Ransomware Protection with NAKIVO Backup & Replication
38 Slides5.76 MB

Ransomware Protection with NAKIVO Backup & Replication

Partner of World’s Leading Technology Companies 2

The World’s Leading Brands Trust NAKIVO 3

What Is Ransomware?

What Is Ransomware? Ransomware is a type of malicious software that encrypts or locks a victim’s data to extort money. Hackers demand that companies pay a ransom through specific online payment methods, mostly Bitcoin, to regain access to their data or risk losing critical data forever. Paying the ransom does NOT guarantee regaining access to your data. 5
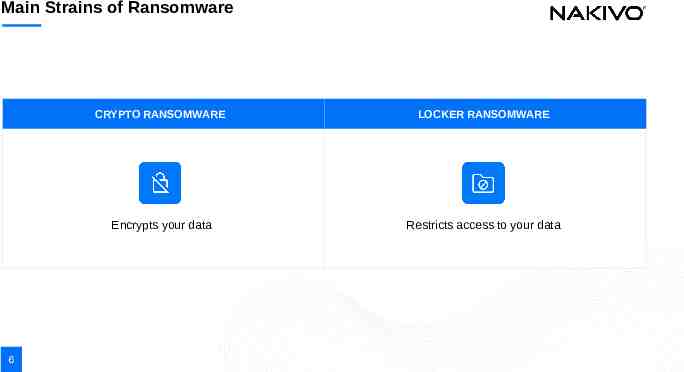
Main Strains of Ransomware 6 CRYPTO RANSOMWARE LOCKER RANSOMWARE Encrypts your data Restricts access to your data
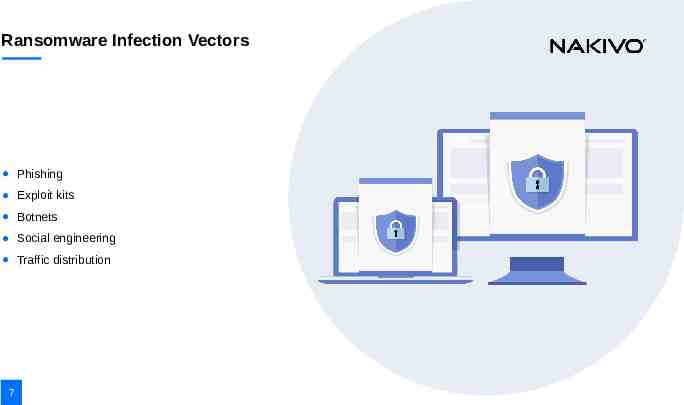
Ransomware Infection Vectors Phishing Exploit kits Botnets Social engineering Traffic distribution 7
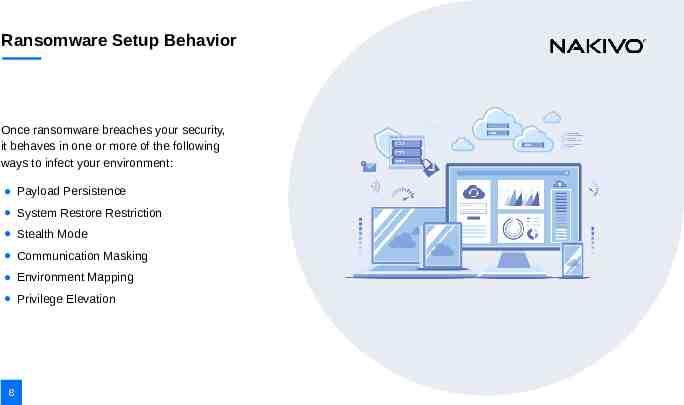
Ransomware Setup Behavior Once ransomware breaches your security, it behaves in one or more of the following ways to infect your environment: Payload Persistence System Restore Restriction Stealth Mode Communication Masking Environment Mapping Privilege Elevation 8
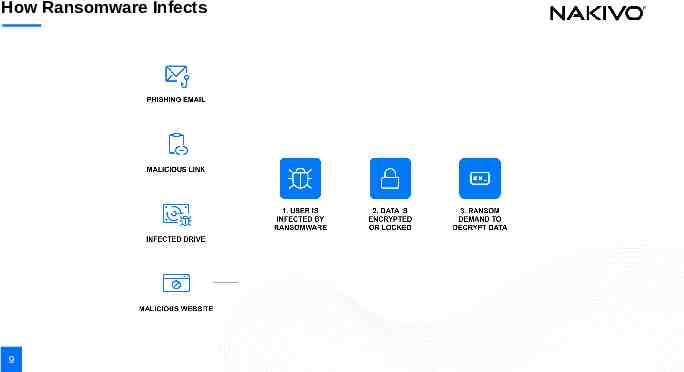
How Ransomware Infects 9

Ransomware Facts and Figures
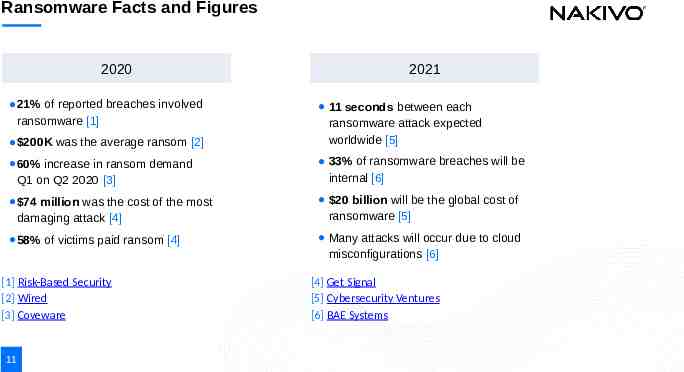
Ransomware Facts and Figures 2020 21% of reported breaches involved ransomware [1] 2021 200K was the average ransom [2] 11 seconds between each ransomware attack expected worldwide [5] 60% increase in ransom demand Q1 on Q2 2020 [3] 33% of ransomware breaches will be internal [6] 74 million was the cost of the most damaging attack [4] 20 billion will be the global cost of ransomware [5] 58% of victims paid ransom [4] Many attacks will occur due to cloud misconfigurations [6] [1] Risk-Based Security [2] Wired [3] Coveware 11 [4] Get Signal [5] Cybersecurity Ventures [6] BAE Systems
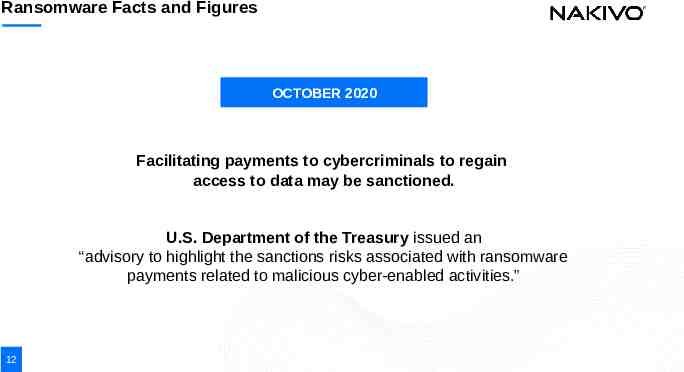
Ransomware Facts and Figures OCTOBER 2020 Facilitating payments to cybercriminals to regain access to data may be sanctioned. U.S. Department of the Treasury issued an “advisory to highlight the sanctions risks associated with ransomware payments related to malicious cyber-enabled activities.” 12

Ransomware Protection
Ransomware Protection If you don’t act ahead, it may be too late when ransomware strikes your business. A preventative, multi-layered approach to ransomware protection is vital to ensuring that you always have access to your data and systems. EDUCATE 14 SECURE PROTECT
Ransomware Protection EDUCATE Invest in security awareness training for your employees so they can identify and avoid clicking on potentially malicious links and phishing emails. 15
Ransomware Protection SECURE Install antivirus software that can quickly detect suspicious emails, links or unwanted malware, eliminate threats and effectively prevent them from gaining access to your systems. 16
Ransomware Protection PROTECT Back up your data regularly: Keep your backups separate from your production environment Follow the 3-2-1 backup rule Verify the functionality and recoverability of your backups 17

Ransomware Protection Best Practices

Ransomware Protection Best Practices Follow the 3-2-1 backup rule Use multiple backup targets Use replication for disaster recovery Create an effective retention policy Automate data protection workflows Control access to backup data Verify your backups and replicas 19
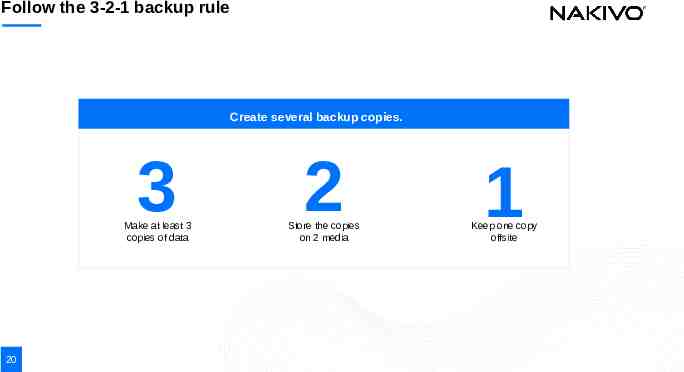
Follow the 3-2-1 backup rule Create several backup copies. 3 Make at least 3 copies of data 20 2 Store the copies on 2 media 1 Keep one copy offsite

Use multiple backup targets 21 COPY 1 COPY 2 COPY 3 Internal hard drive, external hard drive, optical disks, USB drive, etc. Network Attached Storage (NAS) or tape Offsite storage (NAS, tape, hard drives stored offsite) or a public cloud (Azure, Amazon S3, Amazon EC2 or Wasabi)
Use replication for disaster recovery Ensure business continuity by replicating your VM workloads to a secondary site for disaster recovery. 22
Create an effective retention policy Make sure you have enough recovery points for point-in-time restores while not letting storage capacity requirements get out of hand. 23
Control access to backup data Assign specific roles and permissions to IT staff to limit access to data protection activities and ensure that only authorized persons can modify jobs. 24
Verify backup/replica recoverability Test backups and replica to ensure that your machines run after recovery. 25

Ransomware Protection with NAKIVO Backup & Replication

NAKIVO Backup & Replication. Ransomware protection for virtual, physical, cloud and SaaS 27 Agentless, app-aware backup Perform agentless, app-aware, incremental backups Instant VM and granular recovery Instantly boot full VMs or restore files and application objects from VM backups Backup to Multiple Destinations Local files, cloud (Amazon S3, Wasabi, Azure), offsite, tape Ransomware-Proof Backups Immutable backups with Amazon S3 Object Lock Backup automation Set your data protection jobs to run automatically Performance optimization Smaller backups, LAN-free data transfer, global deduplication, and more. Backup/Replica verification Instantly confirm backups/replicas are successful and recoverable Site Recovery Disaster recovery orchestration and automation with non-disruptive testing

NAKIVO Backup & Replication. Comprehensive Backup Reliable backups for all your workloads Perform image-based, application-aware, incremental backup for virtual, physical, cloud, SaaS and mixed environments Create regular backups of your data as frequently as every minute Create up to 4,000 recovery points for each backup job and rotate them the grandfatherfather-son (GFS) retention scheme Ensure that applications and databases like Microsoft Exchange, Active Directory, Microsoft SQL, Oracle Database remain transactionally consistent 28
NAKIVO Backup & Replication. Backup Copy Offsite Effective implementation of the 3-2-1 backup rule Keep a copy of your backup data onsite to ensure fast access and recovery of your data when a ransomware attack hits Avoid having a single point of failure by sending your backup copies to tape or directly to a public cloud (like Amazon S3, Azure or Wasabi) Automate backup copies so that your primary backups and recovery points are automatically copied to a secondary location for rapid ransomware recovery 29

NAKIVO Backup & Replication. Ransomware-Proof Backups Ensure that your backups cannot be locked or encrypted by ransomware Use the S3 Object Lock functionality to make your backups and backup copies stored in Amazon S3 buckets immutable to prevent them from being deleted, altered, or encrypted Define backup administrative roles according to the principle of least privilege with rolebased access control Encrypt your data in flight and at rest using AES-256 encryption to prevent unauthorized third-party access 30
NAKIVO Backup & Replication. Multiple Recovery Options Instantly recover what you need Instantly restore any file, folder or application object to its original or custom location Resume business operations in minutes by booting virtual machines directly from deduplicated backups Immediately recover items of any application by mounting disks from a backup directly Recover backup data across platforms Boot physical machines directly from physical machine backups as VMware vSphere VMs 31
NAKIVO Backup & Replication. Validated Backups/Replicas Ensure your backups and replicas can be used for recovery Automatically test the validity and integrity of backups and replicas upon each job completion Validate backup copies in a sandboxed environment to identify and resolve any vulnerabilities Instantly verify VM replicas and get a report with screenshots of test-recovered machines View the verification results in the solution’s interface or via email 32
NAKIVO Backup & Replication. Replication for Continuous Availability Provide a high degree of availability for mission-critical data Create and maintain replicas of your source VMs on a target host in a secondary location Ensure near-instant recovery with identical copies of your source VMs Replicate VMs directly from backups to reduce the load on the host server and save time Power on the replicas (failover) and have your VMs up and running in no time 33
NAKIVO Backup & Replication. Automated Disaster Recovery Ensure continuous availability in any failure scenario Use the Site Recovery functionality to create workflows of any complexity and quickly restore your operations at a disaster recovery location Streamline and automate disaster recovery with unique failover to replicas and failback scenarios Perform non-disruptive test recoveries for guaranteed disaster recovery 34

Why Choose NAKIVO

Why Choose NAKIVO All-in-One Solution for backup, replication, instant granular restore, site recovery Supports Virtual, Physical, Cloud and SaaS VMware vSphere, Microsoft Hyper-V, Nutanix, Amazon EC2, Windows, Linux, Microsoft 365, Oracle Database Can Be Deployed Anywhere NAS, Linux, Windows, VA, AMI Reduces Administration Time Just set it and forget it Light on Your Budget with affordable prices Extensive Data Protection Feature Set for businesses of all sizes Friendly web user interface Industry leading 24/7 support 36

Integration with NAS devices Runs on QNAP, FreeNAS, NetGEAR, Asustor, Western Digital and Synology 5-in-1 backup appliance 37 Up to 2x faster backups Reduce load on production environment
Want to Learn More? If you want learn more about using NAKIVO Backup & Replication for ransomware protection and recovery, schedule a demo with a NAKIVO expert who can show you the solution in action and answer your questions.