Internal Firewall Design By, Ketan Reddy Peddabachi
21 Slides308.50 KB

Internal Firewall Design By, Ketan Reddy Peddabachi Instructor:Dr.Ravi Mukkamala 06/24/23 10:40 Internal Firewall Design 1
CONTENT Introduction Architecture Requirements Categories of Firewalls Firewall Features Implementing a Firewall Conclusion 06/24/23 10:40 Internal Firewall Design 2

Introduction What is a Firewall? A system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Why a Firewall? Tackle Intrusions Defend internal servers from network attacks Monitor traffic and generate alerts when suspicious patterns detected. 06/24/23 10:40 Internal Firewall Design 3
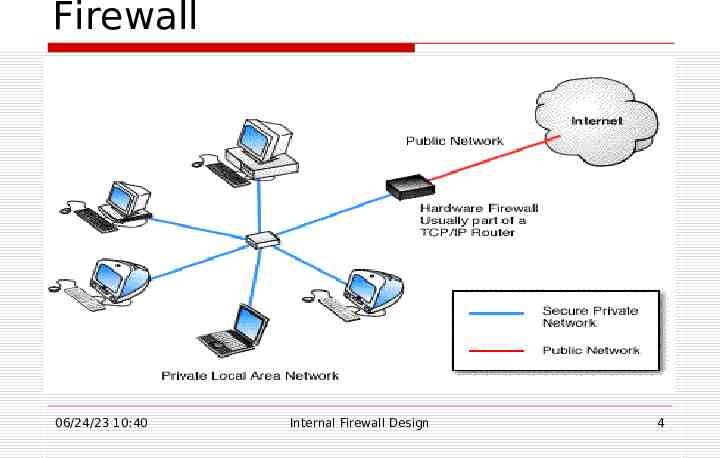
Firewall 06/24/23 10:40 Internal Firewall Design 4

What does a Firewall do? A firewall filters both inbound and outbound traffic. It can be used to log all attempts to enter the private network and trigger alarms when hostile or unauthorized entry is attempted. Firewalls can filter packets based on their source and destination addresses and port numbers. This is known as Address Filtering. Firewalls can also filter specific types of network traffic. This is also known as Protocol Filtering 06/24/23 10:40 Internal Firewall Design 5
Architecture Border Network Perimeter Network Internal Network 06/24/23 10:40 Internal Firewall Design 6
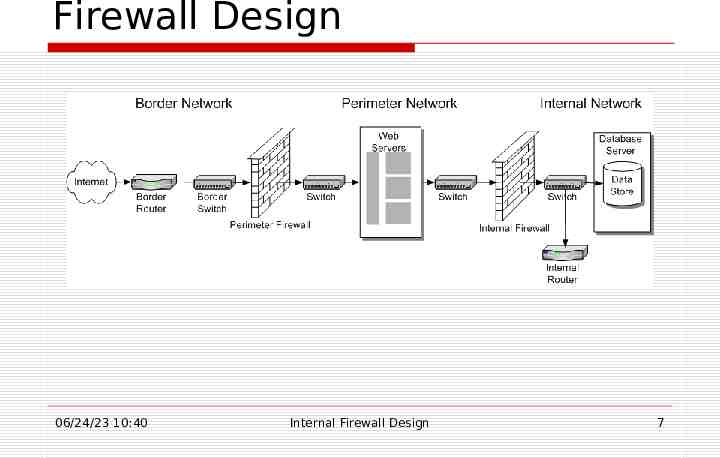
Firewall Design 06/24/23 10:40 Internal Firewall Design 7

Requirements Budget Existing Facilities Availability Scalability Features required 06/24/23 10:40 Internal Firewall Design 8
Categories of Firewalls There are 4 broad types/categories of firewall techniques: Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible to IP spoofing. Application gateway: Applies security mechanisms to specific applications, such as FTP and Telnet servers. This is very effective, but can impose a performance degradation. 06/24/23 10:40 Internal Firewall Design 9

Contd. Circuit-level gateway: Applies security mechanisms when a TCP or UDP connection is established. Once the connection has been made, packets can flow between the hosts without further checking. Proxy server: Intercepts all messages entering and leaving the network. The proxy server effectively hides the true network addresses. 06/24/23 10:40 Internal Firewall Design 10
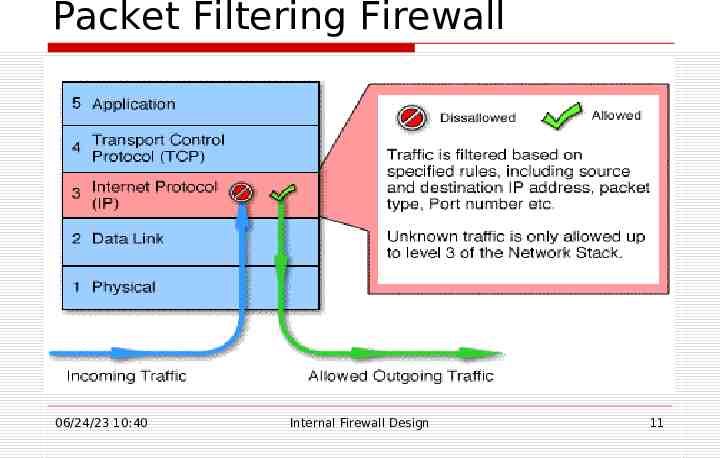
Packet Filtering Firewall 06/24/23 10:40 Internal Firewall Design 11
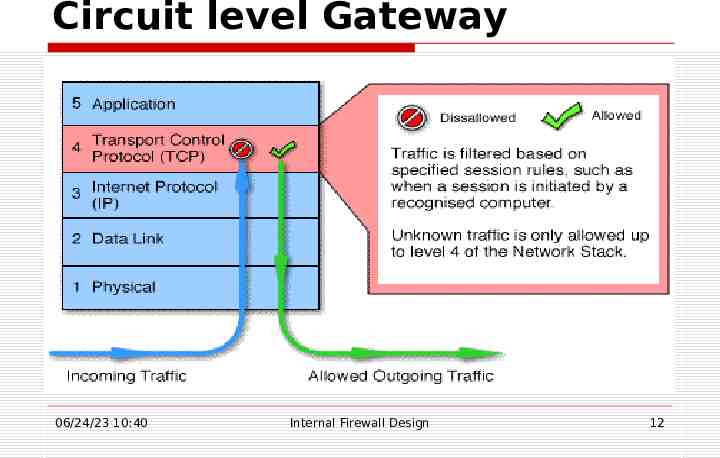
Circuit level Gateway 06/24/23 10:40 Internal Firewall Design 12
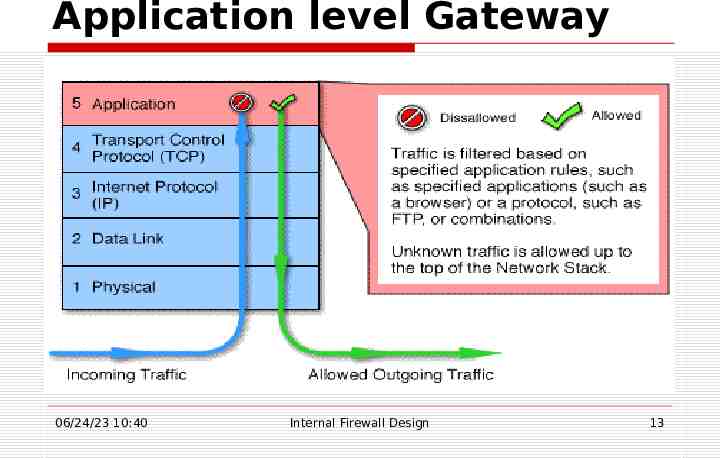
Application level Gateway 06/24/23 10:40 Internal Firewall Design 13
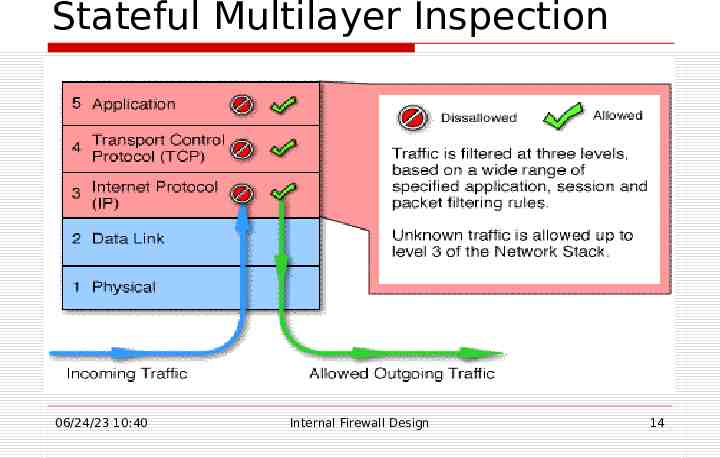
Stateful Multilayer Inspection 06/24/23 10:40 Internal Firewall Design 14

Customize Firewall IP Adresses Domain names Protocols Ports Specific words and phrases 06/24/23 10:40 Internal Firewall Design 15
Firewall behavior At various levels of the TCP/IP Stack N/w-Layer: At this layer a firewall can determine whether a packet is from a trusted source, but cannot be concerned with what it contains or what other packets it is associated with. Transport Layer: Firewalls that operate at the transport layer know a little more about a packet, and are able to grant or deny access depending on more sophisticated criteria. Application Layer: At the application level, firewalls know a great deal about what is going on and can be very selective in granting access. 06/24/23 10:40 Internal Firewall Design 16

Why a Antivirus then? Firewall –not good against a data driven attack-mail, file transfer etc. To Perform less trivial tasks on individual systems. 06/24/23 10:40 Internal Firewall Design 17

How to implement a firewall? Determine the access denial methodology to use. Determine inbound access policy. Determine outbound access policy. 06/24/23 10:40 Internal Firewall Design 18

Contd. Determine if dial-in or dial-out access is required. Decide whether to buy a complete firewall product, have one implemented by a systems integrator or implement one yourself. 06/24/23 10:40 Internal Firewall Design 19

Conclusion Firewall-integral part of any security program, but it is not a security program in and of itself. An organization should consider a well planned and strictly implemented security program that includes but is not limited to firewall protection. 06/24/23 10:40 Internal Firewall Design 20
References http://www.vicomsoft.com/knowledge/ reference/firewalls1.html#Figure5 http://www.howstuffworks.com/firewal l.htm http://www.microsoft.com/technet/sec urity/guidance/networksecurity/secmo d155.mspx 06/24/23 10:40 Internal Firewall Design 21