Cyber Security Summit: Addressing Cyber Security Risk October 10, 2017
62 Slides6.21 MB

Cyber Security Summit: Addressing Cyber Security Risk October 10, 2017 National Rural Electric Cooperative Association (NRECA) & American Public Power Association (Public Power) Dr. Cynthia Hsu Cybersecurity Program Manager NRECA

CHALLENGES Ransomware/Malware Hardware Trojans Software Development Life Cycle (SDLC) International Supply Chain Us
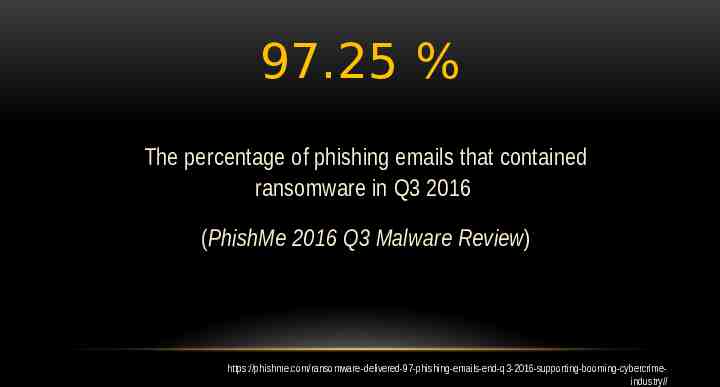
97.25 % The percentage of phishing emails that contained ransomware in Q3 2016 (PhishMe 2016 Q3 Malware Review) https://phishme.com/ransomware-delivered-97-phishing-emails-end-q3-2016-supporting-booming-cybercrimeindustry//

HARDWARE TROJANS Modifications to circuitry by adversaries to exploit hardware or to use hardware mechanisms to gain access to data or software running on the chips A Survey of Hardware Trojan Taxonomy and Detection. 2010. M. Tehranipoor & F. Koushanfar. IEEE Design and Test of Computers
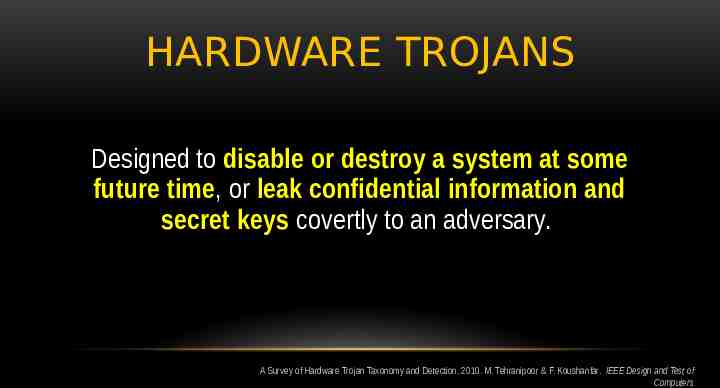
HARDWARE TROJANS Designed to disable or destroy a system at some future time, or leak confidential information and secret keys covertly to an adversary. A Survey of Hardware Trojan Taxonomy and Detection. 2010. M. Tehranipoor & F. Koushanfar. IEEE Design and Test of Computers

HARDWARE TROJANS GLOBALIZATION in the semiconductor design and fabrication process integrated circuits (ICs) are becoming increasingly vulnerable to malicious activities and alterations A Survey of Hardware Trojan Taxonomy and Detection. 2010. M. Tehranipoor & F. Koushanfar. IEEE Design and Test of Computers
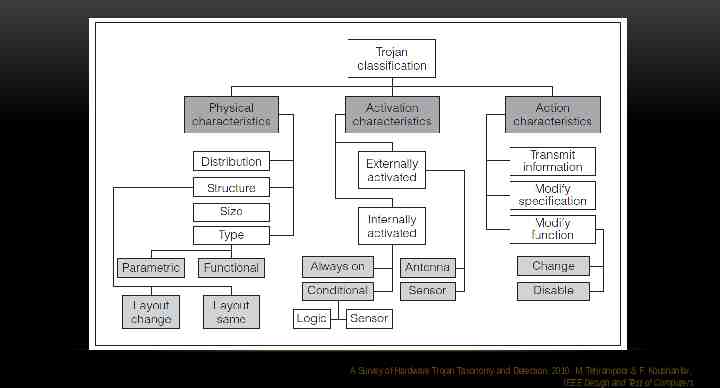
A Survey of Hardware Trojan Taxonomy and Detection. 2010. M. Tehranipoor & F. Koushanfar. IEEE Design and Test of Computers

INTELLIGENCE ADVANCED RESEARCH PROJECTS ACTIVITY (IARPA) OFFICE OF THE DIRECTOR OF NATIONAL INTELLIGENCE “In 2007, a Syrian radar failed to warn of an incoming air strike; a backdoor built into the system’s chips was rumored to be responsible.” http://spectrum.ieee.org/semiconductors/design/stopping-hardware-trojans-in-their-tracks
http://www.dmea.osd.mil/TAPO/foundryServices.html
INSECURE SOFTWARE DEVELOPMENT 1) Poor software design 2) Reliance on open source software as a base, vulnerabilities multiply into hundreds or thousands of software products built on that base and persist over time 3) Commercial Off The Shelf (COTS) products that rely on foreign and nonvetted domestic suppliers

INSECURE SOFTWARE DEVELOPMENT 1) Poor software design 2) Reliance on open source software as a base, vulnerabilities multiply into hundreds or thousands of software products built on that base and persist over time 3) Commercial Off The Shelf (COTS) products that rely on foreign and nonvetted domestic suppliers
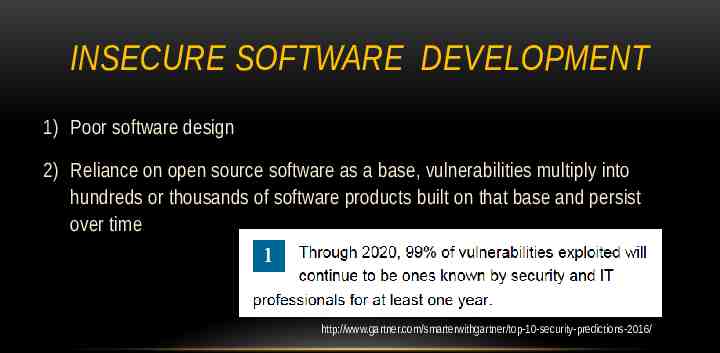
INSECURE SOFTWARE DEVELOPMENT 1) Poor software design 2) Reliance on open source software as a base, vulnerabilities multiply into hundreds or thousands of software products built on that base and persist over time 3) Commercial Off The Shelf (COTS) products that rely on foreign and nonvetted domestic suppliers http://www.gartner.com/smarterwithgartner/top-10-security-predictions-2016/

SOFTWARE DEVELOPMENT LIFE CYCLE (SDLC) Vendors sometimes neglect security and validation of software during rapid development. 2013 5,186 vulnerabilities 2017 9,202 reported by August 17 National Institute of Standards and Technology

SOFTWARE DEVELOPMENT LIFE CYCLE (SDLC) Vendors sometimes neglect security and validation of software during rapid development. 2013 5,186 vulnerabilities 2017 10 11,329 reported by October National Institute of Standards and Technology
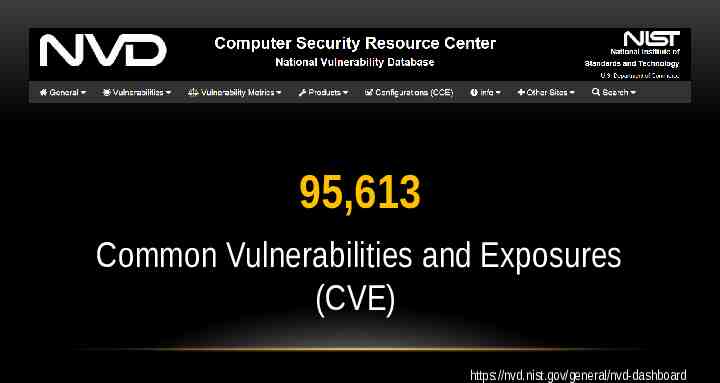
95,613 Common Vulnerabilities and Exposures (CVE) https://nvd.nist.gov/general/nvd-dashboard

EQUIFAX 140 million US consumers
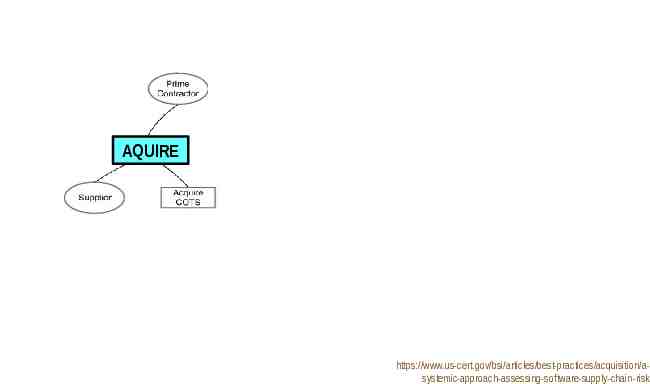
AQUIRE https://www.us-cert.gov/bsi/articles/best-practices/acquisition/asystemic-approach-assessing-software-supply-chain-risk
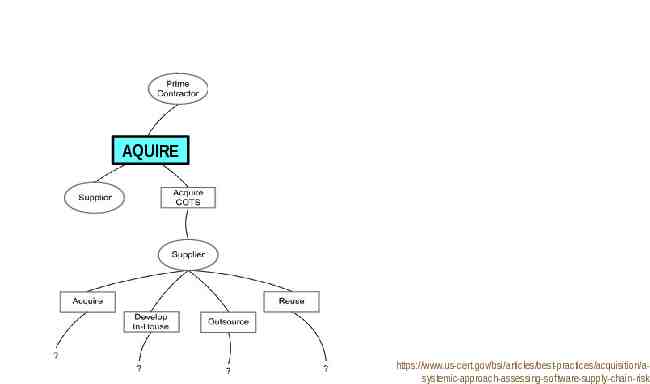
AQUIRE https://www.us-cert.gov/bsi/articles/best-practices/acquisition/asystemic-approach-assessing-software-supply-chain-risk
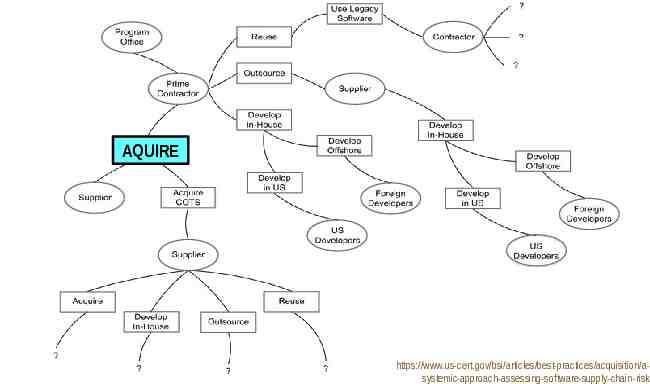
AQUIRE https://www.us-cert.gov/bsi/articles/best-practices/acquisition/asystemic-approach-assessing-software-supply-chain-risk

IMPROVING THE CYBER AND PHYSICAL SECURITY POSTURE OF THE ELECTRIC SECTOR

Up to 7.5 million over three years 2.5 million per year
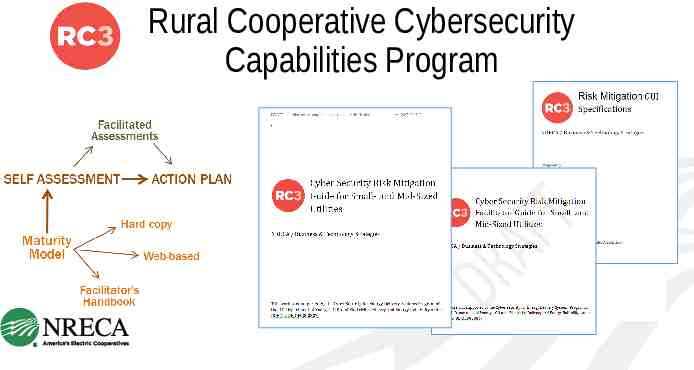
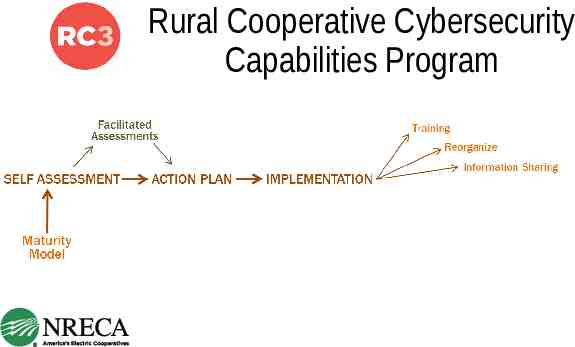
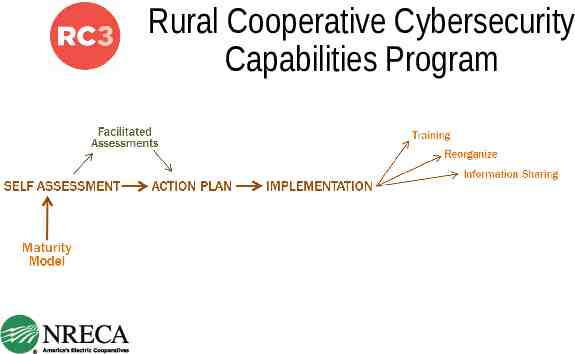
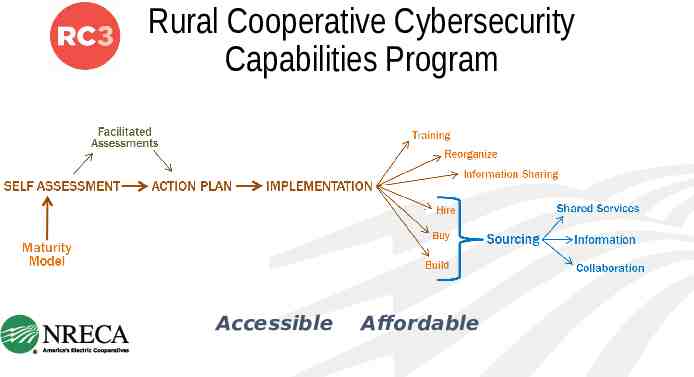
Rural Cooperative Cybersecurity Capabilities Program
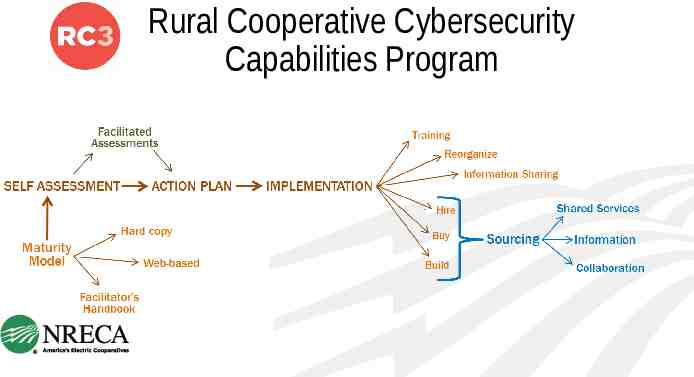
PEOPLE, PROCESS, & TECHNOLOGY

PEOPLE, PROCESS, & TECHNOLOGY

PEOPLE, PROCESS, & TECHNOLOGY

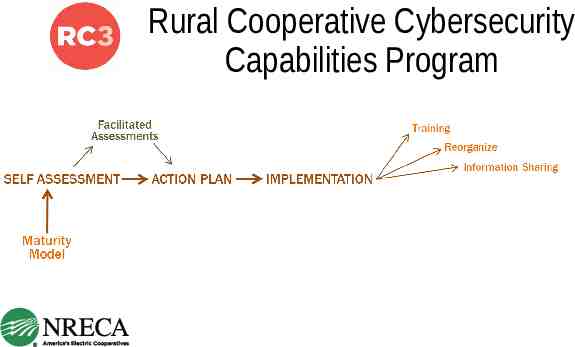
Rural Cooperative Cybersecurity Capabilities Program

Rural Cooperative Cybersecurity Capabilities Program
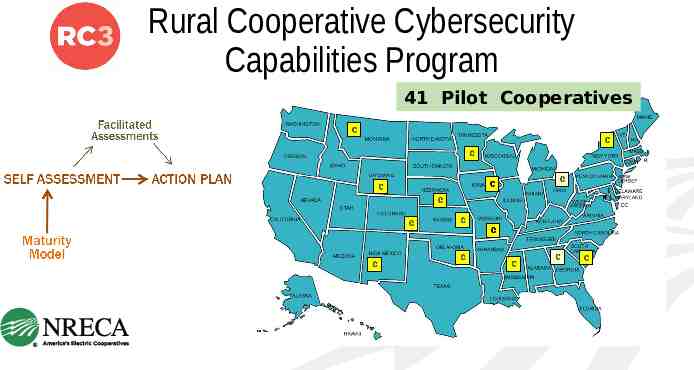
Rural Cooperative Cybersecurity Capabilities Program 41 Pilot Cooperatives
Rural Cooperative Cybersecurity Capabilities Program
Rural Cooperative Cybersecurity Capabilities Program
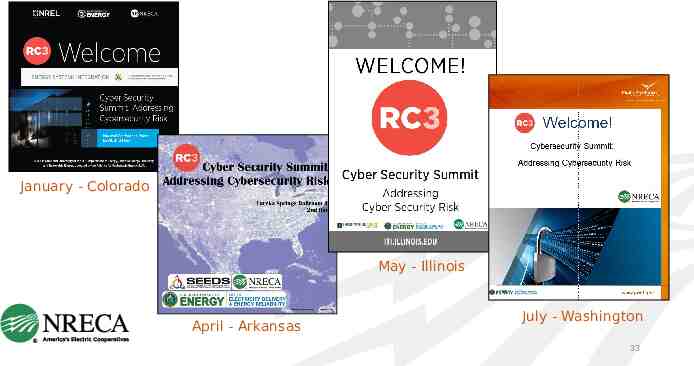
Cybersecurity Summits: Addressing Cybersecurity Risks Greg Sparks, President, CIOsource

January - Colorado May - Illinois April - Arkansas July - Washington 33
YOU DESIGN THE RESEARCH Challenge 1: Scalability of Existing Guidance Documents Challenge 2: Governance – CEO, Board of Directors, General Manager Challenge 3: Risk Management – Risk Register Challenge 4: Asset, Change, and Configuration Management Challenge 5: Time Management Challenge 6: Labor Pool Challenge 7: Technology Challenge Challenge 8: Undocumented Processes – knowledge retention, improvements, business management

WHAT WILL HAPPEN TO THE INFORMATION COLLECTED TODAY? Raw data not shared Aggregated, anonymized summaries will be used to inform: Other co-ops Future RC3 Program directions DOE

WHAT CAN NRECA/BTS DO?

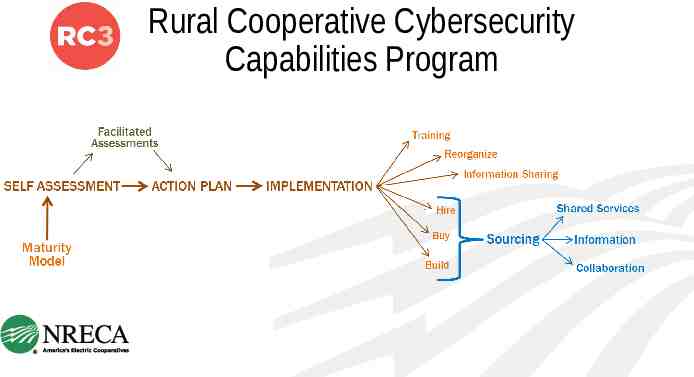
Rural Cooperative Cybersecurity Capabilities Program

GUIDING PRINCIPLES: 1. Funding is limited – solutions must be sustainable beyond the 3 years 2. Voluntary participation 3. Ongoing member engagement in program development and implementation

Rural Cooperative Cybersecurity Capabilities Program
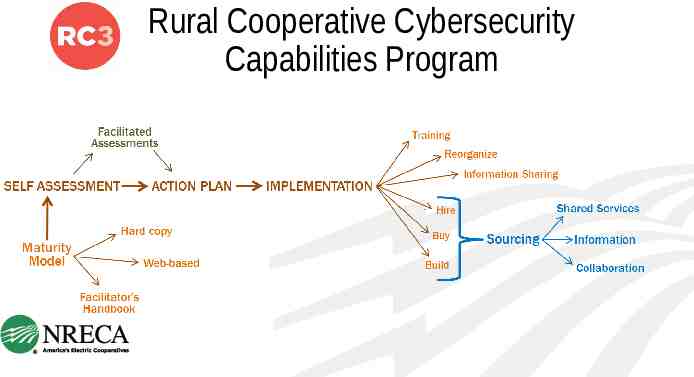
INCREASING ACCESS TO EXISTING CYBERSECURITY COURSES: Training

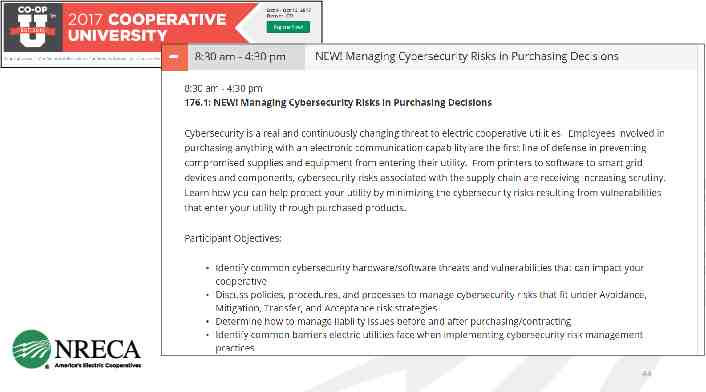
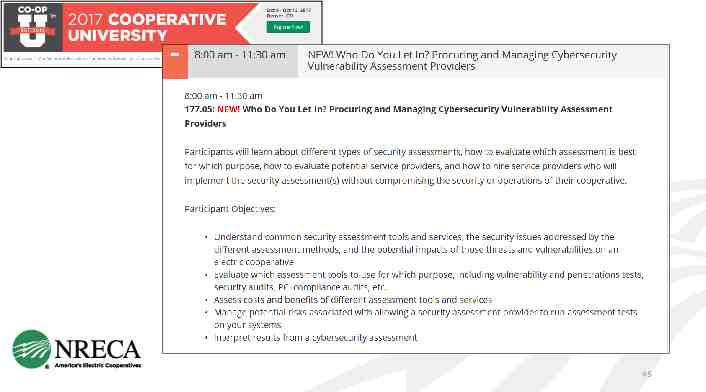
CREATING NEW CURRICULA: Training Purchasing Hardware & Software Security Assessment Services Communicators Finance/Administrative Human Relations Legal Engineers/Operators CEOs/General Managers Board Members
Training 44

Training 45

OUTREACH AND AWARENESS: Training
Rural Cooperative Cybersecurity Capabilities Program
Rural Cooperative Cybersecurity Capabilities Program

Rural Cooperative Cybersecurity Capabilities Program

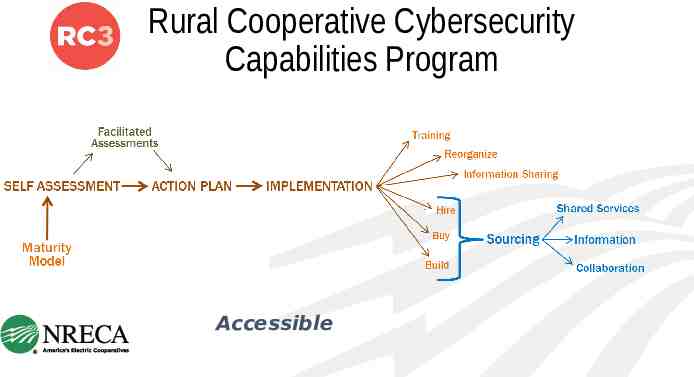
Rural Cooperative Cybersecurity Capabilities Program Accessible

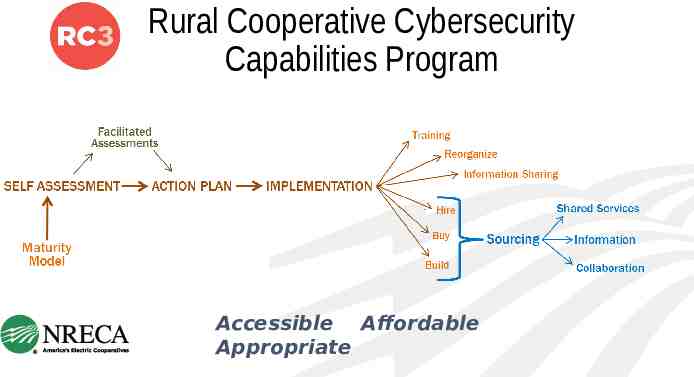
Rural Cooperative Cybersecurity Capabilities Program Accessible Affordable
Rural Cooperative Cybersecurity Capabilities Program Accessible Affordable Appropriate
CYBERSECURITY RESEARCH & DEVELOPMENT:
NRECA Resources (visit Cooperative.com) Guide to Developing a Cyber Security and Risk Mitigation Plan Toolkit – a set of tools and resources cooperatives can use to strengthen their security posture. Cyber Security Policy Framework – a collection of cybersecurity policy templates developed in collaboration with the Kentucky Association of Electric Cooperatives. RC3 Website – cybersecurity resources developed by the RC3 Program. TechUpdate – a twice-monthly email newsletter containing the latest information on technical publications, articles, reports, webinars, and conferences.
Other Resources: Cybersecurity Capability Maturity Model (C2M2) – a self-assessment evaluation tool from the Department of Energy. (https://www.energy.gov/oe/cybersecuritycapability-maturity-model-c2m2program/electricitysubsector-cybersecurity) Cybersecurity Risk Management Process (RMP) Guideline – guidance from the Department of Energy to incorporate risk management processes into a new or existing cybersecurity program. (https:// www.energy.gov/oe/downloads/cybersecurityrisk-management-process-rmp-guideline-final-may-201 2 ) Information Security Program Library (ISPL) – cybersecurity template policies, procedures, standards, and forms developed by SEDC. (https:// www.sedata.com/industry-insider/sedcsinformation-security-program-library-now-shared-with-allnrec a-member-cooperatives ) NISC Cybersecurity Services – a suite of training and network protection resources: cybersecurity.coop. Cyber Mutual Assistance (CMA) – an Electricity Subsector Coordinating Council (ESCC) initiative to develop a pool of industry experts. (http://www.electricitysubsector.org/CMA) Computer Readiness Emergency Teams (CERT) – teams funded by the Department of Homeland Security to respond to major cyber incidents, analyze threats, and exchange critical cybersecurity information with trusted partners. https://www.us-cert.gov https://www.ics-cert.us-cert.gov
IT’S A DOG EAT DOG WORLD OUT THERE
IT’S A DOG EAT DOG WORLD OUT THERE
CYBERSECURITY POLICY AND LEGISLATIVE AFFAIRS BARRY LAWSON SENIOR DIRECTOR POWER DELIVERY & RELIABILITY 703.907.5781 [email protected] OOP BRIDGETTE L. BOURGE SENIOR PRINCIPAL LEGISLATIVE AFFAIRS 703.907.6386 [email protected]

Rural Cooperative Cybersecurity Capabilities Program CYNTHIA HSU, PH.D. CYBERSECURITY PROGRAM MANAGER OFFICE: 703-907-5500 MOBILE: 703-403-8698 EMAIL: [email protected]