Project Portfolio Management Solution Implementer Guide
48 Slides6.16 MB

Project Portfolio Management Solution Implementer Guide
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
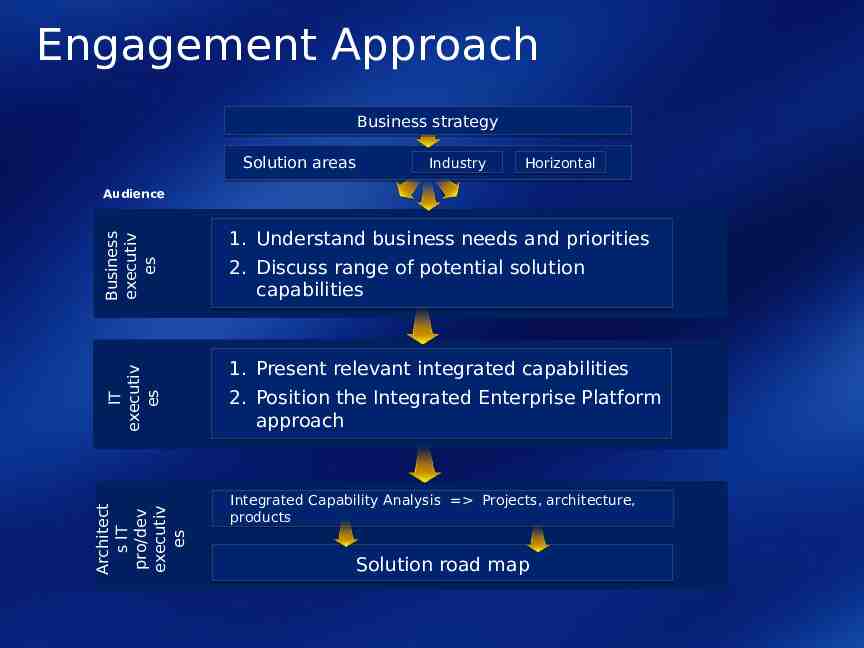
Engagement Approach Business strategy Solution areas Industry Horizontal Business executiv es 1. Present relevant integrated capabilities 2. Position the Integrated Enterprise Platform approach Architect s IT pro/dev executiv es 1. Understand business needs and priorities 2. Discuss range of potential solution capabilities IT executiv es Audience Integrated Capability Analysis Projects, architecture, products Solution road map
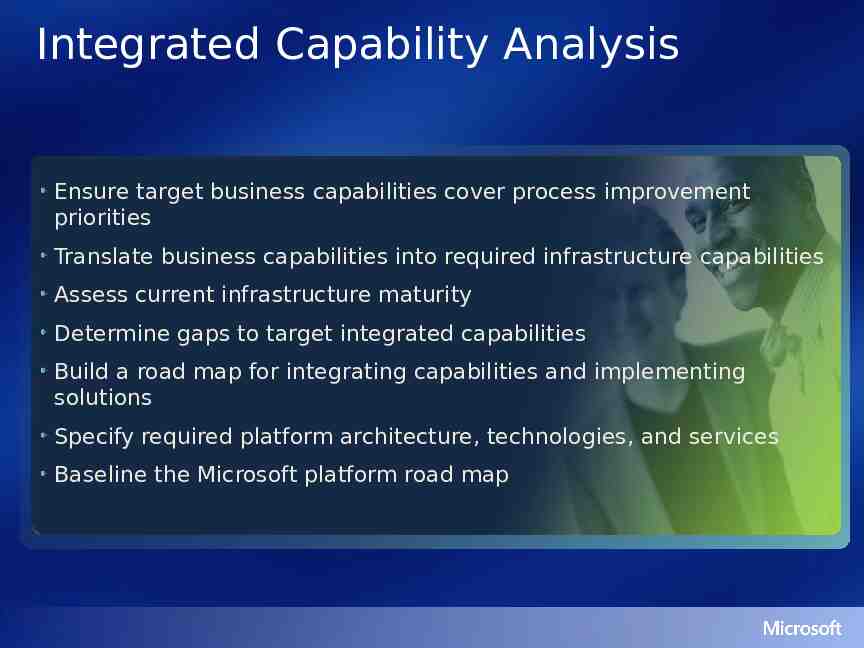
Integrated Capability Analysis Ensure target business capabilities cover process improvement priorities Translate business capabilities into required infrastructure capabilities Assess current infrastructure maturity Determine gaps to target integrated capabilities Build a road map for integrating capabilities and implementing solutions Specify required platform architecture, technologies, and services Baseline the Microsoft platform road map

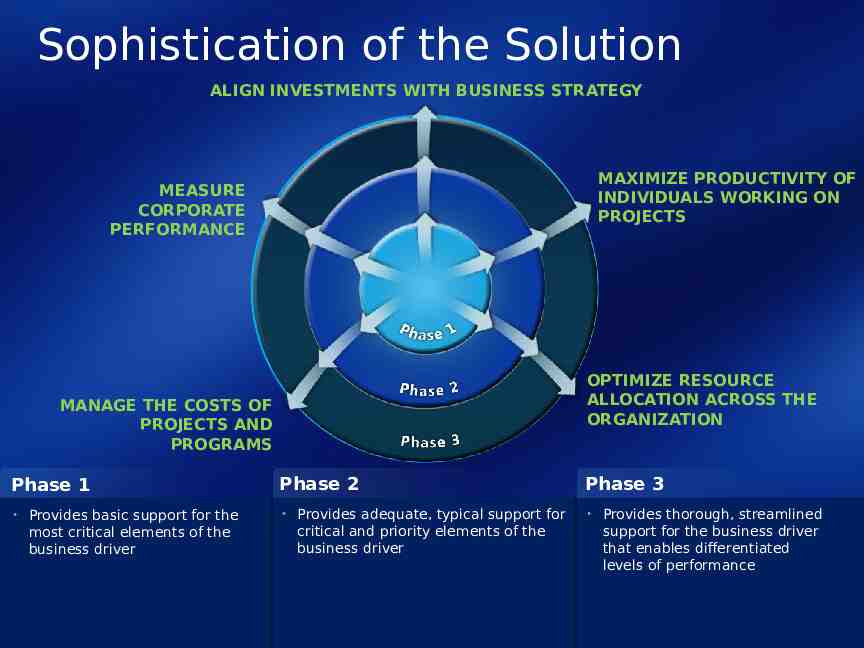
Platform Support for Priority Business Capabilities Business Driver ALIGN INVESTMENTS WITH BUSINESS STRATEGY MEASURE CORPORATE PERFORMANCE Phase 1 Phase 2 Communicate business strategy effectively by using diagrams, charts, and written descriptions, and then collect, update, and manage initiative requests and related information via common productivity tools and business drawing tools, and then storing information in centralized and categorized libraries Collect project investment requests and establish a system to rank and assess them via a centralized managed list or spreadsheet tool Prove investment worth by defending investment positioning via spreadsheet or listbased models that use objective formulas for scoring Collect and objectively prioritize business drivers, and then drive consensus among executives via a business driver collection tool and a pair-wise comparison matrix Identify and select project investment requests by scoring that is aligned with business drivers via a Web-based portfolio inventory tool Select investments based on rational decisions rather than emotions via structured portfolio optimization analysis, by using what-if scenarios to identify tradeoffs and select the optimal portfolio under varying budgetary and business constraints Report corporate effectiveness or failure via project reports that are created from standardized templates in common productivity applications, and are stored in centralized locations Get early performance information regarding projects via on-demand time-phased reports, charts and health indicators, and status reports that are created in common productivity applications Identify and collect information about project risks and issues via managed-list repositories or automated surveys that capture data specific to the risk Make KPIs and underlying performance data available organization-wide via integration from across various project repositories for a consolidated view of information regarding the scoring of business initiatives Make better decisions by standardizing work effort reporting via customized reports that show metrics such as progress and track actuals by percentage of work complete, actual work done, and work remaining; and that show budget vs. forecast built from multidimensional "cubes" from the database Identify and fix problems at a project level by using risk mitigation via a Web-based risk management tool that associates risks and issues with tasks and projects, so that teams can collaborate on specifying probability and Phase 3 Provide organizational control and action according to business strategy via a portfolio management system that prioritizes initiatives for the upcoming planning period; uses the Business Alignment Framework to optimize budgets and recommend portfolios; employs sophisticated optimization algorithms to determine the optimal project or program portfolio under varying budget and business constraints; and uses advanced portfolio analytical techniques Enable a rationalized approach to choose which investments have the highest return and alignment to business strategy via investment maps to effectively evaluate competing investments from multiple perspectives, by using methodologies such as the Business Alignment Framework to optimize budgets and recommend portfolios; and sophisticated optimization algorithms to determine the optimal project or program portfolio under varying budget and business constraints Enhance the business value of the portfolio, to ensure that the mix of investments aligns to established business strategy via performing advanced portfolio optimization analysis such as Efficient Frontier modeling, to identify and break constraints and gain more business value from the portfolio; providing enterprisewide integration across various project repositories; and transferring information about the scoring of business initiatives to ERP systems Automate action on trends, alerts, and performance via portfolio dashboards and scorecards that show the contribution of the portfolio, for decision-making through trend and performance analysis Transmit work effort to LOB and financial systems, pull metrics from financial systems, and combine the results in a comprehensive corporate reporting portal via integration packages that feed to and from project databases and push information into business intelligence portals and reporting applications Build tools to support a comprehensive risk management program via risk dashboards that use heat maps to provide real-time data to identify risks, and workflow-based approaches to manage and aggregate risk, including

Platform Support for Priority Business Capabilities Business Driver MANAGE THE COSTS OF PROJECTS AND PROGRAMS Phase 1 Measure financial performance per project via spreadsheet-based reporting and analysis for measuring performance Maintain a list of projects that is distributed to executives across the organization via a centralized managed-list repository, table, or spreadsheet to show the top-line status of projects Track organization-wide budget performance via desktop spreadsheets that are stored in a centralized location Phase 2 Track financial performance consistently across all projects and initiatives via server-enforced data entry rules in the project management system and enterprise-wide reporting dashboards to show actuals vs. forecasts Eliminate duplicate work effort by making work performed and the results more visible via enterprise search that uses standardized keywords and portfolio views to show all current and proposed work and via graphical representations of project portfolios and initiative work Select investments based on prioritized business value and budget via a portfolio selection system that uses a pair-wise comparison tool to objectively assign value to business drivers, provides cost-sensitive resource allocation based on business initiatives, and prioritizes initiatives for the upcoming planning period Phase 3 Ensure that project financial data automatically flows into and from financial systems via a real-time integration framework that is built on standard Web services to enable connectivity, data access, and event handling between the project management system and other applications with a bi-directional feed to general ledger systems, to compare corporate accounting to project accounting Reduce effort on low-value projects and programs via reports and scorecards for ratio analysis of cost (spend) and benefits; tracking portfolio return on investment (ROI); dynamic assessment of the impact on the project or program portfolio; monitoring the performance of each investment to ensure realization of forecasted benefits; and ongoing alignment and portfolio optimization to enable selection of the right programs and to halt existing programs which allows pending programs to begin Plan demand-management scenarios and make informed decisions about outsourcing via a portfolio management system that uses an efficient frontier analysis to identify and break constraints that prohibit achievement of an optimal portfolio; employs sophisticated optimization algorithms to determine the optimal project or program portfolio under varying budget and business constraints; and uses advanced portfolio analysis techniques

Platform Support for Priority Business Capabilities Business Driver OPTIMIZE RESOURCE ALLOCATION ACROSS THE ORGANIZATION Phase 1 Assess capacity vs. demand on a skill level via spreadsheets or managed-list repositories to collect skill-set data Assign resources as they're needed without formal processes via spreadsheets or project-oriented views of managed lists Track resource performance per project manually via e-mail collaboration by enabling project managers and team members to send and receive task status information Phase 2 Find the right people based on matching their skills, identify optimal project start dates, and assess when to delay projects via an enterprise project management system that centrally stores all resource information including assignments, usage, availability, and skills across the organization; and then selects resources from the enterprise resource database based on criteria such as availability, skills, and location Select the right resource based on skill set and availability, make resource assignments centrally visible, and communicate effectively with resources via an enterprise project management tool that sends task reminders through e-mail; centrally stores all resource information including assignments, usage, availability, and skills; defines custom report templates; allows for online task delegation from leads to team members or peer-to-peer as needed through a Web-based portal; and offers customizable dashboards for resource allocation and availability Automate resource tracking via an enterprise project management tool resource center that helps managers understand the impact of assigning a resource and gain control when they level resources; uses customizable time sheets to accommodate different organizational structures and processes; publishes assignment information on enterprise portals; allows team members to enter time reports directly from their e-mail client; and uses customizable report Phase 3 Understand organizational capabilities across work management scenarios, make headcount and outsourcing decisions, and normalize capabilities decisions from multiple sources via integration with an enterprise project management system that loads data to and from HR systems to perform a strategic capabilities analysis Make smart scheduling decisions about the planning horizon based on forecasted projects and programs via a portfolio management tool that offers cost-sensitive resource allocation based on business initiatives, and consolidates all investments in a central repository to help ensure that executives gain visibility, insight, and control across the entire portfolio, as they assess the capabilities of future work Plan demand-management scenarios and make informed decisions about outsourcing via an enterprise project management tool resource center that builds custom reports to show resource allocation, so managers can assess the resource needs of the organization

Platform Support for Priority Business Capabilities Business Driver MAXIMIZE PRODUCTIVITY OF INDIVIDUALS WORKING ON PROJECTS Phase 1 Increase worker productivity and the consistency of deliverables via custom templates in desktop productivity tools that support project execution; and then store deliverables in centralized locations Enable project teams to understand a basic schedule and deadlines for work assignments via a project management tool or a managed list with a project-oriented view to create project plans and communicate easily with team members and other stakeholders Phase 2 Collectively create, find, and store project artifacts in real time via project-specific Web-based portals that have an integrated portfolio of collaboration and communication services to connect with employees information, processes, and systems; to create, collect, update, and manage relevant resources in categorized libraries; and to integrate project data into enterprise-wide search results based on common metadata to make managed work more visible Ensure that project schedules and deadlines are enforced via an enterprise project management tool with customizable time sheets; custom report templates and project views to monitor planned vs. actual schedules and the achievement of project milestones; collaborative publishing of assignment and status information on enterprise portals, including the communication of scheduling issues; and collection of actual work effort reports through Web-based or e-mail-based forms Phase 3 Improve cross-team collaboration via making reports and data available through Web-based dashboards and shared workflow; searching for subject matter experts across the company and partners based on expertise and roles; and using development tools that support a consistent and compliant application life cycle that enables asset reuse Provide a single interface to enter time information, and automatically post employee work data in billing systems via integration with an enterprise project management tool that collects data from various project repositories to offer a consolidated view, and provides customizable timesheets that gather billing and project information from various data sources
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
Sophistication of the Solution ALIGN INVESTMENTS WITH BUSINESS STRATEGY MAXIMIZE PRODUCTIVITY OF INDIVIDUALS WORKING ON PROJECTS MEASURE CORPORATE PERFORMANCE OPTIMIZE RESOURCE ALLOCATION ACROSS THE ORGANIZATION MANAGE THE COSTS OF PROJECTS AND PROGRAMS Phase 1 Provides basic support for the most critical elements of the business driver Phase 2 Provides adequate, typical support for critical and priority elements of the business driver Phase 3 Provides thorough, streamlined support for the business driver that enables differentiated levels of performance

Solution Guidance PHASE DEFINITION MAPPING TECHNOLOGIES CONCEPTUAL ARCHITECTURE LOGICAL ARCHITECTURE Phase Definition For each business driver, list the business challenges, solution features, and business benefits for this solution phase. Use this information and the “Support for Priority Business Capabilities” slides to structure the conversation with IT professional(s) for capturing, refining, and baselining business problems and solution functionality priorities. Mapping The Optimization mapping indicates the maturity level required for each capability of the solution to fully support the features specified in this solution phase. Use the mapping as a starting point to determine appropriate maturity levels for the solution. After mapping the solution, assess the gap between the current and desired infrastructure to: Understand the scope and sequencing of work required Organize a deployment road map Technologies Use the results of the Optimization mapping to determine the technologies required for the features and supporting capabilities specified in this solution phase. Conceptual Architecture Use this high-level, use case diagram to provide the “black box” definition of this solution phase. Customize to your solution definition during the integrated capability analysis. Logical Architecture Use this logical, component-level architecture view to show all software components and how they interact to support this solution phase. Tailor to fit your particular solution definition during the integrated capability analysis. Note: Physical architecture is covered in the Architecture Guide also used during the integrated capability analysis.
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
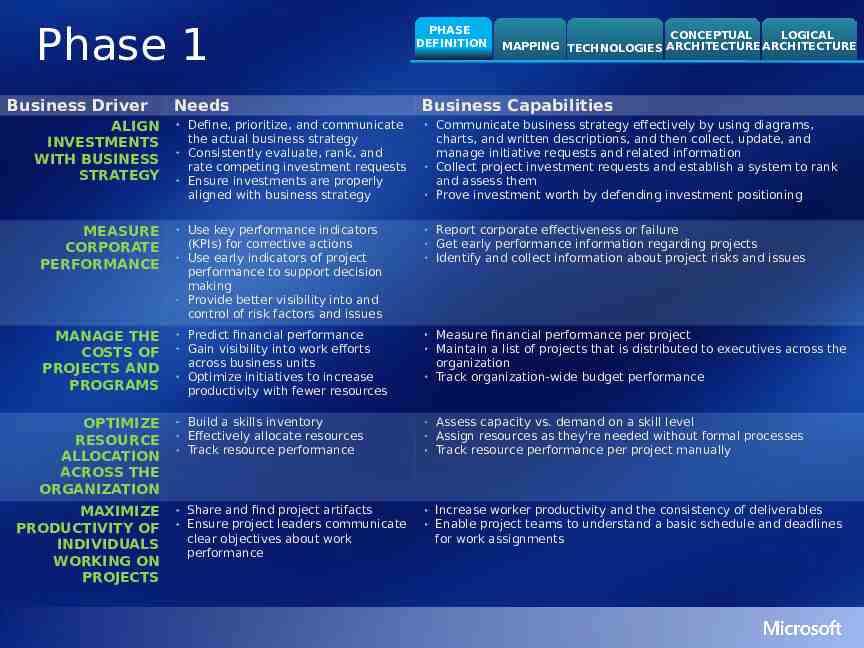
Phase 1 Business Driver Needs PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE Business Capabilities Define, prioritize, and communicate the actual business strategy Consistently evaluate, rank, and rate competing investment requests Ensure investments are properly aligned with business strategy Communicate business strategy effectively by using diagrams, charts, and written descriptions, and then collect, update, and manage initiative requests and related information Collect project investment requests and establish a system to rank and assess them Prove investment worth by defending investment positioning MEASURE CORPORATE PERFORMANCE Use key performance indicators (KPIs) for corrective actions Use early indicators of project performance to support decision making Provide better visibility into and control of risk factors and issues Report corporate effectiveness or failure Get early performance information regarding projects Identify and collect information about project risks and issues MANAGE THE COSTS OF PROJECTS AND PROGRAMS Predict financial performance Gain visibility into work efforts across business units Optimize initiatives to increase productivity with fewer resources Measure financial performance per project Maintain a list of projects that is distributed to executives across the organization Track organization-wide budget performance OPTIMIZE RESOURCE ALLOCATION ACROSS THE ORGANIZATION Build a skills inventory Effectively allocate resources Track resource performance Assess capacity vs. demand on a skill level Assign resources as they're needed without formal processes Track resource performance per project manually Share and find project artifacts Ensure project leaders communicate clear objectives about work performance Increase worker productivity and the consistency of deliverables Enable project teams to understand a basic schedule and deadlines for work assignments ALIGN INVESTMENTS WITH BUSINESS STRATEGY MAXIMIZE PRODUCTIVITY OF INDIVIDUALS WORKING ON PROJECTS
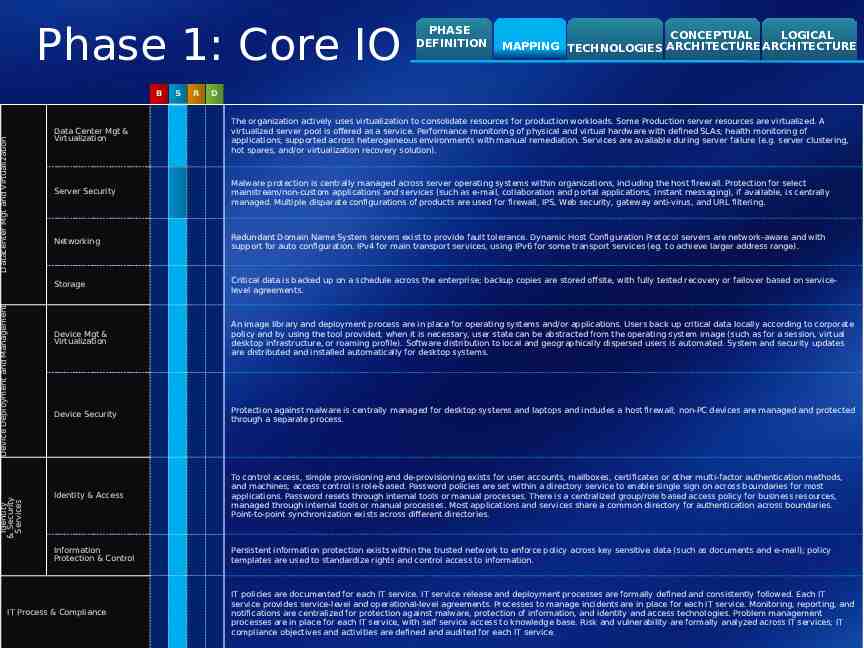
Phase 1: Core IO Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Data Center Mgt & Virtualization The organization actively uses virtualization to consolidate resources for production workloads. Some Production server resources are virtualized. A virtualized server pool is offered as a service. Performance monitoring of physical and virtual hardware with defined SLAs; health monitoring of applications; supported across heterogeneous environments with manual remediation. Services are available during server failure (e.g. server clustering, hot spares, and/or virtualization recovery solution). Server Security Malware protection is centrally managed across server operating systems within organizations, including the host firewall. Protection for select mainstream/non-custom applications and services (such as e-mail, collaboration and portal applications, instant messaging), if available, is centrally managed. Multiple disparate configurations of products are used for firewall, IPS, Web security, gateway anti-virus, and URL filtering. Networking Redundant Domain Name System servers exist to provide fault tolerance. Dynamic Host Configuration Protocol servers are network-aware and with support for auto configuration. IPv4 for main transport services, using IPv6 for some transport services (eg. to achieve larger address range). Storage Critical data is backed up on a schedule across the enterprise; backup copies are stored offsite, with fully tested recovery or failover based on servicelevel agreements. Device Mgt & Virtualization An image library and deployment process are in place for operating systems and/or applications. Users back up critical data locally according to corporate policy and by using the tool provided; when it is necessary, user state can be abstracted from the operating system image (such as for a session, virtual desktop infrastructure, or roaming profile). Software distribution to local and geographically dispersed users is automated. System and security updates are distributed and installed automatically for desktop systems. Device Security Protection against malware is centrally managed for desktop systems and laptops and includes a host firewall; non-PC devices are managed and protected through a separate process. Identity & Access To control access, simple provisioning and de-provisioning exists for user accounts, mailboxes, certificates or other multi-factor authentication methods, and machines; access control is role-based. Password policies are set within a directory service to enable single sign on across boundaries for most applications. Password resets through internal tools or manual processes. There is a centralized group/role based access policy for business resources, managed through internal tools or manual processes. Most applications and services share a common directory for authentication across boundaries. Point-to-point synchronization exists across different directories. Information Protection & Control Persistent information protection exists within the trusted network to enforce policy across key sensitive data (such as documents and e-mail); policy templates are used to standardize rights and control access to information. IT Process & Compliance IT policies are documented for each IT service. IT service release and deployment processes are formally defined and consistently followed. Each IT service provides service-level and operational-level agreements. Processes to manage incidents are in place for each IT service. Monitoring, reporting, and notifications are centralized for protection against malware, protection of information, and identity and access technologies. Problem management processes are in place for each IT service, with self service access to knowledge base. Risk and vulnerability are formally analyzed across IT services; IT compliance objectives and activities are defined and audited for each IT service.
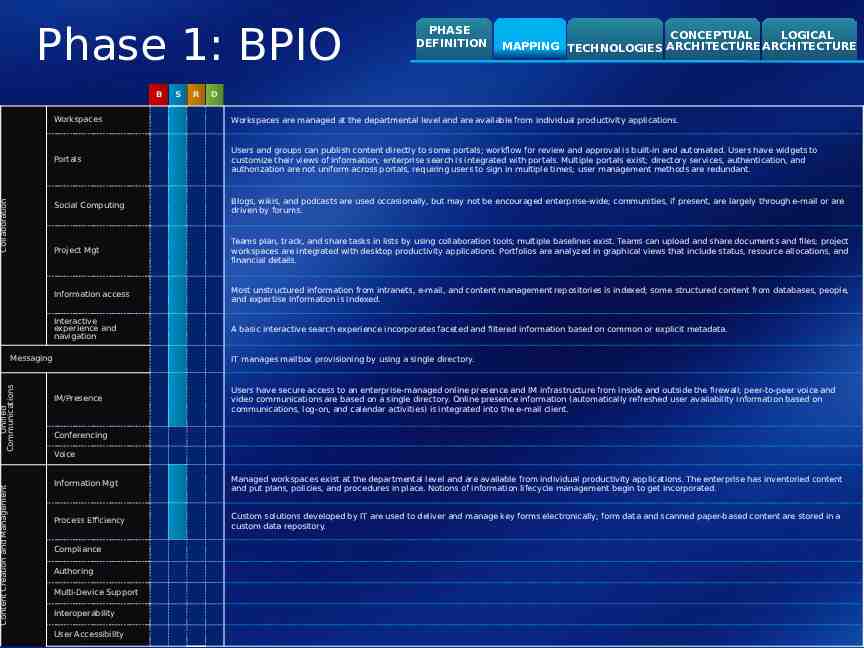
Phase 1: BPIO Collaboration B R CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Workspaces Workspaces are managed at the departmental level and are available from individual productivity applications. Portals Users and groups can publish content directly to some portals; workflow for review and approval is built-in and automated. Users have widgets to customize their views of information; enterprise search is integrated with portals. Multiple portals exist; directory services, authentication, and authorization are not uniform across portals, requiring users to sign in multiple times; user management methods are redundant. Social Computing Blogs, wikis, and podcasts are used occasionally, but may not be encouraged enterprise-wide; communities, if present, are largely through e-mail or are driven by forums. Project Mgt Teams plan, track, and share tasks in lists by using collaboration tools; multiple baselines exist. Teams can upload and share documents and files; project workspaces are integrated with desktop productivity applications. Portfolios are analyzed in graphical views that include status, resource allocations, and financial details. Information access Most unstructured information from intranets, e-mail, and content management repositories is indexed; some structured content from databases, people, and expertise information is indexed. Interactive experience and navigation A basic interactive search experience incorporates faceted and filtered information based on common or explicit metadata. Messaging Unified Communications Content Creation and Management S PHASE DEFINITION IT manages mailbox provisioning by using a single directory. IM/Presence Users have secure access to an enterprise-managed online presence and IM infrastructure from inside and outside the firewall; peer-to-peer voice and video communications are based on a single directory. Online presence information (automatically refreshed user availability information based on communications, log-on, and calendar activities) is integrated into the e-mail client. Conferencing Voice Information Mgt Managed workspaces exist at the departmental level and are available from individual productivity applications. The enterprise has inventoried content and put plans, policies, and procedures in place. Notions of information lifecycle management begin to get incorporated. Process Efficiency Custom solutions developed by IT are used to deliver and manage key forms electronically; form data and scanned paper-based content are stored in a custom data repository. Compliance Authoring Multi-Device Support Interoperability User Accessibility
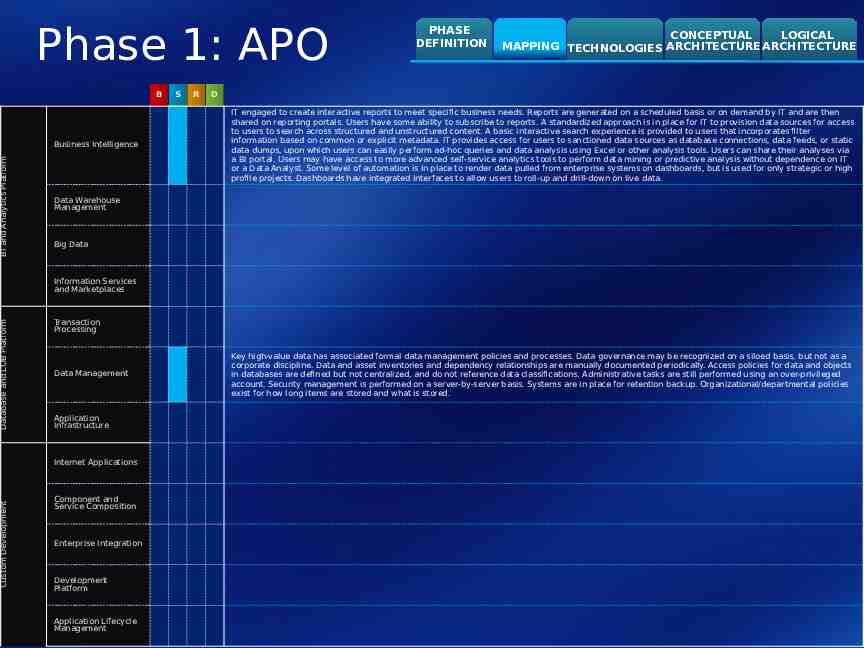
BI and Analytics Platform Database and LOB Platform Custom Development Phase 1: APO B Business Intelligence S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D IT engaged to create interactive reports to meet specific business needs. Reports are generated on a scheduled basis or on demand by IT and are then shared on reporting portals. Users have some ability to subscribe to reports. A standardized approach is in place for IT to provision data sources for access to users to search across structured and unstructured content. A basic interactive search experience is provided to users that incorporates filter information based on common or explicit metadata. IT provides access for users to sanctioned data sources as database connections, data feeds, or static data dumps, upon which users can easily perform ad-hoc queries and data analysis using Excel or other analysis tools. Users can share their analyses via a BI portal. Users may have access to more advanced self-service analytics tools to perform data mining or predictive analysis without dependence on IT or a Data Analyst. Some level of automation is in place to render data pulled from enterprise systems on dashboards, but is used for only strategic or high profile projects. Dashboards have integrated interfaces to allow users to roll-up and drill-down on live data. Data Warehouse Management Big Data Information Services and Marketplaces Transaction Processing Data Management Application Infrastructure Internet Applications Component and Service Composition Enterprise Integration Development Platform Application Lifecycle Management Key high-value data has associated formal data management policies and processes. Data governance may be recognized on a siloed basis, but not as a corporate discipline. Data and asset inventories and dependency relationships are manually documented periodically. Access policies for data and objects in databases are defined but not centralized, and do not reference data classifications. Administrative tasks are still performed using an over-privileged account. Security management is performed on a server-by-server basis. Systems are in place for retention backup. Organizational/departmental policies exist for how long items are stored and what is stored.
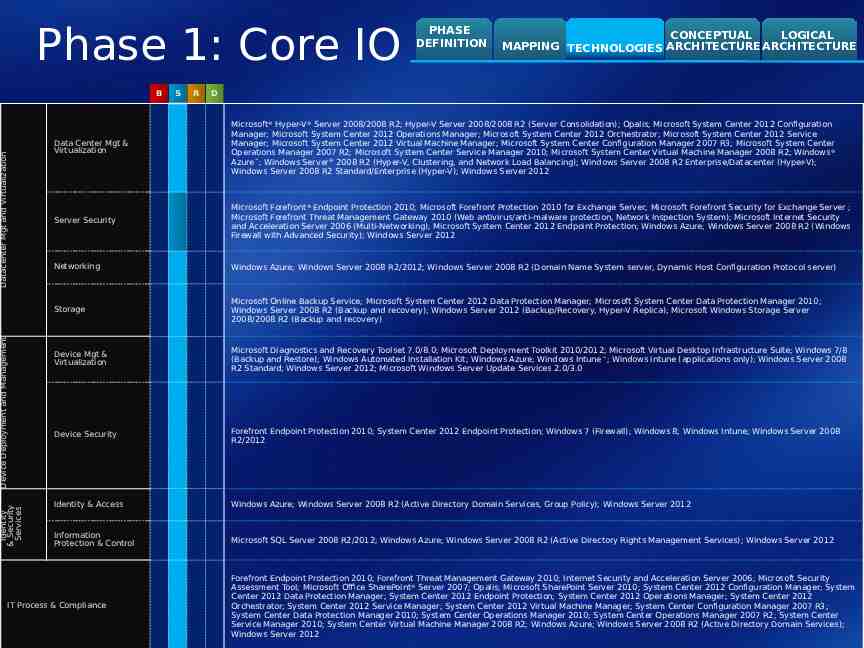
Phase 1: Core IO Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Data Center Mgt & Virtualization Microsoft Hyper-V Server 2008/2008 R2; Hyper-V Server 2008/2008 R2 (Server Consolidation); Opalis; Microsoft System Center 2012 Configuration Manager; Microsoft System Center 2012 Operations Manager; Microsoft System Center 2012 Orchestrator; Microsoft System Center 2012 Service Manager; Microsoft System Center 2012 Virtual Machine Manager; Microsoft System Center Configuration Manager 2007 R3; Microsoft System Center Operations Manager 2007 R2; Microsoft System Center Service Manager 2010; Microsoft System Center Virtual Machine Manager 2008 R2; Windows Azure ; Windows Server 2008 R2 (Hyper-V, Clustering, and Network Load Balancing); Windows Server 2008 R2 Enterprise/Datacenter (Hyper-V); Windows Server 2008 R2 Standard/Enterprise (Hyper-V); Windows Server 2012 Server Security Microsoft Forefront Endpoint Protection 2010; Microsoft Forefront Protection 2010 for Exchange Server; Microsoft Forefront Security for Exchange Server ; Microsoft Forefront Threat Management Gateway 2010 (Web antivirus/anti-malware protection, Network Inspection System); Microsoft Internet Security and Acceleration Server 2006 (Multi-Networking); Microsoft System Center 2012 Endpoint Protection; Windows Azure; Windows Server 2008 R2 (Windows Firewall with Advanced Security); Windows Server 2012 Networking Windows Azure; Windows Server 2008 R2/2012; Windows Server 2008 R2 (Domain Name System server, Dynamic Host Configuration Protocol server) Storage Microsoft Online Backup Service; Microsoft System Center 2012 Data Protection Manager; Microsoft System Center Data Protection Manager 2010; Windows Server 2008 R2 (Backup and recovery); Windows Server 2012 (Backup/Recovery, Hyper-V Replica); Microsoft Windows Storage Server 2008/2008 R2 (Backup and recovery) Device Mgt & Virtualization Microsoft Diagnostics and Recovery Toolset 7.0/8.0; Microsoft Deployment Toolkit 2010/2012; Microsoft Virtual Desktop Infrastructure Suite; Windows 7/8 (Backup and Restore); Windows Automated Installation Kit; Windows Azure; Windows Intune ; Windows Intune (applications only); Windows Server 2008 R2 Standard; Windows Server 2012; Microsoft Windows Server Update Services 2.0/3.0 Device Security Forefront Endpoint Protection 2010; System Center 2012 Endpoint Protection; Windows 7 (Firewall); Windows 8; Windows Intune; Windows Server 2008 R2/2012 Identity & Access Windows Azure; Windows Server 2008 R2 (Active Directory Domain Services, Group Policy); Windows Server 2012 Information Protection & Control Microsoft SQL Server 2008 R2/2012; Windows Azure; Windows Server 2008 R2 (Active Directory Rights Management Services); Windows Server 2012 IT Process & Compliance Forefront Endpoint Protection 2010; Forefront Threat Management Gateway 2010; Internet Security and Acceleration Server 2006; Microsoft Security Assessment Tool; Microsoft Office SharePoint Server 2007; Opalis; Microsoft SharePoint Server 2010; System Center 2012 Configuration Manager; System Center 2012 Data Protection Manager; System Center 2012 Endpoint Protection; System Center 2012 Operations Manager; System Center 2012 Orchestrator; System Center 2012 Service Manager; System Center 2012 Virtual Machine Manager; System Center Configuration Manager 2007 R3; System Center Data Protection Manager 2010; System Center Operations Manager 2010; System Center Operations Manager 2007 R2; System Center Service Manager 2010; System Center Virtual Machine Manager 2008 R2; Windows Azure; Windows Server 2008 R2 (Active Directory Domain Services); Windows Server 2012
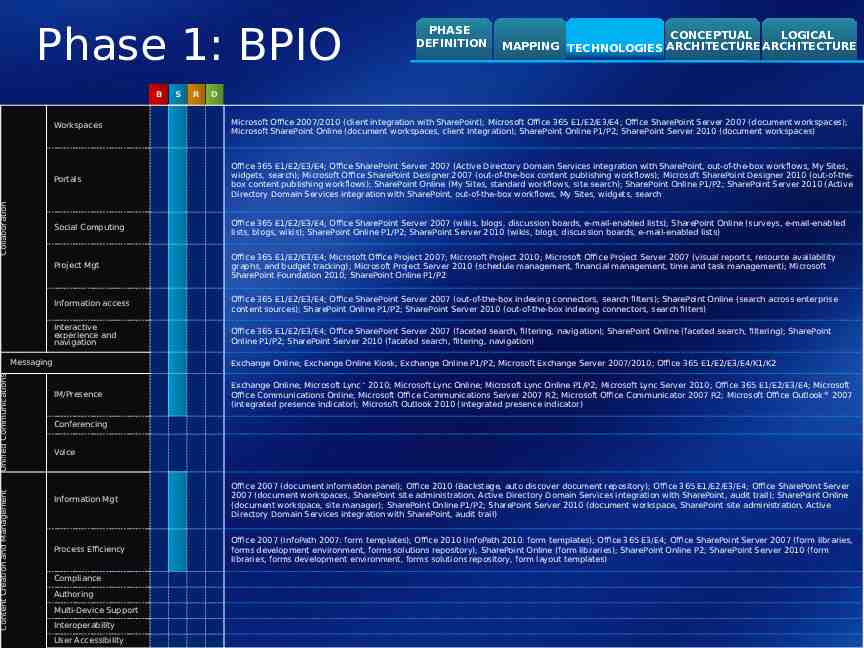
Phase 1: BPIO Content Creation and Management Unified Communications Collaboration B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Workspaces Microsoft Office 2007/2010 (client integration with SharePoint); Microsoft Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (document workspaces); Microsoft SharePoint Online (document workspaces, client integration); SharePoint Online P1/P2; SharePoint Server 2010 (document workspaces) Portals Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (Active Directory Domain Services integration with SharePoint, out-of-the-box workflows, My Sites, widgets, search); Microsoft Office SharePoint Designer 2007 (out-of-the-box content publishing workflows); Microsoft SharePoint Designer 2010 (out-of-thebox content publishing workflows); SharePoint Online (My Sites, standard workflows, site search); SharePoint Online P1/P2; SharePoint Server 2010 (Active Directory Domain Services integration with SharePoint, out-of-the-box workflows, My Sites, widgets, search Social Computing Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (wikis, blogs, discussion boards, e-mail-enabled lists); SharePoint Online (surveys, e-mail-enabled lists, blogs, wikis); SharePoint Online P1/P2; SharePoint Server 2010 (wikis, blogs, discussion boards, e-mail-enabled lists) Project Mgt Office 365 E1/E2/E3/E4; Microsoft Office Project 2007; Microsoft Project 2010; Microsoft Office Project Server 2007 (visual reports, resource availability graphs, and budget tracking); Microsoft Project Server 2010 (schedule management, financial management, time and task management); Microsoft SharePoint Foundation 2010; SharePoint Online P1/P2 Information access Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (out-of-the-box indexing connectors, search filters); SharePoint Online (search across enterprise content sources); SharePoint Online P1/P2; SharePoint Server 2010 (out-of-the-box indexing connectors, search filters) Interactive experience and navigation Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (faceted search, filtering, navigation); SharePoint Online (faceted search, filtering); SharePoint Online P1/P2; SharePoint Server 2010 (faceted search, filtering, navigation) Messaging Exchange Online; Exchange Online Kiosk; Exchange Online P1/P2; Microsoft Exchange Server 2007/2010; Office 365 E1/E2/E3/E4/K1/K2 IM/Presence Exchange Online; Microsoft Lync 2010; Microsoft Lync Online; Microsoft Lync Online P1/P2; Microsoft Lync Server 2010; Office 365 E1/E2/E3/E4; Microsoft Office Communications Online; Microsoft Office Communications Server 2007 R2; Microsoft Office Communicator 2007 R2; Microsoft Office Outlook 2007 (integrated presence indicator); Microsoft Outlook 2010 (integrated presence indicator) Conferencing Voice Information Mgt Office 2007 (document information panel); Office 2010 (Backstage, auto discover document repository); Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (document workspaces, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail); SharePoint Online (document workspace, site manager); SharePoint Online P1/P2; SharePoint Server 2010 (document workspace, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail) Process Efficiency Office 2007 (InfoPath 2007: form templates); Office 2010 (InfoPath 2010: form templates); Office 365 E3/E4; Office SharePoint Server 2007 (form libraries, forms development environment, forms solutions repository); SharePoint Online (form libraries); SharePoint Online P2; SharePoint Server 2010 (form libraries, forms development environment, forms solutions repository, form layout templates) Compliance Authoring Multi-Device Support Interoperability User Accessibility
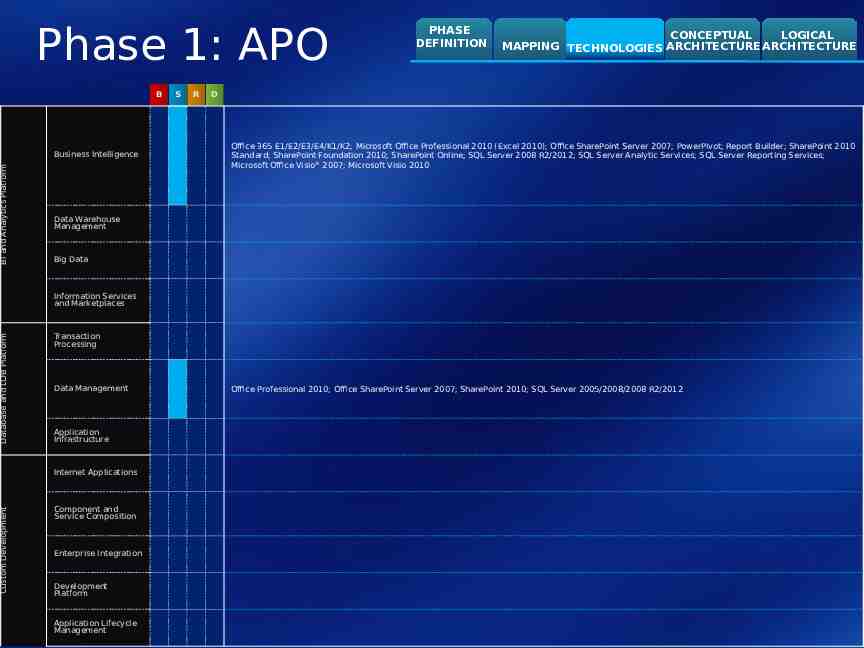
BI and Analytics Platform Database and LOB Platform Custom Development Phase 1: APO B Business Intelligence S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Office 365 E1/E2/E3/E4/K1/K2; Microsoft Office Professional 2010 (Excel 2010); Office SharePoint Server 2007; PowerPivot; Report Builder; SharePoint 2010 Standard; SharePoint Foundation 2010; SharePoint Online; SQL Server 2008 R2/2012; SQL Server Analytic Services; SQL Server Reporting Services; Microsoft Office Visio 2007; Microsoft Visio 2010 Data Warehouse Management Big Data Information Services and Marketplaces Transaction Processing Data Management Application Infrastructure Internet Applications Component and Service Composition Enterprise Integration Development Platform Application Lifecycle Management Office Professional 2010; Office SharePoint Server 2007; SharePoint 2010; SQL Server 2005/2008/2008 R2/2012
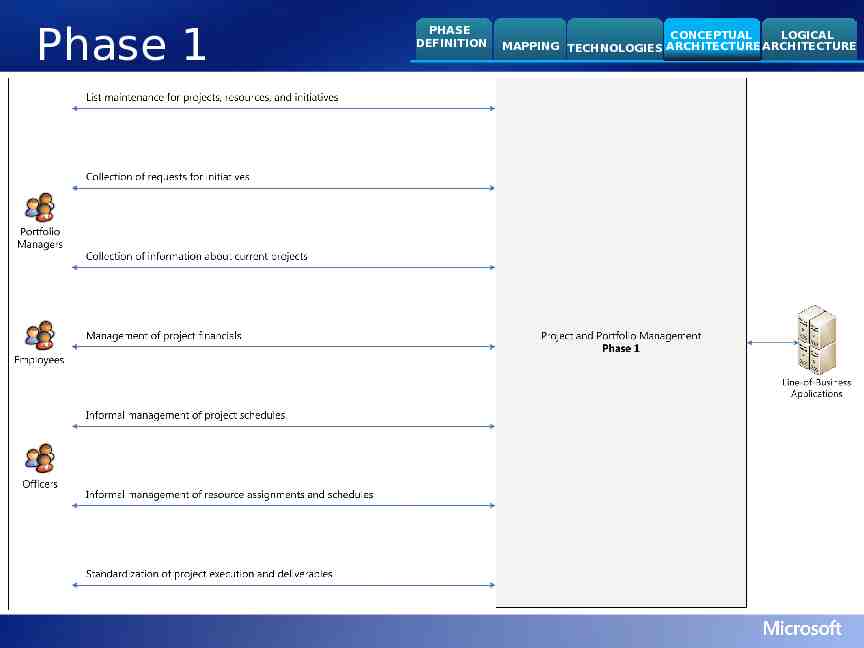
Phase 1 PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE
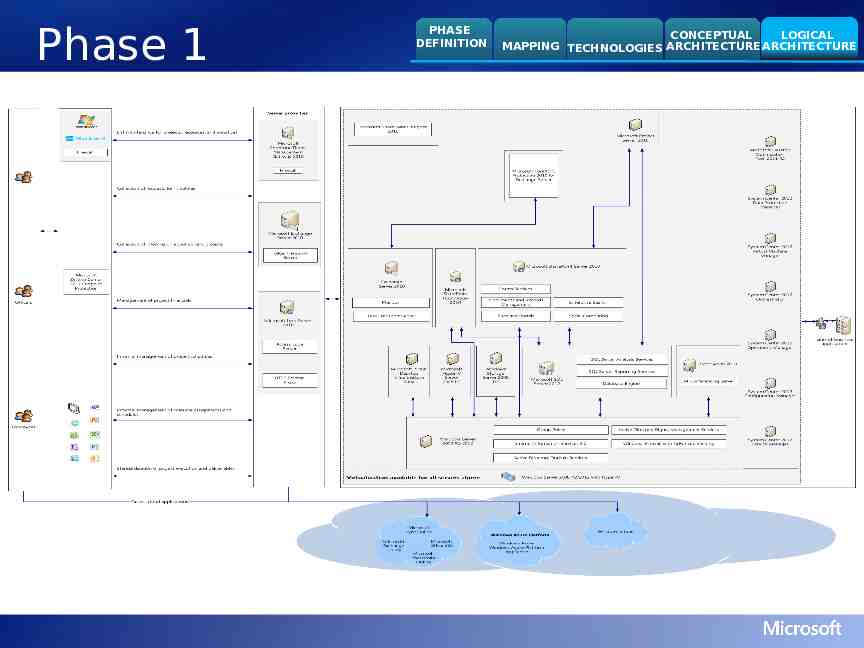
Phase 1 PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
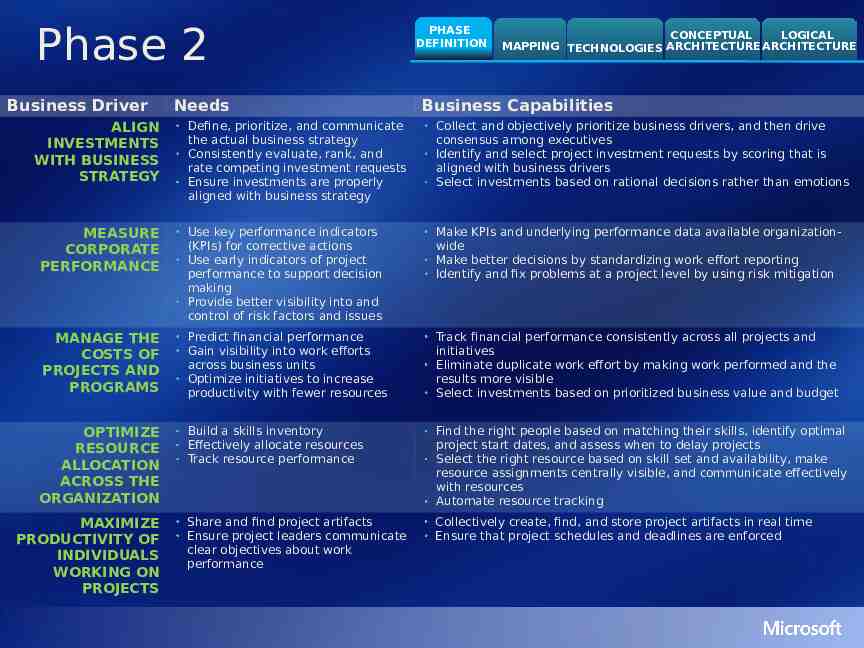
Phase 2 Business Driver Needs PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE Business Capabilities Define, prioritize, and communicate the actual business strategy Consistently evaluate, rank, and rate competing investment requests Ensure investments are properly aligned with business strategy Collect and objectively prioritize business drivers, and then drive consensus among executives Identify and select project investment requests by scoring that is aligned with business drivers Select investments based on rational decisions rather than emotions MEASURE CORPORATE PERFORMANCE Use key performance indicators (KPIs) for corrective actions Use early indicators of project performance to support decision making Provide better visibility into and control of risk factors and issues Make KPIs and underlying performance data available organizationwide Make better decisions by standardizing work effort reporting Identify and fix problems at a project level by using risk mitigation MANAGE THE COSTS OF PROJECTS AND PROGRAMS Predict financial performance Gain visibility into work efforts across business units Optimize initiatives to increase productivity with fewer resources Track financial performance consistently across all projects and initiatives Eliminate duplicate work effort by making work performed and the results more visible Select investments based on prioritized business value and budget OPTIMIZE RESOURCE ALLOCATION ACROSS THE ORGANIZATION Build a skills inventory Effectively allocate resources Track resource performance Find the right people based on matching their skills, identify optimal project start dates, and assess when to delay projects Select the right resource based on skill set and availability, make resource assignments centrally visible, and communicate effectively with resources Automate resource tracking Share and find project artifacts Ensure project leaders communicate clear objectives about work performance Collectively create, find, and store project artifacts in real time Ensure that project schedules and deadlines are enforced ALIGN INVESTMENTS WITH BUSINESS STRATEGY MAXIMIZE PRODUCTIVITY OF INDIVIDUALS WORKING ON PROJECTS
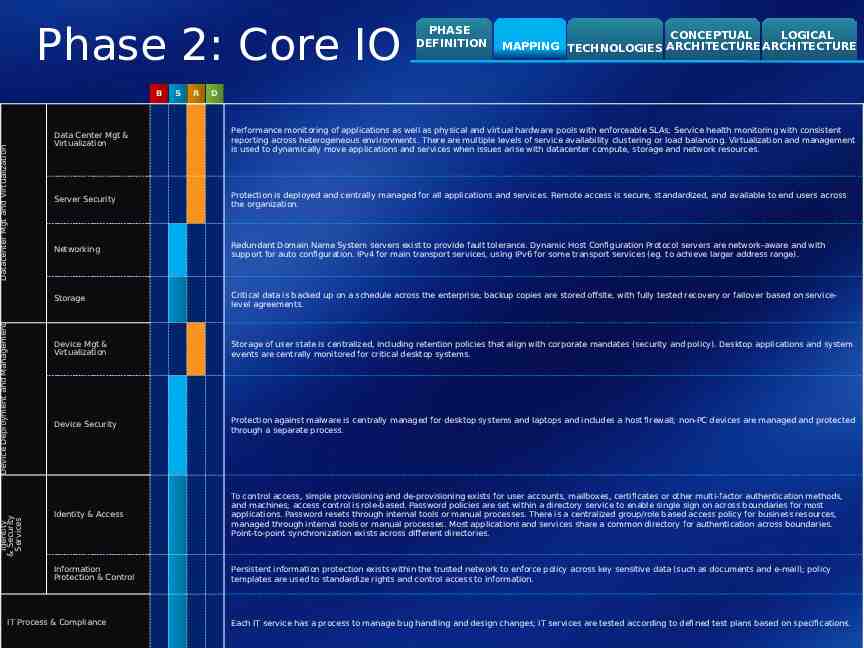
Phase 2: Core IO Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Data Center Mgt & Virtualization Performance monitoring of applications as well as physical and virtual hardware pools with enforceable SLAs; Service health monitoring with consistent reporting across heterogeneous environments. There are multiple levels of service availability clustering or load balancing. Virtualization and management is used to dynamically move applications and services when issues arise with datacenter compute, storage and network resources. Server Security Protection is deployed and centrally managed for all applications and services. Remote access is secure, standardized, and available to end users across the organization. Networking Redundant Domain Name System servers exist to provide fault tolerance. Dynamic Host Configuration Protocol servers are network-aware and with support for auto configuration. IPv4 for main transport services, using IPv6 for some transport services (eg. to achieve larger address range). Storage Critical data is backed up on a schedule across the enterprise; backup copies are stored offsite, with fully tested recovery or failover based on servicelevel agreements. Device Mgt & Virtualization Storage of user state is centralized, including retention policies that align with corporate mandates (security and policy). Desktop applications and system events are centrally monitored for critical desktop systems. Device Security Protection against malware is centrally managed for desktop systems and laptops and includes a host firewall; non-PC devices are managed and protected through a separate process. Identity & Access To control access, simple provisioning and de-provisioning exists for user accounts, mailboxes, certificates or other multi-factor authentication methods, and machines; access control is role-based. Password policies are set within a directory service to enable single sign on across boundaries for most applications. Password resets through internal tools or manual processes. There is a centralized group/role based access policy for business resources, managed through internal tools or manual processes. Most applications and services share a common directory for authentication across boundaries. Point-to-point synchronization exists across different directories. Information Protection & Control Persistent information protection exists within the trusted network to enforce policy across key sensitive data (such as documents and e-mail); policy templates are used to standardize rights and control access to information. IT Process & Compliance Each IT service has a process to manage bug handling and design changes; IT services are tested according to defined test plans based on specifications.
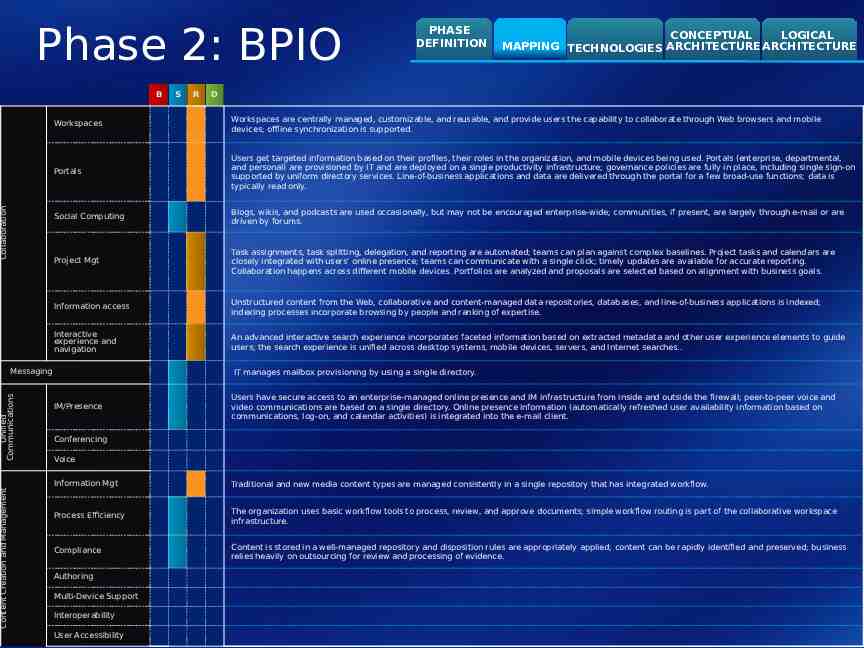
Phase 2: BPIO Collaboration B R CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Workspaces Workspaces are centrally managed, customizable, and reusable, and provide users the capability to collaborate through Web browsers and mobile devices; offline synchronization is supported. Portals Users get targeted information based on their profiles, their roles in the organization, and mobile devices being used. Portals (enterprise, departmental, and personal) are provisioned by IT and are deployed on a single productivity infrastructure; governance policies are fully in place, including single sign-on supported by uniform directory services. Line-of-business applications and data are delivered through the portal for a few broad-use functions; data is typically read only. Social Computing Blogs, wikis, and podcasts are used occasionally, but may not be encouraged enterprise-wide; communities, if present, are largely through e-mail or are driven by forums. Project Mgt Task assignments, task splitting, delegation, and reporting are automated; teams can plan against complex baselines. Project tasks and calendars are closely integrated with users’ online presence; teams can communicate with a single click; timely updates are available for accurate reporting. Collaboration happens across different mobile devices. Portfolios are analyzed and proposals are selected based on alignment with business goals. Information access Unstructured content from the Web, collaborative and content-managed data repositories, databases, and line-of-business applications is indexed; indexing processes incorporate browsing by people and ranking of expertise. Interactive experience and navigation An advanced interactive search experience incorporates faceted information based on extracted metadata and other user experience elements to guide users; the search experience is unified across desktop systems, mobile devices, servers, and Internet searches. Messaging Unified Communications Content Creation and Management S PHASE DEFINITION IT manages mailbox provisioning by using a single directory. IM/Presence Users have secure access to an enterprise-managed online presence and IM infrastructure from inside and outside the firewall; peer-to-peer voice and video communications are based on a single directory. Online presence information (automatically refreshed user availability information based on communications, log-on, and calendar activities) is integrated into the e-mail client. Conferencing Voice Information Mgt Traditional and new media content types are managed consistently in a single repository that has integrated workflow. Process Efficiency The organization uses basic workflow tools to process, review, and approve documents; simple workflow routing is part of the collaborative workspace infrastructure. Compliance Content is stored in a well-managed repository and disposition rules are appropriately applied; content can be rapidly identified and preserved; business relies heavily on outsourcing for review and processing of evidence. Authoring Multi-Device Support Interoperability User Accessibility
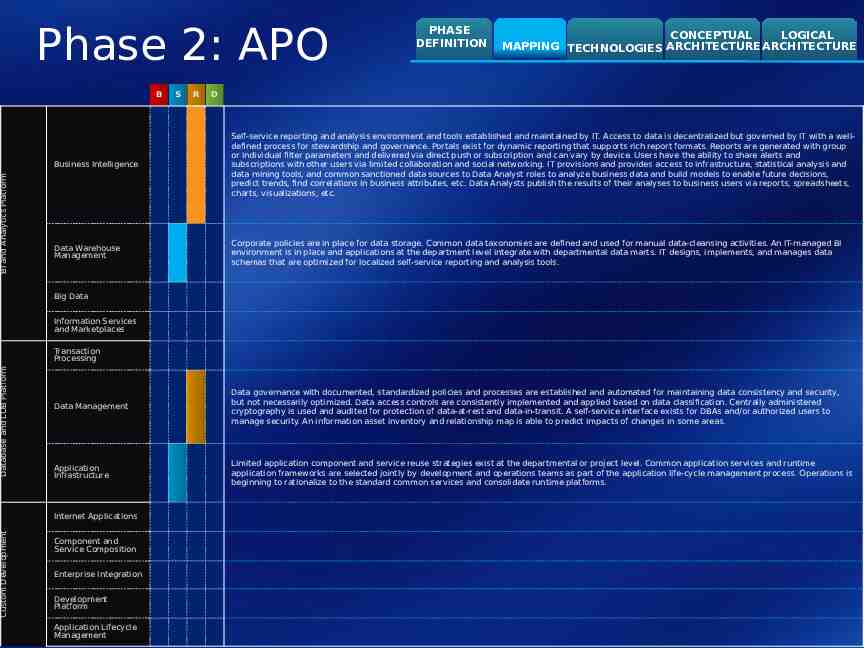
BI and Analytics Platform Database and LOB Platform Custom Development Phase 2: APO B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Business Intelligence Self-service reporting and analysis environment and tools established and maintained by IT. Access to data is decentralized but governed by IT with a welldefined process for stewardship and governance. Portals exist for dynamic reporting that supports rich report formats. Reports are generated with group or individual filter parameters and delivered via direct push or subscription and can vary by device. Users have the ability to share alerts and subscriptions with other users via limited collaboration and social networking. IT provisions and provides access to infrastructure, statistical analysis and data mining tools, and common sanctioned data sources to Data Analyst roles to analyze business data and build models to enable future decisions, predict trends, find correlations in business attributes, etc. Data Analysts publish the results of their analyses to business users via reports, spreadsheets, charts, visualizations, etc. Data Warehouse Management Corporate policies are in place for data storage. Common data taxonomies are defined and used for manual data-cleansing activities. An IT-managed BI environment is in place and applications at the department level integrate with departmental data marts. IT designs, implements, and manages data schemas that are optimized for localized self-service reporting and analysis tools. Big Data Information Services and Marketplaces Transaction Processing Data Management Data governance with documented, standardized policies and processes are established and automated for maintaining data consistency and security, but not necessarily optimized. Data access controls are consistently implemented and applied based on data classification. Centrally administered cryptography is used and audited for protection of data-at-rest and data-in-transit. A self-service interface exists for DBAs and/or authorized users to manage security. An information asset inventory and relationship map is able to predict impacts of changes in some areas. Application Infrastructure Limited application component and service reuse strategies exist at the departmental or project level. Common application services and runtime application frameworks are selected jointly by development and operations teams as part of the application life-cycle management process. Operations is beginning to rationalize to the standard common services and consolidate runtime platforms. Internet Applications Component and Service Composition Enterprise Integration Development Platform Application Lifecycle Management
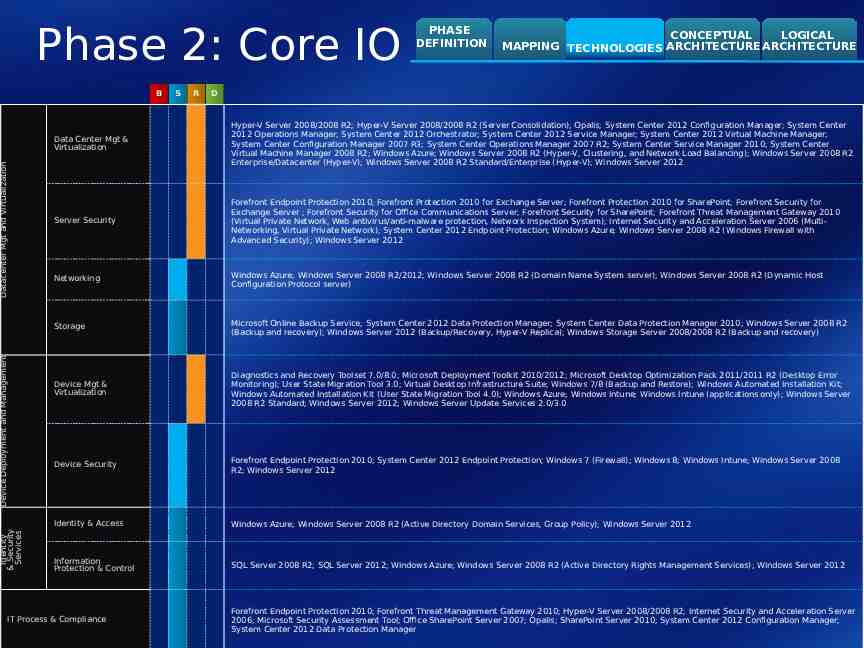
Phase 2: Core IO Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Data Center Mgt & Virtualization Hyper-V Server 2008/2008 R2; Hyper-V Server 2008/2008 R2 (Server Consolidation); Opalis; System Center 2012 Configuration Manager; System Center 2012 Operations Manager; System Center 2012 Orchestrator; System Center 2012 Service Manager; System Center 2012 Virtual Machine Manager; System Center Configuration Manager 2007 R3; System Center Operations Manager 2007 R2; System Center Service Manager 2010; System Center Virtual Machine Manager 2008 R2; Windows Azure; Windows Server 2008 R2 (Hyper-V, Clustering, and Network Load Balancing); Windows Server 2008 R2 Enterprise/Datacenter (Hyper-V); Windows Server 2008 R2 Standard/Enterprise (Hyper-V); Windows Server 2012 Server Security Forefront Endpoint Protection 2010; Forefront Protection 2010 for Exchange Server; Forefront Protection 2010 for SharePoint; Forefront Security for Exchange Server ; Forefront Security for Office Communications Server; Forefront Security for SharePoint; Forefront Threat Management Gateway 2010 (Virtual Private Network, Web antivirus/anti-malware protection, Network Inspection System); Internet Security and Acceleration Server 2006 (MultiNetworking, Virtual Private Network); System Center 2012 Endpoint Protection; Windows Azure; Windows Server 2008 R2 (Windows Firewall with Advanced Security); Windows Server 2012 Networking Windows Azure; Windows Server 2008 R2/2012; Windows Server 2008 R2 (Domain Name System server); Windows Server 2008 R2 (Dynamic Host Configuration Protocol server) Storage Microsoft Online Backup Service; System Center 2012 Data Protection Manager; System Center Data Protection Manager 2010; Windows Server 2008 R2 (Backup and recovery); Windows Server 2012 (Backup/Recovery, Hyper-V Replica); Windows Storage Server 2008/2008 R2 (Backup and recovery) Device Mgt & Virtualization Diagnostics and Recovery Toolset 7.0/8.0; Microsoft Deployment Toolkit 2010/2012; Microsoft Desktop Optimization Pack 2011/2011 R2 (Desktop Error Monitoring); User State Migration Tool 3.0; Virtual Desktop Infrastructure Suite; Windows 7/8 (Backup and Restore); Windows Automated Installation Kit; Windows Automated Installation Kit (User State Migration Tool 4.0); Windows Azure; Windows Intune; Windows Intune (applications only); Windows Server 2008 R2 Standard; Windows Server 2012; Windows Server Update Services 2.0/3.0 Device Security Forefront Endpoint Protection 2010; System Center 2012 Endpoint Protection; Windows 7 (Firewall); Windows 8; Windows Intune; Windows Server 2008 R2; Windows Server 2012 Identity & Access Windows Azure; Windows Server 2008 R2 (Active Directory Domain Services, Group Policy); Windows Server 2012 Information Protection & Control SQL Server 2008 R2; SQL Server 2012; Windows Azure; Windows Server 2008 R2 (Active Directory Rights Management Services); Windows Server 2012 IT Process & Compliance Forefront Endpoint Protection 2010; Forefront Threat Management Gateway 2010; Hyper-V Server 2008/2008 R2; Internet Security and Acceleration Server 2006; Microsoft Security Assessment Tool; Office SharePoint Server 2007; Opalis; SharePoint Server 2010; System Center 2012 Configuration Manager; System Center 2012 Data Protection Manager
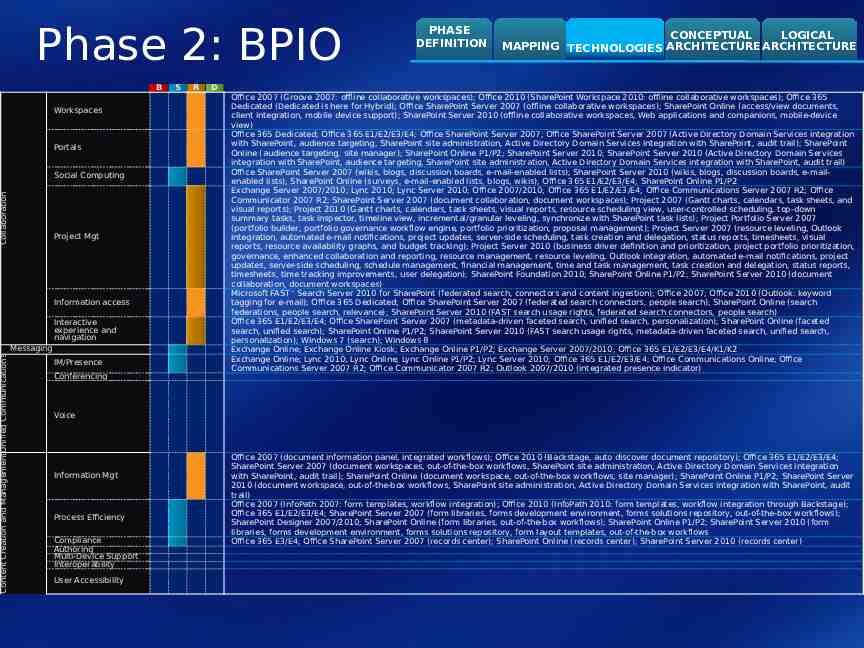
Phase 2: BPIO B Workspaces Portals Content Creation and ManagementUnified Communications Collaboration Social Computing Project Mgt Information access Interactive experience and navigation Messaging IM/Presence Conferencing S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Office 2007 (Groove 2007: offline collaborative workspaces); Office 2010 (SharePoint Workspace 2010: offline collaborative workspaces); Office 365 Dedicated (Dedicated is here for Hybrid); Office SharePoint Server 2007 (offline collaborative workspaces); SharePoint Online (access/view documents, client integration, mobile device support); SharePoint Server 2010 (offline collaborative workspaces, Web applications and companions, mobile-device view) Office 365 Dedicated; Office 365 E1/E2/E3/E4; Office SharePoint Server 2007; Office SharePoint Server 2007 (Active Directory Domain Services integration with SharePoint, audience targeting, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail); SharePoint Online (audience targeting, site manager); SharePoint Online P1/P2; SharePoint Server 2010; SharePoint Server 2010 (Active Directory Domain Services integration with SharePoint, audience targeting, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail) Office SharePoint Server 2007 (wikis, blogs, discussion boards, e-mail-enabled lists); SharePoint Server 2010 (wikis, blogs, discussion boards, e-mailenabled lists); SharePoint Online (surveys, e-mail-enabled lists, blogs, wikis); Office 365 E1/E2/E3/E4; SharePoint Online P1/P2 Exchange Server 2007/2010; Lync 2010; Lync Server 2010; Office 2007/2010; Office 365 E1/E2/E3/E4; Office Communications Server 2007 R2; Office Communicator 2007 R2; SharePoint Server 2007 (document collaboration, document workspaces); Project 2007 (Gantt charts, calendars, task sheets, and visual reports); Project 2010 (Gantt charts, calendars, task sheets, visual reports, resource scheduling view, user-controlled scheduling, top-down summary tasks, task inspector, timeline view, incremental/granular leveling, synchronize with SharePoint task lists); Project Portfolio Server 2007 (portfolio builder, portfolio governance workflow engine, portfolio prioritization, proposal management); Project Server 2007 (resource leveling, Outlook integration, automated e-mail notifications, project updates, server-side scheduling, task creation and delegation, status reports, timesheets, visual reports, resource availability graphs, and budget tracking); Project Server 2010 (business driver definition and prioritization, project portfolio prioritization, governance, enhanced collaboration and reporting, resource management, resource leveling, Outlook integration, automated e-mail notifications, project updates, server-side scheduling, schedule management, financial management, time and task management, task creation and delegation, status reports, timesheets, time tracking improvements, user delegation); SharePoint Foundation 2010; SharePoint Online P1/P2; SharePoint Server 2010 (document collaboration, document workspaces) Microsoft FAST Search Server 2010 for SharePoint (federated search, connectors and content ingestion); Office 2007; Office 2010 (Outlook: keyword tagging for e-mail); Office 365 Dedicated; Office SharePoint Server 2007 (federated search connectors, people search); SharePoint Online (search federations, people search, relevance); SharePoint Server 2010 (FAST search usage rights, federated search connectors, people search) Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (metadata-driven faceted search, unified search, personalization); SharePoint Online (faceted search, unified search); SharePoint Online P1/P2; SharePoint Server 2010 (FAST search usage rights, metadata-driven faceted search, unified search, personalization); Windows 7 (search); Windows 8 Exchange Online; Exchange Online Kiosk; Exchange Online P1/P2; Exchange Server 2007/2010; Office 365 E1/E2/E3/E4/K1/K2 Exchange Online; Lync 2010; Lync Online; Lync Online P1/P2; Lync Server 2010; Office 365 E1/E2/E3/E4; Office Communications Online; Office Communications Server 2007 R2; Office Communicator 2007 R2; Outlook 2007/2010 (integrated presence indicator) Voice Information Mgt Process Efficiency Compliance Authoring Multi-Device Support Interoperability User Accessibility Office 2007 (document information panel, integrated workflows); Office 2010 (Backstage, auto discover document repository); Office 365 E1/E2/E3/E4; SharePoint Server 2007 (document workspaces, out-of-the-box workflows, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail); SharePoint Online (document workspace, out-of-the-box workflows, site manager); SharePoint Online P1/P2; SharePoint Server 2010 (document workspace, out-of-the-box workflows, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail) Office 2007 (InfoPath 2007: form templates, workflow integration); Office 2010 (InfoPath 2010: form templates, workflow integration through Backstage); Office 365 E1/E2/E3/E4; SharePoint Server 2007 (form libraries, forms development environment, forms solutions repository, out-of-the-box workflows); SharePoint Designer 2007/2010; SharePoint Online (form libraries, out-of-the-box workflows); SharePoint Online P1/P2; SharePoint Server 2010 (form libraries, forms development environment, forms solutions repository, form layout templates, out-of-the-box workflows Office 365 E3/E4; Office SharePoint Server 2007 (records center); SharePoint Online (records center); SharePoint Server 2010 (records center)
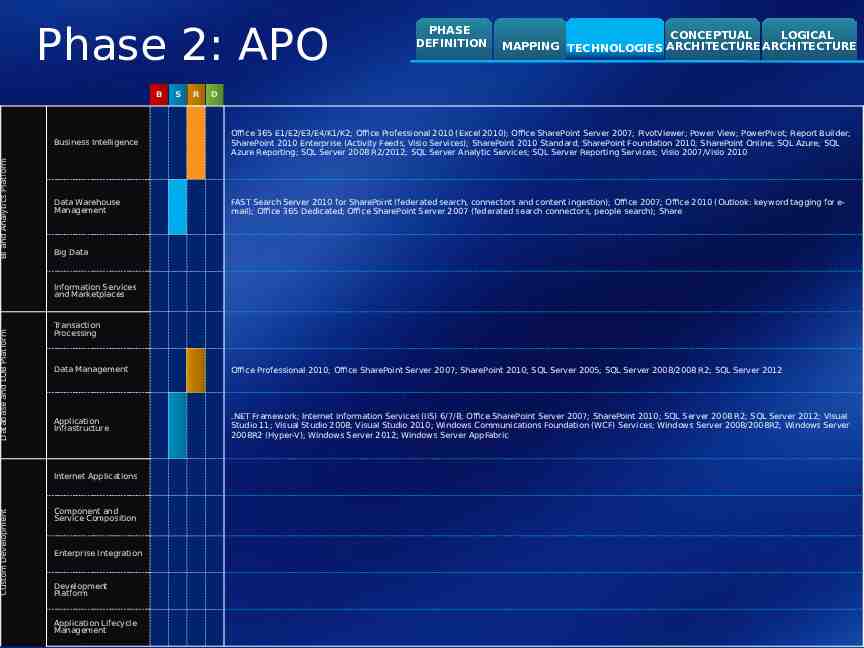
BI and Analytics Platform Database and LOB Platform Custom Development Phase 2: APO B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Business Intelligence Office 365 E1/E2/E3/E4/K1/K2; Office Professional 2010 (Excel 2010); Office SharePoint Server 2007; PivotViewer; Power View; PowerPivot; Report Builder; SharePoint 2010 Enterprise (Activity Feeds, Visio Services); SharePoint 2010 Standard; SharePoint Foundation 2010; SharePoint Online; SQL Azure; SQL Azure Reporting; SQL Server 2008 R2/2012; SQL Server Analytic Services; SQL Server Reporting Services; Visio 2007/Visio 2010 Data Warehouse Management FAST Search Server 2010 for SharePoint (federated search, connectors and content ingestion); Office 2007; Office 2010 (Outlook: keyword tagging for email); Office 365 Dedicated; Office SharePoint Server 2007 (federated search connectors, people search); Share Big Data Information Services and Marketplaces Transaction Processing Data Management Office Professional 2010; Office SharePoint Server 2007; SharePoint 2010; SQL Server 2005; SQL Server 2008/2008 R2; SQL Server 2012 Application Infrastructure .NET Framework; Internet Information Services (IIS) 6/7/8; Office SharePoint Server 2007; SharePoint 2010; SQL Server 2008 R2; SQL Server 2012; Visual Studio 11; Visual Studio 2008; Visual Studio 2010; Windows Communications Foundation (WCF) Services; Windows Server 2008/2008R2; Windows Server 2008R2 (Hyper-V); Windows Server 2012; Windows Server AppFabric Internet Applications Component and Service Composition Enterprise Integration Development Platform Application Lifecycle Management
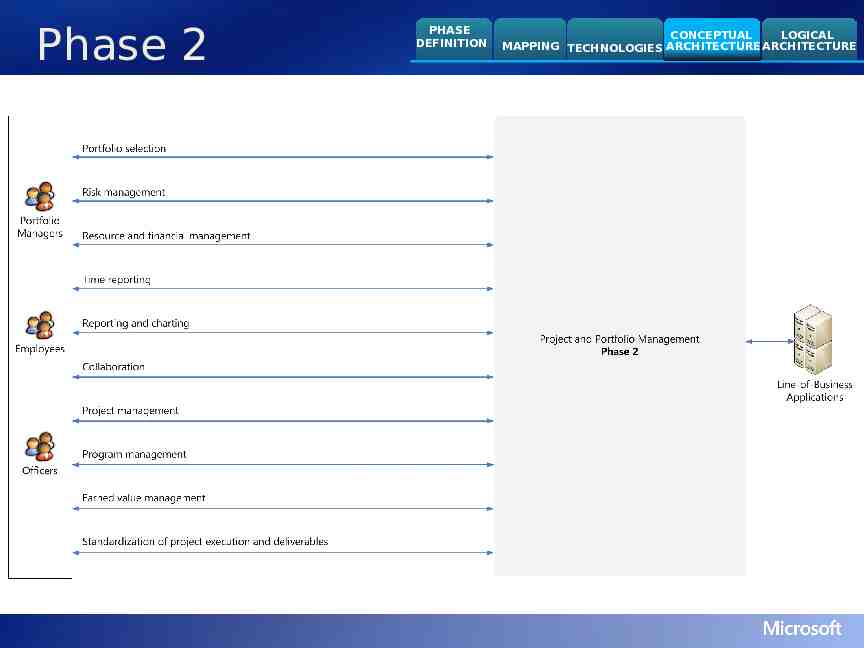
Phase 2 PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE
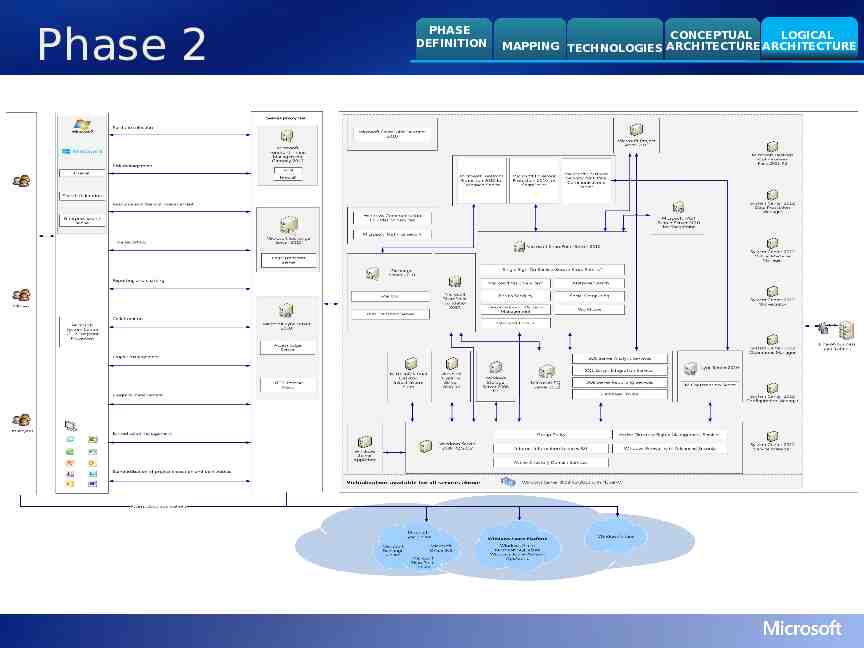
Phase 2 PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
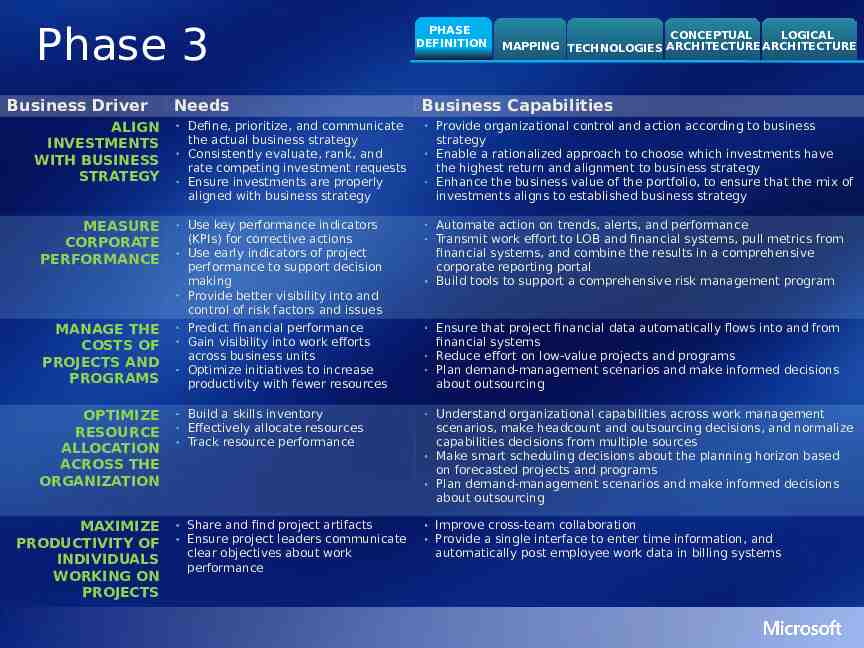
Phase 3 Business Driver Needs PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE Business Capabilities Define, prioritize, and communicate the actual business strategy Consistently evaluate, rank, and rate competing investment requests Ensure investments are properly aligned with business strategy Provide organizational control and action according to business strategy Enable a rationalized approach to choose which investments have the highest return and alignment to business strategy Enhance the business value of the portfolio, to ensure that the mix of investments aligns to established business strategy MEASURE CORPORATE PERFORMANCE Use key performance indicators (KPIs) for corrective actions Use early indicators of project performance to support decision making Provide better visibility into and control of risk factors and issues Automate action on trends, alerts, and performance Transmit work effort to LOB and financial systems, pull metrics from financial systems, and combine the results in a comprehensive corporate reporting portal Build tools to support a comprehensive risk management program MANAGE THE COSTS OF PROJECTS AND PROGRAMS Predict financial performance Gain visibility into work efforts across business units Optimize initiatives to increase productivity with fewer resources Ensure that project financial data automatically flows into and from financial systems Reduce effort on low-value projects and programs Plan demand-management scenarios and make informed decisions about outsourcing OPTIMIZE RESOURCE ALLOCATION ACROSS THE ORGANIZATION Build a skills inventory Effectively allocate resources Track resource performance Understand organizational capabilities across work management scenarios, make headcount and outsourcing decisions, and normalize capabilities decisions from multiple sources Make smart scheduling decisions about the planning horizon based on forecasted projects and programs Plan demand-management scenarios and make informed decisions about outsourcing Share and find project artifacts Ensure project leaders communicate clear objectives about work performance Improve cross-team collaboration Provide a single interface to enter time information, and automatically post employee work data in billing systems ALIGN INVESTMENTS WITH BUSINESS STRATEGY MAXIMIZE PRODUCTIVITY OF INDIVIDUALS WORKING ON PROJECTS
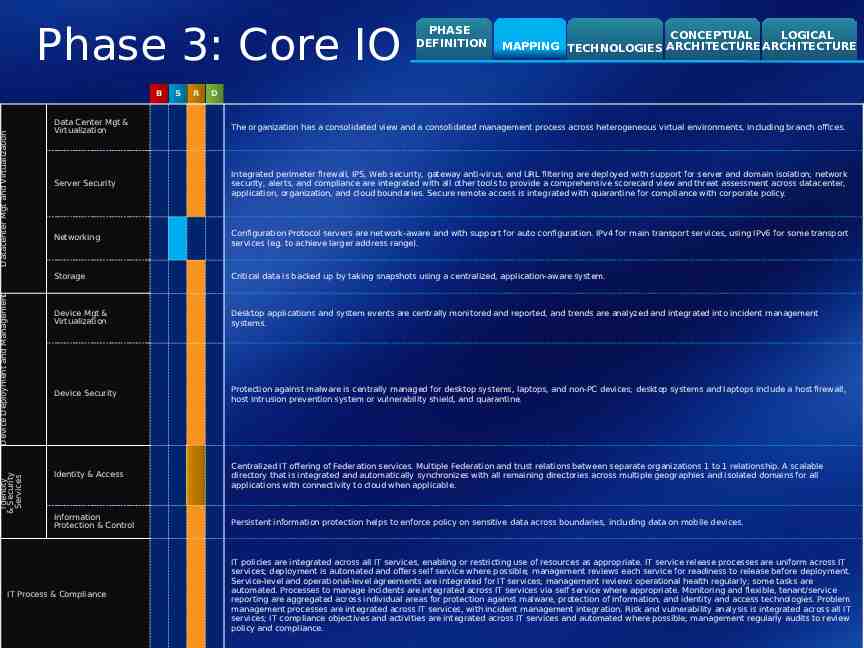
Phase 3: Core IO Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Data Center Mgt & Virtualization The organization has a consolidated view and a consolidated management process across heterogeneous virtual environments, including branch offices. Server Security Integrated perimeter firewall, IPS, Web security, gateway anti-virus, and URL filtering are deployed with support for server and domain isolation; network security, alerts, and compliance are integrated with all other tools to provide a comprehensive scorecard view and threat assessment across datacenter, application, organization, and cloud boundaries. Secure remote access is integrated with quarantine for compliance with corporate policy. Networking Configuration Protocol servers are network-aware and with support for auto configuration. IPv4 for main transport services, using IPv6 for some transport services (eg. to achieve larger address range). Storage Critical data is backed up by taking snapshots using a centralized, application-aware system. Device Mgt & Virtualization Desktop applications and system events are centrally monitored and reported, and trends are analyzed and integrated into incident management systems. Device Security Protection against malware is centrally managed for desktop systems, laptops, and non-PC devices; desktop systems and laptops include a host firewall, host intrusion prevention system or vulnerability shield, and quarantine. Identity & Access Centralized IT offering of Federation services. Multiple Federation and trust relations between separate organizations 1 to 1 relationship. A scalable directory that is integrated and automatically synchronizes with all remaining directories across multiple geographies and isolated domains for all applications with connectivity to cloud when applicable. Information Protection & Control Persistent information protection helps to enforce policy on sensitive data across boundaries, including data on mobile devices. IT Process & Compliance IT policies are integrated across all IT services, enabling or restricting use of resources as appropriate. IT service release processes are uniform across IT services; deployment is automated and offers self service where possible; management reviews each service for readiness to release before deployment. Service-level and operational-level agreements are integrated for IT services; management reviews operational health regularly; some tasks are automated. Processes to manage incidents are integrated across IT services via self service where appropriate. Monitoring and flexible, tenant/service reporting are aggregated across individual areas for protection against malware, protection of information, and identity and access technologies. Problem management processes are integrated across IT services, with incident management integration. Risk and vulnerability analysis is integrated across all IT services; IT compliance objectives and activities are integrated across IT services and automated where possible; management regularly audits to review policy and compliance.
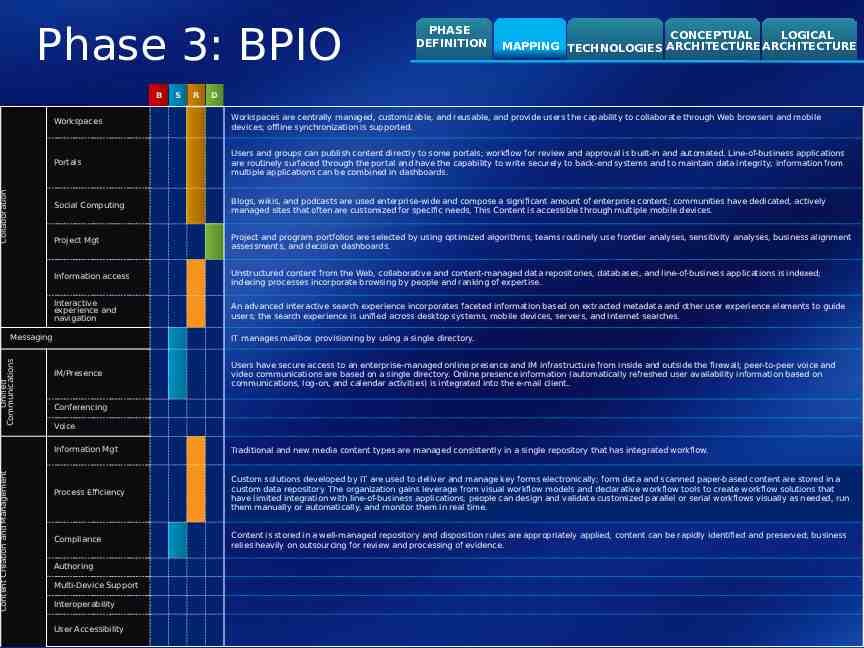
Phase 3: BPIO Collaboration B R CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Workspaces Workspaces are centrally managed, customizable, and reusable, and provide users the capability to collaborate through Web browsers and mobile devices; offline synchronization is supported. Portals Users and groups can publish content directly to some portals; workflow for review and approval is built-in and automated. Line-of-business applications are routinely surfaced through the portal and have the capability to write securely to back-end systems and to maintain data integrity; information from multiple applications can be combined in dashboards. Social Computing Blogs, wikis, and podcasts are used enterprise-wide and compose a significant amount of enterprise content; communities have dedicated, actively managed sites that often are customized for specific needs, This Content is accessible through multiple mobile devices. Project Mgt Project and program portfolios are selected by using optimized algorithms; teams routinely use frontier analyses, sensitivity analyses, business alignment assessments, and decision dashboards. Information access Unstructured content from the Web, collaborative and content-managed data repositories, databases, and line-of-business applications is indexed; indexing processes incorporate browsing by people and ranking of expertise. Interactive experience and navigation An advanced interactive search experience incorporates faceted information based on extracted metadata and other user experience elements to guide users; the search experience is unified across desktop systems, mobile devices, servers, and Internet searches. Messaging Unified Communications Content Creation and Management S PHASE DEFINITION IT manages mailbox provisioning by using a single directory. IM/Presence Users have secure access to an enterprise-managed online presence and IM infrastructure from inside and outside the firewall; peer-to-peer voice and video communications are based on a single directory. Online presence information (automatically refreshed user availability information based on communications, log-on, and calendar activities) is integrated into the e-mail client. Conferencing Voice Information Mgt Traditional and new media content types are managed consistently in a single repository that has integrated workflow. Process Efficiency Custom solutions developed by IT are used to deliver and manage key forms electronically; form data and scanned paper-based content are stored in a custom data repository. The organization gains leverage from visual workflow models and declarative workflow tools to create workflow solutions that have limited integration with line-of-business applications; people can design and validate customized parallel or serial workflows visually as needed, run them manually or automatically, and monitor them in real time. Compliance Content is stored in a well-managed repository and disposition rules are appropriately applied; content can be rapidly identified and preserved; business relies heavily on outsourcing for review and processing of evidence. Authoring Multi-Device Support Interoperability User Accessibility

BI and Analytics Platform Database and LOB Platform Custom Development Phase 3: APO B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Business Intelligence From the BI portal, users are able to connect to internal and external data sources and combine them in a single report or data set for further analysis. Users can do sophisticated analysis and build rich BI applications using Excel or other analysis tools. BI portal has reporting and analysis capabilities that include exception highlighting, guided analysis, and predictive analysis with rich logic. Dashboards are consistently used to provide operational and strategic views of the business from real time or periodically refreshed data. BI portal experience has rich visualizations, dashboards and scorecards with full data interactivity (slicing, filtering, etc.) consistent with self service reporting and analysis tools. Users have the ability to create unique personal and/or shared views of data that are actually combinations of multiple views (i.e. mashups). Data Analysts use powerful data management workbench with integrated access to tools for data preparation, cleansing, multi-variate analysis, and a sophisticated set of data mining algorithms with extensibility and tuning options. Data Analysts can easily publish their findings and data sets for access by business users. Data Warehouse Management EDW is refreshed on a near real-time basis so that information is readily available to mission-critical applications, analytics, and reporting systems. A high degree of concurrency exists, with many users running complex queries and interacting with complex analytics tools simultaneously with data loading. Management and maintenance of storage, hardware, and supporting software is manual and ad hoc. An IT-managed BI environment and applications at the department level are aligned with the enterprise data warehouse (EDW) environment and applications. IT proactively builds, maintains, and manages key reports and analysis models that are used regularly across the business. IT designs, implements, and manages semantic models (such as OLAP) and data schemas optimized for managed and self-service reporting and analysis. Big Data Information Services and Marketplaces Transaction Processing Data Management Metadata and taxonomies are defined, implemented, and formally managed in one or more repositories with more reliance upon policy-based management to ensure proper configuration and adherence to policies. Business has begun to consolidate data, management plans, and policies for consistency across information stores. Application Infrastructure Application messaging services used by development are aligned with standard application operating environments. Development and operations teams have the skills required to effectively and consistently make use of these technologies. A range of application services and infrastructure is provided across operating environments with central governance. A central engineering practices group co-sponsored by development and operations has formed and is providing valuable guidance to application development teams. Application developers consistently build applications using these application frameworks, so hosting, application services requirements, and management are predictable. Operating systems provide support for multiple application frameworks. Internet Applications Component and Service Composition Some use of reusable assets is supported by high-value services, components, and modules. Composition by IT departments requires advanced coding skills. Use of composition frameworks and tools happens on a project-by-project basis. SOA and portal components are not coordinated. Central IT provides managed and secure data services to some of the most commonly needed enterprise entities and provides business units with standard services to some key enterprise systems and for some standard needs like reporting and dashboards. LOB applications expose pre-built web parts that integrate with the company portal and are easily used by users. Developers are beginning to create components and services for the designated portal platform, though the efforts are exploratory in nature or focused on individual projects. Enterprise Integration Use of standardized processes for data integration is at the project level and technologies are used to improve back-end integration. The business leverages an integration broker running on-premises to connect to cloud applications using adapters. Development Platform The organization has selected and implemented a common set of frameworks for major application development and operating environment needs. Developer skill and use of standard frameworks is consistent. A central architecture and engineering practices group has formed with the participation of development and operations teams, and provides valuable guidance to development teams. A standard set of tools and common development approaches are used across multiple development teams in the organization. Application customization is performed through customization support offered by the application, on an isolated project basis with no standard approaches or consideration for future maintenance or integration. Application Lifecycle Management Work-breakdown structures map estimated work to business value. Rudimentary metrics are used to manage project progress. Project managers aggregate data from standard status updates. Effective change management processes are in place. Processes are defined for debugging production defects and incidents, with a standard set of defect artifacts.
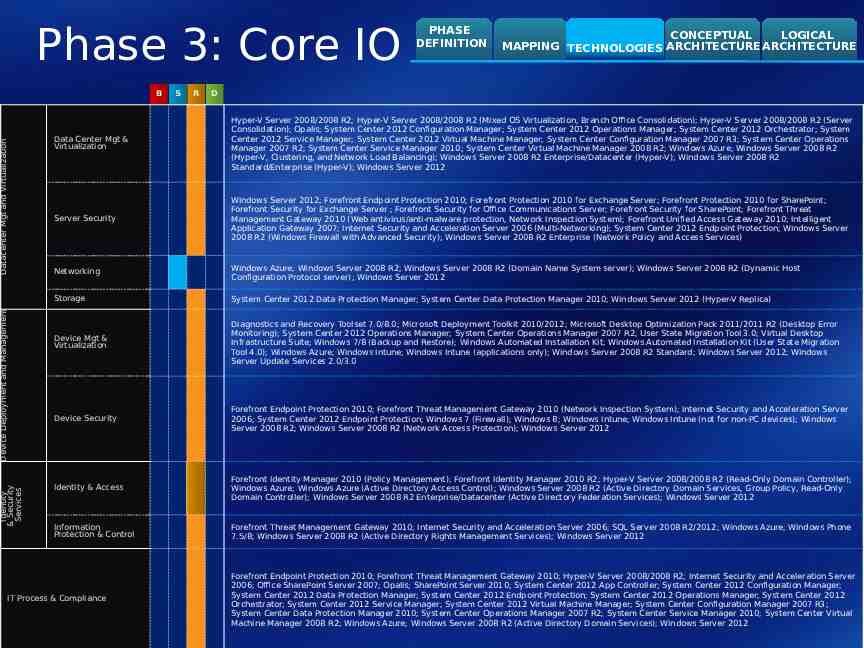
Phase 3: Core IO Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Data Center Mgt & Virtualization Hyper-V Server 2008/2008 R2; Hyper-V Server 2008/2008 R2 (Mixed OS Virtualization, Branch Office Consolidation); Hyper-V Server 2008/2008 R2 (Server Consolidation); Opalis; System Center 2012 Configuration Manager; System Center 2012 Operations Manager; System Center 2012 Orchestrator; System Center 2012 Service Manager; System Center 2012 Virtual Machine Manager; System Center Configuration Manager 2007 R3; System Center Operations Manager 2007 R2; System Center Service Manager 2010; System Center Virtual Machine Manager 2008 R2; Windows Azure; Windows Server 2008 R2 (Hyper-V, Clustering, and Network Load Balancing); Windows Server 2008 R2 Enterprise/Datacenter (Hyper-V); Windows Server 2008 R2 Standard/Enterprise (Hyper-V); Windows Server 2012 Server Security Windows Server 2012; Forefront Endpoint Protection 2010; Forefront Protection 2010 for Exchange Server; Forefront Protection 2010 for SharePoint; Forefront Security for Exchange Server ; Forefront Security for Office Communications Server; Forefront Security for SharePoint; Forefront Threat Management Gateway 2010 (Web antivirus/anti-malware protection, Network Inspection System); Forefront Unified Access Gateway 2010; Intelligent Application Gateway 2007; Internet Security and Acceleration Server 2006 (Multi-Networking); System Center 2012 Endpoint Protection; Windows Server 2008 R2 (Windows Firewall with Advanced Security); Windows Server 2008 R2 Enterprise (Network Policy and Access Services) Networking Windows Azure; Windows Server 2008 R2; Windows Server 2008 R2 (Domain Name System server); Windows Server 2008 R2 (Dynamic Host Configuration Protocol server); Windows Server 2012 Storage System Center 2012 Data Protection Manager; System Center Data Protection Manager 2010; Windows Server 2012 (Hyper-V Replica) Device Mgt & Virtualization Diagnostics and Recovery Toolset 7.0/8.0; Microsoft Deployment Toolkit 2010/2012; Microsoft Desktop Optimization Pack 2011/2011 R2 (Desktop Error Monitoring); System Center 2012 Operations Manager; System Center Operations Manager 2007 R2; User State Migration Tool 3.0; Virtual Desktop Infrastructure Suite; Windows 7/8 (Backup and Restore); Windows Automated Installation Kit; Windows Automated Installation Kit (User State Migration Tool 4.0); Windows Azure; Windows Intune; Windows Intune (applications only); Windows Server 2008 R2 Standard; Windows Server 2012; Windows Server Update Services 2.0/3.0 Device Security Forefront Endpoint Protection 2010; Forefront Threat Management Gateway 2010 (Network Inspection System); Internet Security and Acceleration Server 2006; System Center 2012 Endpoint Protection; Windows 7 (Firewall); Windows 8; Windows Intune; Windows Intune (not for non-PC devices); Windows Server 2008 R2; Windows Server 2008 R2 (Network Access Protection); Windows Server 2012 Identity & Access Forefront Identity Manager 2010 (Policy Management); Forefront Identity Manager 2010 R2; Hyper-V Server 2008/2008 R2 (Read-Only Domain Controller); Windows Azure; Windows Azure (Active Directory Access Control); Windows Server 2008 R2 (Active Directory Domain Services, Group Policy, Read-Only Domain Controller); Windows Server 2008 R2 Enterprise/Datacenter (Active Directory Federation Services); Windows Server 2012 Information Protection & Control Forefront Threat Management Gateway 2010; Internet Security and Acceleration Server 2006; SQL Server 2008 R2/2012; Windows Azure; Windows Phone 7.5/8; Windows Server 2008 R2 (Active Directory Rights Management Services); Windows Server 2012 IT Process & Compliance Forefront Endpoint Protection 2010; Forefront Threat Management Gateway 2010; Hyper-V Server 2008/2008 R2; Internet Security and Acceleration Server 2006; Office SharePoint Server 2007; Opalis; SharePoint Server 2010; System Center 2012 App Controller; System Center 2012 Configuration Manager; System Center 2012 Data Protection Manager; System Center 2012 Endpoint Protection; System Center 2012 Operations Manager; System Center 2012 Orchestrator; System Center 2012 Service Manager; System Center 2012 Virtual Machine Manager; System Center Configuration Manager 2007 R3; System Center Data Protection Manager 2010; System Center Operations Manager 2007 R2; System Center Service Manager 2010; System Center Virtual Machine Manager 2008 R2; Windows Azure; Windows Server 2008 R2 (Active Directory Domain Services); Windows Server 2012
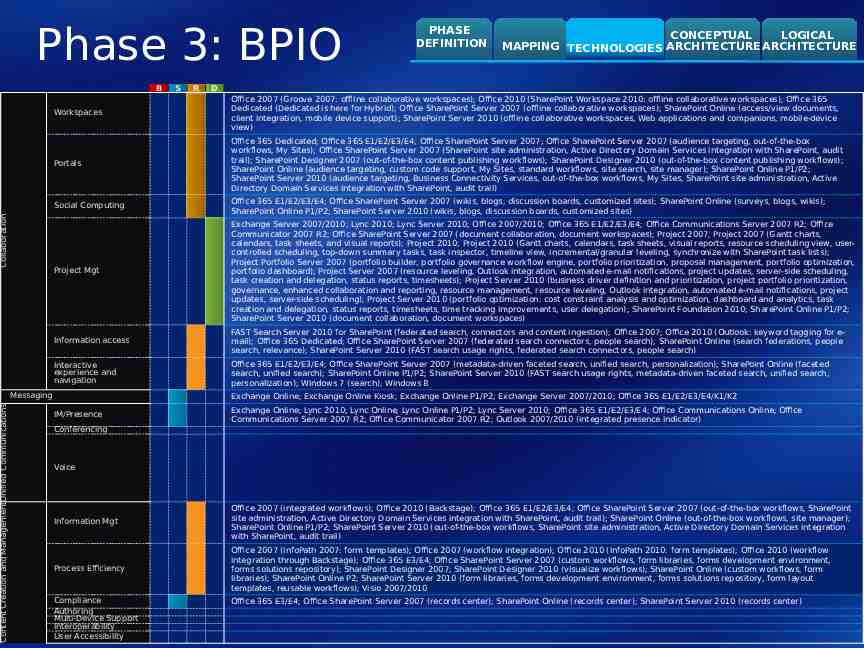
Phase 3: BPIO Content Creation and ManagementUnified Communications Collaboration B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Workspaces Office 2007 (Groove 2007: offline collaborative workspaces); Office 2010 (SharePoint Workspace 2010: offline collaborative workspaces); Office 365 Dedicated (Dedicated is here for Hybrid); Office SharePoint Server 2007 (offline collaborative workspaces); SharePoint Online (access/view documents, client integration, mobile device support); SharePoint Server 2010 (offline collaborative workspaces, Web applications and companions, mobile-device view) Portals Office 365 Dedicated; Office 365 E1/E2/E3/E4; Office SharePoint Server 2007; Office SharePoint Server 2007 (audience targeting, out-of-the-box workflows, My Sites); Office SharePoint Server 2007 (SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail); SharePoint Designer 2007 (out-of-the-box content publishing workflows); SharePoint Designer 2010 (out-of-the-box content publishing workflows); SharePoint Online (audience targeting, custom code support, My Sites, standard workflows, site search, site manager); SharePoint Online P1/P2; SharePoint Server 2010 (audience targeting, Business Connectivity Services, out-of-the-box workflows, My Sites, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail) Social Computing Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (wikis, blogs, discussion boards, customized sites); SharePoint Online (surveys, blogs, wikis); SharePoint Online P1/P2; SharePoint Server 2010 (wikis, blogs, discussion boards, customized sites) Project Mgt Exchange Server 2007/2010; Lync 2010; Lync Server 2010; Office 2007/2010; Office 365 E1/E2/E3/E4; Office Communications Server 2007 R2; Office Communicator 2007 R2; Office SharePoint Server 2007 (document collaboration, document workspaces); Project 2007; Project 2007 (Gantt charts, calendars, task sheets, and visual reports); Project 2010; Project 2010 (Gantt charts, calendars, task sheets, visual reports, resource scheduling view, usercontrolled scheduling, top-down summary tasks, task inspector, timeline view, incremental/granular leveling, synchronize with SharePoint task lists); Project Portfolio Server 2007 (portfolio builder, portfolio governance workflow engine, portfolio prioritization, proposal management, portfolio optimization, portfolio dashboard); Project Server 2007 (resource leveling, Outlook integration, automated e-mail notifications, project updates, server-side scheduling, task creation and delegation, status reports, timesheets); Project Server 2010 (business driver definition and prioritization, project portfolio prioritization, governance, enhanced collaboration and reporting, resource management, resource leveling, Outlook integration, automated e-mail notifications, project updates, server-side scheduling); Project Server 2010 (portfolio optimization: cost constraint analysis and optimization, dashboard and analytics, task creation and delegation, status reports, timesheets, time tracking improvements, user delegation); SharePoint Foundation 2010; SharePoint Online P1/P2; SharePoint Server 2010 (document collaboration, document workspaces) Information access FAST Search Server 2010 for SharePoint (federated search, connectors and content ingestion); Office 2007; Office 2010 (Outlook: keyword tagging for email); Office 365 Dedicated; Office SharePoint Server 2007 (federated search connectors, people search); SharePoint Online (search federations, people search, relevance); SharePoint Server 2010 (FAST search usage rights, federated search connectors, people search) Interactive experience and navigation Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (metadata-driven faceted search, unified search, personalization); SharePoint Online (faceted search, unified search); SharePoint Online P1/P2; SharePoint Server 2010 (FAST search usage rights, metadata-driven faceted search, unified search, personalization); Windows 7 (search); Windows 8 Messaging Exchange Online; Exchange Online Kiosk; Exchange Online P1/P2; Exchange Server 2007/2010; Office 365 E1/E2/E3/E4/K1/K2 IM/Presence Exchange Online; Lync 2010; Lync Online; Lync Online P1/P2; Lync Server 2010; Office 365 E1/E2/E3/E4; Office Communications Online; Office Communications Server 2007 R2; Office Communicator 2007 R2; Outlook 2007/2010 (integrated presence indicator) Conferencing Voice Information Mgt Office 2007 (integrated workflows); Office 2010 (Backstage); Office 365 E1/E2/E3/E4; Office SharePoint Server 2007 (out-of-the-box workflows, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail); SharePoint Online (out-of-the-box workflows, site manager); SharePoint Online P1/P2; SharePoint Server 2010 (out-of-the-box workflows, SharePoint site administration, Active Directory Domain Services integration with SharePoint, audit trail) Process Efficiency Office 2007 (InfoPath 2007: form templates); Office 2007 (workflow integration); Office 2010 (InfoPath 2010: form templates); Office 2010 (workflow integration through Backstage); Office 365 E3/E4; Office SharePoint Server 2007 (custom workflows, form libraries, forms development environment, forms solutions repository); SharePoint Designer 2007; SharePoint Designer 2010 (visualize workflows); SharePoint Online (custom workflows, form libraries); SharePoint Online P2; SharePoint Server 2010 (form libraries, forms development environment, forms solutions repository, form layout templates, reusable workflows); Visio 2007/2010 Compliance Authoring Multi-Device Support Interoperability User Accessibility Office 365 E3/E4; Office SharePoint Server 2007 (records center); SharePoint Online (records center); SharePoint Server 2010 (records center)
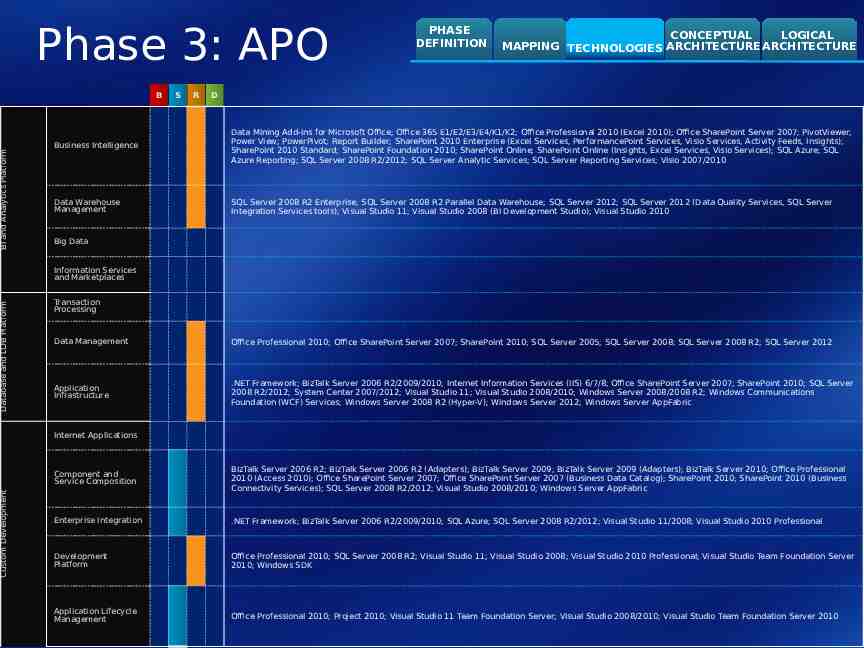
BI and Analytics Platform Database and LOB Platform Custom Development Phase 3: APO B S R PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE D Business Intelligence Data Mining Add-ins for Microsoft Office; Office 365 E1/E2/E3/E4/K1/K2; Office Professional 2010 (Excel 2010); Office SharePoint Server 2007; PivotViewer; Power View; PowerPivot; Report Builder; SharePoint 2010 Enterprise (Excel Services, PerformancePoint Services, Visio Services, Activity Feeds, Insights); SharePoint 2010 Standard; SharePoint Foundation 2010; SharePoint Online; SharePoint Online (Insights, Excel Services, Visio Services); SQL Azure; SQL Azure Reporting; SQL Server 2008 R2/2012; SQL Server Analytic Services; SQL Server Reporting Services; Visio 2007/2010 Data Warehouse Management SQL Server 2008 R2 Enterprise; SQL Server 2008 R2 Parallel Data Warehouse; SQL Server 2012; SQL Server 2012 (Data Quality Services, SQL Server Integration Services tools); Visual Studio 11; Visual Studio 2008 (BI Development Studio); Visual Studio 2010 Big Data Information Services and Marketplaces Transaction Processing Data Management Office Professional 2010; Office SharePoint Server 2007; SharePoint 2010; SQL Server 2005; SQL Server 2008; SQL Server 2008 R2; SQL Server 2012 Application Infrastructure .NET Framework; BizTalk Server 2006 R2/2009/2010; Internet Information Services (IIS) 6/7/8; Office SharePoint Server 2007; SharePoint 2010; SQL Server 2008 R2/2012; System Center 2007/2012; Visual Studio 11; Visual Studio 2008/2010; Windows Server 2008/2008 R2; Windows Communications Foundation (WCF) Services; Windows Server 2008 R2 (Hyper-V); Windows Server 2012; Windows Server AppFabric Internet Applications Component and Service Composition BizTalk Server 2006 R2; BizTalk Server 2006 R2 (Adapters); BizTalk Server 2009; BizTalk Server 2009 (Adapters); BizTalk Server 2010; Office Professional 2010 (Access 2010); Office SharePoint Server 2007; Office SharePoint Server 2007 (Business Data Catalog); SharePoint 2010; SharePoint 2010 (Business Connectivity Services); SQL Server 2008 R2/2012; Visual Studio 2008/2010; Windows Server AppFabric Enterprise Integration .NET Framework; BizTalk Server 2006 R2/2009/2010; SQL Azure; SQL Server 2008 R2/2012; Visual Studio 11/2008; Visual Studio 2010 Professional Development Platform Office Professional 2010; SQL Server 2008 R2; Visual Studio 11; Visual Studio 2008; Visual Studio 2010 Professional; Visual Studio Team Foundation Server 2010; Windows SDK Application Lifecycle Management Office Professional 2010; Project 2010; Visual Studio 11 Team Foundation Server; Visual Studio 2008/2010; Visual Studio Team Foundation Server 2010
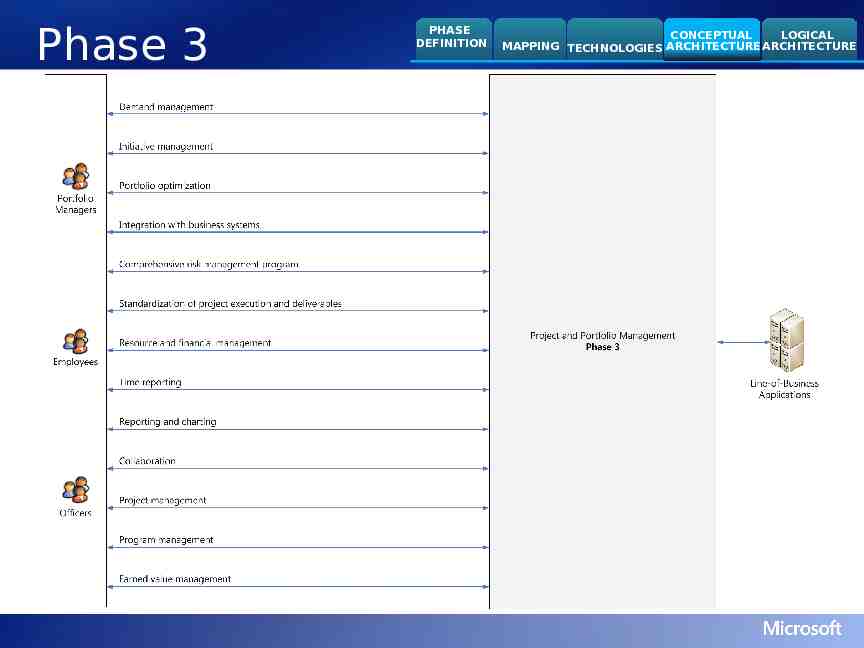
Phase 3 PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE
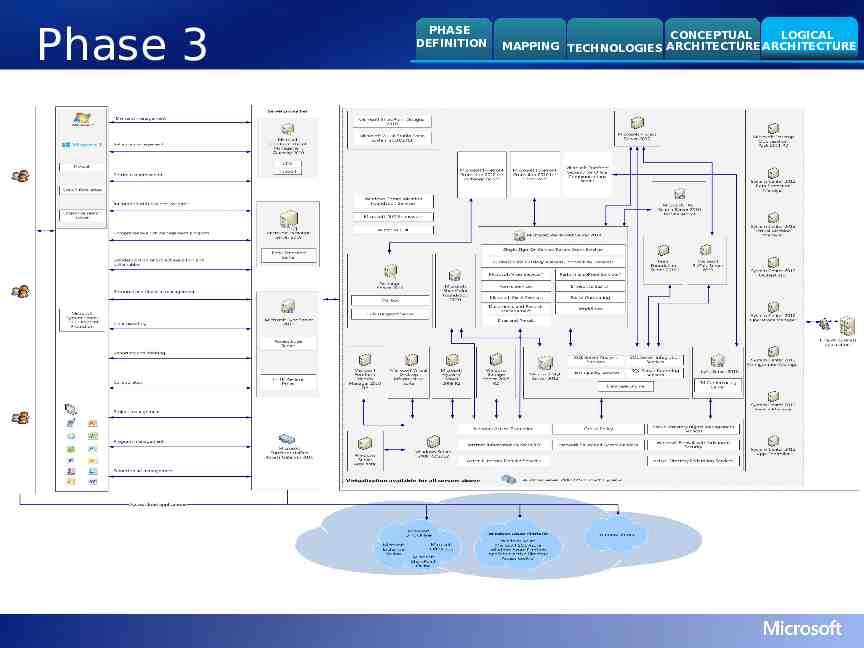
Phase 3 PHASE DEFINITION CONCEPTUAL LOGICAL MAPPING TECHNOLOGIES ARCHITECTURE ARCHITECTURE
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
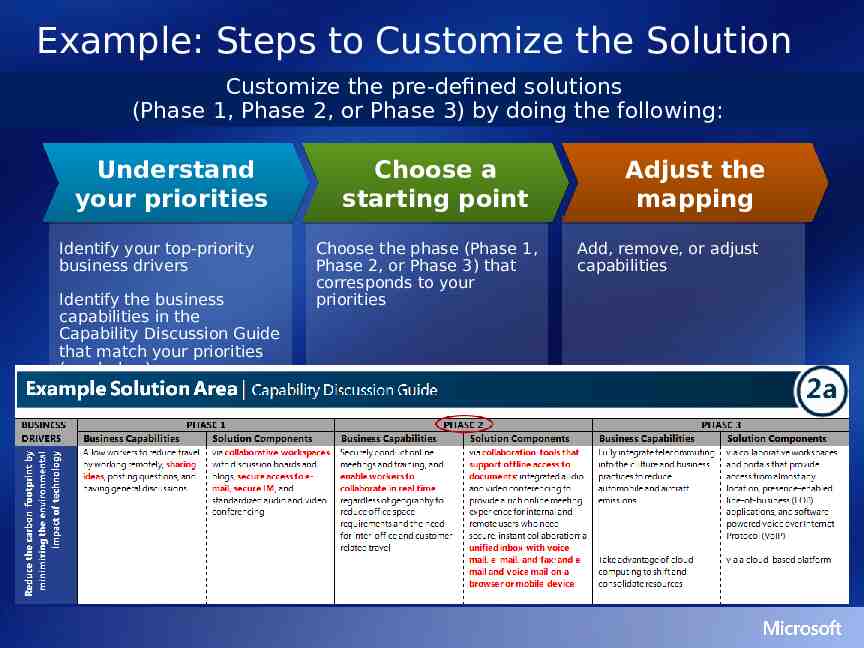
Example: Steps to Customize the Solution Customize the pre-defined solutions (Phase 1, Phase 2, or Phase 3) by doing the following: Understand your priorities Identify your top-priority business drivers Identify the business capabilities in the Capability Discussion Guide that match your priorities (see below) Choose a starting point Choose the phase (Phase 1, Phase 2, or Phase 3) that corresponds to your priorities Adjust the mapping Add, remove, or adjust capabilities
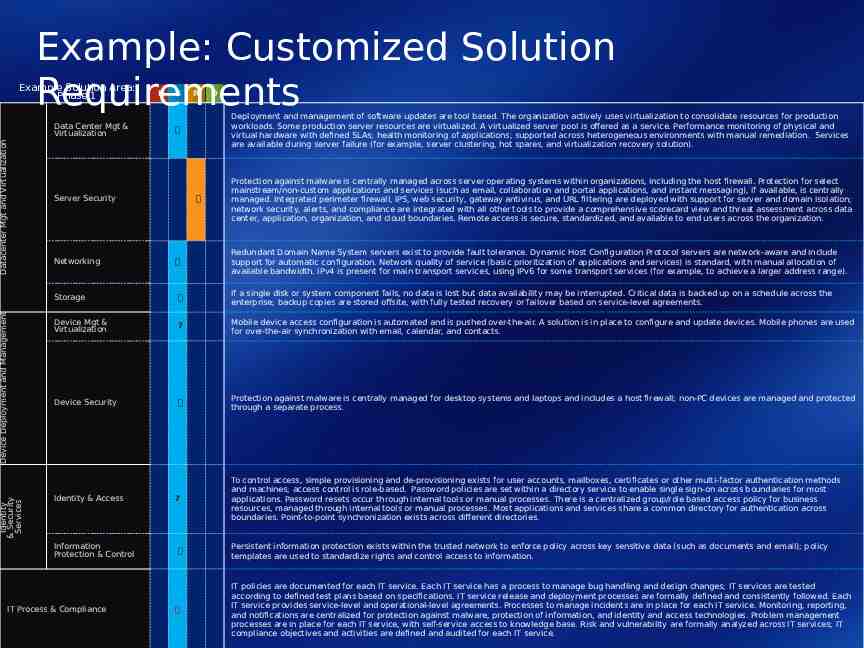
Example: Customized Solution Requirements Example Solution Area: Phase 1 Identity & Security Services Device Deployment and Management Datacenter Mgt and Virtualization Data Center Mgt & Virtualization B S R Deployment and management of software updates are tool based. The organization actively uses virtualization to consolidate resources for production workloads. Some production server resources are virtualized. A virtualized server pool is offered as a service. Performance monitoring of physical and virtual hardware with defined SLAs; health monitoring of applications; supported across heterogeneous environments with manual remediation. Services are available during server failure (for example, server clustering, hot spares, and virtualization recovery solution). Server Security D Protection against malware is centrally managed across server operating systems within organizations, including the host firewall. Protection for select mainstream/non-custom applications and services (such as email, collaboration and portal applications, and instant messaging), if available, is centrally managed. Integrated perimeter firewall, IPS, web security, gateway antivirus, and URL filtering are deployed with support for server and domain isolation; network security, alerts, and compliance are integrated with all other tools to provide a comprehensive scorecard view and threat assessment across data center, application, organization, and cloud boundaries. Remote access is secure, standardized, and available to end users across the organization. Networking Redundant Domain Name System servers exist to provide fault tolerance. Dynamic Host Configuration Protocol servers are network-aware and include support for automatic configuration. Network quality of service (basic prioritization of applications and services) is standard, with manual allocation of available bandwidth. IPv4 is present for main transport services, using IPv6 for some transport services (for example, to achieve a larger address range). Storage If a single disk or system component fails, no data is lost but data availability may be interrupted. Critical data is backed up on a schedule across the enterprise; backup copies are stored offsite, with fully tested recovery or failover based on service-level agreements. Device Mgt & Virtualization ? Mobile device access configuration is automated and is pushed over-the-air. A solution is in place to configure and update devices. Mobile phones are used for over-the-air synchronization with email, calendar, and contacts. Device Security Protection against malware is centrally managed for desktop systems and laptops and includes a host firewall; non-PC devices are managed and protected through a separate process. Identity & Access ? To control access, simple provisioning and de-provisioning exists for user accounts, mailboxes, certificates or other multi-factor authentication methods and machines; access control is role-based. Password policies are set within a directory service to enable single sign-on across boundaries for most applications. Password resets occur through internal tools or manual processes. There is a centralized group/role based access policy for business resources, managed through internal tools or manual processes. Most applications and services share a common directory for authentication across boundaries. Point-to-point synchronization exists across different directories. Information Protection & Control Persistent information protection exists within the trusted network to enforce policy across key sensitive data (such as documents and email); policy templates are used to standardize rights and control access to information. IT policies are documented for each IT service. Each IT service has a process to manage bug handling and design changes; IT services are tested according to defined test plans based on specifications. IT service release and deployment processes are formally defined and consistently followed. Each IT service provides service-level and operational-level agreements. Processes to manage incidents are in place for each IT service. Monitoring, reporting, and notifications are centralized for protection against malware, protection of information, and identity and access technologies. Problem management processes are in place for each IT service, with self-service access to knowledge base. Risk and vulnerability are formally analyzed across IT services; IT compliance objectives and activities are defined and audited for each IT service. IT Process & Compliance
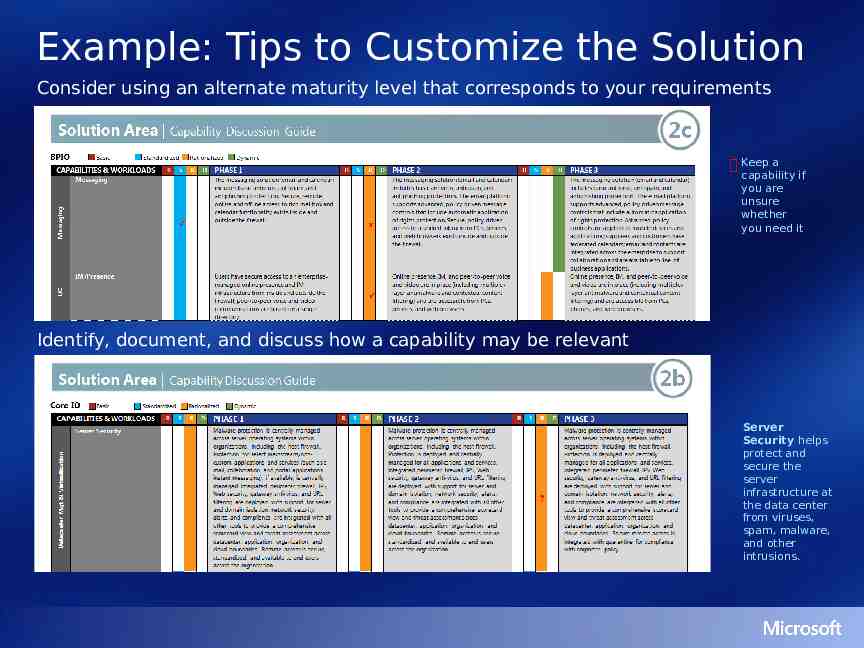
Example: Tips to Customize the Solution Consider using an alternate maturity level that corresponds to your requirements Keep a capability if you are unsure whether you need it Identify, document, and discuss how a capability may be relevant Server Security helps protect and secure the server infrastructure at the data center from viruses, spam, malware, and other intrusions.
Agenda Recap Discussions to Date Solution Guidance Phase 1 Phase 2 Phase 3 ustomize the Solution Requirements Next Steps
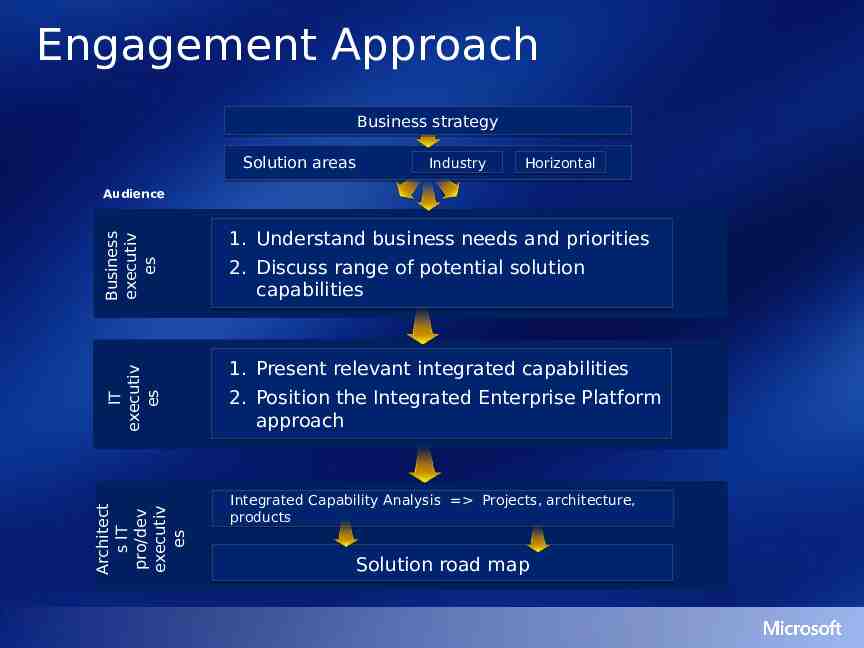
Engagement Approach Business strategy Solution areas Industry Horizontal Business executiv es 1. Present relevant integrated capabilities 2. Position the Integrated Enterprise Platform approach Architect s IT pro/dev executiv es 1. Understand business needs and priorities 2. Discuss range of potential solution capabilities IT executiv es Audience Integrated Capability Analysis Projects, architecture, products Solution road map

2012 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.