Implementing Security Patch Management Alun Rogers
37 Slides3.87 MB

Implementing Security Patch Management Alun Rogers Principal Consultant - Lynx [email protected]
It’s all about Processes Microsoft Operations Framework Datacenters are all about process Windows admins have grown from desktop/helpdesks MOF will prescribe processes to manage Windows in a datacenter People Based on ITIL specs Templates to apply Process Technology
Microsoft Solutions for Management Integrated people, process and technology Targeted customer scenarios Engineered, tested and proven MOF/ITIL Available Offerings: Offerings: Ops Assessment Core Windows Mgt Security Patch Mgt Server Consolidation Service Monitoring Business Desktop Deployment New Application Deployment
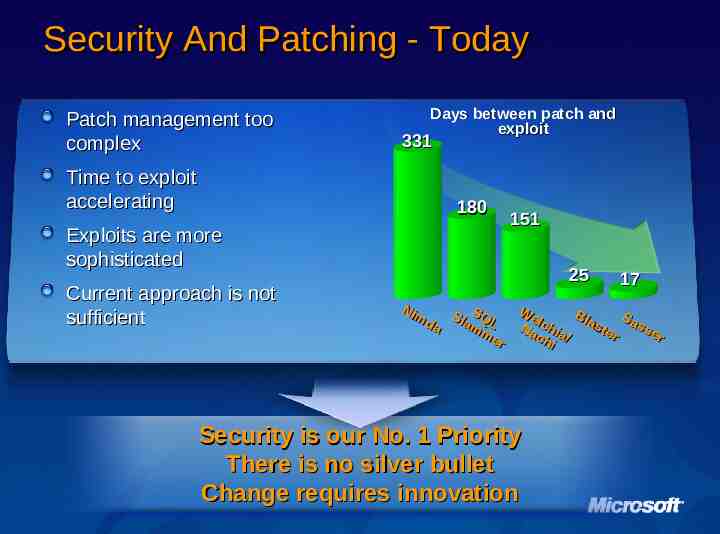
Security And Patching - Today Patch management too complex Time to exploit accelerating Days between patch and exploit 331 180 Exploits are more sophisticated Current approach is not sufficient 151 25 Nim S da SlamQL me r 17 We Bla S l c ste ass Na hia er r ch / i Security is our No. 1 Priority There is no silver bullet Change requires innovation

Management at Microsoft Microsoft is committed to making management an asset for the company Make Windows the best managed environment Make Windows the best platform for customers to manage from and ISV’s to write on Build the best management solutions for Windows All management unified under one group Single VP, 600 working on mgmt & supportability Infrastructure - WMI, MMC, Group Policy, Windows Installer, SAF (The PC Health Support Automation Framework), Help and Support Center, PC Health Solutions - SMS, MOM, Application Center 2000, Terminal Server, Windows Update

Patch Management End to End Awareness Obtain information about the latest software update vulnerabilities Audit your enterprise for applicable software updates Response Assess and authorize available software updates Deploy updates in a timely, accurate, and efficient manner Measurements Track update deployment/compliance

MBSA 1.2.1 Microsoft Baseline Security Analyser

MBSA Objectives What are we trying to solve with MBSA? Know which computers are at risk and how to mitigate / manage MBSA is free assessment (agent less too!) SUS is the free patch deployment tool SMS is the full featured management product MBSA 1.2.1 increases the coverage of Microsoft’s products More consistent patch detection results with MBSA 1.2.1 Target 1-10,000 seat org, 1-5 admin staff, the IT Pro, and power users too

Tool Overview Single executable that runs on Windows 2000, Windows XP, and Windows Server 2003 Performs remote scans against Windows NT 4.0, Windows 2000, Windows XP, and Windows Server 2003 systems Focused on agent less assessment, tactical deployment, easy to use AND easy to leverage MSI package contains GUI (mbsa.exe) Command line interface (mbsacli.exe) Latest version is 1.2.1, released August ‘04
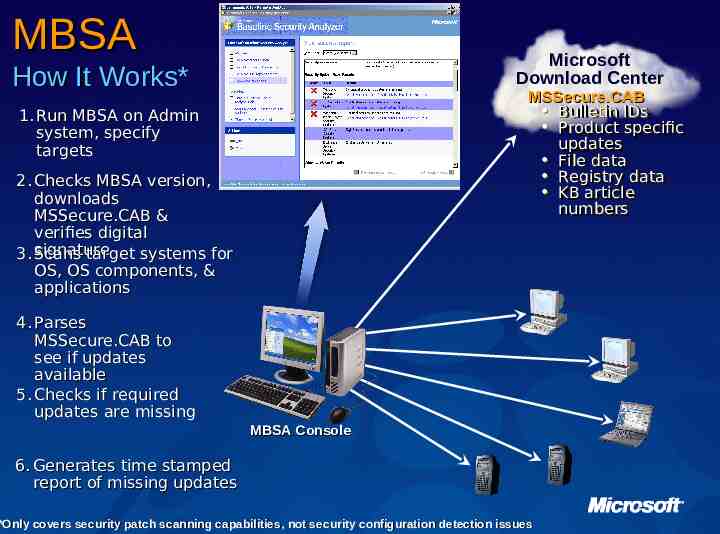
MBSA Microsoft Download Center How It Works* MSSecure.CAB Bulletin Bulletin IDs IDs Product specific Product specific updates updates File File data data Registry Registry data data KB KB article article numbers numbers 1. Run MBSA on Admin system, specify targets 2. Checks MBSA version, downloads MSSecure.CAB & verifies digital 3. signature Scans target systems for OS, OS components, & applications 4. Parses MSSecure.CAB to see if updates available 5. Checks if required updates are missing MBSA Console 6. Generates time stamped report of missing updates *Only covers security patch scanning capabilities, not security configuration detection issues
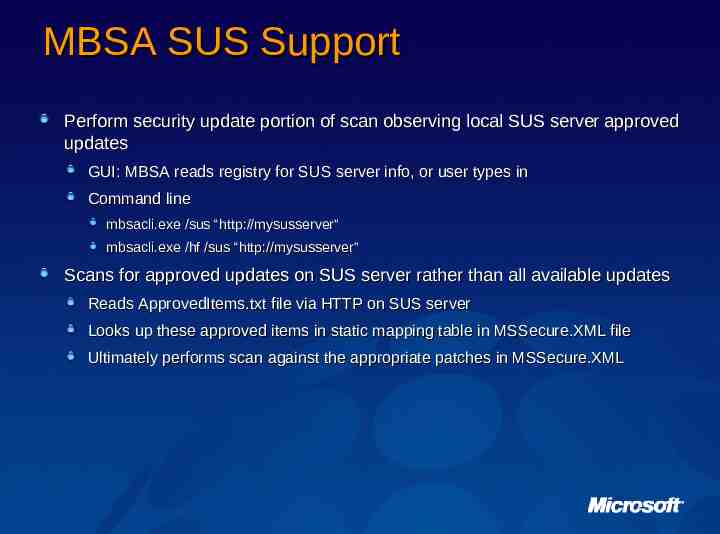
MBSA SUS Support Perform security update portion of scan observing local SUS server approved updates GUI: MBSA reads registry for SUS server info, or user types in Command line mbsacli.exe /sus “http://mysusserver” mbsacli.exe /hf /sus “http://mysusserver” Scans for approved updates on SUS server rather than all available updates Reads ApprovedItems.txt file via HTTP on SUS server Looks up these approved items in static mapping table in MSSecure.XML file Ultimately performs scan against the appropriate patches in MSSecure.XML

MBSA SMS Support Compatibility with SMS 2.0 Software Update Services Feature Pack and SMS 2003 Pushes mbsacli.exe to each client to perform local scan (mbsacli.exe /hf) Parses output SMS Administrators can centrally distribute security updates to clients SMS is now using MBSA v1.2.1 Service packs in addition to security updates and update rollups
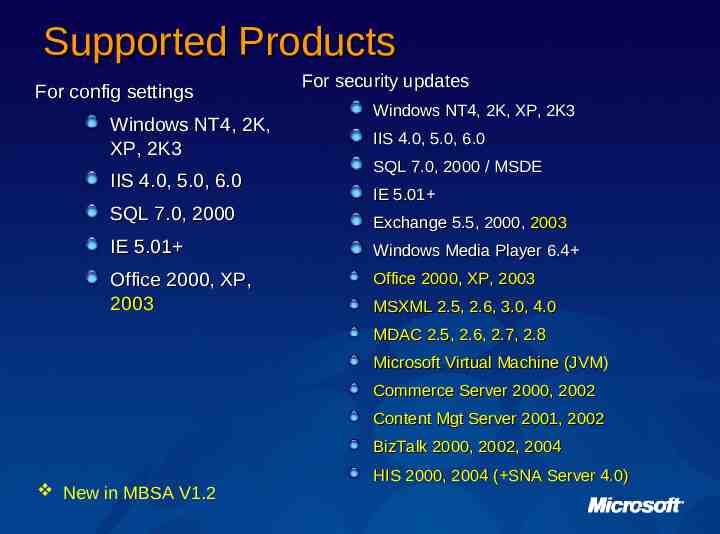
Supported Products For config settings Windows NT4, 2K, XP, 2K3 IIS 4.0, 5.0, 6.0 SQL 7.0, 2000 For security updates Windows NT4, 2K, XP, 2K3 IIS 4.0, 5.0, 6.0 SQL 7.0, 2000 / MSDE IE 5.01 Exchange 5.5, 2000, 2003 IE 5.01 Windows Media Player 6.4 Office 2000, XP, 2003 Office 2000, XP, 2003 MSXML 2.5, 2.6, 3.0, 4.0 MDAC 2.5, 2.6, 2.7, 2.8 Microsoft Virtual Machine (JVM) Commerce Server 2000, 2002 Content Mgt Server 2001, 2002 BizTalk 2000, 2002, 2004 New in MBSA V1.2 HIS 2000, 2004 ( SNA Server 4.0)

SUS Software Update Services
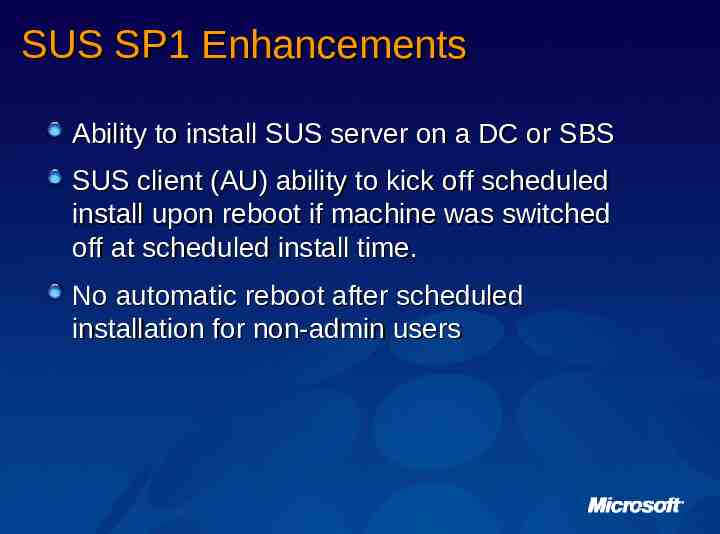
SUS SP1 Enhancements Ability to install SUS server on a DC or SBS SUS client (AU) ability to kick off scheduled install upon reboot if machine was switched off at scheduled install time. No automatic reboot after scheduled installation for non-admin users
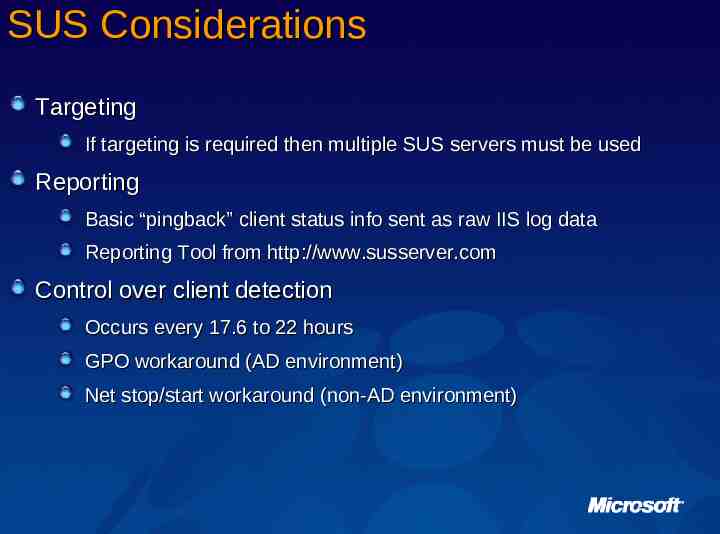
SUS Considerations Targeting If targeting is required then multiple SUS servers must be used Reporting Basic “pingback” client status info sent as raw IIS log data Reporting Tool from http://www.susserver.com Control over client detection Occurs every 17.6 to 22 hours GPO workaround (AD environment) Net stop/start workaround (non-AD environment)
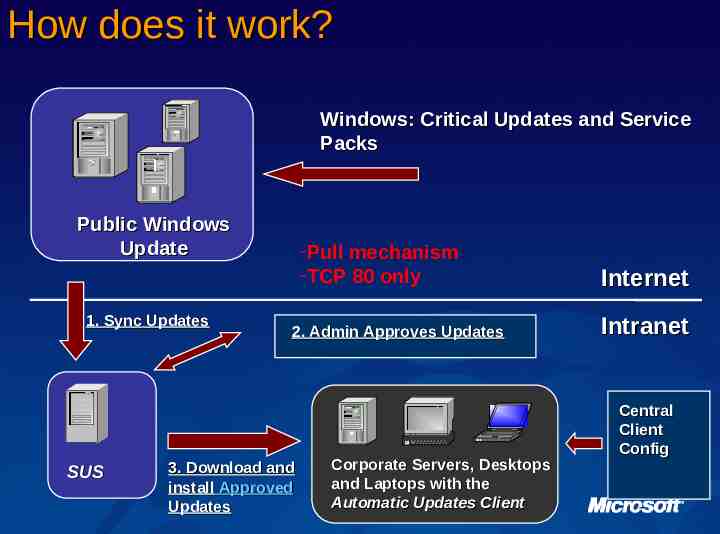
How does it work? Windows: Critical Updates and Service Packs Public Windows Update 1. Sync Updates SUS -Pull mechanism -TCP 80 only 2. Admin Approves Updates 3. Download and install Approved Updates Corporate Servers, Desktops and Laptops with the Automatic Updates Client Internet Intranet Central Client Config

SMS 2003 and SUS Patching the Enterprise

SMS 2003 & Patch Management Vulnerability Assessment Leverages existing tools like MS Baseline Security Analyzer Collects MBSA results for storage in a central repository Rich reporting provides detailed vulnerability analysis and enables mitigation planning Status and Compliance Reporting Deployment status as patches are delivered Built-in reports, status messaging, and summarization Determine actual baselines in the environment before changing the environment Reference computer templates for baseline determination and compliance
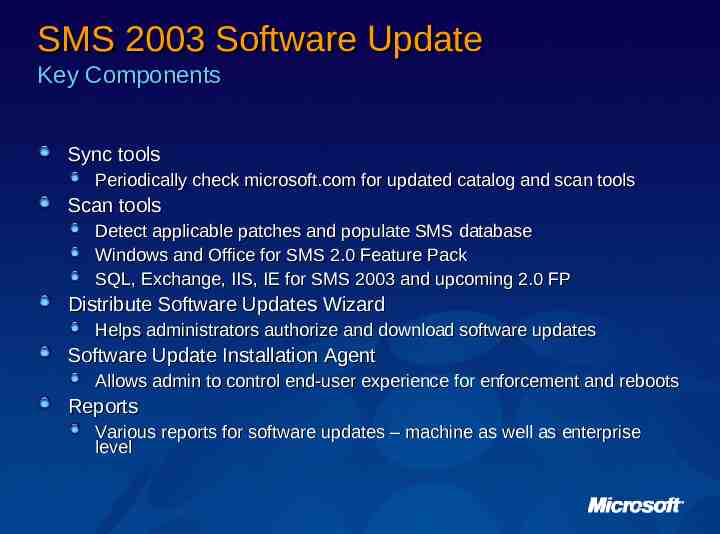
SMS 2003 Software Update Key Components Sync tools Periodically check microsoft.com for updated catalog and scan tools Scan tools Detect applicable patches and populate SMS database Windows and Office for SMS 2.0 Feature Pack SQL, Exchange, IIS, IE for SMS 2003 and upcoming 2.0 FP Distribute Software Updates Wizard Helps administrators authorize and download software updates Software Update Installation Agent Allows admin to control end-user experience for enforcement and reboots Reports Various reports for software updates – machine as well as enterprise level
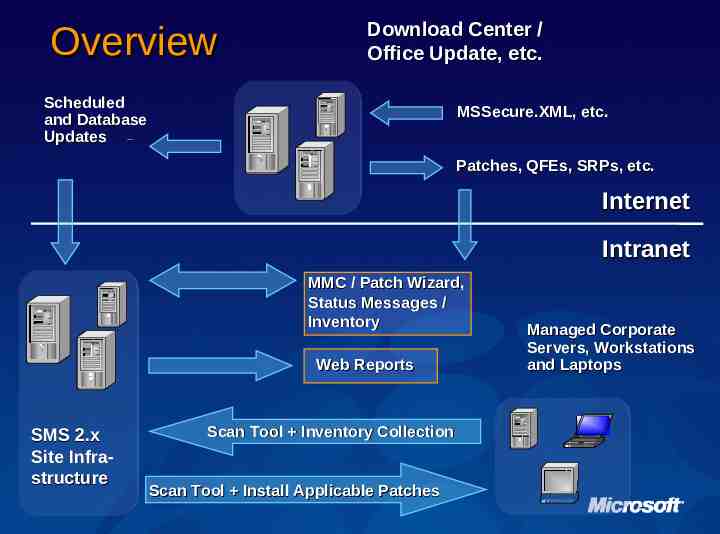
Overview Download Center / Office Update, etc. Scheduled and Database Updates MSSecure.XML, etc. Patches, QFEs, SRPs, etc. Internet Intranet MMC / Patch Wizard, Status Messages / Inventory Web Reports SMS 2.x Site Infrastructure Scan Tool Inventory Collection Scan Tool Install Applicable Patches Managed Corporate Servers, Workstations and Laptops
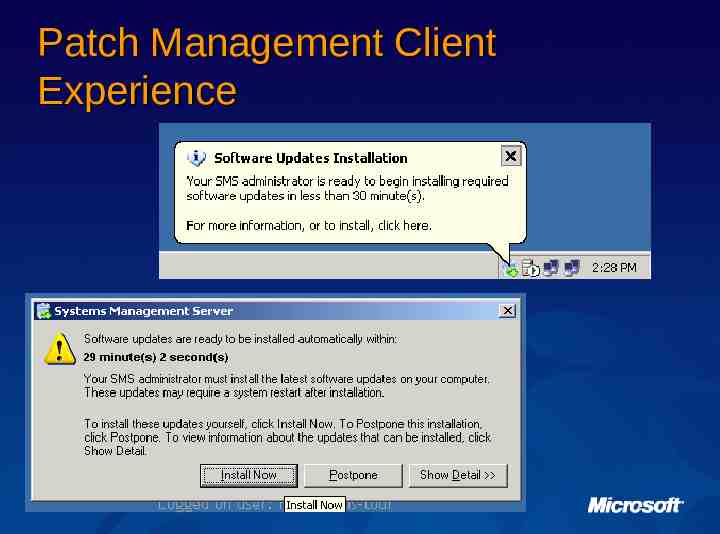
Patch Management Client Experience
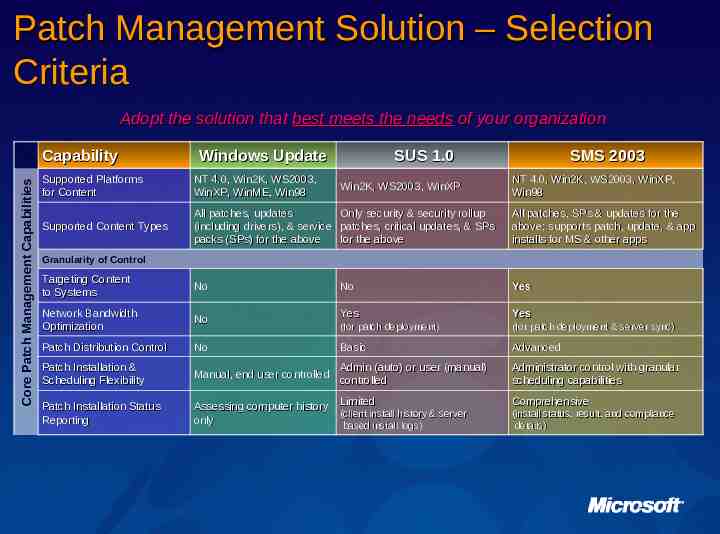
Patch Management Solution – Selection Criteria Adopt the solution that best meets the needs of your organization Core Patch Management Capabilities Capability Windows Update SUS 1.0 SMS 2003 Supported Platforms for Content NT 4.0, Win2K, WS2003, WinXP, WinME, Win98 Supported Content Types All patches, updates Only security & security rollup (including drivers), & service patches, critical updates, & SPs packs (SPs) for the above for the above All patches, SPs & updates for the above; supports patch, update, & app installs for MS & other apps Targeting Content to Systems No No Yes Network Bandwidth Optimization No Yes Yes (for patch deployment) (for patch deployment & server sync) Patch Distribution Control No Basic Advanced Patch Installation & Scheduling Flexibility Manual, end user controlled Admin (auto) or user (manual) controlled Administrator control with granular scheduling capabilities Patch Installation Status Reporting Assessing computer history Limited (client install history & server only based install logs) Win2K, WS2003, WinXP NT 4.0, Win2K, WS2003, WinXP, Win98 Granularity of Control based install logs) Comprehensive (install status, result, and compliance details)
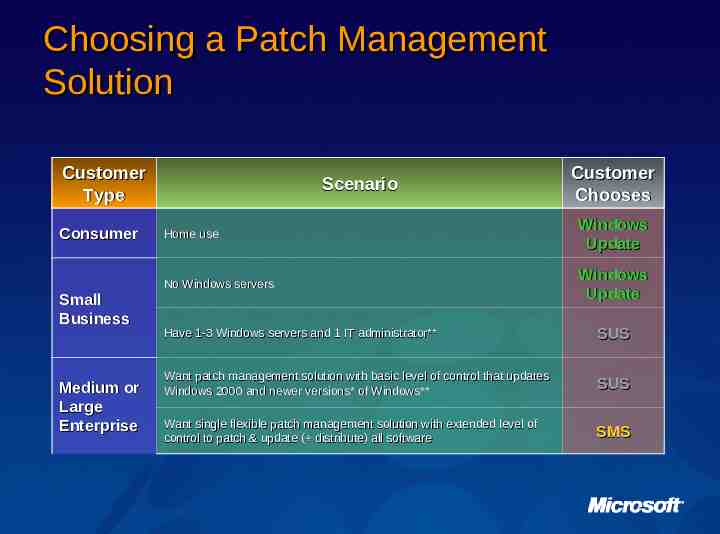
Choosing a Patch Management Solution Customer Type Consumer Small Business Medium or Large Enterprise Scenario Customer Chooses Home use Windows Update No Windows servers Windows Update Have 1-3 Windows servers and 1 IT administrator** SUS Want patch management solution with basic level of control that updates Windows 2000 and newer versions* of Windows** SUS Want single flexible patch management solution with extended level of control to patch & update ( distribute) all software SMS

Futures

General Futures XP SP2 - Automatic Update (WUS ready) Includes Windows 2000 SP3 and 2003 SP1 SMS 2003 SP1 - AU from XP SP2 WUS – Greater flexibility Beta open today www.microsoft.com/wus
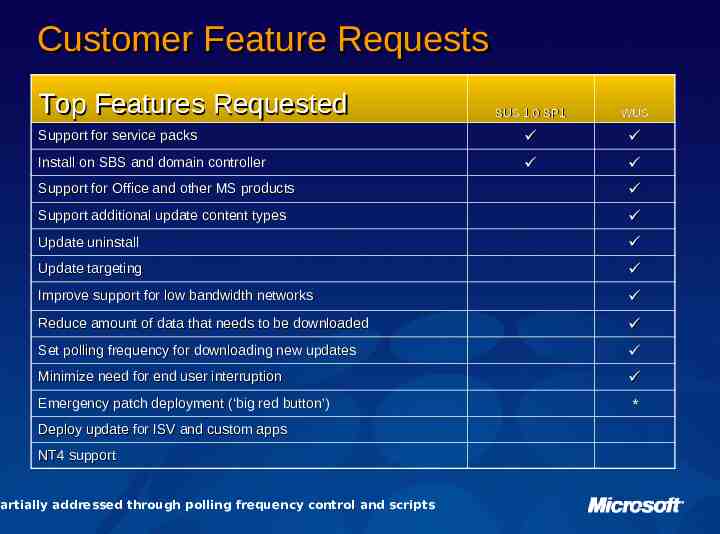
Customer Feature Requests Top Features Requested SUS 1.0 SP1 WUS Support for service packs Install on SBS and domain controller Support for Office and other MS products Support additional update content types Update uninstall Update targeting Improve support for low bandwidth networks Reduce amount of data that needs to be downloaded Set polling frequency for downloading new updates Minimize need for end user interruption Emergency patch deployment (‘big red button’) * Deploy update for ISV and custom apps NT4 support Partially addressed through polling frequency control and scripts

WUS Features Administrator control Initiate install, uninstall, pre-deployment check Deploy different updates to target groups Date-based deadlines for patch deployment Configurable polling frequency Pre-set rules for auto-deployment Non-administrators can receive update notifications Explicit server admin roles Bandwidth efficiency BITS for client-server and server-server downloads Update subscriptions (per product/classification) Support for “delta compression” technologies Option to only download updates when deployed
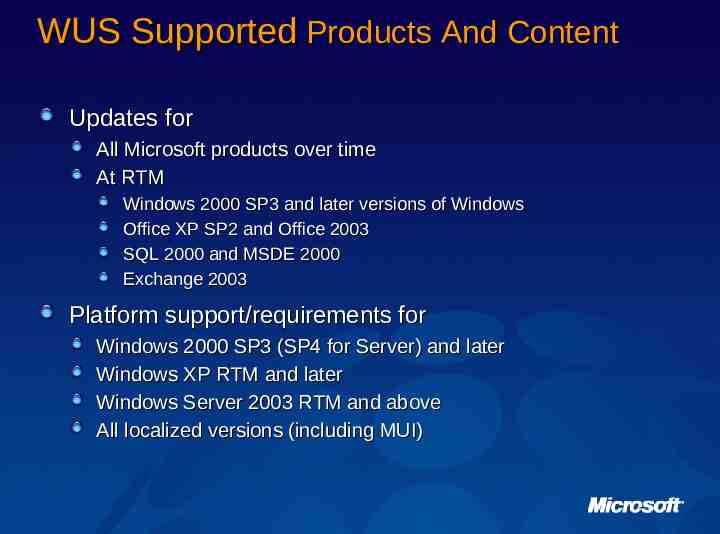
WUS Supported Products And Content Updates for All Microsoft products over time At RTM Windows 2000 SP3 and later versions of Windows Office XP SP2 and Office 2003 SQL 2000 and MSDE 2000 Exchange 2003 Platform support/requirements for Windows 2000 SP3 (SP4 for Server) and later Windows XP RTM and later Windows Server 2003 RTM and above All localized versions (including MUI)

Update Management Features Target Groups Registry-based policy support for AD environments Server-side lists for non-AD environments Administrator control Initiate scan of machines for patch applicability Approve for install and uninstall (requires update support) Date-based deadlines for approved updates Deploy different updates to target groups Configurable client polling frequency Configurable reboot behavior Port configurability Non-administrators can install updates (like administrators) Install at Shutdown (XP SP2 only)
Network Use Optimization Features Resilient and transparent BITS* for client-server and server-server downloads Downloads are in the background Minimized data downloads Update subscriptions (per product/classification) Support for “delta compression” technologies for clientserver communications Option to only download approved updates *Background Intelligent Transfer Service

Reporting Features Standard consolidated reports(for client activity) Per machine/per update/per target group Download, install success & failures with error information Content synchronization status reports What’s new, what changed Aggregate reports for multiple servers Summary event roll-up to parent server Event log integration Client and server status events sent to local event log
Web Resources Management http://www.microsoft.com/management Microsoft Management Alliance http://www.microsoft.com/management/mma Microsoft Solutions for Management http://www.microsoft.com/solutions/msm http://www.microsoft.com/mof SMS http://www.microsoft.com/smserver SUS http://www.microsoft.com/windows2000/windowsupdate/sus/ default.asp ITIL http://www.itil.co.uk http://www.itsmf.net

Community Resources Community Resources http://www.microsoft.com/communities/default.mspx Most Valuable Professional (MVP) http://www.microsoft.com/communities/mvp Newsgroups Converse online with Microsoft Newsgroups, including Worldwide http://communities2.microsoft.com/communities /newsgroups/en-us/default.aspx User Groups - Meet and learn with your peers http://www.microsoft.com/communities/usergroups default.mspx
Microsoft Learning Security Resources for IT Professionals Free Online Skills Assessments Introduction to Microsoft Security Guidance Hands-On Instructor-Led Training Course 2823 Managing the Deployment of Service Packs and Security Updates Protecting the Perimeter of Networks Free Self-Paced E-Learning Clinics Clinic 2801 Clinic 2802 Microsoft Security Guidance Training I (1 day) Microsoft Security Guidance Training II (1 day) Implementing and Administering Security in a Windows Server 2003 Network (5 days) Hands On Labs 2811 Applying Microsoft Security Guidance (1 day) Course 2830 Designing Security for Microsoft Networks (3 days) Course 2824 Implementing Internet Security and Acceleration Server 2004 (4 days) Microsoft Certified Professional Specializations Self-Paced Microsoft Press Reference Books Microsoft Windows Security Resource Kit ISBN: 0-7356-1868-2 Assessing Network Security ISBN: 0-7356-2033-4 Microsoft Windows Server 2003 PKI and Certificate Security ISBN: 0-7356-2021-0
Event Information What’s Next? Technical Roadshow Post Event Website www.microsoft.com/uk/techroadshow/postevents Available from Monday 18th April Please complete your Evaluation Form!

2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.






