Managing & Securing the Directory John Howard IT Pro
29 Slides940.00 KB

Managing & Securing the Directory John Howard IT Pro Evangelist http://blogs.technet.com/jhoward

Delegation of administration Reference document on this topic is the Best practices for delegating Active Directory administration whitepaper http://www.microsoft.com/downloads/details.aspx? FamilyID 631747a3-79e1-48fa-9730dae7c0a1d6d3&DisplayLang en Need to understand business requirements and how they are going to deploy delegated admin.

Delegation of Admin (2) Fundamental approaches: – Manual configuration. This will mean creating security groups; modifying the permissions on the appropriate OUs / Objects; and providing the tools to do the job. Either mmc consoles or use command line tools. – Third party tool. Most common third party tool for this currently is Quest ActiveRoles although this should not necessarily be taken as an endorsement!
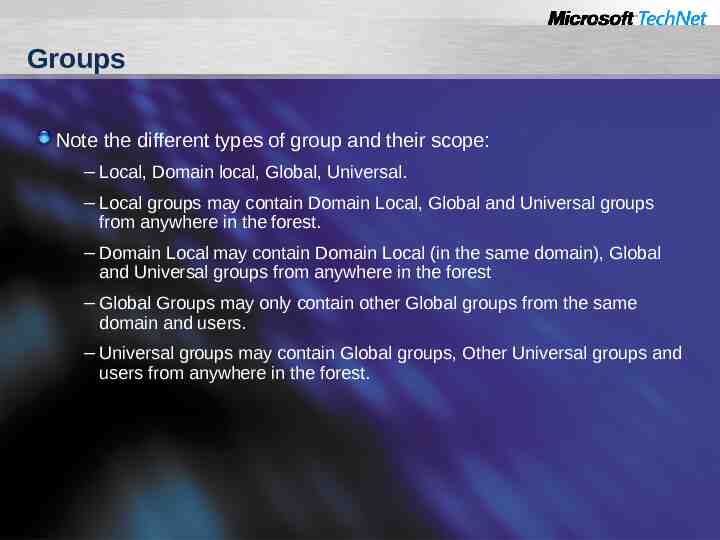
Groups Note the different types of group and their scope: – Local, Domain local, Global, Universal. – Local groups may contain Domain Local, Global and Universal groups from anywhere in the forest. – Domain Local may contain Domain Local (in the same domain), Global and Universal groups from anywhere in the forest – Global Groups may only contain other Global groups from the same domain and users. – Universal groups may contain Global groups, Other Universal groups and users from anywhere in the forest.
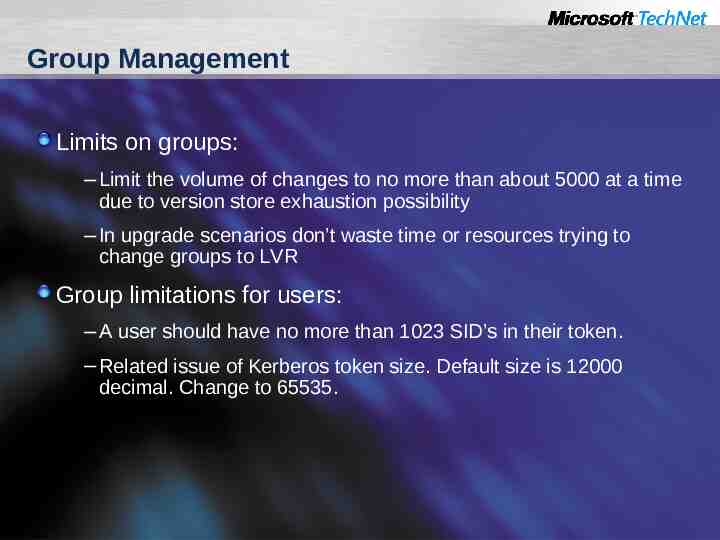
Group Management Limits on groups: – Limit the volume of changes to no more than about 5000 at a time due to version store exhaustion possibility – In upgrade scenarios don’t waste time or resources trying to change groups to LVR Group limitations for users: – A user should have no more than 1023 SID’s in their token. – Related issue of Kerberos token size. Default size is 12000 decimal. Change to 65535.

Group Management (2) Administrative groups are important! – Membership is key. The smaller the member ship the better. – Consider using Group Policy Restricted Groups feature – Common to see groups such as Schema Admins empty and are only populated when schema changes are about to be made

Group Policy The prime way to manage an organisation. Over 1300 individual settings out of the box Will be extended over time with new releases of the client and server operating systems Can be extended by third parties as well as organisations for applications Can use the engine to extend existing settings to registry settings but bear in mind this will be preference mode.
Group Policy tips ‘n tricks (1) Limits. – No more than 999 GPOs can apply to any single object in AD. – Biggest performance hit will be the number of settings that are applied via Group Policy not necessarily the number of GPOs – WMI filters only apply to Windows Server 2003 and Windows XP machines Please remember that GPOs apply only to users and computers!
Group Policy tips ‘n tricks (2) Tips. – Depending on the number of GPOs consider removing adm files from SYSVOL – Block auto update of adm files – Use site based GPOs carefully – Use the published resources. We have masses of great content on Group Policy including whitepapers and webcasts. http://www.microsoft.com/windowsserver2003/technologies/ management/grouppolicy/default.mspx – http://www.microsoft.com/seminar/events/series/grouppolicy.mspx
Group Policy tips ‘n tricks (3) Tips. – Include GPOs in your naming standards – Use a normalised approach to developing GPOs and do not create monolithic GPOs – Note that by default cross forest processing of GPOs will not happen. Need to enable this through GPO “Allow Cross-Forest User Policy and Roaming User Profiles” setting – Ensure you have backups of all GPO’s – Define a process and strategy for deploying and maintaining GPOs
Group Policy tips ‘n tricks (4) Avoid: – Cross domain linked GPOs – Excessive use of loopback processing, block inheritance and no override. You will only make your life more complicated – Disabling the default GPOs – Creating “GPO” OU
Managing Group Policy GPMC is your friend! – Allows you to manage your GPOs in a much more manageable and intuitive way – Allows you to delegate viewing of GPOs without having to give viewers full control – Provides a visual presentation of location of GPOs, links and precedence. This last one especially is useful for understanding what may be going wrong or unexpectedly with your GPOs! – RSoP. Massive improvement over the old method of gpresult. It allows you to troubleshoot as well as perform GP modelling

Domain Security Policy Password policy: – Use complex passwords / passphrases – Specify max and min password ages – Minimum password length 7 Account lockout – Account lockout duration: 15 – 30 minutes – Reset account lockout counter: 15 – 30 minutes – Account lockout threshold: 10

Backup and restore Absolutely critical to your AD management. Needed for a number of scenarios: – Quicker deployment of DC’s – Recovery of accidentally deleted objects – Forest recovery Often overlooked especially the validation of the process Choice of tools – It should be noted that there are some products that have issues with AD specifically

Backup and restore (2) Choose your strategy – What exactly is it I am protecting / preparing for? – Do I need to back up all DC’s? – Which DC’s should I focus on? – Which DC’s should I never consider restoring? – How often am I going to back up? – How often will I validate the backups and test my restore procedures? Understand the difference between a restore and an authoritative restore
Tools Group Policy: – GPMC main Group Policy tool but is also supported by gpresult, gpupdate, gpinventory, gpmonitor, gpotool, dcgpofix, admx. – Third party tools come from Quest, NetIQ, Autoprof, Full Armor and Bindview AD – Dsquota, dsadd, dsacls, adsiedit, ldp, mpsreports, dsquery, dsget, dsrm, whoami
Forest recovery This is a significant topic in its own right! Scenarios: – A schema change / corruption that you want to roll back – Some fatal administrative error that has rendered the forest beyond economical salvage – A malicious administrator

Forest recovery (2) Good news – PSS worldwide have yet to be involved in a major forest recovery situation. We have been close a couple of times! Bad news – It is not necessarily a quick process – Not many people have actually tested and validated their forest recovery procedures – The forest recovery whitepaper will not be a complete solution for you. http://www.microsoft.com/downloads/details.aspx? FamilyID 3eda5a79-c99b-4df9-823c933feba08cfe&displaylang en
Forest recovery (3) Tools for forest recovery – There are third party tools out there such as Quest Recovery Manager which make compelling claims. – However, not all tools will be “fully supported” by Microsoft. http://support.microsoft.com/default.aspx?scid kb;en-us;296257
Forest recovery (4) Technical preparation strategies – Lag sites for replication – A number of customers use 2 lag sites or some combination of two lag sites – Also consider manual replication sites and Virtual Server as options – Be aware of the tombstone lifetime value
Forest recovery (5) Processes – Being prepared technically is one thing. You must also have defined processes and procedures for handling this scenario. – What are the decision points for phases in recovery. For example at what point do you abandon a lag site recovery option and go for full forest recovery? – Has the process been tested? Do the engineers know what they are doing? – What backup do you use? How do you verify the backup to use? – What is your plan if recovery fails? How easy is it to recreate the forest?

Securing domain controllers Physical: – DC’s must be physically secure – Out of sight and reach – Based on business requirements / fears / strategy. For example, are we centralising? Do we have applications that require local access to a DC for better performance? – Consider restricting floppy / removable media booting capabilities – Anti virus is a must but be conscious of the requirements
Securing DC’s (2) Logical: – Ensure that the default Domain Controller GPO is enabled and active – Ensure no extra / unnecessary services are running – Restrict physical console access make use of remote desktop – Consider using syskey to protect the DS – DSRM password strategy. Common or unique? Complex? Secured?

Managing FSMO’s The good news is that they are pretty much self managing! Key FSMO to watch is the PDC Emulator – This is typically far and away the busiest FSMO – Consider lowering srv priority rating to remove general authentication load Understand the FSMO roles and requirements – We have seen issues in segmented networks where FSMO’s are unreachable. For example the DNM is required by DC’s with DNS in Windows Server 2003 For larger environments plan for FSMO fail over – If necessary configure direct replication connection

Performance of the directory System Monitor is great for – Establishing baselines – Carrying out general perf measurements Server Performance Advisor (SPA)
Deploying domain controllers How do you deploy DC’s? – Typical approach these days is to image or script the base server build followed by either a manual or an automated dcpromo – Problems in the early days with large companies racking up DC’s in preparation for shipping out and then falling foul of tombstone lifetime Windows Server 2003 has 2 new options rapidly deploy DC’s. – IFM: This is especially useful in bandwidth constrained situations as well as those where the DIT is huge. – ADS: Most suited to a large data centre type operation but has uses in smaller organisations for deploying DC’s both in production and in test

Placement of DC’s DC’s should be placed in the Domain Controllers OU – Do not move them out of this tree – You can consider creating child OUs within the Domain Controllers although this is not a practice that is favoured by the product group – Although technically nothing should go wrong if you do move DC’s out of the default location there have been instances where things have gone very pear shaped indeed. – Create Sites at the beginning of AD deployment – Make sure DC is in the correct site – Ensure that site topology has been defined correctly
Delegating admin of DC’s First answer is Don’t! Bear in mind that DC’s hold the keys to your kingdom. All user accounts are located in the DS along with important information. What would the impact be in your organisation if these were compromised? Pragmatic approach: – Remember that any admin that has logon access to a DC must be as trusted as your Enterprise Admins – Be careful with the functions you delegate (this is a common reason companies want to create sub OUs inside or outside the domain controllers OU) – Delegation often means that you want to run additional services / applications on a DC. Our typical recommendation is not to. However that is not always possible or practical with smaller organisations.

2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.