Microsoft Virtual Academy ® Module 6/7 Implementing Remote Access
51 Slides2.52 MB

Microsoft Virtual Academy Module 6/7 Implementing Remote Access

Module Overview Overview of Remote Access Implementing DirectAccess by Using the Getting Started Wizard Implementing and Managing an Advanced DirectAccess Infrastructure Implementing VPN Web Application Proxy

Overview of Remote Access

Lesson 1: Overview of Remote Access Remote Access Options Managing Remote Access in Windows Server 2012 Demonstration: Installing and Managing the Remote Access Role Network Address Translation Considerations for Deploying a PKI for Remote Access Configuring User Settings for Remote Access
Remote Access Options Remote access options in Windows Server 2012 R2 include: DirectAccess VPN Routing Web Application Proxy
Managing Remote Access in Windows Server 2012 You can manage the Remote Access role by using: Remote Access Management Console Routing and Remote Access console Windows PowerShell Set-DAServer Get-DAServer Set-RemoteAccess Get-RemoteAccess
Demonstration: Installing and Managing the Remote Access Role In this demonstration, you will see how to: Install the Remote Access role Manage the Remote Access role
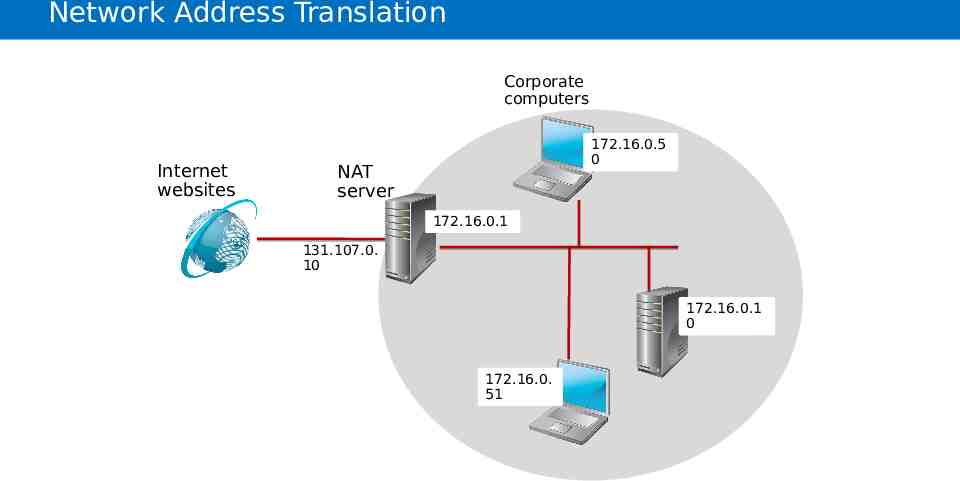
Network Address Translation Corporate computers Internet websites 172.16.0.5 0 NAT server 172.16.0.1 131.107.0. 10 172.16.0.1 0 172.16.0. 51

Configuring User Settings for Remote Access User Settings for Remote Access include: Network Access Permission Allow access Deny access Control access through NPS Network Policy Verify Caller-ID Callback Options Assign Static IP Addresses Apply Static Routes

Implementing DirectAccess by Using the Getting Started Wizard

Lesson 1: Implementing DirectAccess by Using the Getting Started Wizard DirectAccess Components DirectAccess Server Deployment Options DirectAccess Tunneling Protocol Options How DirectAccess Works for Internal Clients How DirectAccess Works for External Clients Demonstration: Running the Getting Started Wizard Getting Started Wizard Configuration Changes Demonstration: Identifying the Getting Started Wizard Settings Limitations of DirectAccess Deployments When Using the

DirectAccess Components Internal clients Internet websites AD DS domain controller DNS server DirectAccess server NRPT/ Consec IPv6/ IPsec External clients Internal network resources PKI deployment Network location server

DirectAccess Server Deployment Options DirectAccess server deployment options include: Deploying multiple endpoints Supporting Multiple domains Deploying a server behind a NAT Supporting OTP and virtual smart cards Supporting NIC Teaming Provisioning Off-premise

DirectAccess Tunneling Protocol Options DirectAccess tunneling protocols include: ISATAP – Tunnels IPv6 traffic over IPv4 networks for intranet communication 6to4 – Used by DirectAccess clients with a public IP address Teredo – Used by DirectAccess clients with a private IP address behind a NAT device IP HTTPS – Used by DirectAccess clients if they are not able to use ISATAP, 6to4, or Teredo
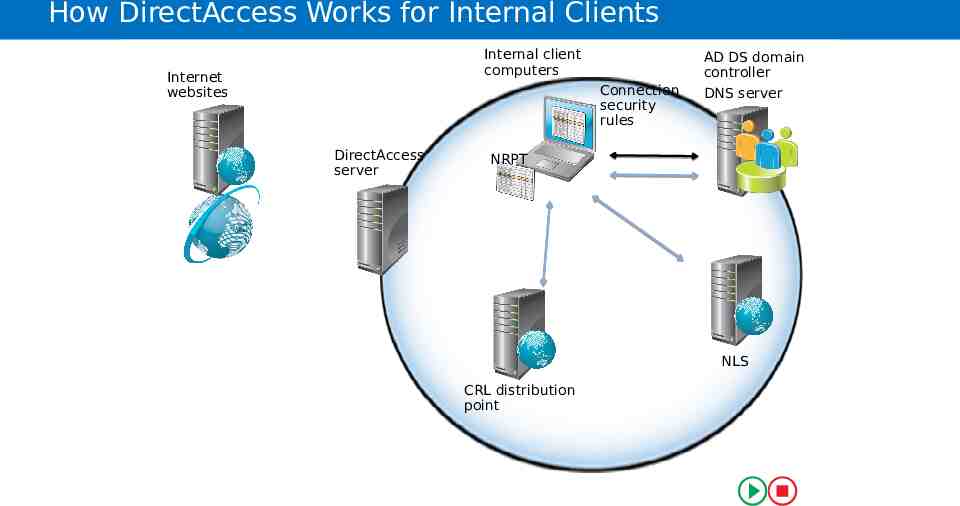
How DirectAccess Works for Internal Clients Internalclient client Internal computers computers Internet Internet websites websites Connection security rules DirectAccess DirectAccess server server ADDS DSdomain domain AD controller controller DNSserver server DNS NRPT NLS NLS Internal network CRL distribution resources point
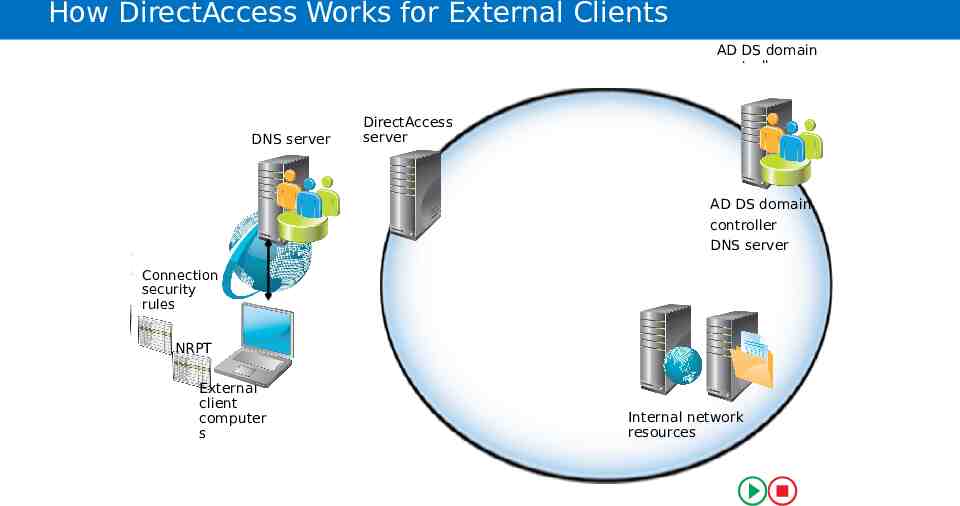
How DirectAccess Works for External Clients AD DS domain controller DNS server DNS server Internet websites Connection Connection security Connection Connection security rules security security rules rules rules DirectAccess DNS server server DNS server DNS server DirectAccess server e ur t c tur ru astrucu t s Infr ruct r a r as t f In Inefr e NRPT NRPT NRPT NRPT External client External External External client computers client client computer computer s computer s s Direct Access server Direct Access server AD DS domain AD DS domain AD DS domain controller controller controller DNS server DNS server DNS server t aneet r t I n an Intr Internal network resources Internal network Internal network Internal network resources resources resources

Demonstration: Running the Getting Started Wizard In this demonstration, you will see how to configure DirectAccess by running the Getting Started Wizard
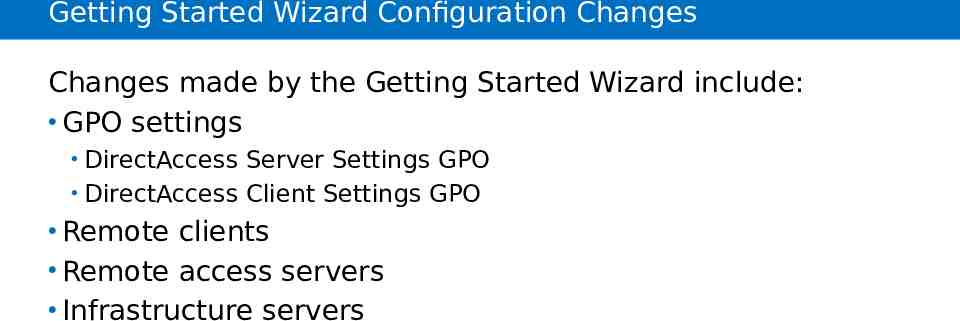
Getting Started Wizard Configuration Changes Changes made by the Getting Started Wizard include: GPO settings DirectAccess Server Settings GPO DirectAccess Client Settings GPO Remote clients Remote access servers Infrastructure servers

Demonstration: Identifying the Getting Started Wizard Settings In this demonstration, you will see how to identify changes made by the DirectAccess Getting Started Wizard

Limitations of DirectAccess Deployments When Using the Getting Started Wizard Certificates Self-signed certificates cannot be used in multisite deployments Needs you to ensure the CRL distribution point for both certificates is available externally Network Location Server Design Deploys the Network Location Server on the same server as the DirectAccess server Windows client operating system support Getting Started Wizard configuration is applicable for clients running Windows 8 or Windows Server 2012 Windows 7 clients require a client certificate for IPsec authentication

Implementing and Managing an Advanced DirectAccess Infrastructure

Lesson 2: Implementing and Managing an Advanced DirectAccess Infrastructure Overview of the Advanced DirectAccess Options Integrating a PKI with DirectAccess Implementing Client Certificates for DirectAccess Internal Network Configuration Options Configuring Advanced DNS Settings Implementing Network Location Servers Implementing Management Servers Demonstration: Modifying the DirectAccess Infrastructure How to Monitor DirectAccess Connectivity How to Troubleshoot DirectAccess Connectivity Demonstration: Monitoring and Troubleshooting DirectAccess

Overview of the Advanced DirectAccess Options Advanced DirectAccess configuration options include: Scalable and customized PKI infrastructure Customized network configuration options Scalable and highly-available server deployment Customized monitoring and troubleshooting

Integrating a PKI with DirectAccess Configuring PKI for DirectAccess includes the following steps: 1. Add and configure the CA server role if not already present 2. Create the certificate template 3. Create a CRL distribution point and publish the CRL list 4. Distribute the computer certificates

Implementing Client Certificates for DirectAccess A computer certificate for IPSec authentication is needed for DirectAccess clients running Windows 7 Steps for deploying certificates for client computers: 1. Create a GPO and link it to the organizational unit that contains the DirectAccess clients 2. Configure the GPO for automatic certificate request for the computer account 3. Apply the GPO 4. Verify that the certificates are issued

Internal Network Configuration Options Planning for internal network configuration requires you to plan for: DirectAccess server location (Edge, perimeter network, and internal network) IP address assignment Firewall configuration Active Directory Client deployment

Configuring Advanced DNS Settings DirectAccess uses DNS for resolving: NLS IP-HTTPS CRL distribution point ISATAP Connectivity verifiers You can configure NRPT by using Group Policy with the following settings: DNS suffixes CRL distribution point Split-brain DNS

Implementing Network Location Servers NLS can be located on: A DirectAccess server Another server with IIS installed Requirements for NLS configuration: Configuring NLS web site certificate CA that is trusted by DirectAccess clients Configuring NLS web site certificate CRL NLS should be accessible by internal clients NLS should not be accessible by Internet clients NLS should be highly available

Implementing Management Servers Management servers in DirectAccess are: Domain controllers SCCM servers Management servers are detected by DirectAccess: Automatically Manually if modified Management server requirements: Must be accessible for the infrastructure tunnel Must fully support IPv6

Demonstration: Modifying the DirectAccess Infrastructure In this demonstration, you will see how to: Modify the DirectAccess infrastructure deployed by using the Getting Started Wizard Apply advanced configuration settings
How to Monitor DirectAccess Connectivity Remote Access Management Console monitoring components: Dashboard Operations Status Remote Access Client Status Remote Access Reporting

How to Troubleshoot DirectAccess Connectivity You can troubleshoot DirectAccess connectivity by using: A troubleshooting methodology Command-line tools GUI tools
Demonstration: Monitoring and Troubleshooting DirectAccess Connectivity In this demonstration, you will see how to monitor and troubleshoot DirectAccess connectivity

Implementing VPN

Lesson 2: Implementing VPN VPN Scenarios VPN Tunneling Protocol Options VPN Authentication Options What Is VPN Reconnect? VPN Configuration by Using the Getting Started Wizard Options for Modifying the VPN Configuration Demonstration: Configuring VPN What Is the Connection Manager Administration Kit? Demonstration: How to Create a Connection Profile
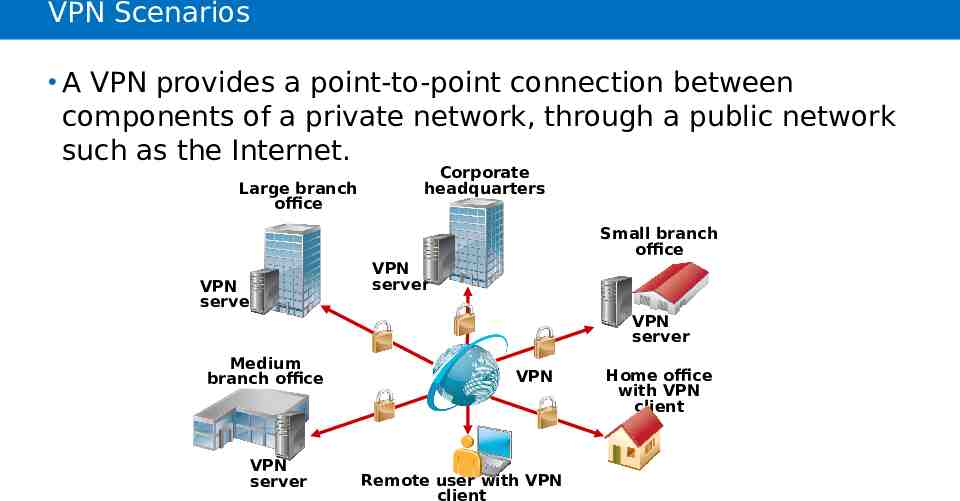
VPN Scenarios A VPN provides a point-to-point connection between components of a private network, through a public network such as the Internet. Large branch office Corporate headquarters Small branch office VPN server VPN server VPN server Medium branch office VPN server VPN Remote user with VPN client Home office with VPN client

VPN Tunneling Protocol Options Windows Server 2012 supports four VPN tunneling protocols Tunneling Firewall access Description PPTP TCP port 1723 Provides data confidentiality but not data integrity or data authentication. L2TP/IPsec UDP port 500, UDP port 1701, UDP port 4500, and IP protocol ID 50 Uses either certificates or preshared keys for authentication. Certificate authentication is recommended. SSTP TCP port 443 Uses SSL to provide data confidentiality, data integrity, and data authentication. IKEv2 UDP port 500 Supports the latest IPsec encryption algorithms to provide data confidentiality, data integrity, and data authentication. protocol

VPN Authentication Options Protocol Description Security level PAP Uses plaintext passwords. Typically used if the remote access client and remote access server cannot negotiate a more secure form of validation. The least secure authentication protocol. Does not protect against replay attacks, remote client impersonation, or remote server impersonation. CHAP A challenge-response authentication protocol that uses the industry-standard MD5 hashing scheme. An improvement over PAP in that the password is not sent over the PPP link Requires a plaintext version of the password to validate the challenge response. Does not protect against remote server impersonation. MSCHAPv2 An upgrade of MS-CHAP. Provides twoway authentication, also known as mutual authentication. The remote access client receives verification that the remote access server to which it is dialing in to has access to the user’s password. Provides stronger security than CHAP. EAP Allows for arbitrary authentication of a remote access connection through the use of authentication schemes, known Offers the strongest security by providing the most flexibility in authentication variations.

What Is VPN Reconnect? VPN Reconnect maintains connectivity across network outages VPN Reconnect: Provides seamless and consistent VPN connectivity Uses the IKEv2 technology Automatically reestablishes VPN connections when connectivity is available Maintains the connection if users move between different networks Provides transparent connection status to users

VPN Configuration by Using the Getting Started Wizard Configure VPN by using the Getting Started Wizard in the Remote Access Management console VPN server configuration requirements include: Two network interfaces (public and private) IP Address allocation (static pool or DHCP) Authentication provider (NPS/RADIUS or the VPN server) DHCP relay agent considerations Membership in the local Administrators group or equivalent

Options for Modifying the VPN Configuration You may need to perform additional steps to help to secure the installation of the VPN solution: Configure static packet filters Configure services and ports Adjust logging levels for routing protocols Configure number of available VPN ports Create a Connection Manager profile for users Add Active Directory Certificate Services Increase remote access security Increase VPN security Consider implementing VPN Reconnect
Demonstration: Configuring VPN In this demonstration, you will see how to: Review the default VPN configuration Verify certificate requirements for IKEv2 and SSTP Configure the Remote Access server
What Is the Connection Manager Administration Kit? The CMAK: Allows you to customize users’ remote connection experience by creating predefined connections on remote servers and networks Creates an executable file that can be run on a client computer to establish a network connection that you have designed Reduces Help Desk requests related to the configuration of RAS connections by: Assisting in problem resolution because the configuration is known Reducing the likelihood of user errors when users configure their own connection objects

Web Application Proxy

Lesson 5: Implementing Web Application Proxy What Is Web Application Proxy? What is AD FS Authentication Options for Web Application Proxy Publishing Applications with Web Application Proxy Demonstration: Publishing a Secure Website

What Is Web Application Proxy? Web Application Proxy: Is introduced in Windows Server 2012 R2 Functions as a reverse web proxy Uses AD FS proxy functionality Is located in a perimeter network Web Application Proxy Client Devices Firewall Internet AD FS AD DS LOB Applications Firewall Microsoft Applications Corporate Network

What is AD FS AD FS is the Microsoft identity federation solution that can use claims-based authentication AD FS includes the following features: Web SSO Web services interoperability Support for different types of clients Extensible architecture Enhanced security

Authentication Options for Web Application Proxy User authentication: AD FS pre-authentication Pass-through pre-authentication AD FS benefits: Workplace join SSO Multifactor authentication Multifactor access control

Publishing Applications with Web Application Proxy Configuring Web Application Proxy settings AD FS server name AD FS administrator credentials AD FS certificate Publishing web application Type of preauthentication, for example Pass-through Details of the application that will be published The external URL of the application, for example, https://lon-svr1.adatum.com/ A certificate whose subject name covers the external URL, for example lon-svr1.adatum.com URL of the back end server
Demonstration: Publishing a Secure Website In this demonstration, you will see how to: Install the Web Application Proxy role service Configure access to an internal web site Verify access to the internal web site from the client computer

Additional Resources & Next Steps Instructor-Led Courses 20411C: Administering Windows Server 2012 Books Exam Ref 70-411: Administering Windows Server 2012 Exams & Certifications Exam 70-411: Administering Windows Server 2012