ASGC Site Update Yi-Ping Wu Jeng-Hsueh Wu
35 Slides167.50 KB
ASGC Site Update Yi-Ping Wu Jeng-Hsueh Wu

Two Significant Researches 1.Oracle Security issues and Studies for 3D 2.Streams Replications Study Report in Oracle 10.2g

1.Oracle Security issues and Studies for 3D 2.Streams Replications Study Report in Oracle 10.2g

Oracle Security issues and Studies for 3D Yi-Ping Wu

Outline Enterprise User Security Introduction Oracle Advanced Security Introduction and SSL Configuration Enterprise User Security Configuration
Enterprise User Security Introduction Oracle Advanced Security Introduction and SSL Configuration Enterprise User Security Configuration

Oracle Enterprise Security A distributed environment makes the issues more critical about “who is a user “ and “what are they allowed to do”. However, the user management price may deduct the cost saving gained from grid computing. Oracle Advanced Security provides the solution to the security in enterprise grid computing environments.
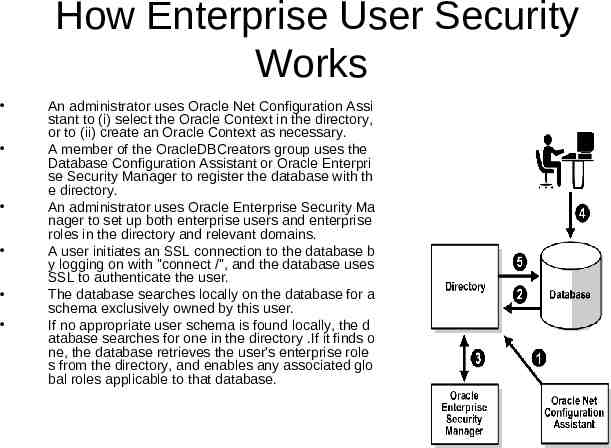
How Enterprise User Security Works An administrator uses Oracle Net Configuration Assi stant to (i) select the Oracle Context in the directory, or to (ii) create an Oracle Context as necessary. A member of the OracleDBCreators group uses the Database Configuration Assistant or Oracle Enterpri se Security Manager to register the database with th e directory. An administrator uses Oracle Enterprise Security Ma nager to set up both enterprise users and enterprise roles in the directory and relevant domains. A user initiates an SSL connection to the database b y logging on with "connect /", and the database uses SSL to authenticate the user. The database searches locally on the database for a schema exclusively owned by this user. If no appropriate user schema is found locally, the d atabase searches for one in the directory .If it finds o ne, the database retrieves the user's enterprise role s from the directory, and enables any associated glo bal roles applicable to that database.
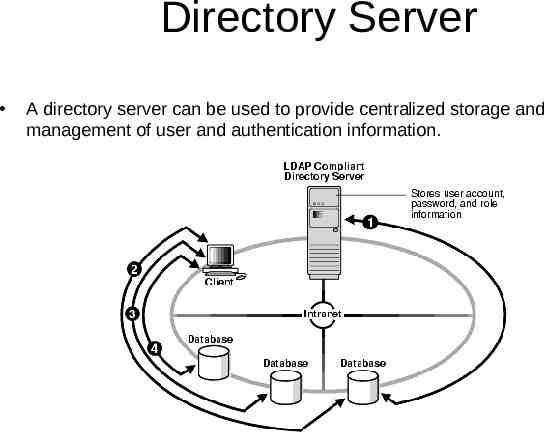
Directory Server A directory server can be used to provide centralized storage and management of user and authentication information.

Enterprise User Security Introduction Oracle Advanced Security Introduction and SSL Configuration Enterprise User Security Configuration

Oracle Advanced Security Configurations Configuring Secure Sockets Layer (SSL) Authentication

Authentication by the Secure Socket Layer Protocol SSL can be used for user authentication to a database, independent of global user managem ent in Oracle Internet Directory. That is, users ca n use SSL to authenticate to the database witho ut implying anything about their directory access. However, if you wish to use the enterprise user f unctionality to manage users and their privileges in a directory, the user must use SSL to authenti cate to the database.

Tasks for SSL Configuration Task 1: Install Oracle Advanced Security and Related Products Task 2: Configure SSL on the Client Task 3: Configure SSL on the Server Task 4: Log on to the Database
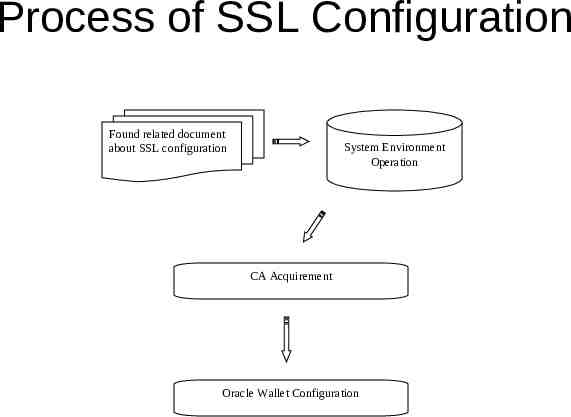
Process of SSL Configuration Found related document about SSL configuration System Environment Operation CA Acquirement Oracle Wallet Configuration
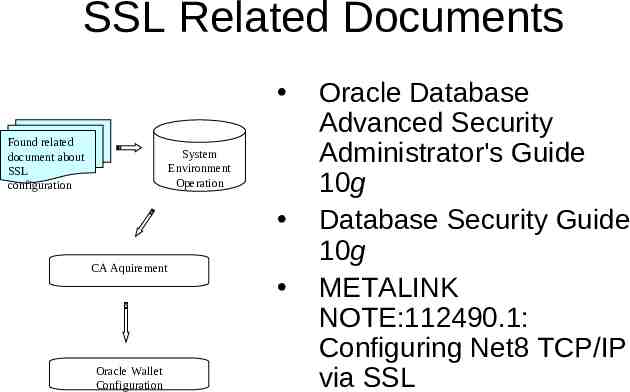
SSL Related Documents Found related document about SSL configuration System Environment Operation CA Aquirement Oracle Wallet Configuration Oracle Database Advanced Security Administrator's Guide 10g Database Security Guide 10g METALINK NOTE:112490.1: Configuring Net8 TCP/IP via SSL
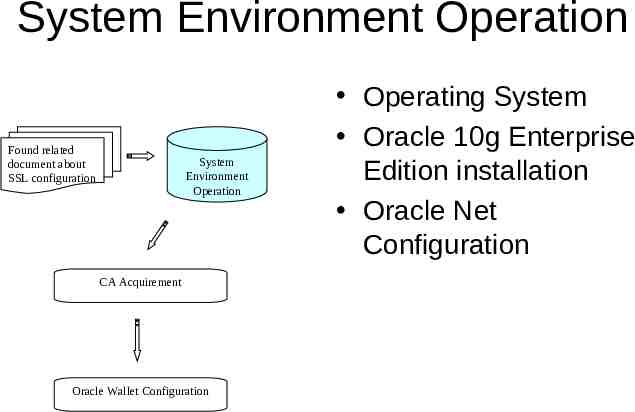
System Environment Operation Found related document about SSL configuration System Environment Operation CA Acquirement Oracle Wallet Configuration Operating System Oracle 10g Enterprise Edition installation Oracle Net Configuration
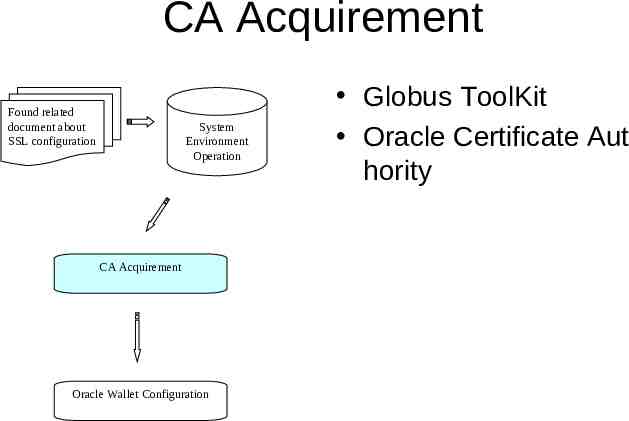
CA Acquirement Found related document about SSL configuration System Environment Operation CA Acquirement Oracle Wallet Configuration Globus ToolKit Oracle Certificate Aut hority
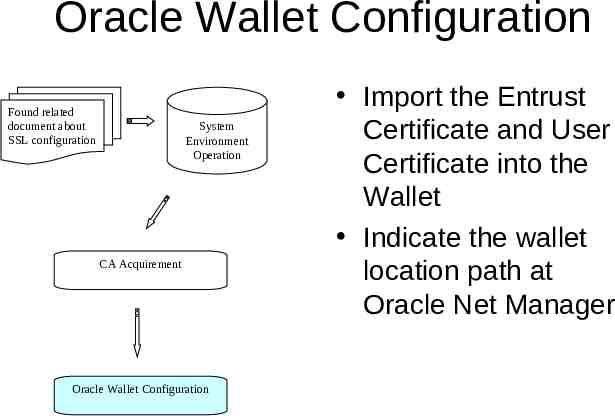
Oracle Wallet Configuration Found related document about SSL configuration System Environment Operation CA Acquirement Oracle Wallet Configuration Import the Entrust Certificate and User Certificate into the Wallet Indicate the wallet location path at Oracle Net Manager
Enterprise User Security Introduction Oracle Advanced Security Introduction and SSL Configuration Enterprise User Security Configuration
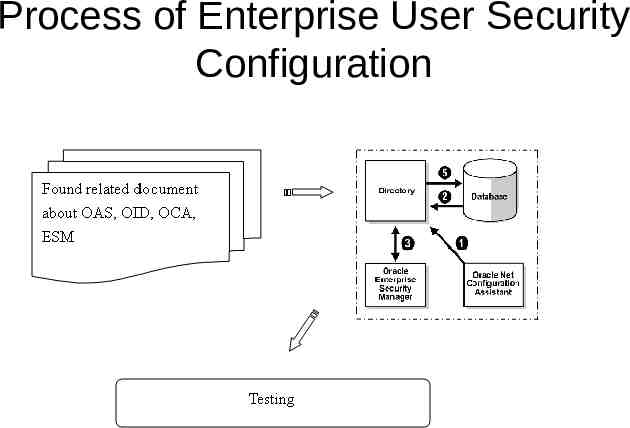
Process of Enterprise User Security Configuration
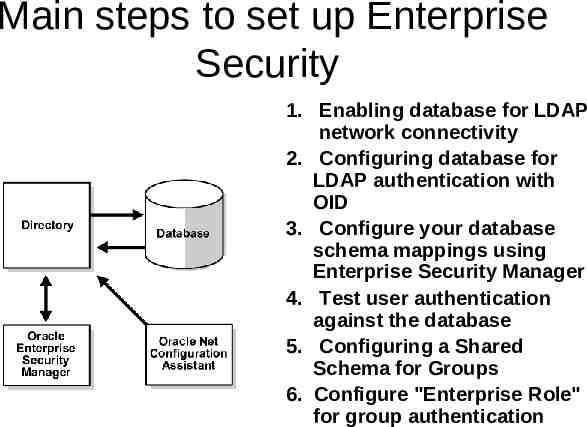
Main steps to set up Enterprise Security 1. Enabling database for LDAP network connectivity 2. Configuring database for LDAP authentication with OID 3. Configure your database schema mappings using Enterprise Security Manager 4. Test user authentication against the database 5. Configuring a Shared Schema for Groups 6. Configure "Enterprise Role" for group authentication

Testing Verify that the database server can bind to the OID serve r ldapbind –h oid homstname -p SSL port -U 3 –W “file: Wallet path -P wallet password Verify that the database is registered with OID RDBM S SERVER DN ‘CN ORA9pc,cn OracleContext,dc or acle,dc com’ corresponding to user wallet DN entry Verify that the new user has been created Verify that the database locate the enterprise domain l dapsearch –h OID host p- OID SSL port -U 3 –W “fi le:,database wallet location ” –P wallet password -b“cn OracleDBSecurity,cn Products,dn OracleContext , DN of domain ” “objectclass orcldbenterprisedomain”

Conclusion Oracle provides a complete infrastructure, Identity Management, for the security solution. During the past months, we have already collected sufficient documents and have the general understanding of Oracle Identity Management and Advanced Security. SSL authentication has been successfully configured, which is essential for the future security environment settings. We are currently testing the Enterprise User Security with password authentication, and our next step will be Enterprise User Security with SSL authentication.

Related Documents Oracle Database Advanced Security Administrat or's Guide 10g Database Security Guide 10g Oracle Identity Management Online Training http://www.oracle.com/technology/products/oid/oid html/sec idm training/html masters/gsmain.htm Oracle Internet Directory Online Training http://www.oracle.com/technology/products/oid/oid html/oidqs/html masters/gsmain.htm

Streams Replications Study Report in Oracle 10.2g
Official Docs and References Oracle Streams configuration by Eva Sample Scripts by EM in 10g R2 Streams Concepts and Administration Streams Replication Administrator's Guide PL/SQL Packages and Types Reference

Streams Replications Study Report in Oracle 10.2g Jeng-Hsueh Wu

Official Docs and References Oracle Streams configuration by Eva Sample Scripts by EM in 10g R2 Streams Concepts and Administration Streams Replication Administrator's Guide PL/SQL Packages and Types Reference

1.Oracle Security issues and Studies for 3D 2.Streams Replications Study Report in Oracle 10.2g
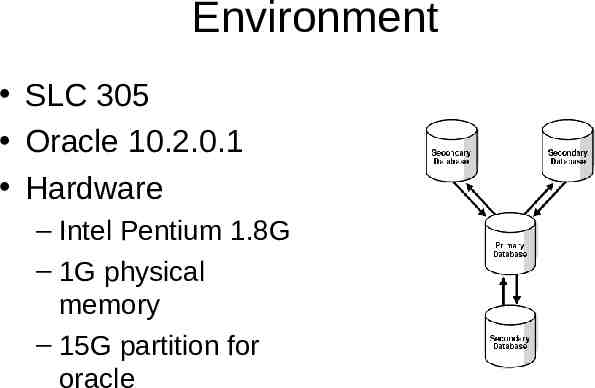
Environment SLC 305 Oracle 10.2.0.1 Hardware – Intel Pentium 1.8G – 1G physical memory – 15G partition for oracle

3 Stages Stage DB Bi-directional 1 One DB to One DB No 2 One DB to One DB Yes 3 One DB to Many DB Yes
Scripts and Notes by ASGC Concepts for Oracle Streams Replications – http://gate.sinica.edu.tw/ jhwu/streams/streams.concepts.050929.pdf Scripts for building the streams with type "hub and spoke" and bi-directional – http://gate.sinica.edu.tw/ jhwu/streams/streams.scripts.tar.gz
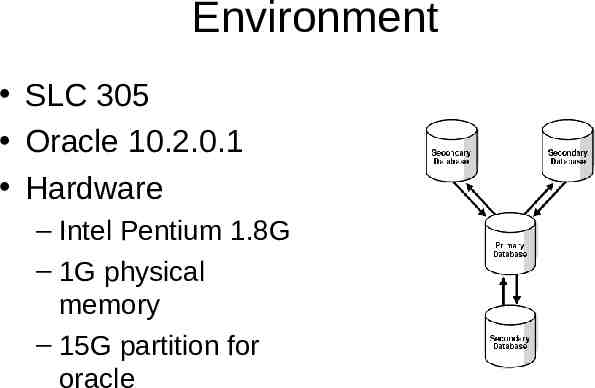
Environment SLC 305 Oracle 10.2.0.1 Hardware – Intel Pentium 1.8G – 1G physical memory – 15G partition for oracle

3 Stages Stage DB Bi-directional 1 One DB to One DB No 2 One DB to One DB Yes 3 One DB to Many DB Yes
Scripts and Notes by ASGC Concepts for Oracle Streams Replications – http://gate.sinica.edu.tw/ jhwu/streams/streams.concepts.050929.pdf Scripts for building the streams with type "hub and spoke" and bi-directional – http://gate.sinica.edu.tw/ jhwu/streams/streams.scripts.tar.gz