Advancing Networks: Cloud Computing and Zero Trust Security Planning
58 Slides1.29 MB

Advancing Networks: Cloud Computing and Zero Trust Security Planning Susan Lincke

Security Planning: An Applied Approach 03/19/2024 2 External Solutions: Cloud Computing Laptop Database Cloud Computing Web Server App Server VPN Server PC

Security Planning: An Applied Approach 03/19/2024 3 Introduction to Cloud ThisThis would cost would 200/month. cost 200/month. NIST Visual Model of Cloud Computing Definition National Institute of Standards and Technology, www.cloudstandards.org

Security Planning: An Applied Approach 03/19/2024 4 Basic Cloud Services Software (SaaS): Provider runs own applications on cloud infrastructure. Platform (PaaS): Consumer provides apps; provider provides system and development environment. SaaS Cloud Software & Apps Infrastructure (laaS): Provides customers access to processing, storage, networks or other fundamental resources PaaS Your application E.g., Cloud’s OS, DB IaaS Your OS, software Cloud’s computer, hardware

Security Planning: An Applied Approach 03/19/2024 5 Various Subset Cloud Services Software (SaaS) Software As a Service Data (DaaS) Cloud Service Platform as a Service Infrastructure as a Service Retrieve DB data from cloud provider Container (Caas) Drop a VM into a Container Disaster Recovery (DRaaS) Backup Data to Cloud

Security Planning: An Applied Approach 03/19/2024 6 Additional Cloud Models: Container as a Service One PaaS implementation is the Container service Users develop a container image, or a code execution environment, for deployment. Containers may run directly on hardware or within a virtual machine. Examples include: Google’s Kubernetes Engine (GKE), Amazon’s Elastic Container Service (ECS), Azure’s Kubernetes Service (AKS), and Red Hat’s OpenShift. Programming tools automatically configure containers ensure a consistent hardened implementation by establishing policy needs and reducing configuration errors Tools include Kubernetes, Docker and Open Shift. Can enforce egress firewall rules, network logging, vulnerability testing via container image scanning, default container login, and incident/event notification methods.

Security Planning: An Applied Approach 03/19/2024 7 Additional Cloud Models: Disaster Recovery Disaster Recover as a Service (DRaaS): provides a hot-site backup service for services hosted at the customer site, potentially bringing up a site in 0-60 minutes. Also consider that the cloud does not assume redundancy Redundancy must be specified in the contract Better backup capability costs more Different versions of this service may include (Baginda et al. 2018): Backup and Restore: Backup data is sent continuously to the DRaasS, but no software is operational on the cloud (except for disaster recovery testing) Warm Backup or Pilot Light: Backup data is sent continuously and the program is loaded but zero to minimal transactions are run on the cloud.

Security Planning: An Applied Approach 03/19/2024 8 Cloud Deployment Models Private Cloud: Dedicated to one organization Community Cloud: Several organizations with shared concerns share computer facilities E.g., Financial or Medical Public Cloud: Available to the public or a large industry group Hybrid Cloud: Two or more clouds (private, community or public clouds) remain distinct but are bound together by standardized or proprietary technology

Security Planning: An Applied Approach 03/19/2024 9 Process of Deployment Define security and compliance requirements Select a cloud provider and service/deployment model Define the architecture Assess security controls Identify gaps in control Address and implement missing security controls Monitor and manage changes Define Security/Compliance Requirements Select a cloud provider & deployment model Define architecture Assess shared security responsibility: yours & cloud’s Monitor and manage changes

Security Planning: An Applied Approach 03/19/2024 10 Define Security Requirements Additional Cloud Security Issues include: Attack application External attacker Fail equipment Fail network Nature/disaster Reduced control: reliability of network, backup service May rarely accessed data to be removed to improve cloud profitability? Misconfiguration Reduce control/privacy Rogue employee Use unauthorized app Reduce priority Cloud employee/auditor Shadow IT Privacy: retrieval of personal information for curiosity or greediness. access of users’ identity, preferences, habits by cloud employees, auditors; Multitenancy: ensure data protection from other cloud customers: segmentation, isolation, policy Cloud misconfigurations (yours or theirs) vulnerabilities in software or API interfaces. Shadow IT: Are employees using unapproved apps in the cloud?

Security Planning: An Applied Approach 03/19/2024 11 Define Security Requirements Workbook Confidentiality: Security issue: Grades are released resulting in FERPA investigation. Security issue: Assignments are unknowingly copied from 1 student to another. Security issue: Cloud employee sells or gives answers to students. Privacy issue: Copied files from top student is thought to be cheating; student earns a zero. Integrity: Security issue: Submitted assignments are mixed up, lost or deleted by system failure, attacker or rogue employee. Security Issue: Ransomware deletes all homework; ransom is too high to pay; no grades are available for courses for semester. Privacy issue: Students whose work is lost suffer undeserved bad grades. Availability: Security issue: Assignments are due but students can’t access the system to submit. This is particularly problematic during homework and exam submission deadlines. Privacy issue: Students worried about not submitting on time; late grade

Security Planning: An Applied Approach 03/19/2024 12 Select Cloud Provider and Deployment Model Service Level Agreement (SLA): contract between cloud provider and customer May be personalized for smaller organization May be configurable with larger organization (e.g., programmed configuration) Ownership of data: privacy policies, security controls, monitoring performed, data location, data subpoena Audit report: Penetration testing, security/availability metrics, logs, policy change notifications Incident Response: Disaster recovery, informational reports Contract termination: at any time, data export, costs, data destruction Define Security/Compliance Requirements Select a cloud provider & deployment model Define architecture Assess shared security responsibility: yours & cloud’s Monitor and manage changes

Security Planning: An Applied Approach 03/19/2024 13 SLA: Regulatory issues What do my nation’s laws require in protecting my data? What international laws, data privacy laws and state breach laws are my data subject to? Where (e.g., which country) will my client data reside? What government intrusion, security and privacy laws might my data be subject to? What is cloud provider policy if law enforcement subpoenas a client’s sensitive information? What cloud controls are in place to address these regulations? How will breaches be notified and handled? (Ultimately the cloud customer is responsible for security) What are cloud provider privacy policies related to client data? What security controls and monitoring are provided for the client?

Security Planning: An Applied Approach 03/19/2024 14 SLA: Cloud Provider Security Implementation What controls are implemented by the cloud provider for confidentiality, integrity and availability? What controls relate to authentication, access control, digital certificate exchange, IDS, trusted platform? What network security controls exist? What policies and security implementations prevent cloud personnel from accessing and leaking client data? What third-party audit processes exist? What does the audit involve and how are results disseminated? How often are audit/compliance results provided? What have previous audit results shown? Does the cloud provider maintain and publish metrics on availability (or downtime)? What cloud tools are available for testing and monitoring of security? What protocol and restrictions exist for the cloud user to perform vulnerability and penetration testing? What types of alarm/logs does the cloud provider monitor for? Are client-system logs available to clients? Can clients monitor the usage and access of their data?

Security Planning: An Applied Approach 03/19/2024 15 SLA Incident/Disaster Recovery Issues How does the cloud provider handle disaster recovery? What are the cloud server provider policies for disaster recovery? What is included in the contractual agreements? What rates of availability does the cloud provider maintain? Can data be maintained redundantly in multiple regions? How is data synchronization achieved? Can the organization’s recovery point objectives and recovery time objectives be achieved? How is incident response handled by the cloud provider? What tools are available to clients to forensically analyze incidents?

Security Planning: An Applied Approach 03/19/2024 16 SLA Contractual Issues: Meeting Contracts, Reputation, Programmability Is the cloud provider reputable, financially stable, protected by insurance, located primarily (or entirely) in the home country? What is the cloud provider standard Service Level Agreement? Can this SLA be personalized to client’s needs? What happens at contract termination? What are the cloud provider’s data privacy policies? How does data export to another system work, what is this cost, and what are cloud provider policies for data destruction? If we are under contract to another organization, does the cloud proposal meet our contracts’ requirements? What issues does our contract specify or imply? What security APIs or form interfaces are supported to automatically configure a security configuration? Does the cloud provider support the API required by the client?

Security Planning: An Applied Approach 03/19/2024 17 Define Architecture Architectures are generally layered, consisting of the following layers: Software as a Service: Contains the presentation layer software (e.g., web user interface), API to a multitenant application with local data; Platform as a Service: Consists of integration and middleware software, including base software such as OS with database; Infrastructure as a Service: Consists of the virtual machine abstraction, hardware, networking and storage facilities. Define Requirements Select a cloud provider & deployment model Define architecture Virtualization: Virtualization used to separate services and tenants. Cloud provider may secure the hardware and hypervisor Customer secures controls within the VM environment. Multicloud system: When multiple cloud services are used, potential interface issues may result Assess shared security responsibility: yours & cloud’s Monitor and manage changes

Security Planning: An Applied Approach 03/19/2024 18 Assess Shared Security Responsibility Cloud provider, users both responsible for security, depending on cloud service model You can transfer security responsibility but not accountability cloud provider provides security for the bottom portion that it configures and manages; cloud user responsible for user part it defines and manages. Customer Data Customer Data Encryption Client Encryption Server Encryption Application Management Application Platform Management Cloud Security Alliance (CSA 2021) recommends: providers clearly define security features they implement; Users should complete a security matrix defining: controls provided by the cloud provider necessary controls they must add CSA provides a (free) baseline Cloud Controls Matrix for this process. Networks Storage/OS Hardware Firewall Configuration Network Configuration Operating System Storage/Network Infrastructure Hardware

Security Planning: An Applied Approach 03/19/2024 19 Assess Shared Responsibility Model Infrastructure as a Service Customer Data Customer Data Software as a Service Customer Data Customer Data Encryption Client Encryption Server Encryption Encryption Client Encryption Server Encryption Application Application Management Platform Management Application Application Management Platform Management Networks Firewall Configuration Network Configuration Networks Firewall Configuration Network Configuration Storage/ Compute Compute (Server) Storage/Network Storage/ Compute Compute Storage/Network Hardware Infrastructure Hardware Hardware Infrastructure Hardware

Security Planning: An Applied Approach 03/19/2024 20 Shared Responsibility Model - AWS

Security Planning: An Applied Approach 03/19/2024 21 Assess shared security responsibility: Your part (S/W) When software is developed in-house, before software deployment (Bird and Johnson 2021): static analysis: scans code automatically looking for programming vulnerabilities and bugs. container image scanning: Static scanning of container can check configuration issues and known vulnerabilities; automated testing: includes regression testing and fuzzing before release other software development techniques: risk analysis, code reviews, etc., covered in later chapters. After software deployment: runtime application self-protection: monitors an application to notify of unusual system uses or violations of policy. web application firewalls: tracks user accesses to the application and validates some input. vulnerability scanning and penetration testing: testing the run-time environment after deployment network detection and response (NDR) and network traffic analysis (NTA): monitor for unusual network traffic patterns, preferably via machine learning; host intrusion detection systems: track changes to system, files and configuration to adhere to policy.

Security Planning: An Applied Approach 03/19/2024 22 Monitor and Manage Changes in the Cloud Key Process Indicators (KPI) or Metrics related to cloud deployment may include: Number of open security vulnerabilities False positive rates of reported vulnerabilities Time to detect security vulnerabilities Time to fix security vulnerabilities Number of security vulnerabilities found after deployment Cost to fix audit issues KPIs related to cloud software deployment include: Automated test coverage Change cycle time: Time to build and deploy Rate of build delays due to security issues Define Security/Compliance Requirements Select a cloud provider & deployment model Define architecture Assess shared security responsibility: yours & cloud’s Monitor and manage changes

Security Planning: An Applied Approach 03/19/2024 23 Advanced: Dev-Sec-Ops Dev-Sec-Ops refers to Development-Security-Operations, who work closely together to secure software during development and deployment. Continuous Integration/Continuous Delivery (CI/CD): Automated build, integration, testing, and deployment ensures that both new applications and software patches are automatically configured and deployed quickly, according to compliance policies. Requires automated, thorough testing. To counter ‘software update’ attacks, SolarWinds analyzes builds against their source code to ensure correctness. Specific programming languages automatically configure and provision a software stack for deployment on the cloud. E.g., Terraform has an HCL high-level language that can be used across multiple cloud providers. Compliance testing: Asserts or guard rails are true/false tests that enable policy checking within the code, These automated test results facilitate auditing, called audit hooks. Open source tools help: AWS CloudFormation Guard, Chef InSpec, Conftest, Dev-sec.io, and Terraform Compliance. Continuous Monitoring: The Cloud Trust Protocol (CTP) defines an API that enables customers to automatically query the security status of their cloud services.

Security Planning: An Applied Approach 03/19/2024 24 Blockchains Blockchain is a solution that helps to encrypt and ensure integrity for transmissions. Applications: bitcoin, smart contracts, financial transactional requests and expanding use in Internet of Things (IoT) Blockchains provide a decentralized, system of distributed and replicated nodes. Transactions must be correctly ordered through all nodes using consensus algorithms: “unanimouslyordered transactions”

Security Planning: An Applied Approach 03/19/2024 25 How Blockchains work example: Public-style Proof-of-Work Blockchain 1. User A submitting a transaction to User B which is broadcast and saved in the blockchain memory pool. 2. A ‘peer’ miner process selects a transaction, generates a numerically complex hash to confirm the transaction and creates a block, and adds the block to the blockchain and back to the distributed memory pool. 3. Transaction processing confirms that the sender has the required finances 4. sender signs the transaction with their digital signature, providing non-repudiation. 5. Users submitting transactions pay a mining fee to incentivize miners to perform the necessary processing.

Security Planning: An Applied Approach 03/19/2024 26 Blockchain Issues Public blockchains (including Bitcoin) can be problematic: they provide anonymous access to the public. DDOS attacks have considerably slowed down processing. Integrity hash code failures have resulted in spoofed transactions costing millions. Private blockchains are more protected because users are vetted, known and trusted.

Security Planning: An Applied Approach 03/19/2024 27 Question Match the vocabulary Continuous Monitoring Shadow IT Multicloud Multitenancy Continuous Integration/ Continuous Delivery Service Level Agreement Employees may be using cloud services without their business knowing about it A customer uses multiple cloud platforms to implement software solutions Cloud build is patched and deployed automatically Customer can get security status on their cloud system An issue where a customer may share cloud hardware/software with other customers A business contract between a cloud provider and cloud user

Security Planning: An Applied Approach 03/19/2024 28 Question Match the vocabulary Continuous Monitoring Shadow IT Multicloud Multitenancy Continuous Integration/ Continuous Delivery Service Level Agreement Employees may be using cloud services without their business knowing about it A customer uses multiple cloud platforms to implement software solutions Cloud build is patched and deployed automatically Customer can get security status on their cloud system on demand An issue where a customer may share cloud hardware/software with other customers A business contract between a cloud provider and cloud user

Security Planning: An Applied Approach 03/19/2024 29 Question Container as a Service best fits under this type of model: 1. Software as a Service 2. Infrastructure as a Service 3. Platform as a Service 4. Disaster Recovery as a Service

Security Planning: An Applied Approach 03/19/2024 30 Question Shared Security Model means that: 1. The cloud provider provides full security for everything within its service model 2. The cloud user must analyze and configure for security for systems provided by both cloud provider and its own areas of control 3. The cloud user must audit areas of security only for the cloud users’ responsibility 4. The cloud user must audit areas of security for both the cloud provider and cloud user’s responsibility.

Security Planning: An Applied Approach 03/19/2024 31 Zero Trust Architectures

Security Planning: An Applied Approach 03/19/2024 32 Zero Trust After Architecture: False assumption: Before Architecture: Untrusted Network Firewall Trusted Internal Network Once within the firewall’s perimeter, the network traffic can be trusted Social Engineering/Phishing: Once inside the network, criminals find it easier to move around Deperimiterization: Limit network trust based on location Resources may lie outside the internal network: e.g., cloud services, third party Devices within the internal network may not be enterprise-managed (Bring-YourOwn-Device: BYOD) Any internal or external network may be compromised to read/modify data

Security Planning: An Applied Approach 03/19/2024 33 Zero Trust Architecture Zero Trust Architecture: Untrusted Network PEP Data 1 PEP Device 3 PEP Data 2 PEP 4 Set Assume Breach: Assume internal network is compromised Least Privilege limits access to authorized individuals Zero Trust: Evaluate on a per-transaction basis to resources: devices, data Policy Enforcement Point: Proxy validates requests to: Identity-based access: granular permissions allocated based on source identity Micro-segmentation: individual or set of resources protected by gateway Software defined network: dynamic micronetwork reconfigures as necessary

Security Planning: An Applied Approach 03/19/2024 34 Security Principles for Zero Trust Zero Trust: Evaluate on a per-transaction basis to resources (devices, data) Authentication: Confirm the subject’s identity who initiates the transaction Determine confidence in risk in subject’s identity based on: Authentication based on n-factor authentication Subject’s device configuration, location, time, etc. Subject’s permissible and traditional behavior Authorization: Determine whether the source has the required permissions Access control Authorization may change due to time-of-day, state of resource, subject’s behavior

Security Planning: An Applied Approach 03/19/2024 35 Zero Trust Principles (Part 1) All data sources and computing services are considered resources: All enterprise-owned resources should be carefully classified All communications are secured regardless of network location: All transmissions inside or outside an enterprise network are equally subject to CIA. Access to individual enterprise resources is granted on a per-session basis: Authentication is provided on a per resource basis (not per transaction). All resource authentication and authorization are dynamically and strictly enforced before access is allowed: Policy and risk decide (re)authentication and permissions

Security Planning: An Applied Approach 03/19/2024 36 Zero Trust Principles (Part 2) Access to resources is determined by a dynamic policy: Risk is evaluated based on multiple factors, such as client identity, service requested, asset configuration, past history and other situational factors. The enterprise monitors and measures the integrity and security posture of all owned and associated assets: All devices and assets must be monitored for intrusion, vulnerabilities, patching; associated assets include bring-your-own-device The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications and uses it to improve its security posture. Risk must be determined by monitoring the current state of the enterprise network.
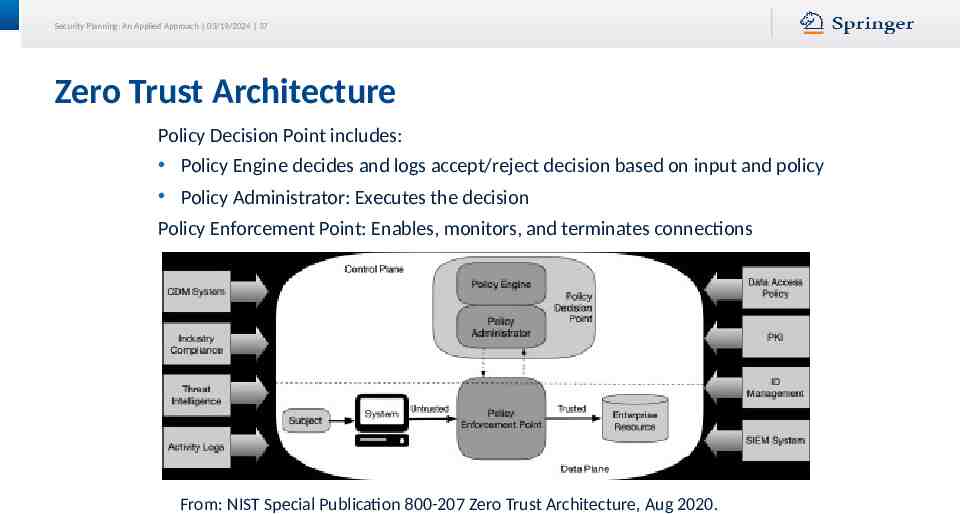
Security Planning: An Applied Approach 03/19/2024 37 Zero Trust Architecture Policy Decision Point includes: Policy Engine decides and logs accept/reject decision based on input and policy Policy Administrator: Executes the decision Policy Enforcement Point: Enables, monitors, and terminates connections From: NIST Special Publication 800-207 Zero Trust Architecture, Aug 2020.

Security Planning: An Applied Approach 03/19/2024 38 Zero Trust Inputs – Zero Trust Analysis Access Policies: Policy and permissions for access control Industry Compliance System: Policy related to regulation, such as HIPAA, Gramm-Leach-Bliley, FISMA, etc. ID Management system: Manages user accounts and identity (e.g., Microsoft Lightweight Directory Access Protocol or LDAP) with associated roles and permissions Policy Enterprise Public Key Infrastructure: Generates certificates for use with authentication/authorization Security Information & Event Management (SIEM): Network & system activity logs Thread Intelligence Feed: Internal or external sources of newly found threats, such as malware or current attacks. Continuous diagnostics and mitigation (CDM) system: Monitors vulnerabilities, patching, metrics collection Identity Threats

Security Planning: An Applied Approach 03/19/2024 39 ZTA Policy Decision Point Policy Decision Point includes: Policy Engine: Makes accept/reject decision. Best to track Subject history to make good decisions: Policy Decision Point Policy Engine Policy Administrator Unusual number of accesses Unusual time or location Policy Administrator: Informs PEP to establish and/or close communication between Subject and Resource Policy Enforcement Point (PEP)

Security Planning: An Applied Approach 03/19/2024 40 Zero Trust Architecture (ZTA) Software Defined Network: Configuration Transaction Request Actual transaction Subject Enterprise System with Agent: Interfaces with PA/PE Policy Administrator/ Policy Engine: Decision EvaluateTransaction( request, policy, input) Policy Enforcement Point: Gateway ensures all transactions are approved Resource or Set of resources

Security Planning: An Applied Approach 03/19/2024 41 Varying Zero Trust Architectures Identity-based access: granular permissions allocated based on source identity Useful for Cloud Services Agent may be separate from local device Agent may be in a container or VM Little visibility into client system configuration Micro-segmentation: individual or set of resources protected by gateway Legacy systems use gateways serving multiple resources Higher possibility of cross-contamination Software defined network: dynamic micro-network reconfigures as necessary PEP configures communications channel for Subject to interface with Resource (e.g., IP address/port, encryption key) PEP may be software agent within Resource or separate device

Security Planning: An Applied Approach 03/19/2024 42 Zero Trust Architecture: Network Requirements Network must be able to validate that Source device is an enterprise-owned/managed device and uses enterpriseissued credentials e.g., IP/MAC address can be spoofed Resources may only be accessed after being filtered through a Policy Enforcement Point (PEP) Resources should not be discoverable except through PEP (except network devices e.g., DNS) The data plane and control plane are logically separate. They may be physically separate also. Enterprise tracks all network data communication metadata informs PE enabling dynamically updated policy Metadata includes time, destination, device ID from data plane

Security Planning: An Applied Approach 03/19/2024 43 ZTA Network Requirements (cont’d) The Zero Trust Architecture must be scalable to support expected and increased traffic capacities It is not necessary to travel across enterprise-owned network to access a Resource E.g., Cloud implementations should not require Virtual Private Network or enterprise-infrastructure traversal. PEPs are accessible by policy-approved devices. PEPs may not be accessible by all enterprise devices (e.g., international locations)

Security Planning: An Applied Approach 03/19/2024 44 ZTA Cloud Configurations Common apps may be available in cloud (email, web) Cloud: PDP Cloud PE/PA(s) provide high availability and remote access Clouds may use different systems permission PEP is located with Resource May/may not be located with PE/PA PEP provides statistics to PE/PA PEP gets configuration for permissions from PE/PA Cloud: PEP/ Resource data Remote Worker Enterprise Network Branch Office

Security Planning: An Applied Approach 03/19/2024 45 Zero Trust Planning Step 1: Inventory and assess data flows, workflows, subjects Leverage information classification and rolebased access control from Information Security Step 2: Assess risk and develop policy Test a small application first Expand applications as the organization gains confidence in zero trust. Pilot applications that may benefit from zero trust: require higher levels of confidentiality and integrity are accessed often remotely small application(s) with lower availability/reliability requirements Inventory & assess data flows, workflows, subjects Assess risk Develop policy Deploy & monitor operations

Security Planning: An Applied Approach 03/19/2024 46 Zero Trust Planning Step 3: Develop policy zero trust can: further restrict access to roles verify device configurations tighten policy around selected application(s) but do not hinder valid access Issue: find technical compatibility between ZT components Step 4: Deploy and monitor operations helpful to be lenient in policies initially use greater logging and monitoring while: training to recognize anomalous behavior automatically Inventory & assess data flows, workflows, subjects Assess risk Develop policy Deploy & monitor operations

Security Planning: An Applied Approach 03/19/2024 47 Vocabulary – Zero Trust Network Micro-segmentation Software defined network Policy enforcement point Policy decision point Identity-based access a) A configuration where individual or small set of resources are protected by a Policy Enforcement Points (PEP) b) A component in a zero-trust network responsible for evaluating the appropriateness of a transaction, based on user authorization, past history, recent actions, current threats c) A configuration where granular permissions are allocated based on source identity (login, IP, time, date) d) A configuration where micro-networks may be reconfigured dynamically as necessary e) A component in a zero-trust network that serves as a firewall; implementing policy to accept or reject transactions

Security Planning: An Applied Approach 03/19/2024 48 Question Which of the following might not be automatically caught by a full Zero Trust implementation 1. A user executes more transactions than is allowed 2. A user stays logged in beyond their allowed work duration 3. Someone impersonates a customer using their login-password 4. Multiple SQL attacks are generated by an IP address

Security Planning: An Applied Approach 03/19/2024 49 Question The device which decides whether permissions are granted to allow the transaction is: 1. Enterprise system with agent 2. Policy Administrator/Policy Engine 3. Policy Enforcement Point 4. Decisions are granted on a per connection basis only

Security Planning: An Applied Approach 03/19/2024 50 Question The Policy Decision Point may make decisions based on: 1. User identity 2. Threats reported by SIEM 3. Changes in policy 4. All of the above

Security Planning: An Applied Approach 03/19/2024 51 Question Zero trust is meant to protect: 1. Primarily organizations who use the cloud 2. Primarily external connections to the internet 3. Protecting all internal and external connections 4. Protecting all internal and external transactions

Security Planning: An Applied Approach 03/19/2024 52 Question In what type of implementation would a Policy Decision Point update the Policy Enforcement Point that an existing IP connection should no longer be allowed: 1. Software-Defined Network 2. Micro-segmentation 3. Identity-based access 4. Cloud implementation

Security Planning: An Applied Approach 03/19/2024 53 CASE STUDY - CLOUD

Security Planning: An Applied Approach 03/19/2024 54 Step 1: Define Security and Compliance Requirements Workbook Confidentiality: Security issue: Grades are released resulting in FERPA investigation. Security issue: Assignments are unknowingly copied from 1 student to another. Security issue: Cloud employee sells or gives answers to students. Privacy issue: Copied files from top student is thought to be cheating; student earns a zero. Integrity: Security issue: Submitted assignments are mixed up, lost or deleted by system failure, attacker or rogue employee. Security Issue: Ransomware deletes all homework; ransom is too high to pay; no grades are available for courses for semester. Privacy issue: Students whose work is lost suffer undeserved bad grades. Availability: Security issue: Assignments are due but students can’t access the system to submit. This is particularly problematic during homework and exam submission deadlines. Privacy issue: Students worried about not submitting on time; late grade assigned results in course failure. Regulation: FERPA: School grades are protected. State Breach Notification: Student identifiers must be protected. Social security numbers and financial records are not maintained in this DB

Security Planning: An Applied Approach 03/19/2024 55 Step 2: Select a Cloud Provider and Service/Deployment Model Regulatory Issues Workbook Questions What do my nation’s laws require in protecting my data? What international laws, data privacy laws and state breach laws are my data subject to? Where (e.g., which country) will my client data reside, and what government intrusion, security and privacy laws might my data be subject to? What is cloud provider policy if law enforcement subpoenas a client’s sensitive information? What cloud controls are in place to address these regulations? How will breaches be notified and handled? (Ultimately the cloud customer is responsible for security) What are cloud provider privacy policies related to client data? What security controls and monitoring are provided for the client? Notes

Security Planning: An Applied Approach 03/19/2024 56 Cloud Provider Security Implementation Workbook Questions What controls are implemented by the cloud provider for confidentiality, integrity and availability, or more specifically, authentication, access control, digital certificate exchange, IDS, trusted platform? What network security controls exist? What policies and security implementations prevent cloud personnel from accessing and leaking client data? What third-party audit processes exist? What does the audit involve and how are results disseminated? How often are audit/compliance results provided? What have previous audit results shown? Does the cloud provider maintain and publish metrics on availability (or downtime)? What cloud tools are available for testing and monitoring of security? What protocol and restrictions exist for the cloud user to perform vulnerability and penetration testing? What types of alarm/logs does the cloud provider monitor for? Are client-system logs available to clients? Can clients monitor the usage and access of their data? Notes

Security Planning: An Applied Approach 03/19/2024 57 Cloud Incident and Disaster Recovery Workbook Questions What rates of availability does the cloud provider maintain? Can data be maintained redundantly in multiple regions? How is data synchronization achieved? Can the organization’s recovery point objectives and recovery time objectives be achieved? What are the cloud server provider policies for disaster recovery? How does the cloud provider handle disaster recovery? What is included in the contractual agreements? How is incident response handled by the cloud provider? What tools are available to clients to forensically analyze incidents? Notes

Security Planning: An Applied Approach 03/19/2024 58 Contractual Issues – Cloud Provider and Third Party Workbook Questions What is the cloud provider standard Service Level Agreement? Can this SLA be personalized for my needs? If we are under contract to another organization, does the proposed cloud implementation meet our contracts’ requirements? What issues does our contract specify or imply? What happens at contract termination? What are the cloud provider’s data privacy policies? How does data export to another system work, what is this cost, and what are cloud provider policies for data destruction? Is the cloud provider reputable, financially stable, protected by insurance, located primarily (or entirely) in the home country? What recent legal cases have involved the cloud provider? (casetext.com can provide details.) What security APIs or form interfaces are supported to automatically configure a security configuration? Does the cloud provider support the API required by the client? What kind of scripting and key management options does the cloud provider provide? Notes






