PROGRESS ON THE IMPLEMENTATION OF AUDIT RECOMMENDATIONS FOR
11 Slides518.27 KB

PROGRESS ON THE IMPLEMENTATION OF AUDIT RECOMMENDATIONS FOR 2014/15: INFORMATION AND COMMUNICATION TECHNOLOGY (ICT) 16 February 2016 Briefing presentation to the Portfolio Committee on Environmental Affairs (PCEA) 1

PRESENTATION OUTLINE – – – – Summary for the implementation of audit recommendations Information Technology (IT) security management IT service continuity Corporate Governance of IT/Governance of IT 2
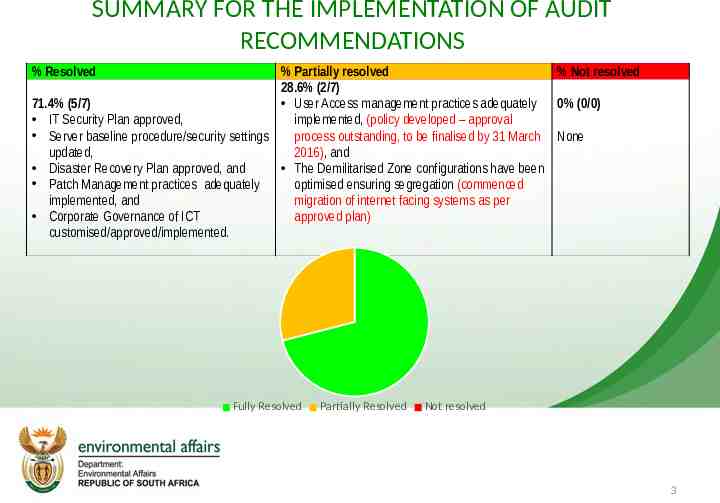
SUMMARY FOR THE IMPLEMENTATION OF AUDIT RECOMMENDATIONS % Resolved % Partially resolved % Not resolved 28.6% (2/7) User Access management practices adequately 0% (0/0) 71.4% (5/7) IT Security Plan approved, implemented, (policy developed – approval Server baseline procedure/security settings process outstanding, to be finalised by 31 March None updated, 2016), and Disaster Recovery Plan approved, and The Demilitarised Zone configurations have been Patch Management practices adequately optimised ensuring segregation (commenced implemented, and migration of internet facing systems as per Corporate Governance of ICT approved plan) customised/approved/implemented. Fully Resolved Partially Resolved Not resolved 3
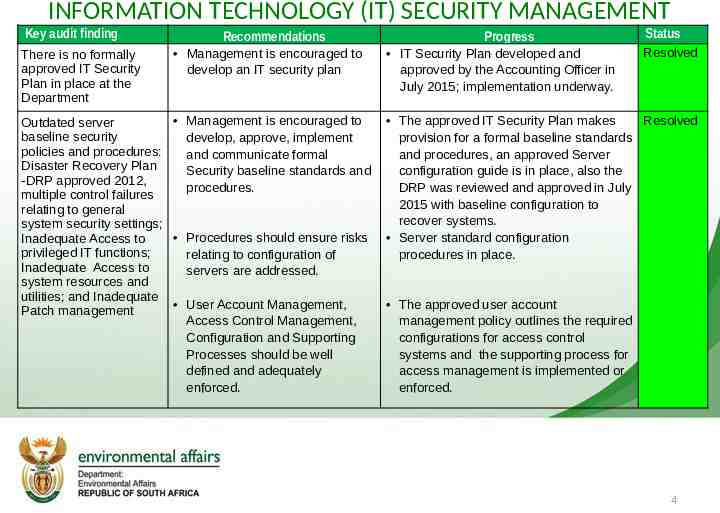
INFORMATION TECHNOLOGY (IT) SECURITY MANAGEMENT Key audit finding There is no formally approved IT Security Plan in place at the Department Recommendations Management is encouraged to develop an IT security plan Management is encouraged to Outdated server baseline security develop, approve, implement policies and procedures: and communicate formal Disaster Recovery Plan Security baseline standards and -DRP approved 2012, procedures. multiple control failures relating to general system security settings; Procedures should ensure risks Inadequate Access to privileged IT functions; relating to configuration of Inadequate Access to servers are addressed. system resources and utilities; and Inadequate User Account Management, Patch management Access Control Management, Configuration and Supporting Processes should be well defined and adequately enforced. Progress IT Security Plan developed and approved by the Accounting Officer in July 2015; implementation underway. Status Resolved The approved IT Security Plan makes Resolved provision for a formal baseline standards and procedures, an approved Server configuration guide is in place, also the DRP was reviewed and approved in July 2015 with baseline configuration to recover systems. Server standard configuration procedures in place. The approved user account management policy outlines the required configurations for access control systems and the supporting process for access management is implemented or enforced. 4
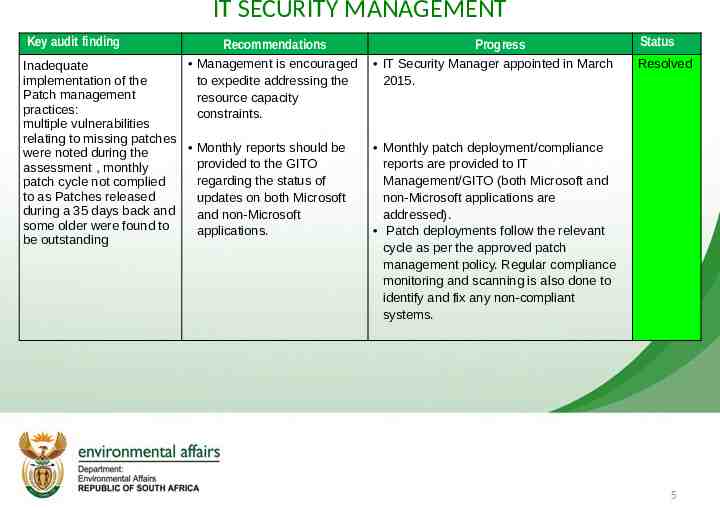
IT SECURITY MANAGEMENT Key audit finding Recommendations Management is encouraged Inadequate implementation of the to expedite addressing the Patch management resource capacity practices: constraints. multiple vulnerabilities relating to missing patches Monthly reports should be were noted during the provided to the GITO assessment , monthly regarding the status of patch cycle not complied to as Patches released updates on both Microsoft during a 35 days back and and non-Microsoft some older were found to applications. be outstanding Progress IT Security Manager appointed in March 2015. Status Resolved Monthly patch deployment/compliance reports are provided to IT Management/GITO (both Microsoft and non-Microsoft applications are addressed). Patch deployments follow the relevant cycle as per the approved patch management policy. Regular compliance monitoring and scanning is also done to identify and fix any non-compliant systems. 5
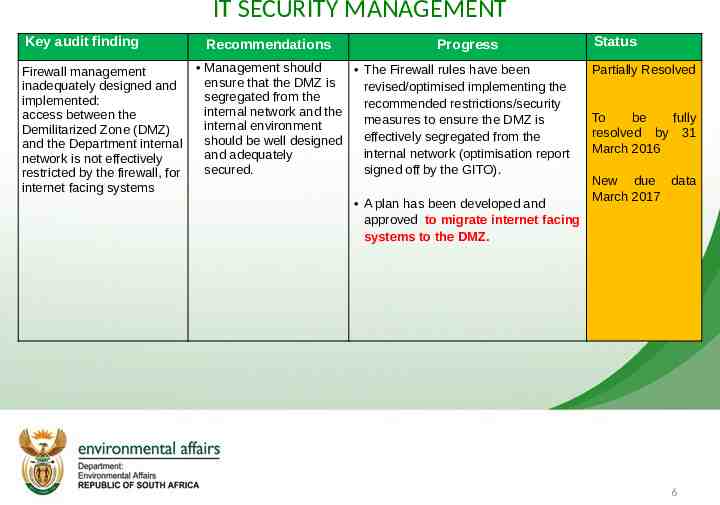
IT SECURITY MANAGEMENT Key audit finding Recommendations Progress Management should The Firewall rules have been Firewall management ensure that the DMZ is inadequately designed and revised/optimised implementing the segregated from the implemented: recommended restrictions/security internal network and the access between the measures to ensure the DMZ is internal environment Demilitarized Zone (DMZ) effectively segregated from the should be well designed and the Department internal internal network (optimisation report and adequately network is not effectively secured. signed off by the GITO). restricted by the firewall, for internet facing systems A plan has been developed and approved to migrate internet facing systems to the DMZ. Status Partially Resolved To be fully resolved by 31 March 2016 New due data March 2017 6
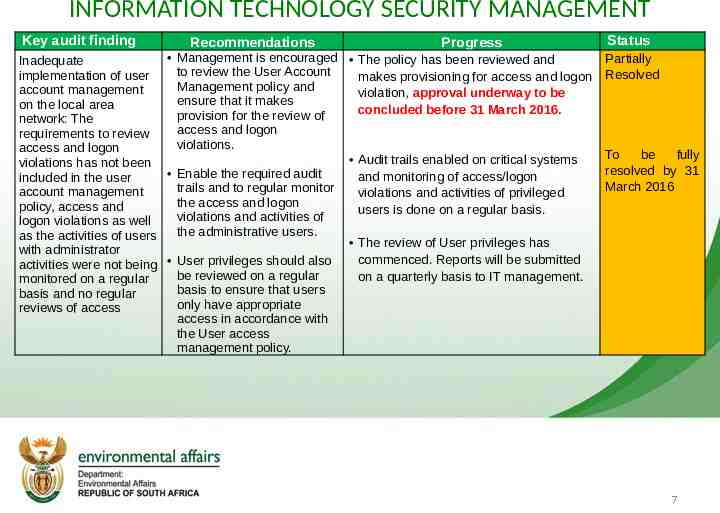
INFORMATION TECHNOLOGY SECURITY MANAGEMENT Key audit finding Recommendations Progress Management is encouraged The policy has been reviewed and Inadequate to review the User Account implementation of user makes provisioning for access and logon Management policy and account management violation, approval underway to be ensure that it makes on the local area concluded before 31 March 2016. provision for the review of network: The access and logon requirements to review violations. access and logon Audit trails enabled on critical systems violations has not been Enable the required audit and monitoring of access/logon included in the user trails and to regular monitor account management violations and activities of privileged the access and logon policy, access and users is done on a regular basis. violations and activities of logon violations as well the administrative users. as the activities of users The review of User privileges has with administrator commenced. Reports will be submitted activities were not being User privileges should also be reviewed on a regular on a quarterly basis to IT management. monitored on a regular basis to ensure that users basis and no regular only have appropriate reviews of access access in accordance with the User access management policy. Status Partially Resolved To be fully resolved by 31 March 2016 7

INFORMATION TECHNOLOGY SERVICES CONTINUITY Key audit finding Outdated Business continuity plan (BCP) and Information technology disaster recovery plan: plans have not yet been updated to reflect the changes in the environment since the relocation to the new office building, which also includes the migration to Microsoft Active Directory Recommendations Progress Status Management is encouraged to update the current BCP and DRP with the changes in the environment due to the relocation to the new office building and migration projects from IT. Resolved The BCP has been updated by the respective Directorate with inputs from relevant Management structures to reflect the changes of the new environment and outlining all the continuity requirements. The IT Disaster Recovery Plan has been reviewed and updated to cater for the new environment and platforms in place, and it was approved by the Accounting Officer in July 2015. The updated BCP including the DRP should periodically be tested to ensure that the plan is practical with regard to its execution/activation. The DRP is tested twice annually, the first test has been concluded successfully. The second recovery test is scheduled before the financial year end (disaster recovery site commissioned at SITA Centurion). 8
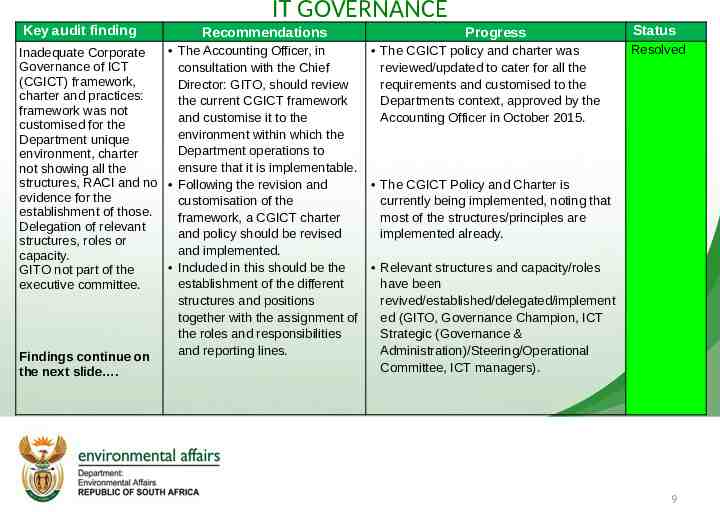
Key audit finding IT GOVERNANCE Recommendations The Accounting Officer, in Inadequate Corporate Governance of ICT consultation with the Chief (CGICT) framework, Director: GITO, should review charter and practices: the current CGICT framework framework was not and customise it to the customised for the environment within which the Department unique Department operations to environment, charter ensure that it is implementable. not showing all the structures, RACI and no Following the revision and evidence for the customisation of the establishment of those. framework, a CGICT charter Delegation of relevant and policy should be revised structures, roles or and implemented. capacity. Included in this should be the GITO not part of the establishment of the different executive committee. structures and positions together with the assignment of the roles and responsibilities and reporting lines. Findings continue on the next slide . Progress The CGICT policy and charter was reviewed/updated to cater for all the requirements and customised to the Departments context, approved by the Accounting Officer in October 2015. Status Resolved The CGICT Policy and Charter is currently being implemented, noting that most of the structures/principles are implemented already. Relevant structures and capacity/roles have been revived/established/delegated/implement ed (GITO, Governance Champion, ICT Strategic (Governance & Administration)/Steering/Operational Committee, ICT managers). 9
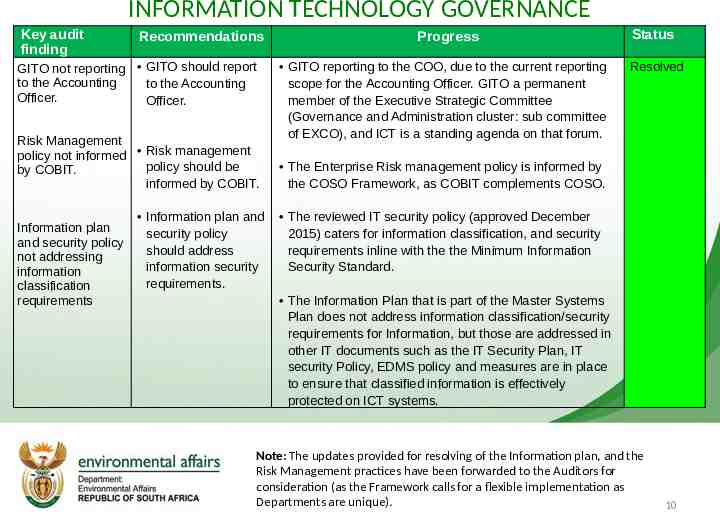
INFORMATION TECHNOLOGY GOVERNANCE Key audit finding Recommendations GITO not reporting GITO should report to the Accounting to the Accounting Officer. Officer. Risk Management policy not informed Risk management policy should be by COBIT. informed by COBIT. Information plan and security policy not addressing information classification requirements Information plan and security policy should address information security requirements. Progress GITO reporting to the COO, due to the current reporting scope for the Accounting Officer. GITO a permanent member of the Executive Strategic Committee (Governance and Administration cluster: sub committee of EXCO), and ICT is a standing agenda on that forum. Status Resolved The Enterprise Risk management policy is informed by the COSO Framework, as COBIT complements COSO. The reviewed IT security policy (approved December 2015) caters for information classification, and security requirements inline with the the Minimum Information Security Standard. The Information Plan that is part of the Master Systems Plan does not address information classification/security requirements for Information, but those are addressed in other IT documents such as the IT Security Plan, IT security Policy, EDMS policy and measures are in place to ensure that classified information is effectively protected on ICT systems. Note: The updates provided for resolving of the Information plan, and the Risk Management practices have been forwarded to the Auditors for consideration (as the Framework calls for a flexible implementation as Departments are unique). 10

Thank you. 11