Information Security Forum From an ISO17799 Audit to an Information
15 Slides748.00 KB

Information Security Forum From an ISO17799 Audit to an Information Security Plan (the 100 day plans - part 2) By Jim Reiner Sacramento County July 31, 2007

The end-goal: a formal information security program Governance Security Committee & Professionals Employee Training Security Controls Information Classification Monitoring & Auditing Policy and Procedures Business Continuity & Disaster Planning Information Risk Management

My focus as the Information Security Officer: Articulate the overall strategy 1st 100 days Oct-Jan Survey managers & staff Set a goal and a strategy Select a security audit checklist 2nd 100 days Jan-April ISO 17799 info security audit Update security intranet site ID who does what relative to security My Approach: Staging 100 day plans for an immediate focus while achieving longer term objectives. 3rd 100 days 4th 100 days May-August Aug-Nov 1. Select 1. Publish performance updated metrics policies Build a 2. Budget for the security Security business plan Program Manage the 3. Put in place security security training program

www.ocit.saccounty.net/InformationSecurity/index.htm

Audit IS Plan IS Pgm

We used the ISO 17799 Checklist Information Security Management Audit Check List http://www.sans.org/score/checklists/ISO 17799 checklist.pdf Governance Information Security Professionals Employee Security Training Audit Security Controls Information Classification Monitoring & Auditing Policies, Standards, and Procedures Business Continuity & Disaster Planning Information Risk Management

ISO 17799 Audit Initial Results 10 audit topics – 127 individual items 32 57 Compliant Don't Know Gap/Weakness 38

Audit Final Results 77 21 High Risk Compliant Don't Know Gap/Weakness 50

Organizing the initiatives Administrative Technical Physical

IS Plan 1 of 4

High Low Value – Risk Mitigation IS Pgm Low High Level of Effort – Impact on OCIT

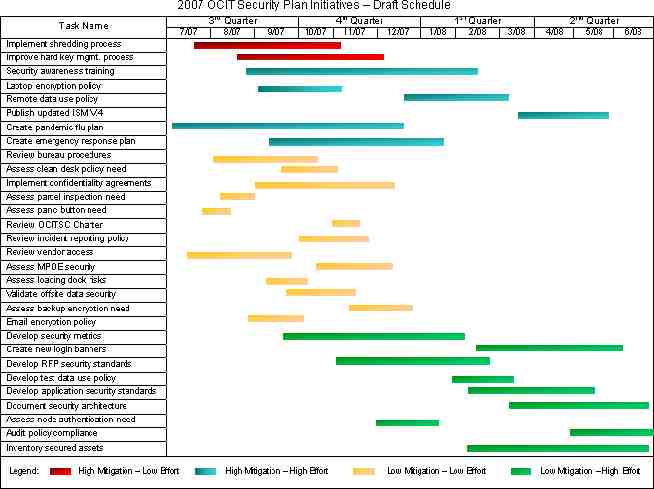
High Laptop encryption Shredding Emergency response plan Hard key mgmt Loading dock OCITSC charter E-mail encryption Incident MPOE security Low Value – Risk Mitigation Ratings of 2007 OCIT Security Plan Initiatives List reporting Bureau procedures Security awareness ISM V.4 DR plans Pandemic flu plan RFP Test Security standards data metrics Application OCIT Network security Access Ctl compliance Security architecture Vendor access Confidentiality Panic Offsite agreements button data Parcel Backup inspection Clean desks encryption Low Remote data access Level of Effort – Impact on OCIT Login banners Asset inventory High Completed In progress Not started
Network Vulnerability Assessment and Mitigation A CASE STUDY

www.ocit.saccounty.net/InformationSecurity/index.htm







