Questions for Chapter 6,9 Ying Zhang
21 Slides356.50 KB

Questions for Chapter 6,9 Ying Zhang

Question 1 Consider the two ways in which communication occurs between a managing entity and a managed device: requestresponse mode and trapping. What are the pros and cons of these two approaches, in terms of (1) overhead, (2) notification time when exceptional events occur, and (3) robustness with respect to lost messages between the managing entity and the device?

request-response

Request response mode will generally have more overhead (measured in terms of the number of messages exchanged) for several reasons. – First, each piece of information received by the manager requires two messages: the poll and the response. – Trapping generates only a single message to the sender. If the manager really only wants to be notified when a condition occurs, – polling has more overhead, since many of the polling messages may indicate that the waited-for condition has not yet occurred. – Trapping generates a message only when the condition occurs.

Trapping will also immediately notify the manager when an event occurs. With polling, the manager needs will need to wait for half a polling cycle (on average) between when the event occurs and the manager discovers (via its poll message) that the event has occurred.

If a trap message is lost, the managed device will not send another copy. If a poll message, or its response, is lost the manager would know there has been a lost message (since the reply never arrives). Hence the manager could repoll, if needed.

Question 2 In the book, we saw that it was preferable to transport SNMP messages in unreliable UDP datagrams. Why do you think the designers of SNMP choose UDP rather than TCP as the transport protocol of choice for SNMP?

Often, the time when network management is most needed is in times of stress, when the network may be severely congested and packets are being lost. With SNMP running over TCP, TCP's congestion control would cause SNMP to back-off and stop sending messages at precisely the time when the network manager needs to send SNMP messages.

Question 3 Consider Figure 9.9,in the text book, what would be the BER encoding of {weight,271} {lastname, ‘Jackson’}

BER: Basic Encoding Rules – specify how ASN.1-defined data objects to be transmitted – each transmitted object has Type, Length, Value (TLV) encoding
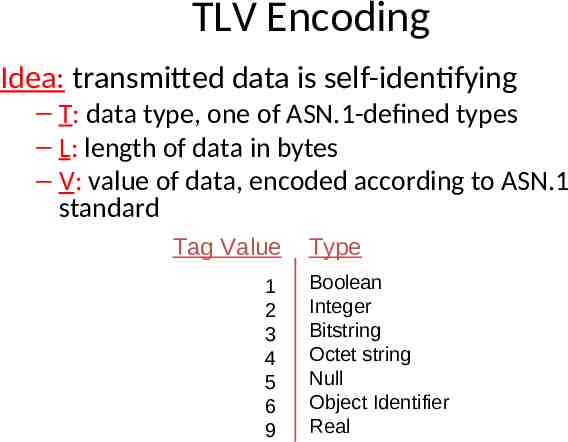
TLV Encoding Idea: transmitted data is self-identifying – T: data type, one of ASN.1-defined types – L: length of data in bytes – V: value of data, encoded according to ASN.1 standard Tag Value 1 2 3 4 5 6 9 Type Boolean Integer Bitstring Octet string Null Object Identifier Real

TLV encoding: example Value, 259 Length, 2 bytes Type 2, integer Value, 5 octets (chars) Length, 5 bytes Type 4, octet string

4 7 'J' 'a' 'c' 'k' 's' 'o' 'n' 2 2 1 15

Question 4 Consider the single-sender CDMA example in Figure 6.4 in the book. What could be the sender’s output ( for the 2 data bits shown) if the sender’s CDMA code were (1,-1,1,-1,1,1,1,-1)?

CDMA Encode/Decode sender data bits code Zi,m di.cm d0 1 -1 -1 -1 1 -1 1 1 1 -1 -1 -1 slot 1 -1 slot 1 channel output 1 -1 1 1 1 1 1 1 1 d1 -1 1 1 1 channel output Zi,m -1 -1 -1 slot 0 1 -1 -1 -1 -1 slot 0 channel output M Di Zi,m.cm m 1 received input code receiver 1 1 1 1 1 1 1 -1 -1 -1 -1 1 1 1 1 -1 -1 -1 -1 -1 1 1 1 -1 -1 -1 slot 1 M 1 1 -1 -1 -1 -1 slot 0 d0 1 d1 -1 slot 1 channel output slot 0 channel output

– Output corresponding to bit d1 [-1,1,-1,1,-1,1,-1,1] – Output corresponding to bit d0 [1,-1,1,-1,1,-1,1,-1]

Consider sender 2 in Figure 6.5, what is the sender’s output to the channel ( before it is added to the signal from sender 1), Z 2 { I,m}

CDMA: two-sender interference

Sender 2 output [1,-1,1,1,1,-1,1,1]; [ 1,1,1,1,1,-1,1,1]

Suppose that the receiver in Figure 6.5 wanted to receive the data being sent by sender 2. Show that the receiver is indeed able to recover sender 2’s data from the aggregate channel signal by using sender 2’s code

CDMA: two-sender interference






