Addressing Security Satisfaction Cliff Evans Security and Privacy
22 Slides5.27 MB

Addressing Security Satisfaction Cliff Evans Security and Privacy Lead Trustworthy Computing Group Microsoft UK

Agenda The Fundamentals Satisfaction – How are we doing? The Approach Trustworthy Computing Security Development Lifecycle (SDL) Vulnerability Analysis Helping you Secure your IT Environment (free tools and information) SDL the next steps Microsoft Security Assessment Tool

Satisfaction – How are we doing? Consumers Very High Overall Satisfaction High Security Satisfaction High Privacy Satisfaction IT Professionals / Business Decision Makers Moderate Overall Satisfaction Moderate Security Satisfaction Moderate Privacy Satisfaction

Trustworthy Computing TWC Announced SDL begins 2002 Windows Server 2003 2003 Windows XP SP2 DSI Launched SQL Server 2005 Visual Studio 2005 Windows Server 2003 SP1 Malicious SW Removal Tool 2004 2005 Windows Defender Windows Live OneCare 2006 Windows Vista Office 2007 Forefront 2007 Windows Server 2008 SQL Server 2008 2008

The Microsoft Security Development Lifecycle Conception Goals Protect Microsoft customers by Reducing the number of vulnerabilities Reducing the severity of vulnerabilities Releas e Key Principles Prescriptive yet practical approach Proactive – not just “looking for bugs” Eliminate security problems early Secure by design

First Year of Vulnerabilities* 2007* SDL Results 120 54 50 80 65 2 7 30 30 20 19 35 20 10 36 0 17 0 Windows XP Unfixed Windows XP SP2 Windows Vista Windows Vista Fixed Low Vulnerabilities Fixed One Year After Release* 30 Moderate Important Ciritcal Vulnerabilities disclosed and fixed Quarterly totals, 2000-2006** 20 18 25 16 8 14 20 12 15 3 18 10 10 8 6 14 5 4 2 Medium *Source: http://blogs.csoonline.com/blog/jeff jones 2006 Q4 Q2 Q3 Q4 2005 Q1 Q3 Q1 Q3 2004 Q4 Q1 Q2 Q3 2003 Q4 Q1 Microsoft SQL Server Q2 Q3 2002 Q4 Q1 Q2 2001 Q2 IE 7 Q3 200 0 Q2 Q4 IE 6 Q1 0 0 High 15 40 60 40 2 4 Q4 100 60 **Source: Which database is more secure? Oracle vs. Microsoft, David Litchfield, NGS Software, 21November-2006

SDL Results 10.0% 4000 9.0% 3500 8.0% 3000 7.0% 2500 6.0% 2000 5.0% 1500 3179 3268 3296 2573 1000 500 0 708 631 44 66 1954 11381391 64 88 75 9.5% 4.0% 2815 3.0% 5.9% 2712 2.0% 1.0% 5.3%5.9% 4.9% 3.7% 4.2% 3.3% 3.0% 0.0% 87 98 168 146 90 03 03 4 80 4 0 5 0 5 1H 2H 0 H 6 0 1 0 2H 1H 06 07 2H 1H 07 08 H H 2 H 1 2 1H non-MSFT vulns MSFT vulns Source: http://blogs.csoonline.com/blog/jeff jones 3.1% 2.9% 03 03 04 4 H 5 1 2H 1H H0 H0 05 06 7 2 06 H 7 1 2 1H 2H H0 H0 08 1 H 2 1 Expon. (MSFT % of All Disclosures)

Windows Server @ 90 Days Vulnerabilities in First 90 Days 10 8 6 4 9 9 6 2 0 4 Windows Server 20033 all Windows Server 2003gui Windows Server 2008all Windows Server 2008gui Windows Server 2008core Source: internal study by Jeff Jones

Windows Vista – First 12 Months First Year of Vulnerabilities 400 350 300 250 200 150 100 50 Unfixe 0 d Windows XP Metric Vulnerabilities fixed Security Updates Patch Events Weeks with at least 1 Patch Event Windows Vista Windows Vista (year 1) 36 17 9 9 RHEL4 reduced UbuntuLTS reduced 65 30 26 Red Hat rhel4ws reduced (year 1) 360 125 64 25 44 Windows XP (year 1) Mac OS X 10.4 Ubuntu 6.06 LTS reduced (year 1) Mac OS X 10.4 (year 1) 224 80 65 116 17 17 39 15 http://blogs.csoonline.com/blog/jeff jones
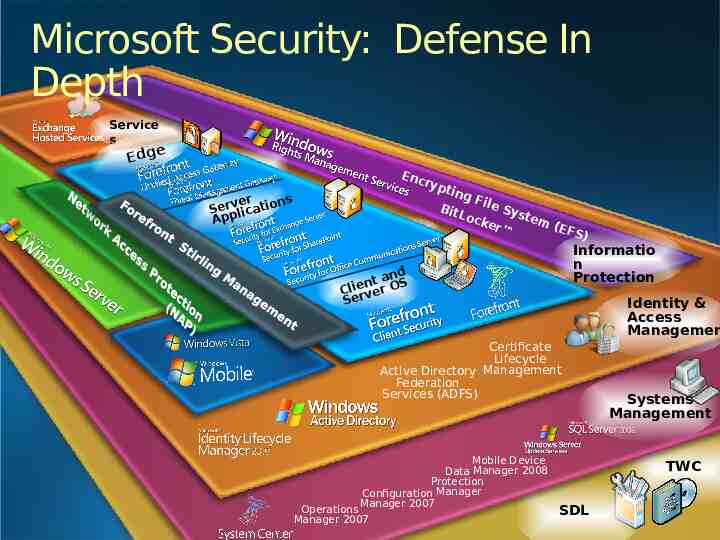
Microsoft Security: Defense In Depth Service s Ed g e Edge verations Serp lic Ap Enc ryp tin gF ile Bit Sys L oc t em k er (E F Server S) Applicatio ns d t an n S e O i Cl rver e S Client and Server OS Informatio n Protection Certificate Lifecycle Active Directory Management Federation Services (ADFS) Mobile Device Data Manager 2008 Protection Configuration Manager Manager 2007 Operations Manager 2007 Identity & Access Managemen Systems Management TWC SDL

Comprehensive line of business security products that helps you gain greater protection and secure access through deep integration and simplified management Next Next Generation Generation Microsoft Microsoft Forefront Forefront

Microsoft Forefront Product Roadmap H1 2008 H2 2008 NEW Integrated BETA Security System H1 2009 Network Edge NEXT NEW BETA NEW Server Applications NEW NEXT NEXT Client and Server OS Codename “Stirling”

SDL Pro Network Security service providers that specialize in application security and have been trained by Microsoft in the tools and guidance associated with its Security Development Lifecycle. These service providers will guide and support organizations - both large and small - in implementing the SDL in their environments. www.microsoft.com/sdl

SDL Optimization Model Created to facilitate gradual, consistent and cost-effective implementation of the SDL in development organizations outside of Microsoft. The model, which will be freely available for download in November, is based on the Microsoft IT Infrastructure and Application Platform Optimization models, www.microsoft.com/sdl which focus on

Microsoft SDL Threat Allows for early, Modelling structured analysis and proactive mitigation and tracking of potential security and privacy issues in new and existing applications. Due for release in November, this new, freely available tool will offer a threat modelling methodology that any software architect can lead effectively. www.microsoft.com/sdl

Microsoft Security Assessment Tool (MSAT) The Microsoft Security Assessment Tool (MSAT) is a free tool designed to help organizations assess weaknesses in your current IT security environment, reveal a prioritized list of issues, and help provide specific guidance to minimize those risks. www.microsoft.com/security/msat

Microsoft Security Assessment Tool (MSAT) www.microsoft.com/security/msat

UK Security Newsletter www.microsoft.com/uk/security

Microsoft’s Security Strategy [email protected]

2008 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.








