Introduction to WS Authorization Brian P. Barrett CS 551 1
18 Slides812.50 KB

Introduction to WS Authorization Brian P. Barrett CS 551 1

Authorization WS-Authorization – Complete? Steps of Authorization Security Token Acquisition SAML Authorization in Firewall Map of Authorization Authorization in Code References CS 551 2

Where does Authorization fit in? Authorization is an aspect of security that falls in with other categories: Secure Conversation Federation Policy Trust Federation Privacy CS 551 Is this Authorized? 3

Security Authentication Determine identity of a person/object Authorization Determine what the person is allowed to do Integrity Ensure the data was not altered on its way to you Signature Validate the source of the data Confidentiality Limit the people allowed to view the data Privacy Make sure no one abuses your data Digital Rights Management Limit users from doing whatever they want CS 551 4

Authorization work with other services? If Authorization were to be on a layer working with other Services. It would work in conjunction with the Federation layer. WS-Federation CS 551 WS-Secure Conversation WS-Authorization 5

Authorization with other WS CS 551 6

CS 551 7

PMI or Privilege Management Infrastructure Privilege Management Infrastructure: Source of Authority (SOA) The topmost root of trust, sometimes also referred to as trust anchor Attribute Authority (AA) (also Privilege Allocator, Authoritative Entity) The issuer of an attribute certificate Certificate Holder / Privilege Holder The User or Subject of an Attribute Certificate CS 551 8

Security Token Authorized Requestor Issues a request. The Web Service Obtains security Token The Data and policies will be Web Service Trusts Validated for that Established. Request was Particular client Processed and response returned Auth and Trust are Validated. Service must find Data and policies that are authorized for the user. CS 551 9

SAML – Security Assertion Markup Language SAML’s purpose was to be a Security language that could be used as an industry standard for security. It uses XML digital signatures with XML encryption. The languages uses assertions made in the code that can convey information about authentication functions, and authorization decisions. CS 551 10

SAML Authorization Map CS 551 11
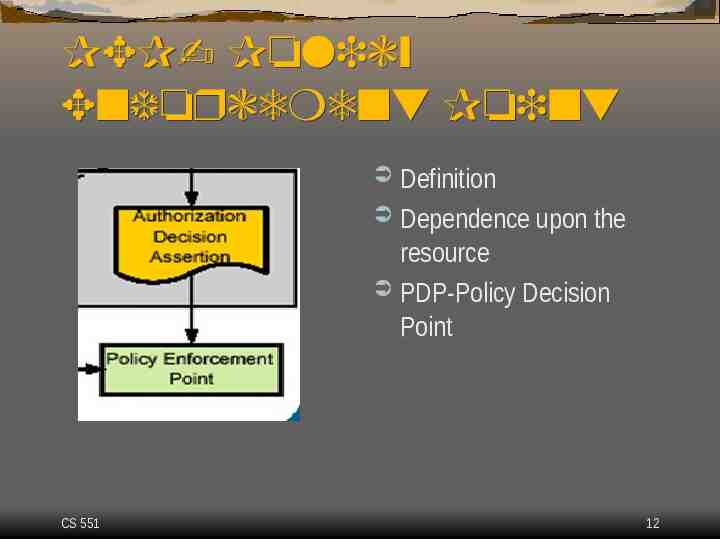
PEP- Policy Enforcement Point Definition Dependence upon the resource PDP-Policy Decision Point CS 551 12

Authorization in Firewall Processing Insurance Co. Claims officer/ Customer Web-Service CS 551 13

Authorization Process Map Client -Give server trust -Invocate policy -consult policy Server -Access Policy -Give client resource -Policy authority Authorization Process Role based Authorization Instance based Authorization Capability listings CS 551 14

How does the the Authorization code fit? CS 551 15

Authorization in code Show SAML code and explain. SAML doc Authorization decision: by subject S, for access type A, to resource R, given evidence E. CS 551 16

Code Example Rule RuleId "//medico.corules/rule3" Effect "Permit" Target Subjects saml:Attribute AttributeName "RFC822Name" AttributeNamespace "//medico.com" saml:AttributeValue * /saml:AttributeValue /saml:Attribute /Subjects Resources saml:Attribute AttributeName "documentURI" AttributeNamespace "//medico.com" saml:AttributeValue //medico.com/records.* /saml:AttributeValue /saml:Attribute /Resources Actions saml:Action read /saml:Action /Actions /Target Condition Equal AttributeDesignator AttributeName "urn:oasis:names:tc:xacml:identifiers:AccessSubject" / AttributeDesignator AttributeName "patientName" / /Equal /Condition /Rule CS 551 17

References Primary www.Globus.org – Globus is a resource to see the latest changes with WS-Authorization and other new standards. http://www.cs.huji.ac.il/course/2002/sdbi/ – If you go here and choose XML Security under Lecture slides you will find some detail about coding with SAML and its interaction for Authorization processes. Secondary http://msdn.microsoft.com/library/default.asp?url /library/en-us/dnwssecur/html/ securitywhitepaper.asp – Here you will fine some significant images that detail security over the web. http://www.lightshipinc.com/lightship/resourcecenter/Etips.aspx – At this site you can learn new technology dealing with XML, SAML and XMACL. CS 551 18