Good Cyber Hygiene Habits Alex Boyd POLSINELLI PC
32 Slides983.62 KB

Good Cyber Hygiene Habits Alex Boyd POLSINELLI PC [email protected] August 15, 2019
Agenda Expanding reach of cyber Cybersecurity trends and legal implications Learning from common data security scenarios Ways to protect yourself and your organization

What is Cyber Hygiene and Why Does it Matter? Practices to protect yourself, your organization, and your data Financial fraud and identity theft Legal compliance Business operations Reputation and trust

Expanding Scope of Cyber At work At home or while traveling Types of data Your own personal information Employee personal information Business data Customer data
Data Privacy and Cyber Security Data privacy What information is collected How that information is used To whom that information is disclosed Cybersecurity Policies and procedures designed to avoid the loss or unauthorized disclosure of collected information
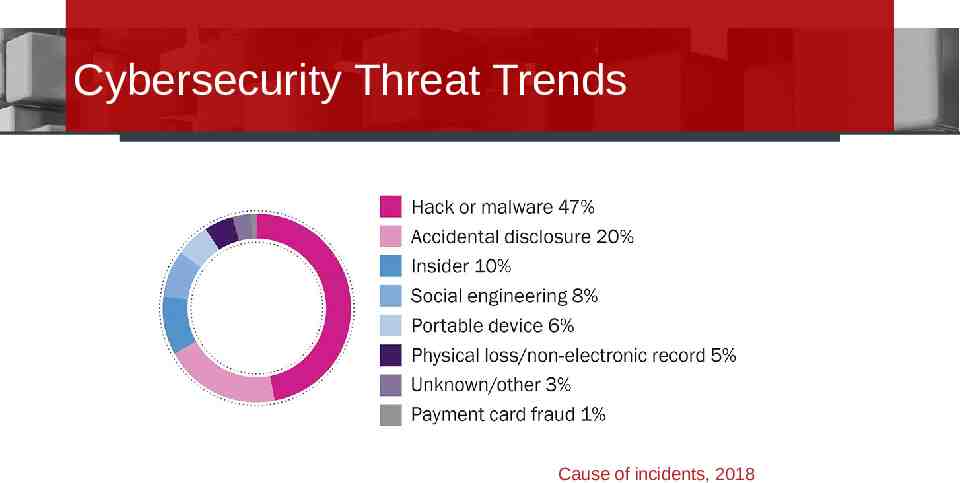
Cybersecurity Threat Trends Cause of incidents, 2018
Email Compromise: Motivation for Threat Actors Wire transfers (lead to losses due to fraudulent wire and lawsuits) Reconnaissance/targeted spam Payroll redirect Access sensitive information in the inbox

Ransomware & Cyber Extortion Ransomware Business disruption Loss of customers Often deployed after unauthorized access Potential breach notification obligations True Extortion Theft or Destruction of Digital Assets Demand for payment

Potential Legal Obligations Legal obligations arising from the unauthorized access of personal information Statutory data breach notification obligations to individuals, regulators and business partners State or federal law This may include notification to investors, key customers, unfriendly parties (e.g., litigation adversaries) Contractual obligations to third parties
Data Breach Response Have you mitigated the security risk? Was “personal information” involved in a “security breach?” Do you need to notify impacted persons? Do you need to notify state regulators? Do you need to notify any federal regulators?
Learning from Common Scenarios How should you respond if the incident occurs? How could the incident have been prevented? How could the impact have been minimized?
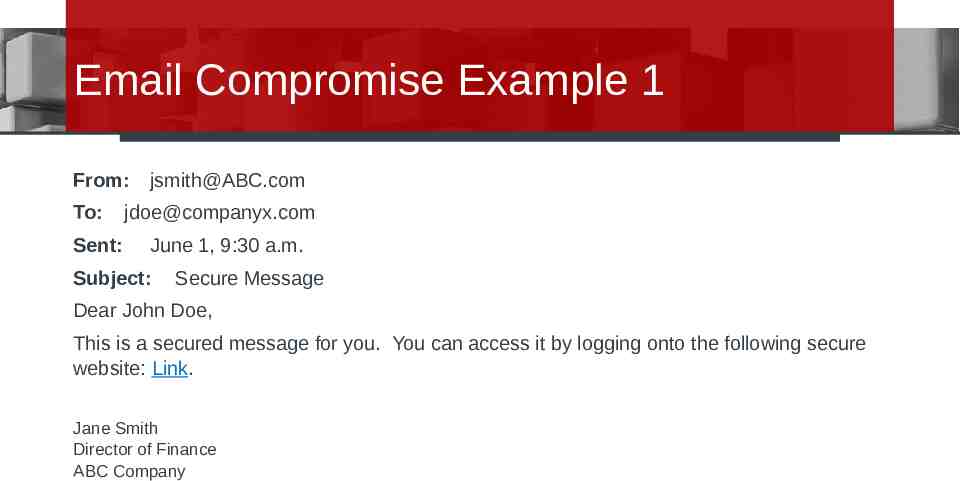
Email Compromise Example 1 From: To: Sent: [email protected] [email protected] June 1, 9:30 a.m. Subject: Secure Message Dear John Doe, This is a secured message for you. You can access it by logging onto the following secure website: Link. Jane Smith Director of Finance ABC Company
Email Compromise Example 1 (Contact) No compromise at your company, yet. Don’t click the link, enter any passwords, or open any attachments. Was the sender from a known contact? Were you expecting this email?
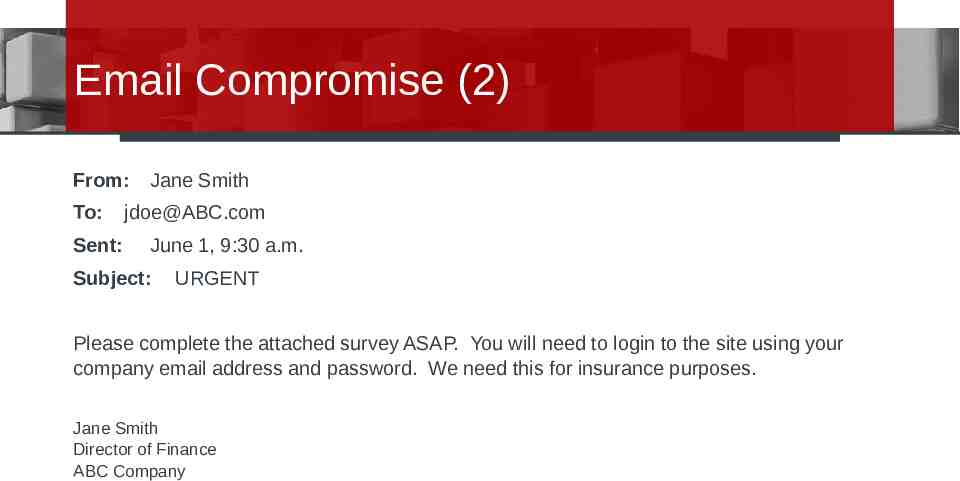
Email Compromise (2) From: To: Sent: Jane Smith [email protected] June 1, 9:30 a.m. Subject: URGENT Please complete the attached survey ASAP. You will need to login to the site using your company email address and password. We need this for insurance purposes. Jane Smith Director of Finance ABC Company
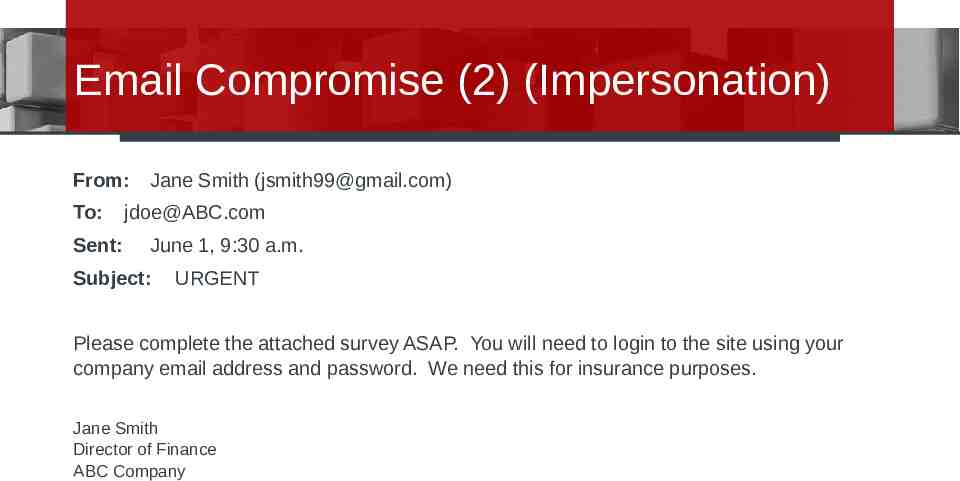
Email Compromise (2) (Impersonation) From: To: Sent: Jane Smith ([email protected]) [email protected] June 1, 9:30 a.m. Subject: URGENT Please complete the attached survey ASAP. You will need to login to the site using your company email address and password. We need this for insurance purposes. Jane Smith Director of Finance ABC Company
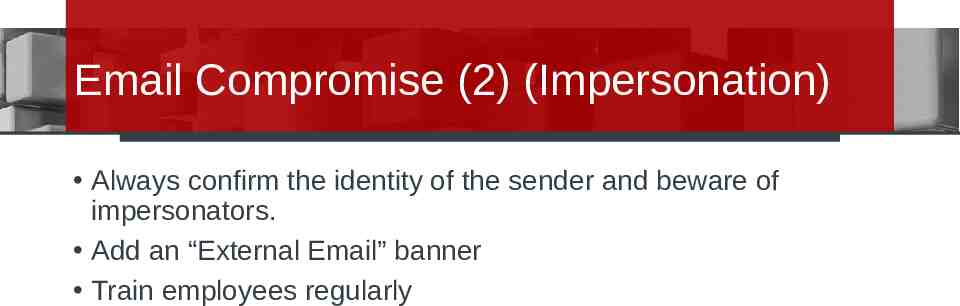
Email Compromise (2) (Impersonation) Always confirm the identity of the sender and beware of impersonators. Add an “External Email” banner Train employees regularly
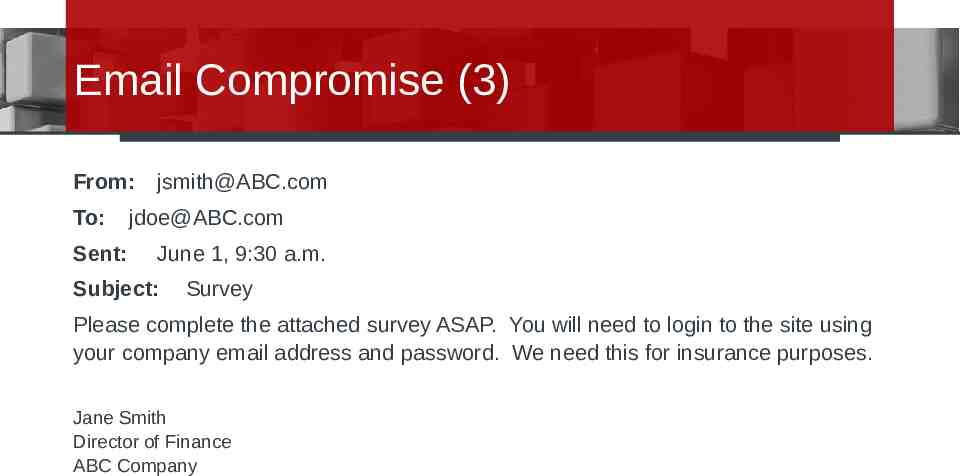
Email Compromise (3) From: To: Sent: [email protected] [email protected] June 1, 9:30 a.m. Subject: Survey Please complete the attached survey ASAP. You will need to login to the site using your company email address and password. We need this for insurance purposes. Jane Smith Director of Finance ABC Company
Email Compromise (3) (Active Compromise) Now we know we have a problem. Additional facts learned upon investigation: Employee clicked a link in a phishing email and entered their username and password for their work email account. Threat actor accessed the account Searched for emails with wire instructions for outstanding invoices and emailed the customer with changes to the instructions. Established rules that deleted incoming emails from that customer. Established forwarding rules to send emails to an external account. Later sent further phishing emails to contacts inside and outside the organization. Several employees clicked on the links and entered credentials, including employees who routinely send spreadsheets containing employee information.

Email Compromise (3) (Active Compromise) How should you respond if the incident occurs? Follow your incident response plan Remediation Password changes Remove rules Detect any fraudulent wire transfers Investigation Determine if any personal information may have been accessed or acquired Notification Comply with any applicable notification requirements Notify customers or contacts who may be at risk Prevention Mitigate the risk that led to the compromise
Email Compromise (3) (Active Compromise) How could the incident have been prevented? Methods to prevent the first compromise External banner Training Multifactor authentication Blocking certain foreign IP addresses or unapproved IP addresses

Email Compromise (3) (Active Compromise) How could the impact have been minimized? Earlier detection Alerts when rules are created Alerts regarding suspicious logins from unknown IP addresses Regular password changes (and rule removals) Reduce or eliminate personal information from email accounts Do not send actual copies of sensitive records. Send through hyperlinks to internal documents or through links to secure file transfer sites Delete older emails
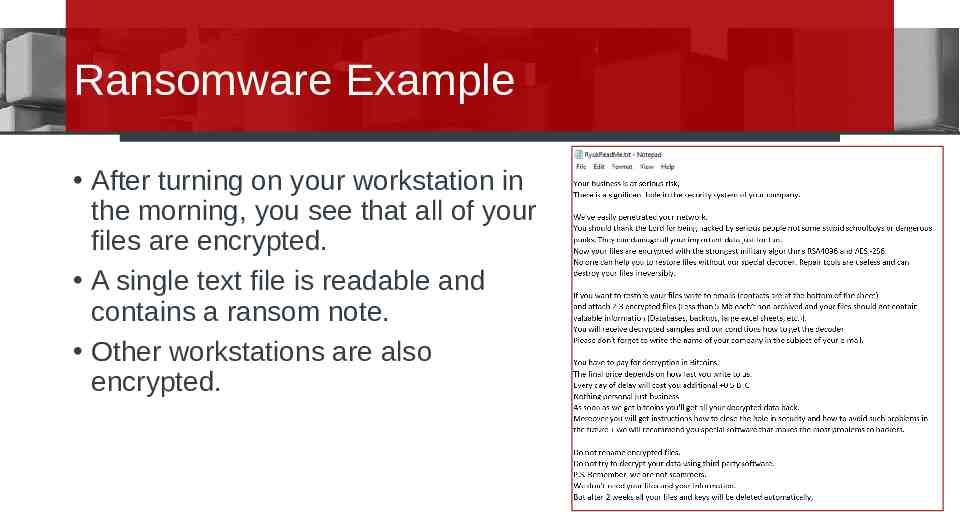
Ransomware Example After turning on your workstation in the morning, you see that all of your files are encrypted. A single text file is readable and contains a ransom note. Other workstations are also encrypted.

Ransomware Example How should you respond if the incident occurs? Report to the information security team Individual employees should not pay the ransom Balancing operational needs with preserving forensic evidence Disconnect impacted systems from the network and from the internet Leave the machine alone. Do not turn off the machine and do not run any anti-virus scans. Determining availability of backups Forensic investigation
Ransomware Example How could the incident have been prevented? Forensic investigation is key to determining entry point Securing remote desktop connections Multifactor authentication Blocking foreign or unapproved IP addresses Stronger network passwords Ensuring patches and updates are installed

Ransomware Example How could the impact have been minimized? Backups Not encrypted Up to date Preserving forensic evidence to aid with legal compliance Proving no data was exfiltrated from the company’s servers
Avoiding Scams Calls/texts/emails from: The IRS The utility company Law enforcement or the courts Tech support Red flags Urgent Payment in gift cards When in doubt, call the actual entity
Credit Monitoring/Identity Theft Protection Watch your credit report Review your bank statements Fraud alerts Credit freeze Take advantage of credit monitoring services when offered
More Tips for Good Cyber Hygiene Unique passwords Strong passwords Do not store passwords in places accessible to others Sticky notes Passwords file on your computer Do not leave your mobile device or laptop unattended or in your car Do not email or mail unencrypted data Do not send sensitive information using public WiFi
More Tips for Good Cyber Hygiene Multifactor authentication whenever possible Lock down access to email accounts or remote desktop applications that can be accessed anywhere in the world Have active backups separate from your primary systems Encrypt laptops, phones, and storage devices (password protection is not enough)
More Tips for Good Cyber Hygiene Do not install unapproved software Do not permit automated forwarding of work emails to personal accounts Obtain verbal confirmation for changes to wire instructions Maintain antivirus and antimalware software Policies for ensuring terminated employees cannot access company information Enable and preserve audit logging for all available systems

More Tips for Good Cyber Hygiene Keep tabs on your vendors Conduct periodic risk assessments Have an incident response plan Delete data after it is no longer needed. More data more risk. Cyberinsurance
Polsinelli PC provides this material for informational purposes only. The material provided herein is general and is not intended to be legal advice. Nothing herein should be relied upon or used without consulting a lawyer to consider your specific circumstances, possible changes to applicable laws, rules and regulations and other legal issues. Receipt of this material does not establish an attorney-client relationship. Polsinelli is very proud of the results we obtain for our clients, but you should know that past results do not guarantee future results; that every case is different and must be judged on its own merits; and that the choice of a lawyer is an important decision and should not be based solely upon advertisements. 2019 Polsinelli is a registered trademark of Polsinelli PC. In California, Polsinelli LLP. Polsinelli PC, Polsinelli LLP In California polsinelli.com






