RESEARCH SUPPORT DIVISION (RSD) OVERVIEW Carol Johnson July 31,
15 Slides748.45 KB

RESEARCH SUPPORT DIVISION (RSD) OVERVIEW Carol Johnson July 31, 2019 This Briefing is: UNCLASSIFIED//FOR OFFICIAL USE ONLY

Research Support Division Program Overview Mission Vision Consult with stakeholders across the VA enterprise participating in research programs providing guidance in complying with research information security policy. Respond to research security needs by using a risk management approach to develop and implement enterprise information security standards, guidelines, and procedures that address security objectives that are in alignment with the customer’s business considerations and objectives. Provide stakeholders participating in VA Research with a transparent and risk-based security process that uses security controls to protect research data, but not as a reason to limit the appropriate research uses of the data. Identify and address data security risks to participant data while enabling VA Research to advance. Scope Stakeholders Enterprise Construct: Enterprise support is representative of research systems, protocols, applications, and projects occurring at the national and multi-site level. Collaborative and Cooperative research involving Investigators from more than one institution. Principal Investigators (Researchers) Facility ISSOs & Network ISSMs Research Staff System Owners Supporting 110 Sites accredited to conduct: Human Subject, Clinical, & Biomedical Research Animal Research Basic Science Research
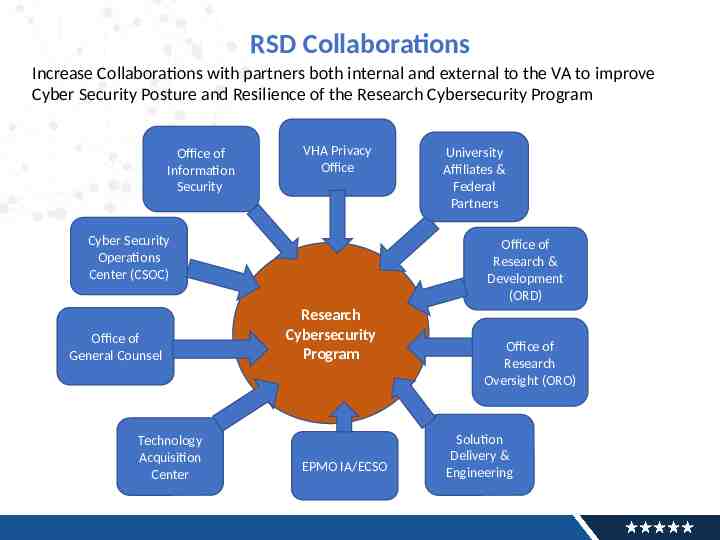
RSD Collaborations Increase Collaborations with partners both internal and external to the VA to improve Cyber Security Posture and Resilience of the Research Cybersecurity Program Office of Information Security VHA Privacy Office Cyber Security Operations Center (CSOC) Office of General Counsel Technology Acquisition Center University Affiliates & Federal Partners Office of Research & Development (ORD) Research Cybersecurity Program EPMO IA/ECSO Office of Research Oversight (ORO) Solution Delivery & Engineering
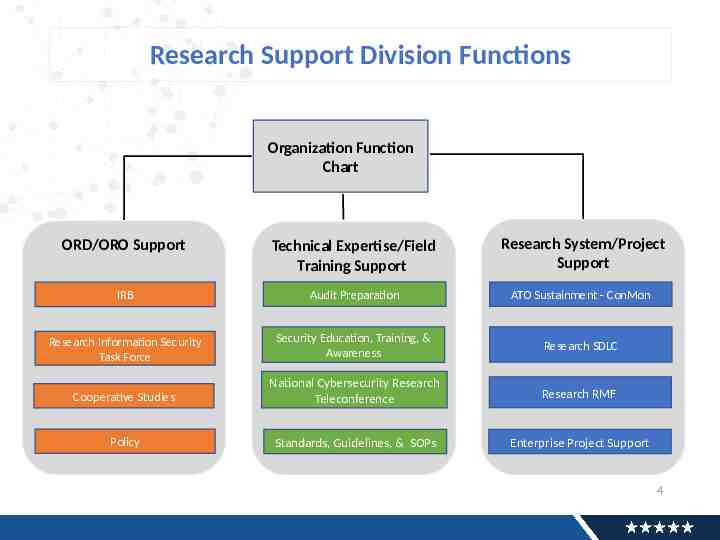
Research Support Division Functions Organization Function Chart ORD/ORO Support Technical Expertise/Field Training Support Research System/Project Support IRB Audit Preparation ATO Sustainment - ConMon Research Information Security Task Force Security Education, Training, & Awareness Research SDLC Cooperative Studies National Cybersecurity Research Teleconference Research RMF Policy Standards, Guidelines, & SOPs Enterprise Project Support 4

ORD/ORO Support ORD/ORO Support IRB Research Information Security Task Force Cooperative Studies Policy Enterprise Level Research Support Includes: Support to VACO IRB on Research Protocol, Informed Consent, Data Usage Agreement, MOU, CRADA, reviews Develops and provides input to standards, guidelines, and processes to comply with policies in support of VA Research Support to national Cooperative/Collaborative Study Programs on Research Protocol, Informed Consent, research contract security, and written data agreement reviews Identify, monitor, review and provide input to enterprise Research data/System security policy impacting the Research Data Security Program Activities Complete To-Date: Provide input to new policy i.e 1200.01, 1200.05, 1080.01 Sits as non-voting member for VACO IRB, and MAVERIC CSP IRB Completed reviews on over 200 research protocols Completed Enterprise Cybersecurity Assessments on Applications to support the standardization of ISSO security reviews (TRIAD) Established Research Information Security Task Force Charter Reviewed 50 DUA’s for inclusion of information security language. Supporting Business Owners on National Research MOU/ISAs (NIHERA, IBM Watson, University of Chicago Data Commons, NIH-All of Us, VA/DOE-MVP) 5

Technical Expertise/Field Training Support Technical Expertise/Field Training Support Audit Preparation Security Education, Training, & Awareness National Cybersecurity Research Teleconference Standards, Guidelines, & SOPs Enterprise Level Research Support Includes: Identify, manage enterprise Research assets and ensuring alignment with VA Risk Management Framework Establish and maintain an enterprise Research configuration model and baseline for systems and scientific computing devices. Identify, manage, and define role-based training competencies. Provide consistent management forums. Establish and maintain enterprise security control to protect Research Data/ Systems. Activities Complete To-Date: Conduct Monthly Teleconference (ISSO/ISSM audience) Published 3 ITWD On Demand Training Courses Published Enterprise Security Guidance documents to support standardization of ISSO security reviews (NCI Sponsored Research) Implemented Audit Preparatory Program (On-site Visits) Established MOU with the Office of Research Oversight to conduct Joint Focused Research Compliance Reviews Collaborate for completion of whitepaper draft to define scientific computing devices Collaborate for completion of CONOPs to support the loaning of GFE devices to Research participants Provide ongoing security remediation guidance for implementation of Shared Folder and File Exchange (SFFX) to comply with folder 6 permissions.

Research System/Project Support Research System/Project Support ATO Sustainment - ConMon Research SDLC Research RMF Enterprise Project Support Enterprise Level Research Support Includes: Determine, support, and sustain enterprise Research operational systems that are key drivers to the stakeholders business operations Provide ongoing security posture monitoring for authorized enterprise Research systems (ATO Support) Define, manage, and maintain standards, practices, and procedures to support enterprise Research System Owners in complying with VA Policy and security framework Provide support to System Owners with securing enterprise Research information assets and performing control selfassessments Assist System Owners with the investigations, resolution, and recovery from incidents involving enterprise Research systems Activities Complete To-Date: Supporting Continuous Monitoring for 18 Research ATOs/FISMA Projects Participated in over 20 projects for security review Developing Enterprise Research Data Security Plan Supporting ORD and OI&T in the development of a Research IT Service Catalog Supporting Research Business Owners with the Submission of 3 Enterprise STAT Waivers and supporting POA&Ms (FileMaker Pro, 7 Blaise, Go-to-Webinar)

RSD Metrics Reviewed 38 electronic case report forms(eCRF)/web portals for VA compliance. Responded to 120 request For Information (RFI) to date. Conducted 8 National Cybersecurity Research Teleconference sessions. Developed 33 Research Cybersecurity FAQs for Principal Investigators Developed 114 Research Cybersecurity FAQs for ISSOs Implemented 3 ITWD On Demand Training Courses Research Overview Security Protocol Assessments eCRF/Webportal Compliance Conducted 3 Remote and On-site RCAPP/Focused Reviews with 6 more scheduled through December 2019 Completed reviews on over 200 research protocols Participated in over 20 projects for security review Reviewed 50 DUA’s for inclusion of information security language 8

Summary of Services DUAs Data Ownership Devices i.e software, hardware, sponsor provided etc Data Storage ATOs Policy Interpretations Training & Awareness of ISSO Equipment Inventory List (EIL) MOU/ISA Central IRB participation R&DC Website reviews Access Controls (SFFX) Data Protection Data Sharing Data Transmission Incident Reporting Data Security Plan Cloud Services Scientific Computing Devices

On The Horizon Transition to the Enterprise Mission Assurance Support Service Governance, Risk, and Compliance Tool Help the VA Authorization Official and System Owners maintain cybersecurity situational awareness, manage risk, implement the VA’s Risk Management Framework (RMF), and comply with FISMA Supports Reciprocity by providing a common operating picture and a simplified enterprise architecture environment to facilitate information exchange and dynamic connection decisions Streamlines the Risk Management Framework (RMF) assessment, authorization, and connection approval processes as well as speeds the delivery of systems support business operations Centralizes management of cybersecurity activities and offers system security practitioners increased flexibility to manage system artifacts and strengthen the security posture of information systems VHA Research Benefits: Provides new capabilities to apply tailored information system security controls or overlays to special systems/devices operating within special operational environments (i.e. Research Scientific Computing Devices/Systems) Improved Governance (System Ownership & Accountability) for Enterprise Research Applications and Systems 10 Increased Secure System Interoperability and reciprocity with Federal Partners and University Affiliates

On The Horizon Enterprise Research Protocol Review & Assessment Intake Portal Development of an Enterprise Research Protocol Review & Assessment Intake Portal to facilitate the information security review for multi-site research protocols Promotes the centralization of multi-site protocol information security reviews for facility Information System Security Officers (ISSOs) and Principal Investigators (PIs) Streamlines the facility ISSO review process and aims to reduce the ISSO approval time for multi-site protocols VHA Research Benefits: Limits the duplication of effort among local facility ISSO’s involved in multi-site protocol reviews Increases consistency in the information security review processes for research facilities that are engaged in multi-site research protocols Aligns with updated 1200.01 guidance for Information Security Review criteria for Research Protocols 11

On The Horizon Migration to Research Big Data Science Platforms Support provided to VHA and OI&T in the development of architectures and information systems that enables big data science and genomic focused research (VHA Data Commons (De-identified), DOEORNL(identified), DOE-LLNL(imaging), DOE-ANL(genomic)) Support provided to Federal Partners in leveraging RMF Reciprocity for potential secure interagency and interoperable information systems Support provided to ORD Data Owners with establishing Data Access Policies and security controls for enabling greater controlled access to VA Research Data (MVP) Enable cloud based big data science population focused research to enhance the care of the veteran population at large (VA Enterprise Cloud, Commercial Cloud Platforms, etc) Promote increased infrastructures to organize, share data, and collaborate with partners including other federal agencies, industry, and academia Research Data Cloud Storage Solution Pilot Support provided to VHA and OI&T ITOPS in the development and implementation of a VA Enterprise Cloud hosted environment to accommodate the growing data storage needs for Researchers to securely store large datasets Pilot initiative to fund the migration of research data (Boston & San Francisco) to the VA Enterprise Cloud to support increased data management, sharing, archiving, retention, security, and cost effectiveness Increased research data security access management through the implementation of the Shared File & 12 File Exchange Solution

On The Horizon Research Data Science Wireless Network Support provided to VHA and OI&T ITOPS in the development of more robust secure network architectures and information systems that enables dedicated interconnections between VA and university affiliates (i.e. internet2 and eDUROAM) Reduction of substantial amount of research external connections supporting affiliate communications to a common physical infrastructure connection to Internet2 for improved customer service Reduction in time-consuming process for establishing Business Partner Extranet connections with university affiliates and provide robust research IT infrastructure for the VA Science and Research community Support integration into Internet2 Scientific Community consortium for increased collaboration, access to high speed advanced networks with federal and university affiliate researchers 13
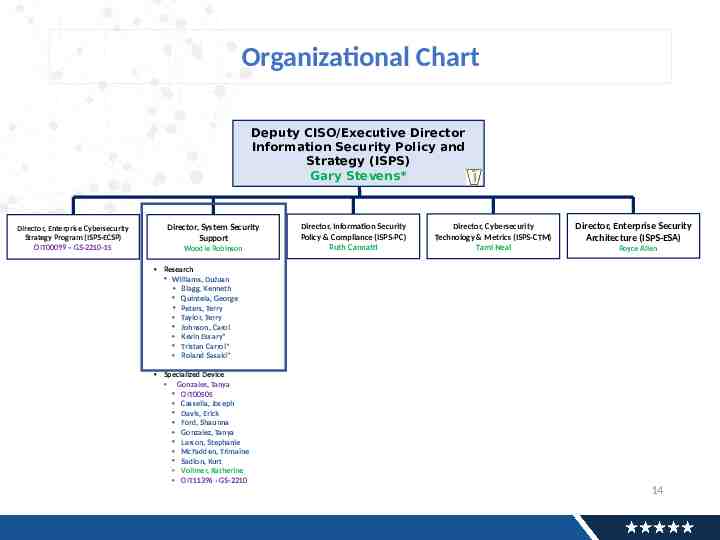
Organizational Chart Deputy CISO/Executive Director Information Security Policy and Strategy (ISPS) Gary Stevens* Director, Enterprise Cybersecurity Strategy Program (ISPS-ECSP) OIT00099 – GS-2210-15 Director, System Security Support Woodie Robinson Director, Information Security Policy & Compliance (ISPS-PC) Ruth Cannatti Director, Cybersecurity Technology & Metrics (ISPS-CTM) Tami Neal Director, Enterprise Security Architecture (ISPS-ESA) Royce Allen Research Williams, DuJuan Blagg, Kenneth Quintela, George Peters, Terry Taylor, Terry Johnson, Carol Kevin Essary* Tristan Carrol* Roland Sasaki* Specialized Device Gonzales, Tanya OIT00505 Cassella, Joseph Davis, Erick Ford, Shaunna Gonzalez, Tanya Larson, Stephanie McFadden, Trimaine Sadlon, Kurt Vollmer, Katherine OIT11396 - GS-2210 14

Q&A 15






