can be done manually Set an owner for the issue Set estimated remediation date May be required due to complexity of the issue or change control requirements Automation speeds resolution and
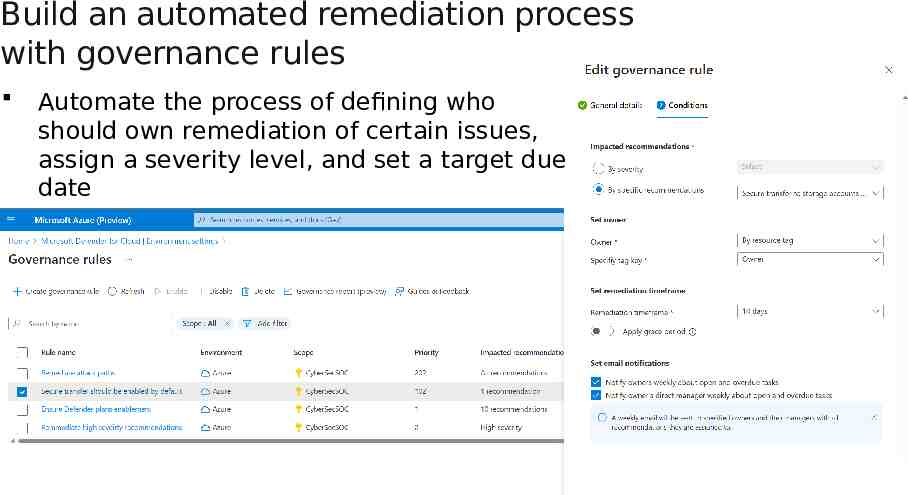
Build an automated remediation process with governance rules Automate the process of defining who should own remediation of certain issues, assign a severity level, and set a target due date
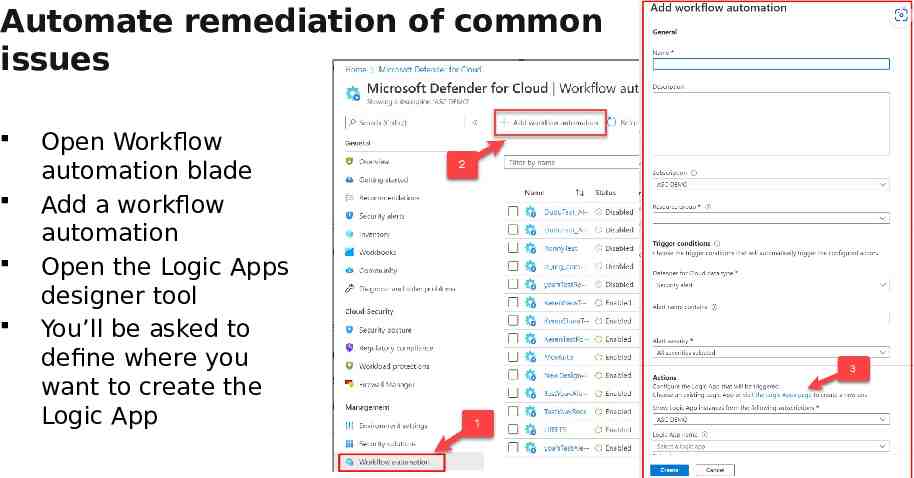
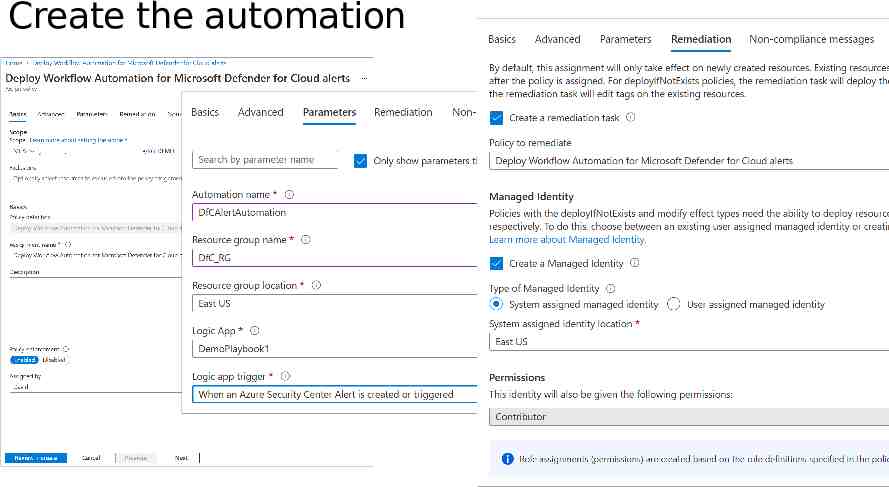
Automate remediation of common issues Open Workflow automation blade Add a workflow automation Open the Logic Apps designer tool You’ll be asked to define where you want to create the Logic App
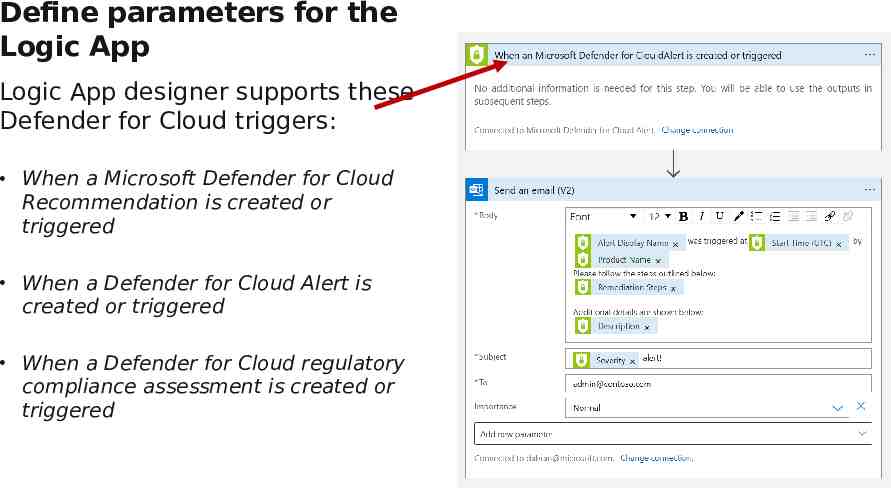
Define parameters for the Logic App Logic App designer supports these Defender for Cloud triggers: When a Microsoft Defender for Cloud Recommendation is created or triggered When a Defender for Cloud Alert is created or triggered When a Defender for Cloud regulatory compliance assessment is created or triggered
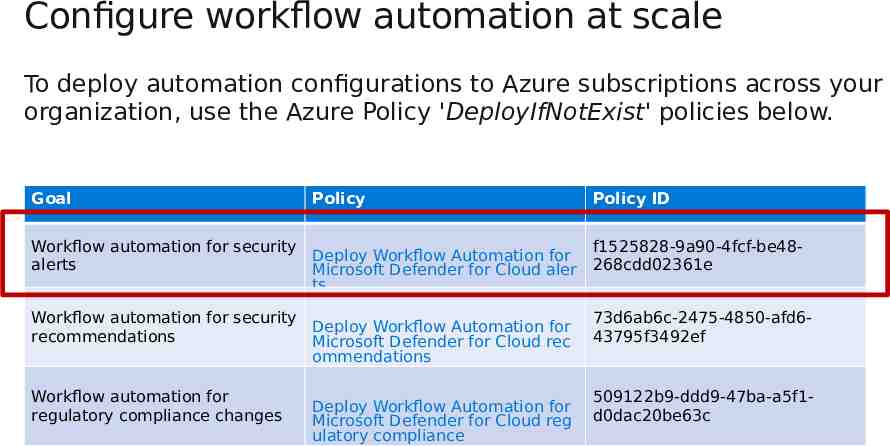
Configure workflow automation at scale To deploy automation configurations to Azure subscriptions across your organization, use the Azure Policy 'DeployIfNotExist' policies below. Goal Policy Policy ID Workflow automation for security Deploy Workflow Automation for alerts Microsoft Defender for Cloud aler ts f1525828-9a90-4fcf-be48268cdd02361e Workflow automation for security Deploy Workflow Automation for recommendations Microsoft Defender for Cloud rec ommendations 73d6ab6c-2475-4850-afd643795f3492ef Workflow automation for regulatory compliance changes 509122b9-ddd9-47ba-a5f1d0dac20be63c Deploy Workflow Automation for Microsoft Defender for Cloud reg ulatory compliance
Create the automation
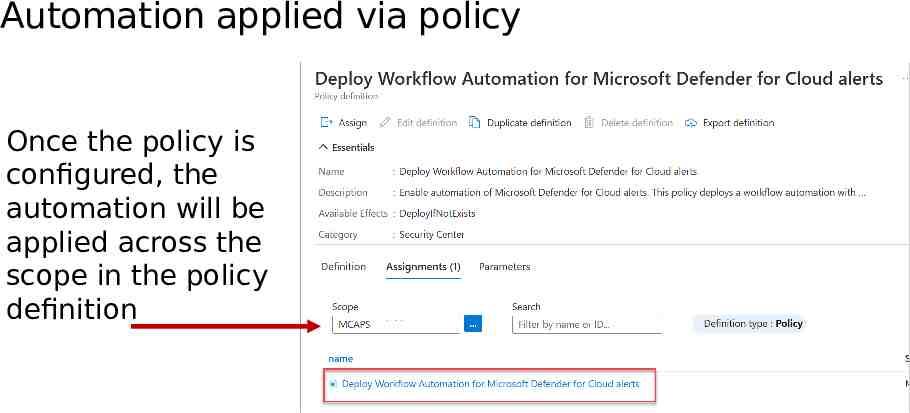
Automation applied via policy Once the policy is configured, the automation will be applied across the scope in the policy definition

DEMO

Database and Storage Protection with Microsoft Defender

Defender for Databases
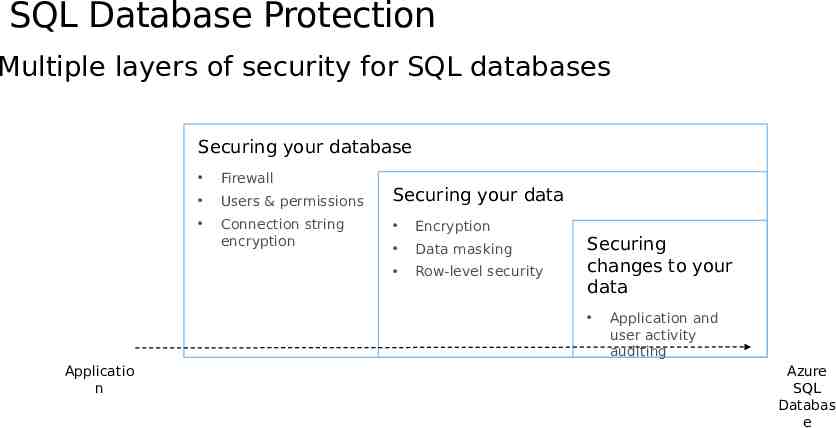
SQL Database Protection Multiple layers of security for SQL databases Securing your database Firewall Users & permissions Securing your data Connection string encryption Encryption Data masking Row-level security Securing changes to your data Applicatio n Application and user activity auditing Azure SQL Databas e
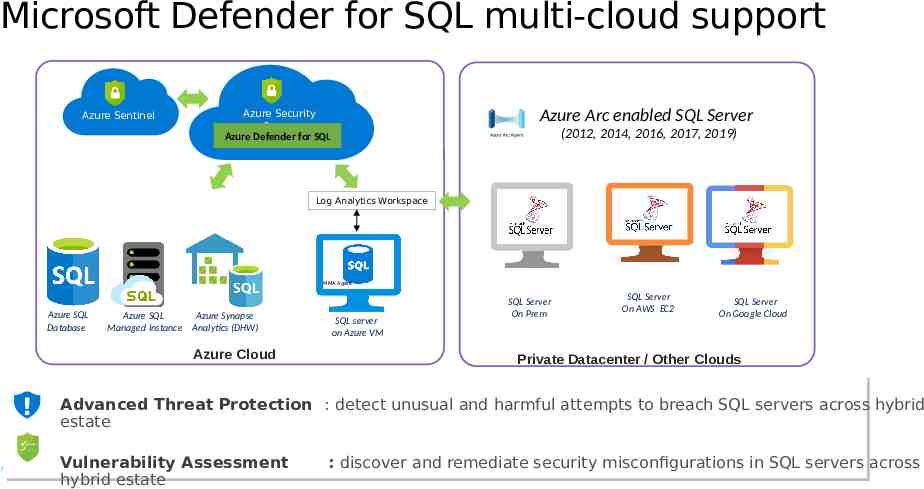
Microsoft Defender for SQL multi-cloud support Azure Sentinel Azure Arc enabled SQL Server Azure Security Center Azure Defender for SQL (2012, 2014, 2016, 2017, 2019) Log Analytics Workspace MMA Agent Azure SQL Database Azure SQL Azure Synapse Managed Instance Analytics (DHW) SQL server on Azure VM Azure Cloud ! SQL Server On Prem SQL Server On AWS EC2 SQL Server On Google Cloud Private Datacenter / Other Clouds Advanced Threat Protection : detect unusual and harmful attempts to breach SQL servers across hybrid estate applications applications Vulnerability Assessment hybrid estate Microsoft Corporation : discover and remediate security misconfigurations in SQL servers across Azure
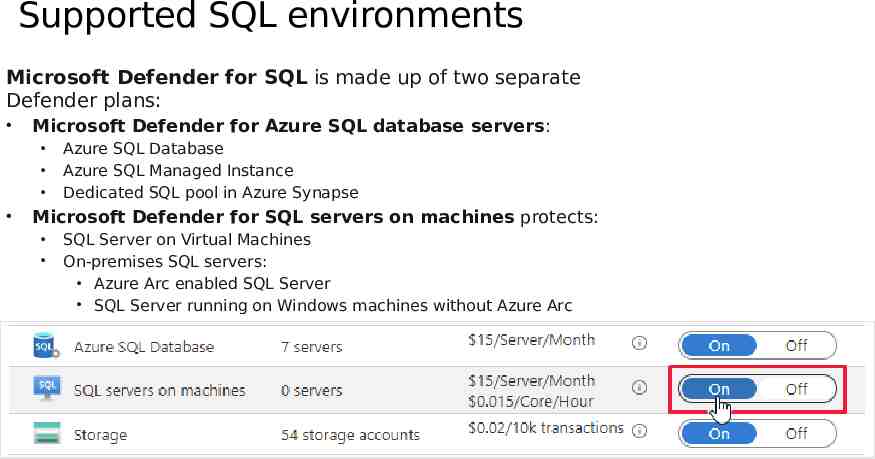
Supported SQL environments Microsoft Defender for SQL is made up of two separate Defender plans: Microsoft Defender for Azure SQL database servers: Azure SQL Database Azure SQL Managed Instance Dedicated SQL pool in Azure Synapse Microsoft Defender for SQL servers on machines protects: SQL Server on Virtual Machines On-premises SQL servers: Azure Arc enabled SQL Server SQL Server running on Windows machines without Azure Arc
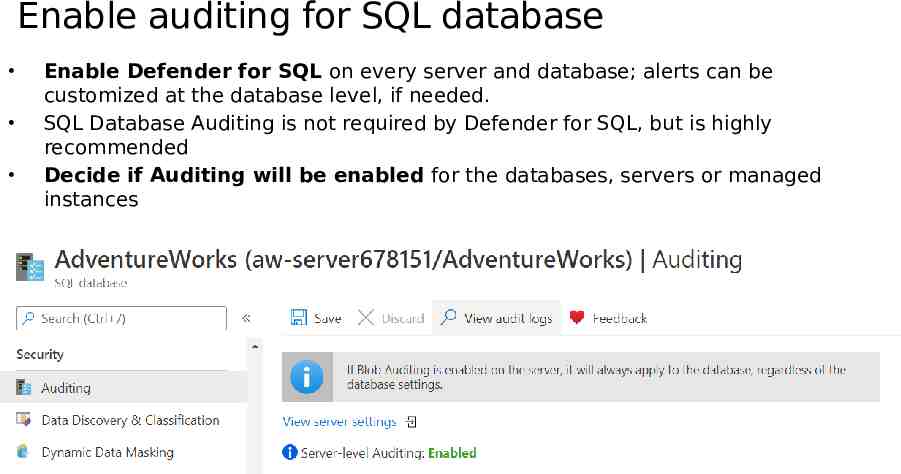
Enable auditing for SQL database Enable Defender for SQL on every server and database; alerts can be customized at the database level, if needed. SQL Database Auditing is not required by Defender for SQL, but is highly recommended Decide if Auditing will be enabled for the databases, servers or managed instances
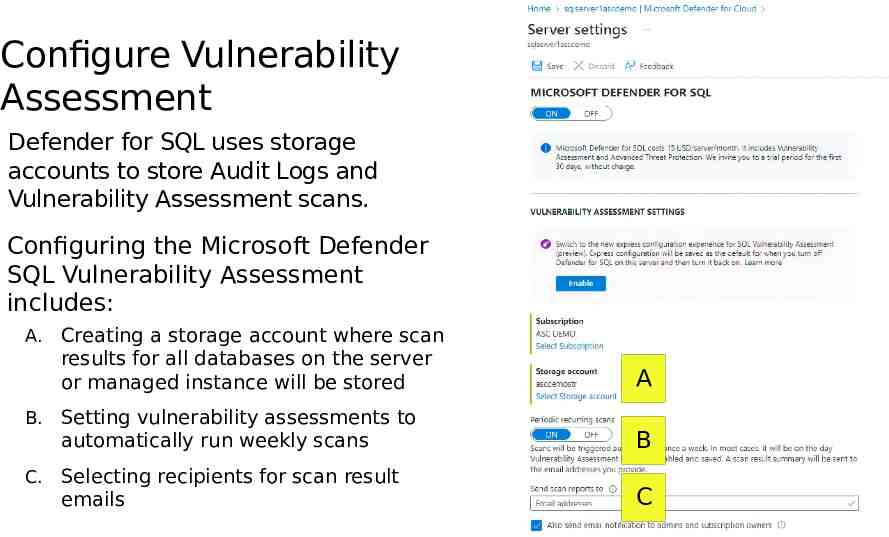
Configure Vulnerability Assessment Defender for SQL uses storage accounts to store Audit Logs and Vulnerability Assessment scans. Configuring the Microsoft Defender SQL Vulnerability Assessment includes: Creating a storage account where scan results for all databases on the server or managed instance will be stored A B. Setting vulnerability assessments to automatically run weekly scans B C. Selecting recipients for scan result emails C A.
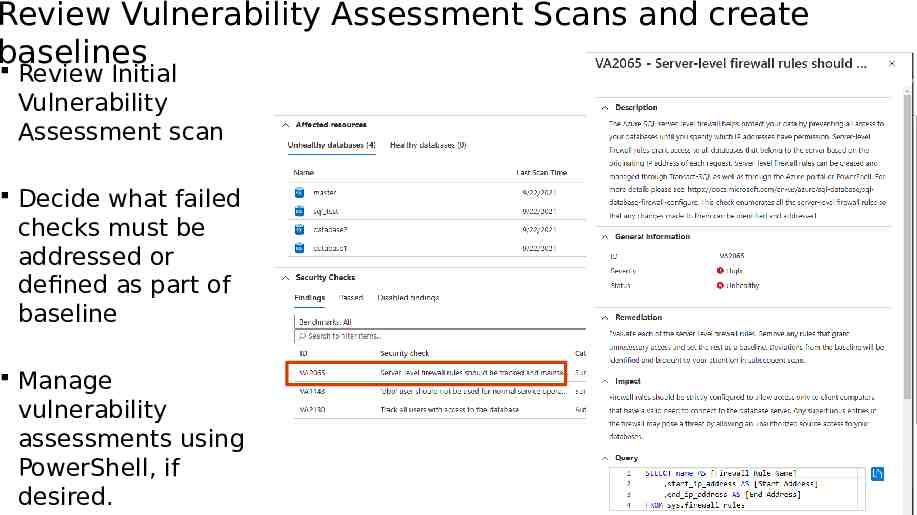
Review Vulnerability Assessment Scans and create baselines Review Initial Vulnerability Assessment scan Decide what failed checks must be addressed or defined as part of baseline Manage vulnerability assessments using PowerShell, if desired.
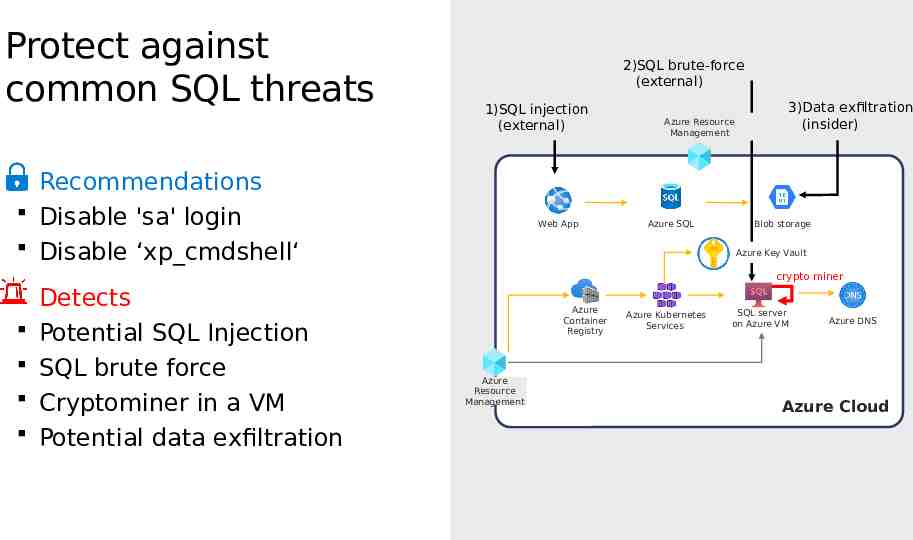
Protect against common SQL threats 2)SQL brute-force (external) 1)SQL injection (external) Recommendations Disable 'sa' login Disable ‘xp cmdshell‘ Web App Azure Resource Management Azure SQL 3)Data exfiltration (insider) Blob storage Azure Key Vault crypto miner Detects Potential SQL Injection SQL brute force Cryptominer in a VM Potential data exfiltration Microsoft Corporation Azure Container Registry Azure Kubernetes Services Azure Resource Management SQL server on Azure VM Azure DNS Azure Cloud Azure

Defender for Storage
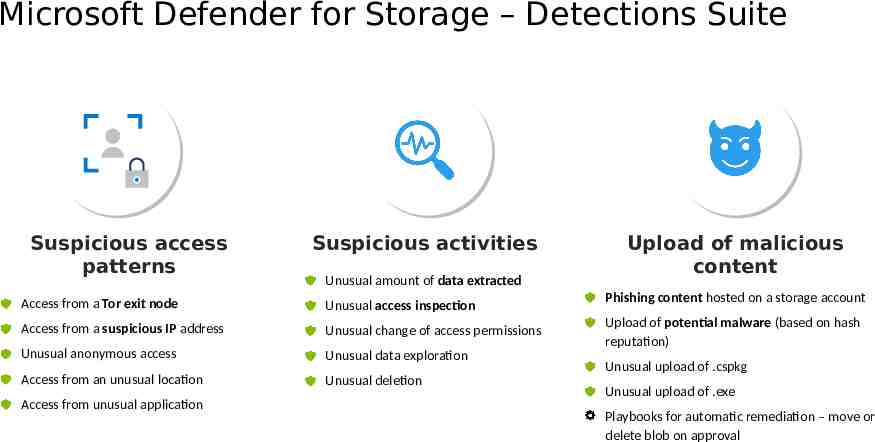
Microsoft Defender for Storage – Detections Suite Suspicious access patterns Suspicious activities Unusual amount of data extracted Access from a Tor exit node Unusual access inspection Access from a suspicious IP address Unusual change of access permissions Unusual anonymous access Unusual data exploration Access from an unusual location Unusual deletion Access from unusual application Upload of malicious content Phishing content hosted on a storage account Upload of potential malware (based on hash reputation) Unusual upload of .cspkg Unusual upload of .exe Playbooks for automatic remediation – move or delete blob on approval
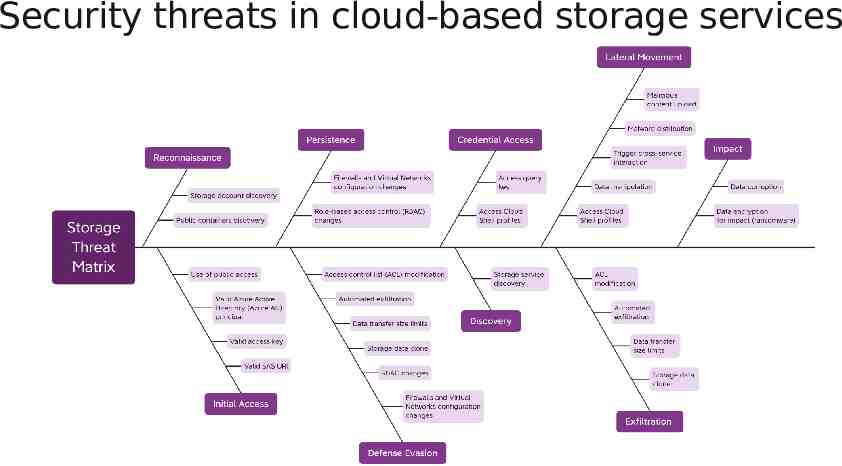
Security threats in cloud-based storage services
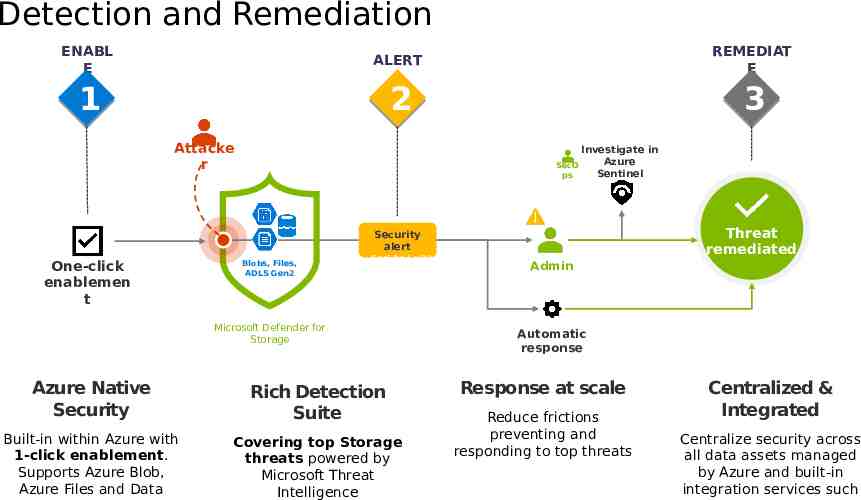
Detection and Remediation ENABL E ALERT REMEDIAT E 1 2 3 Attacke r Investigate in Azure SecO Sentinel ps Threat remediated Security alert One-click enablemen t Blobs, Files, ADLS Gen2 Enriched with Microsoft Threat Intelligence Storage protected by Microsoft Defender for Storage Azure Native Security Rich Detection Suite Built-in within Azure with 1-click enablement. Supports Azure Blob, Azure Files and Data Covering top Storage threats powered by Microsoft Threat Intelligence Admin Automatic response Response at scale Reduce frictions preventing and responding to top threats Centralized & Integrated Centralize security across all data assets managed by Azure and built-in integration services such
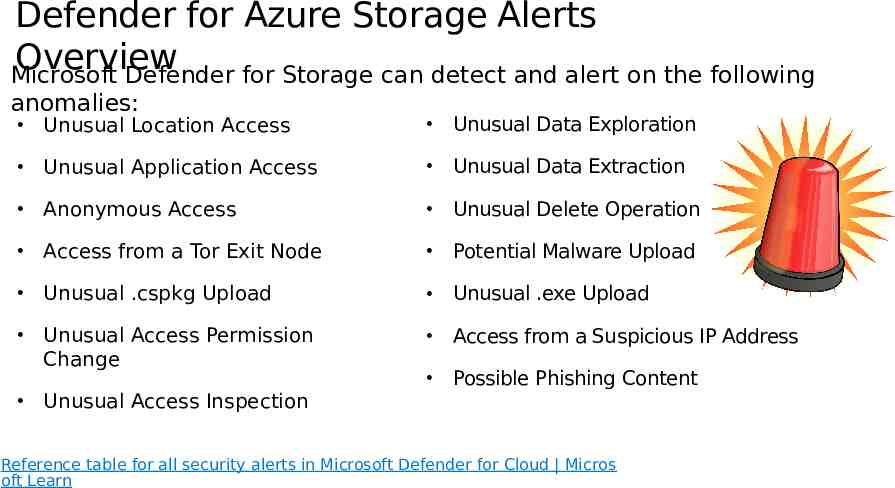
Defender for Azure Storage Alerts Overview Microsoft Defender for Storage can detect and alert on the following anomalies: Unusual Location Access Unusual Data Exploration Unusual Application Access Unusual Data Extraction Anonymous Access Unusual Delete Operation Access from a Tor Exit Node Potential Malware Upload Unusual .cspkg Upload Unusual .exe Upload Unusual Access Permission Change Access from a Suspicious IP Address Possible Phishing Content Unusual Access Inspection Reference table for all security alerts in Microsoft Defender for Cloud Micros oft Learn

Identifying threats with Microsoft Defender for Storage Looks for: Suspicious access patterns Suspicious activities Upload of malicious content Alerts can be exported to SIEM or other external tools Hash reputation analysis compares hashes of uploaded files with known viruses, trojans, spyware and ransomware Microsoft Corporation Azure
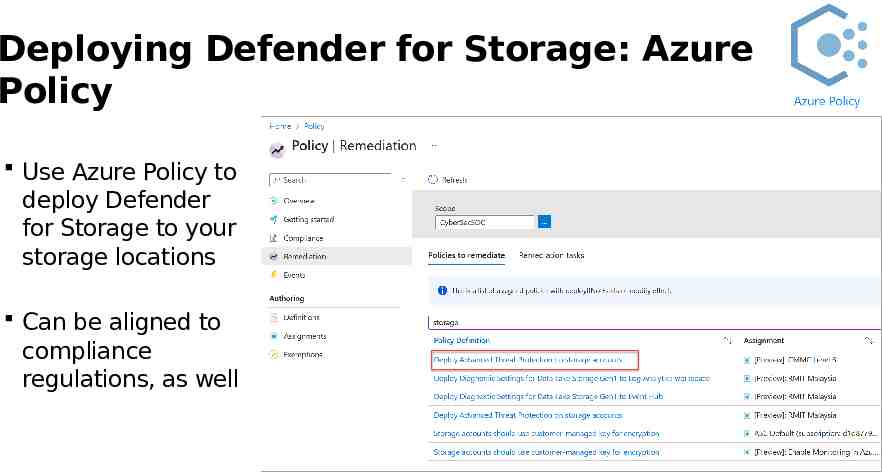
Deploying Defender for Storage: Azure Policy Use Azure Policy to deploy Defender for Storage to your storage locations Can be aligned to compliance regulations, as well
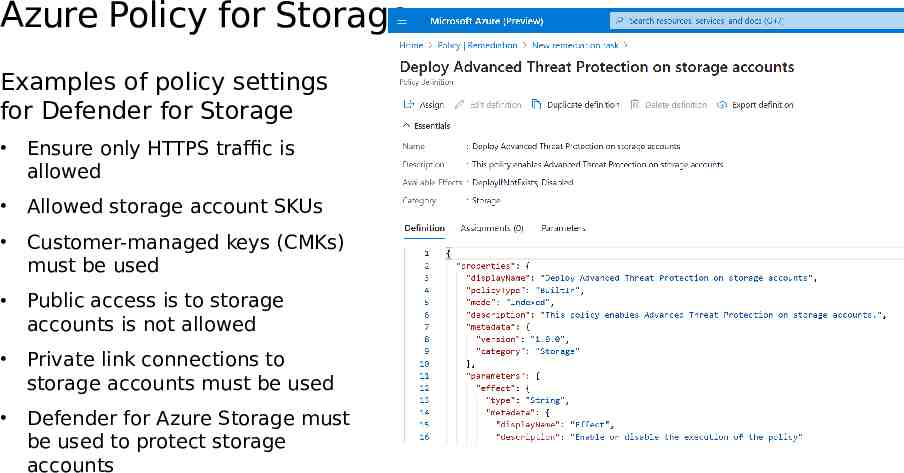
Azure Policy for Storage Examples of policy settings for Defender for Storage Ensure only HTTPS traffic is allowed Allowed storage account SKUs Customer-managed keys (CMKs) must be used Public access is to storage accounts is not allowed Private link connections to storage accounts must be used Defender for Azure Storage must be used to protect storage accounts
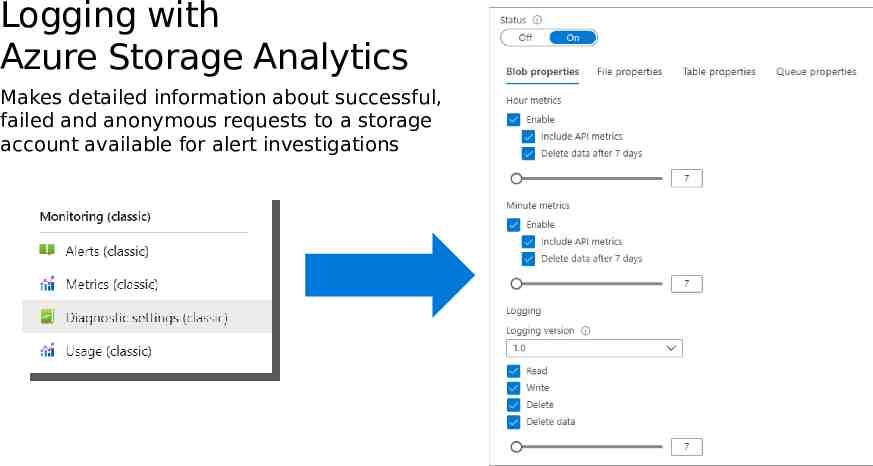
Logging with Azure Storage Analytics Makes detailed information about successful, failed and anonymous requests to a storage account available for alert investigations
Defender for Storage protects against “blob-hunting” Data exfiltration from unsecured storage (whether Azure, AWS or GCP) by threat actors is extremely common Your customers may think their storage is secure. It’s probably not. Hardening security on public storage can be done quickly and painlessly. Protect your storage resources against blob hunting (microsoft .com)
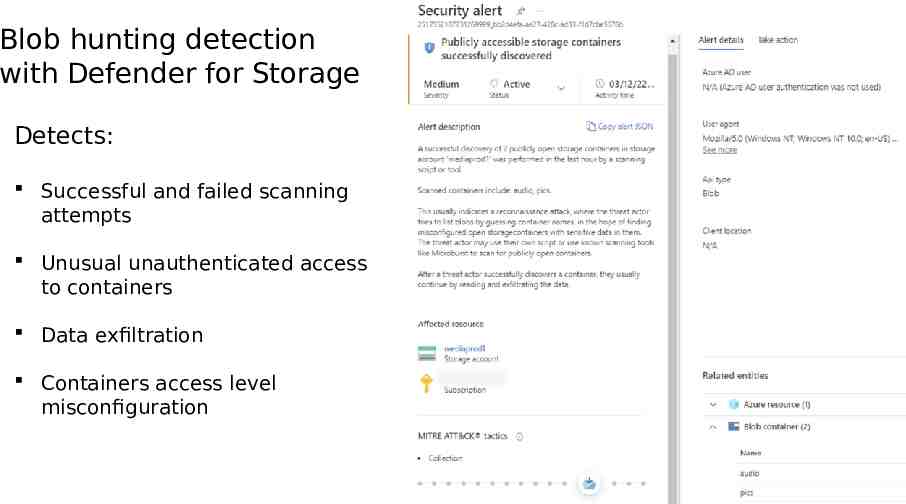
Blob hunting detection with Defender for Storage Detects: Successful and failed scanning attempts Unusual unauthenticated access to containers Data exfiltration Containers access level misconfiguration

Thank you!






