Information Assurance Update: Cloud, Trusted Internet Connections
37 Slides3.42 MB

Information Assurance Update: Cloud, Trusted Internet Connections and Continuous Monitoring Steven Hernandez Chief Information Security Officer HHS/OIG September 4th 2014 LIMITED OFFICIAL USE ONLY DHHS/OIG

Agenda Introduction Overview of terminology and concepts – – – Cloud Continuous Monitoring and “CDM” Trusted Internet Connections Cloud assurance overview Cloud Assessment Continuous Monitoring Challenges in the Cloud Trusted Internet Challenges in the Cloud Moving forward with best recommendations Questions 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 2

Introduction Who I am: Steven Hernandez MBA, CISSP, CISA, CSSLP, CAP, SSCP, CNSS(4011-4016), HCISPP – Director of the HHS/OIG Information Assurance Division – Chief Information Security Officer 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 3

What is Cloud? Possibilities: – Software as a Service (SaaS) Vendor is responsible for the vast majority of security control implementation and operation. – Platform as a Service (PaaS) Vendor is responsible for typically the operating system and hardware security controls. – Infrastructure as a Service (IaaS) Customer is responsible for the Majority of 02/11/2024 USE ONLY Contols. LIMITED OFFICIAL DHHS/OIG 4
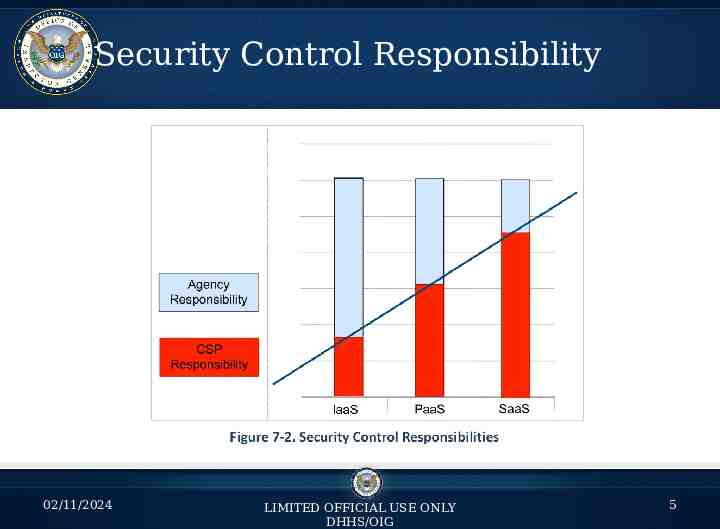
Security Control Responsibility 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 5
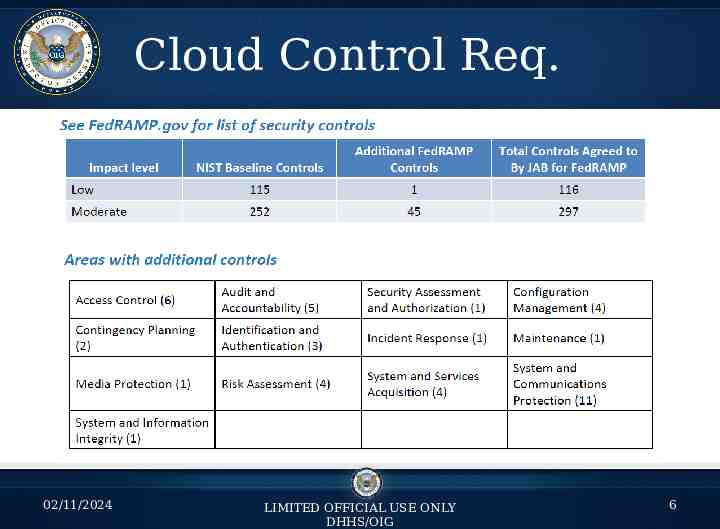
Cloud Control Req. 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 6

Additional Responsibility Agency Responsibilities 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 7

Agency Responsibilities Agency Responsibilities 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 8

Cloud Authorization 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 9

Minimum Cloud Assurance Evidence 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 10

Document Examples Templates (Fedramp) – http://cloud.cio.gov/fedramp/templates Package Request Form Security Assessment Frame work Guide to Understanding FedRAMP FedRAMP Revision 4 Transition Guid e Quick Guide to FedRAMP Readiness Process FedRAMP Policy Memo Security Controls Control Quick Guide 02/11/2024 Standard Contract Clauses Control Specific Contract Cla uses Cloud Procurement Best Prac tices Template FedRAMP ATO Letter JAB Charter Continuous Monitoring Strate gy Guide Significant Change Form Incident Communications Pro cedure Branding Guidance LIMITED OFFICIAL USE ONLY DHHS/OIG 11

Submission of Cloud to GSA 1. CSP contracts with an accredited 3PAO and submits a 3PAO Designation Form to the FedRAMP PMO. 2. FedRAMP ISSO holds a meeting with CSP and 3PAO to discuss expectations and set timeframes for deliverables. 3. 3PAO creates and the FedRAMP ISSO approves a testing plan that ensures the assessment will cover the state authorization boundary and controls. 4. 3PAO performs and independently tests the CSP's system and generates a Security Assessment Report (SAR) that documents findings and provides and analysis of the test results to determine the risk exposure. 5. CSP develops a Plan of Action & Milestones (POA&M) that addresses the specific tasks, resources, and schedule for correcting each of the weaknesses and residual risks identified. 6. CSP submits the SAR and POA&M to the FedRAMP ISSO for a completeness and overall risk posture review. 7. The Joint Authorization Board (JAB) makes a risk-based decision on whether to accept the vulnerabilities and planned fixes. 8. If JAB determines the risk level is too high it recommends remediation steps that the FedRAMP ISSO shares with the CSP. 9. CSP corrects control implementations, retests affected controls, and resubmits revised documentation 02/11/2024 12 LIMITED USEthe ONLY 10. If JAB accepts the risks associated withOFFICIAL the system, FedRAMP ISSO notifies the CSP DHHS/OIG

Submission of Cloud to GSA 1.GSA is VERY backlogged right now! 1.This is good: Cloud providers are heading the warning and complying with Fedramp 2.This is bad: Cloud providers will not have JAB provisional authorizations in a timely manner 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 13

Continuous Monitoring Continuous Monitoring has always been part of the NIST Risk Management Framework (RMF!) Continuous monitoring has always been part of the certification and accreditation/authorization process. Why does Certification/Assessment and Authorization matter? – – – – Understanding the risk you take when using a system Understanding the limitations and strengths of a system Having a level of assurance and due diligence for a system Continuously monitor a system for vulnerabilities and resulting risk – It’s the Law! FISMA requires we do this and for good reason! 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 14

C&A Introduction Why does Certification/Assessment and Authorization matter? – Understanding the risk you take when using a system – Understanding the limitations and strengths of a system – Having a level of assurance and due diligence for a system – Continuously monitor a system for vulnerabilities and resulting risk – It’s the Law! FISMA requires we do this and for good reason! 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 15
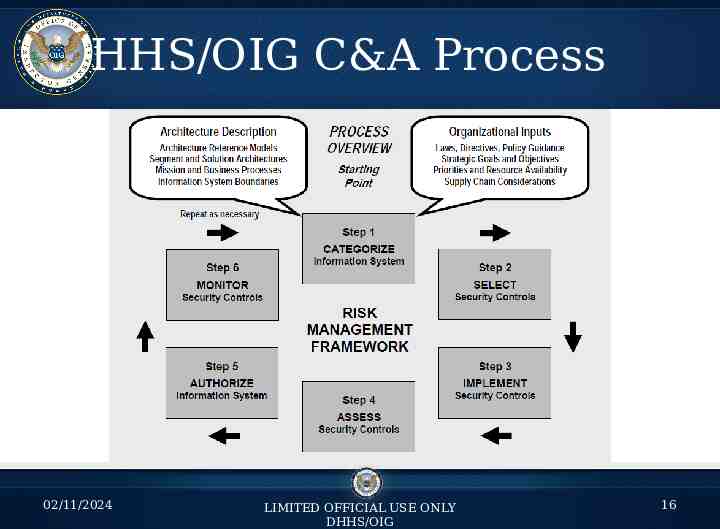
HHS/OIG C&A Process 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 16

DHS CDM DHS’ Continuous Diagnostics and Mitigation – A subset of continuous monitoring – NOT complete or holistic security approach – Works in coordination and compliments existing continuous monitoring 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 17

DHS CDM 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 18

DHS CDM First, agencies install and/or update their diagnostic sensors and the agency-installed sensors begin performing automated searches for known cyber flaws. Results are fed into enterprise-level dashboards that produce customized reports, alerting IT managers to the most critical cyber risks, enabling them to readily identify which network security issues to address first, thus enhancing the overall security posture of agency networks. Progress reports that track results can be shared within and among agencies. Summary information can feed into an enterprise-level dashboard to inform and prioritize ongoing cyber risk assessments. 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 19
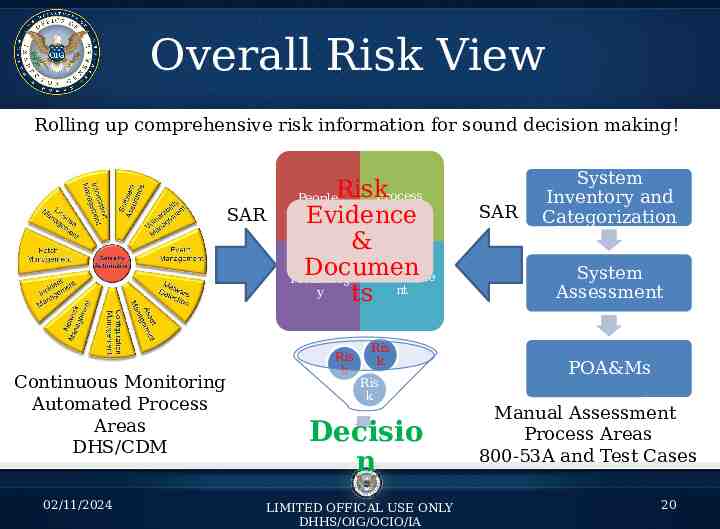
Overall Risk View Rolling up comprehensive risk information for sound decision making! SAR Continuous Monitoring Automated Process Areas DHS/CDM 02/11/2024 Process PeopleRisk Evidence & Documen Technolog Environme y ts nt Ris k Ris k Ris k Decisio n LIMITED OFFICAL USE ONLY DHHS/OIG/OCIO/IA SAR System Inventory and Categorization System Assessment POA&Ms Manual Assessment Process Areas 800-53A and Test Cases 20
Cloud Continuous Monitoring When the vendor controls everything how can we ensure risk visibility? Remember: – FedRamp is going to ensure the CM capability exists for the cloud provider in three areas: Operational Visability Change Management Incidence Response 02/11/2024 LIMITED OFFICAL USE ONLY DHHS/OIG/OCIO/IA 21
Cloud Continuous Monitoring Operational Visibility: Operational visibility provides a look-in into the security control implementations of the CSP – What contract language or clauses does the organization have for ongoing and as needed (ad hoc) security assessments? – How much visibility through automated or manual assessments does the organization have into the cloud provider. Change Control and Management: How does the cloud provider control changes and configurations? What assurance does the organization and agency have that breaches or downtime will not occur due to unintended changes or poorly tested changes? 02/11/2024 LIMITED OFFICAL USE ONLY DHHS/OIG/OCIO/IA 22

Cloud Continuous Monitoring Incident Response and Law Enforcement – What automated scanning, patching and reporting is available to the agency? – Is the cloud provider using SCAP compliant tools and providing DHS compliant feeds back to the agency? – What contractual provisions are in place for internal investigations, employee monitoring and formal investigations? 02/11/2024 LIMITED OFFICAL USE ONLY DHHS/OIG/OCIO/IA 23

Cloud Continuous Monitoring Recommendations: – Ensure contractual provisions exist which ensure the cloud provider must provide SCAP compliant configuration, asset, vulnerability and patch status for DHS CDM dashboards and feeds. – Ensure contracts are vetted by law enforcement partners and Legal to ensure all legal actions are routed to the appropriate agency resources and when the agency needs information from the cloud provider there are no surprises. – Ensure you have the ability to send in an independent assessment team to perform ad hoc or after action assessments. – Ensure a full FedRamp provisional ATO is required for new contracts and consider recompeting existing contracts which do not contain the FedRamp requirements. 02/11/2024 LIMITED OFFICAL USE ONLY DHHS/OIG/OCIO/IA 24
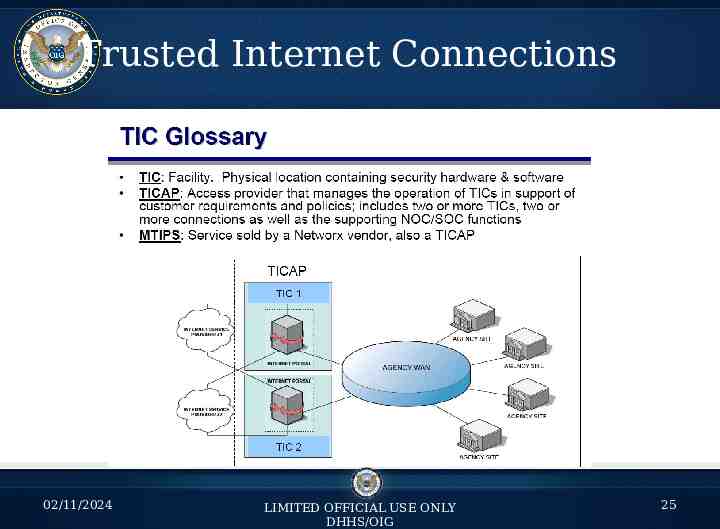
Trusted Internet Connections 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 25

Trusted Internet Connections Required through: 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 26
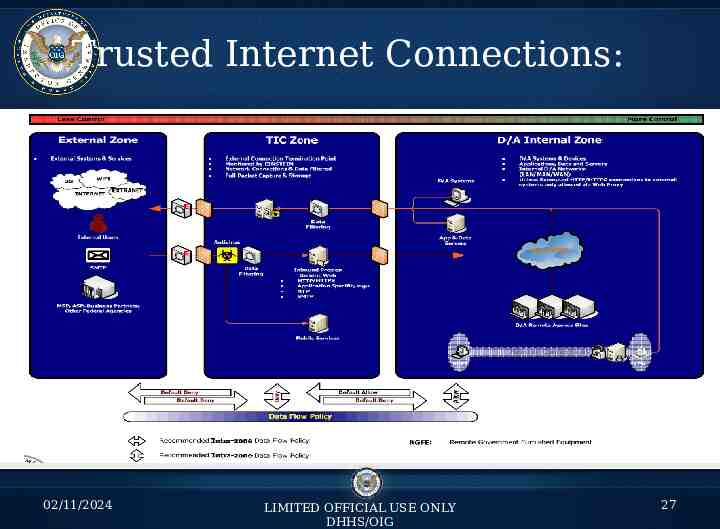
Trusted Internet Connections: 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 27
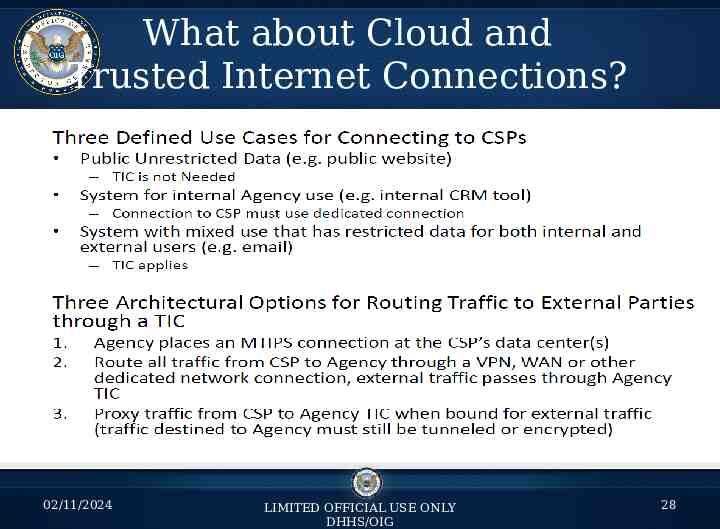
What about Cloud and Trusted Internet Connections? 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 28
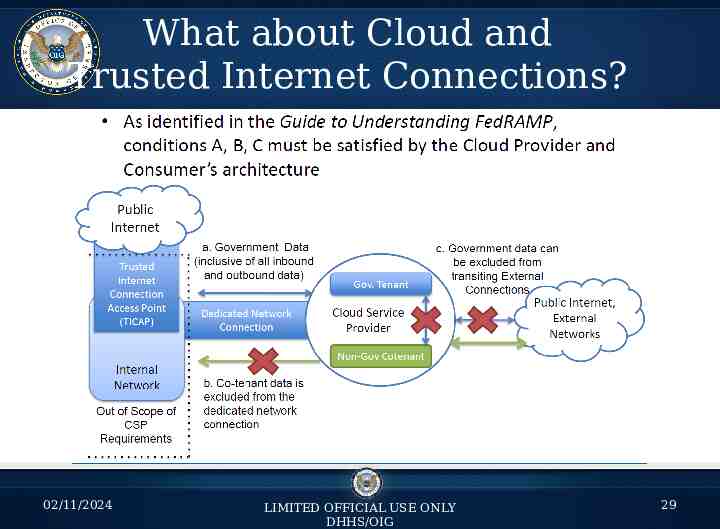
What about Cloud and Trusted Internet Connections? 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 29
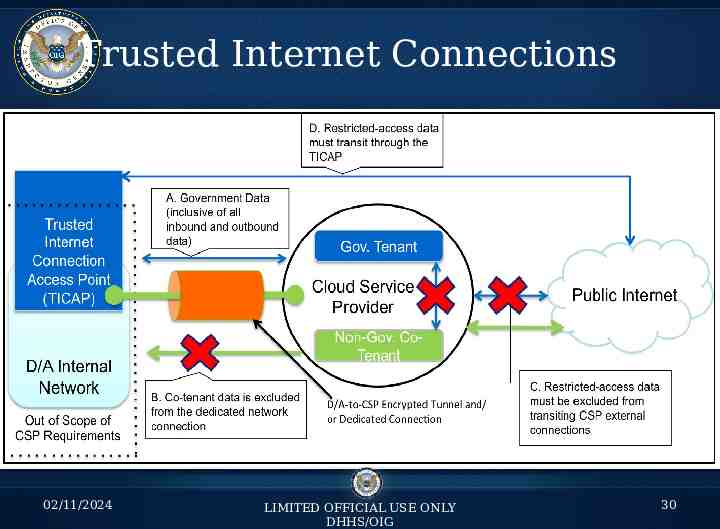
Trusted Internet Connections 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 30

What have we learned from vendors? 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 31
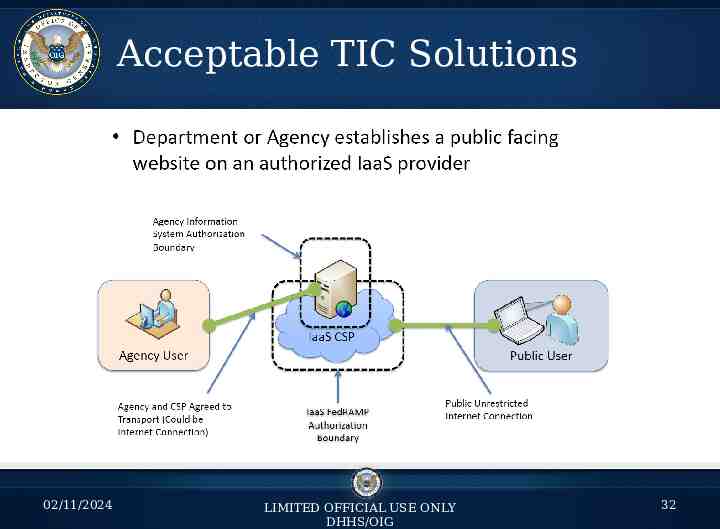
Acceptable TIC Solutions 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 32
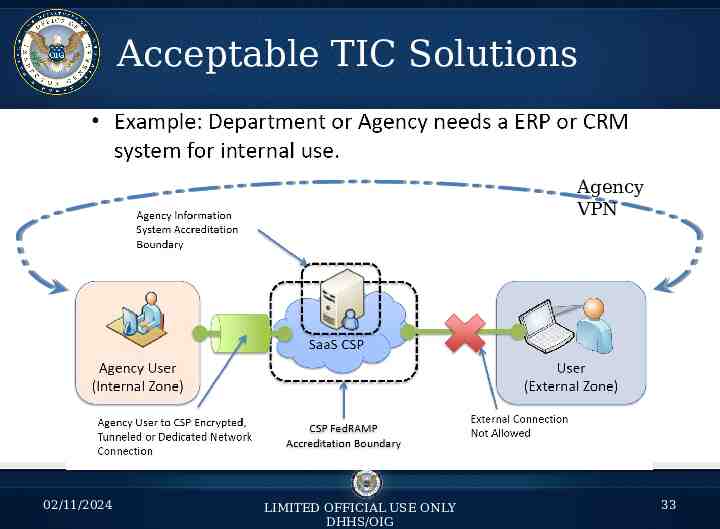
Acceptable TIC Solutions Agency VPN 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 33
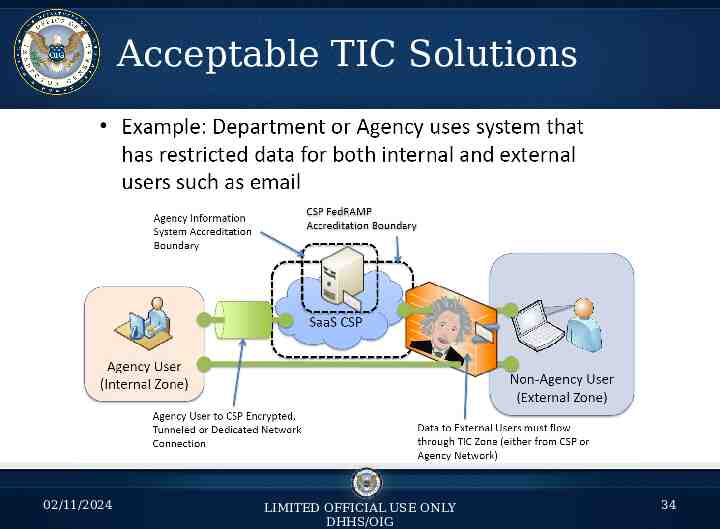
Acceptable TIC Solutions 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 34

Critical issues between vendors and agencies? 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 35

Questions 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 36

Thanks!! Contact Me: Steven Hernandez [email protected] ov 02/11/2024 LIMITED OFFICIAL USE ONLY DHHS/OIG 37






