Vulnerability Assessment in Smart Grids Jinyuan Stella Sun UTK
54 Slides4.97 MB

Vulnerability Assessment in Smart Grids Jinyuan Stella Sun UTK Fall 2015

Contents Background Roadmap Vulnerability Assessment of Phasor Networks Defense and countermeasures 2

Background The advent of Smart Grid A class of technologies used to modernize electricity delivery systems, using computer-based remote control and automations Two-way communication and computer processing that has been used for decades in other industries 3

Background The advent of Smart Grid Benefits by incorporating richer data Better interoperability Big improvements in efficiency Electricity delivery system Energy users A more resilient power grid 4

Background Data security is critical Security: control, operation, applications in the smart grid rely on accurate and timely data 5

Background Data security under threat External: hackers, state sponsored cyberwarfare targeting the critical infrastructure. Internal: Disgruntled employee, industrial espionage 6
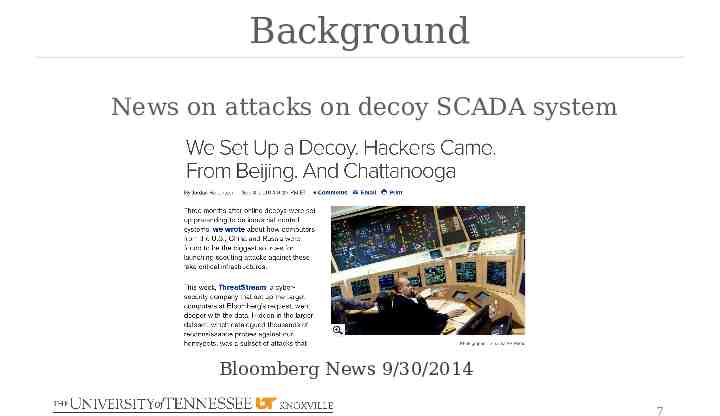
Background News on attacks on decoy SCADA system Bloomberg News 9/30/2014 7

Background 8

Background Challenges New technologies Larger volume, wider variety More entities involved Multiple data creators (ownership) Multiple data consumers Private data cross multiple trust boundaries 9
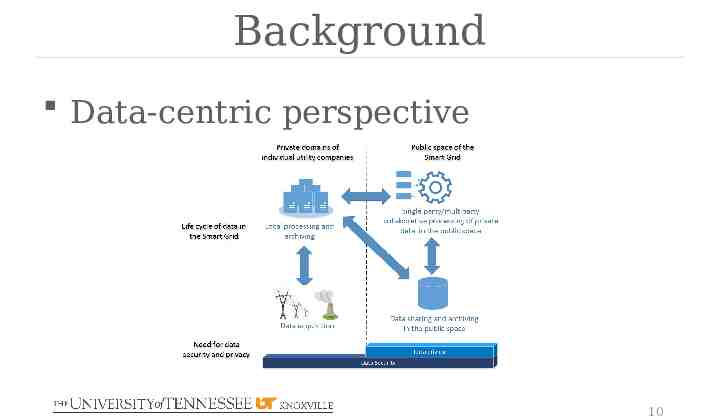
Background Data-centric perspective 10
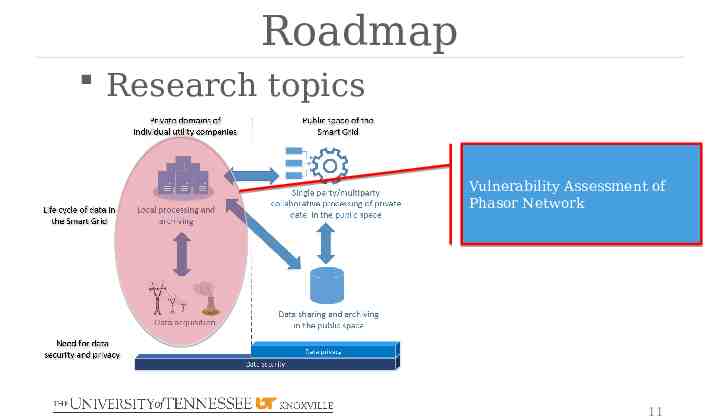
Roadmap Research topics Vulnerability Assessment of Phasor Network 11

Phasor Network Applications Introduction Phasor network enables many useful phasor data applications Phasor data applications rely on accurate and timely phasor data collected and transferred by the phasor network Vulnerabilities may exist in the standards, protocols, implementations, and configurations of the phasor network technologies. 12

What is Vulnerability Assessment? Vulnerability assessment The process of identifying, quantifying, and prioritizing the vulnerabilities of a system, network, or application. 13

Vulnerability Assessment in Literature State-of-the-art Zhu, Bonnie, Anthony Joseph, and Shankar Sastry. "A taxonomy of cyber attacks on SCADA systems." Internet of Things (iThings/CPSCom), 2011 International Conference on and 4th International Conference on Cyber, Physical and Social Computing. IEEE, 2011. Stewart, John, et al. "Synchrophasor Security Practices." (2010). Sridhar, Siddharth, Adam Hahn, and Manimaran Govindarasu. "Cyber–physical system security for the electric power grid." Proceedings of the IEEE 100.1 (2012): 210-224. 14
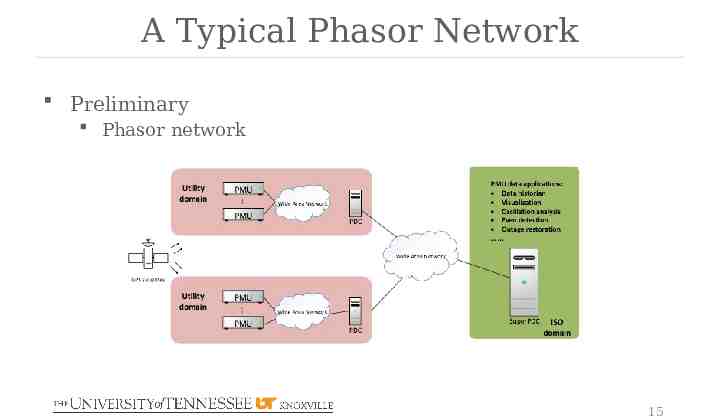
A Typical Phasor Network Preliminary Phasor network 15

IEEE C37.118 Standard Preliminary IEEE C37.118 standard Synchronization to the UTC time Time accuracy Definitions of synchrophasors Criterion for the evaluation of quality of synchrophasor measurements Messaging system Four types of frames A data transfer protocol 16
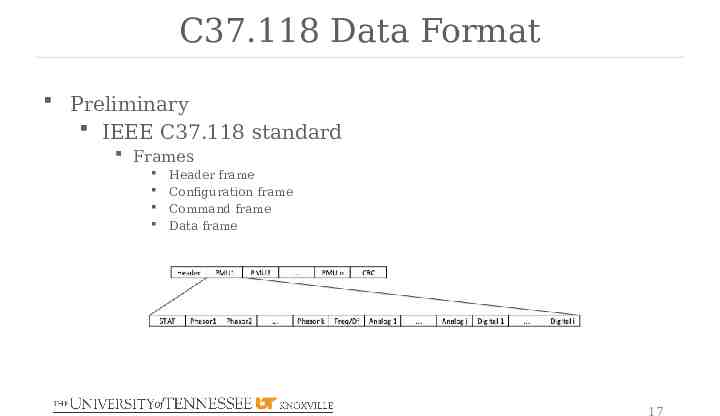
C37.118 Data Format Preliminary IEEE C37.118 standard Frames Header frame Configuration frame Command frame Data frame 17
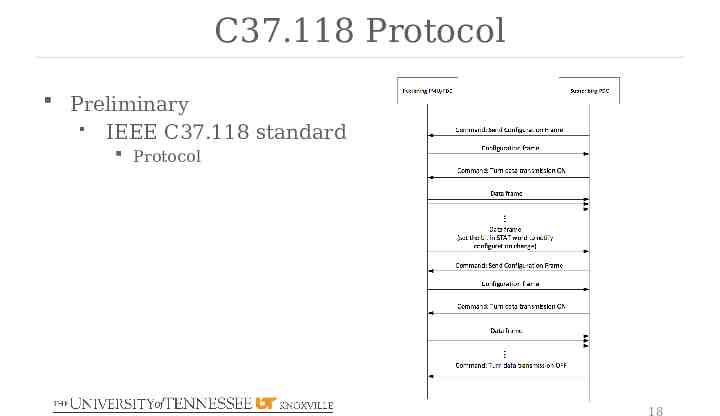
C37.118 Protocol Preliminary IEEE C37.118 standard Protocol 18
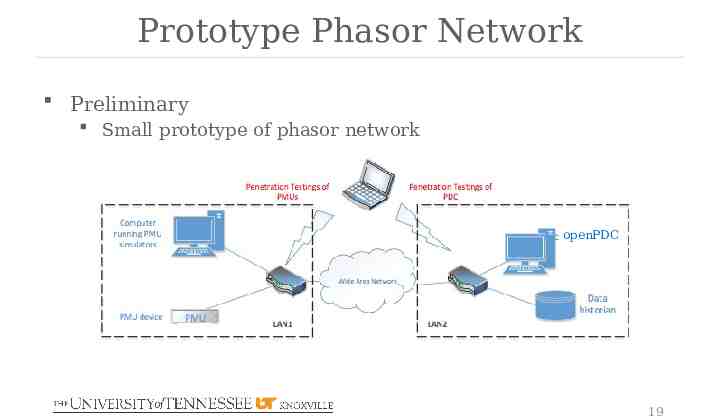
Prototype Phasor Network Preliminary Small prototype of phasor network openPDC 19
Penetration Testing Procedure What is penetration testing? Using the discovered vulnerabilities to exploit a system, network, or application We followed the procedure of penetration testing Formally, it is defined in PTES (penetration testing execution standard) Pre-engagement interactions Intelligence gathering Threat modeling Vulnerability analysis Exploitation Post-exploitation Reporting 20

Key Steps We focus on the key steps Reconnaissance Exploitation Exploit development -exploit: an exploit is the means by which an attacker, or pentester, takes advantage of a flaw within a system, an application, or a service. An attacker uses an exploit to attack a system in a way that results in a particular desired outcome that the developer never intended. 21

Reconnaissance Reconnaissance Collect information about the system under test Host discovering, operating system fingerprinting, packet sniffing Social engineering 22

Exploitation Vulnerability Exploitation Validate the possible vulnerabilities Automated Manual 23

Exploit Development Exploit development Develop practical attacks that exploits the vulnerabilities Serve as a proof to convince the asset owner their system is vulnerable Provide mitigation recommendations 24
Pentesting Techniques/Attacks Used Packet Sniffing Shared media network: listening to network traffic using NIC under promiscuous mode Switched network: MAC flooding or ARP poisoning to force the network traffic to be forwarded to the sniffer Wireshark Packet Injection Send packets to target network service. Packets appear to be legitimate but will interfere normal execution of the network services or applications. Scapy Fuzz testing (Fuzzing) Enumerate all possible inputs (emulate inputs that cross trust boundaries) Test the devices with frames carrying the enumerated inputs Identify inputs that cause the network service to behave abnormally or even crash Scapy 25
Common Pentesting Tools Metasploit Consists of modules: auxiliaries, exploits, payloads Kali Linux Contains more than 300 pentesting tools for various use cases (password cracking, wireless attack, ) Nmap Network mapper Contains a set of tools: Nmap, Nping, Zenmap 26
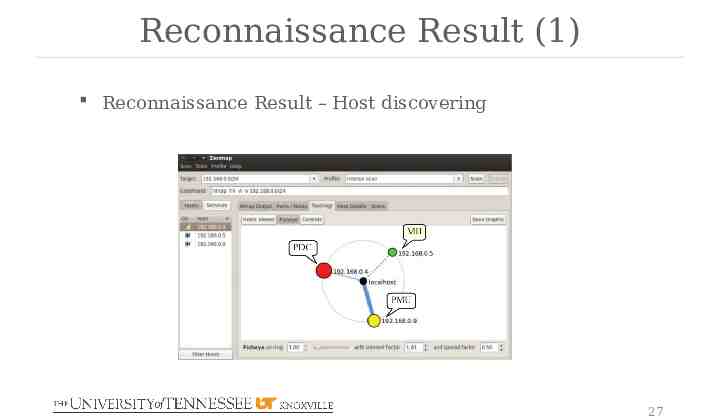
Reconnaissance Result (1) Reconnaissance Result – Host discovering 27
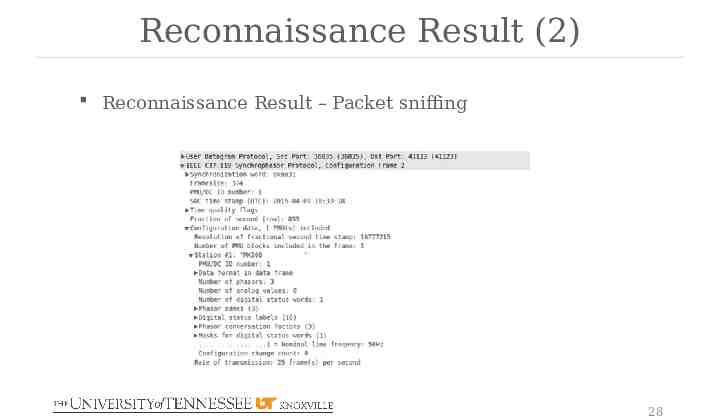
Reconnaissance Result (2) Reconnaissance Result – Packet sniffing 28

Reconnaissance Result Summary Summary of Reconnaissance Result Packets are not encrypted or integrity protected PMU/PDC ID Configuration information of the data frame Possible attacks: eavesdropping, packet modification Lack of user or message authentication mechanisms Possible attacks: packet injection, impersonation Stateful Protocol Possible attacks: Denial-of-Service (DoS) PDC stores and processes external inputs using SQL Possible attacks: SQL injection 29

Exploitation Vulnerability Exploitation Criteria for choosing vulnerabilities Easy to exploit High impact on the data security 30
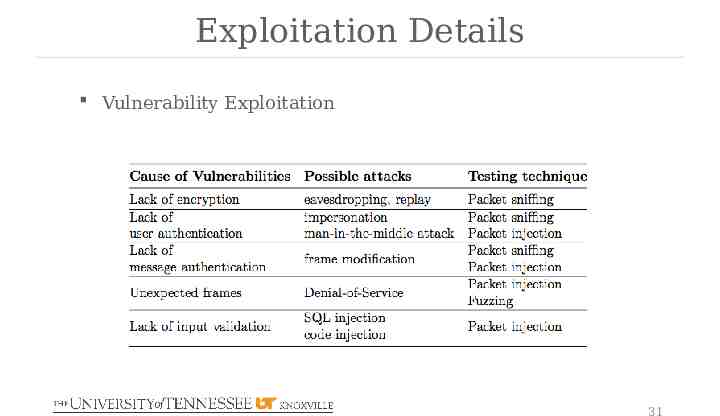
Exploitation Details Vulnerability Exploitation 31
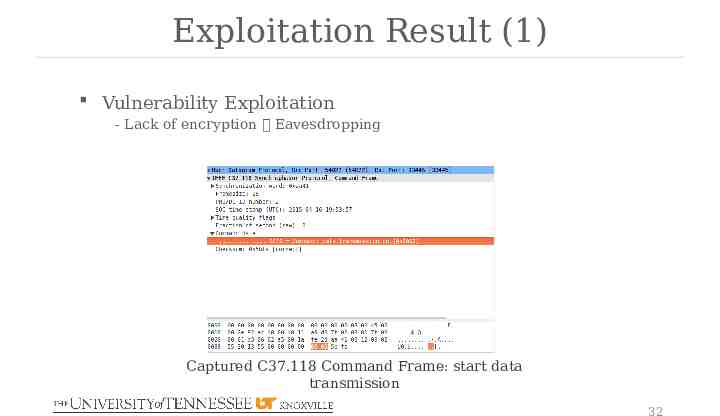
Exploitation Result (1) Vulnerability Exploitation - Lack of encryption Eavesdropping Captured C37.118 Command Frame: start data transmission 32
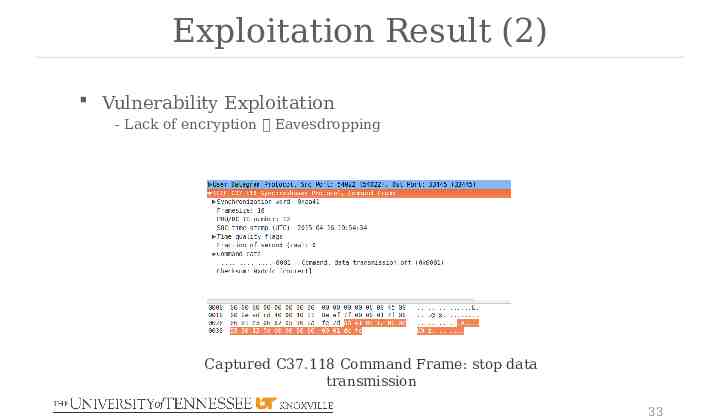
Exploitation Result (2) Vulnerability Exploitation - Lack of encryption Eavesdropping Captured C37.118 Command Frame: stop data transmission 33
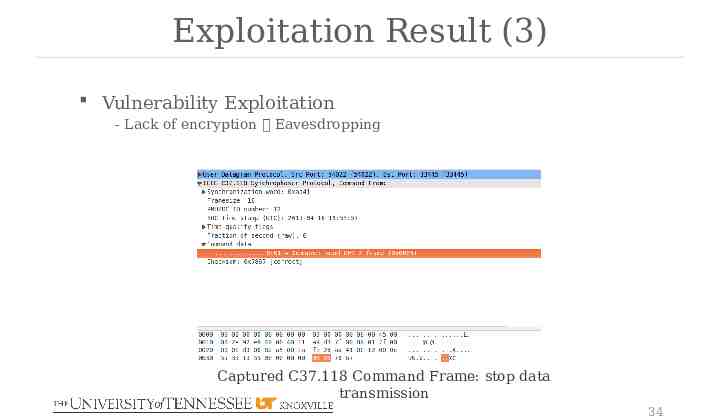
Exploitation Result (3) Vulnerability Exploitation - Lack of encryption Eavesdropping Captured C37.118 Command Frame: stop data transmission 34
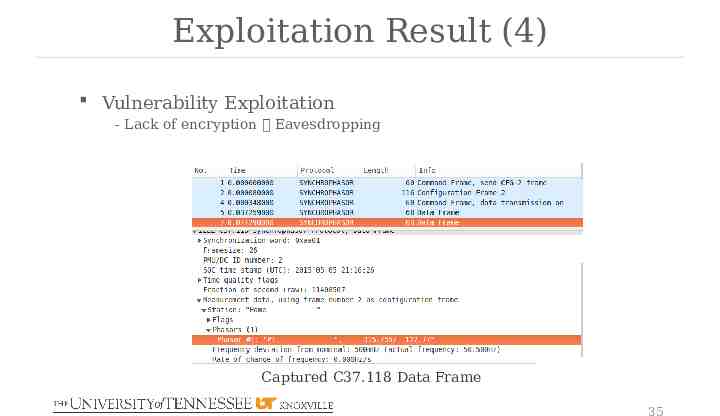
Exploitation Result (4) Vulnerability Exploitation - Lack of encryption Eavesdropping Captured C37.118 Data Frame 35

Exploitation Result (5) Vulnerability Exploitation Lack of user and message authentication frame spoofing Procedures Capture an authentic frame Duplicate the captured frame but change the bytes that indicate the actual commands, measurements, or configurations to the spoofing values. Change the time stamp of the frame Recalculate the checksum Inject the forged frames 36
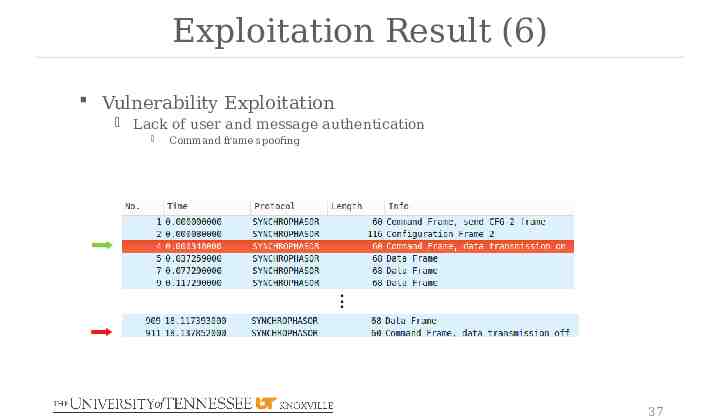
Exploitation Result (6) Vulnerability Exploitation Lack of user and message authentication Command frame spoofing . 37
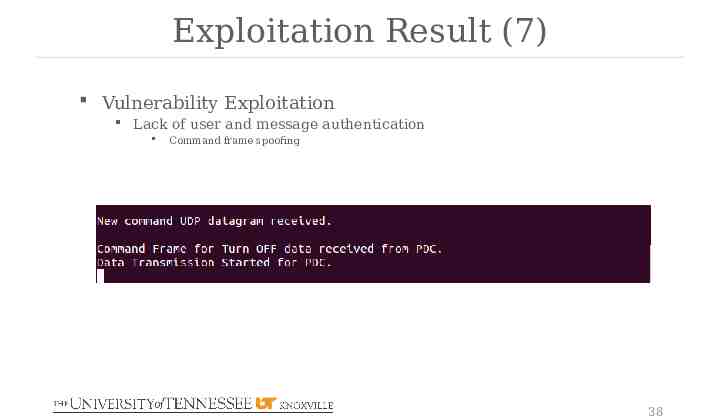
Exploitation Result (7) Vulnerability Exploitation Lack of user and message authentication Command frame spoofing 38
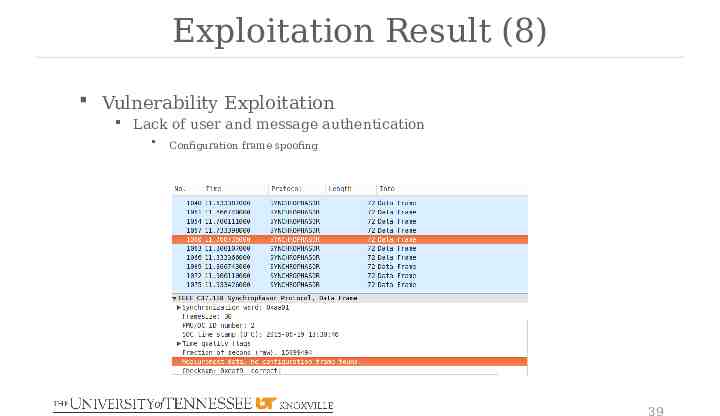
Exploitation Result (8) Vulnerability Exploitation Lack of user and message authentication Configuration frame spoofing 39
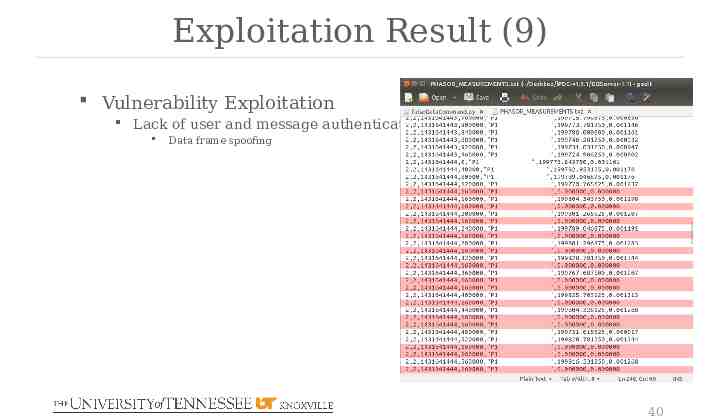
Exploitation Result (9) Vulnerability Exploitation Lack of user and message authentication Data frame spoofing 40

Exploitation Result (10) Vulnerability Exploitation Mishandling of unexpected frames To improve the efficiency of fuzzing SYNCHRONIZE word: fixed Checksum: recalculate 41
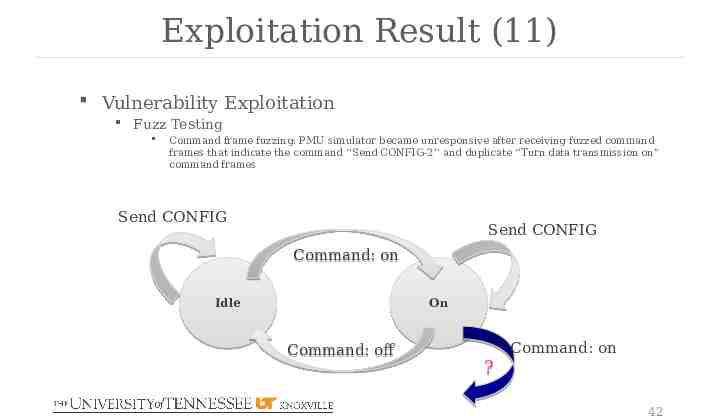
Exploitation Result (11) Vulnerability Exploitation Fuzz Testing Command frame fuzzing: PMU simulator became unresponsive after receiving fuzzed command frames that indicate the command ‘’Send CONFIG-2’’ and duplicate ‘’Turn data transmission on” command frames Send CONFIG Send CONFIG Command: on Idle On Command: off Command: on ? 42

Exploitation Result (12) Vulnerability Exploitation Fuzz Testing Command frame fuzzing: PMU simulator became unresponsive after receiving fuzzed frames that indicate the command ‘’Send CONFIG-2’’ and duplicate ‘’Turn data transmission on” command frames. Configuration frame fuzzing: passed Data frame fuzzing: passed 43

Exploitation Result (13) Vulnerability Exploitation Lack of input validation (SQL injection) SQL was used to manage the configurations of different registered PMU devices. SELECT * FROM MAIN CONFIG TABLE WHERE DEVICE ID PMU ID Number PMU ID Number is provided by external input and extracted from the received configuration frame If the PMU ID Number is specified as “2; DROP TABLE MAIN CONFIG TABLE” The SQL query becomes: SELECT * FROM MAIN CONFIG TABLE WHERE DEVICE ID 2; DROP TABLE MAIN CONFIG TABLE 44

Exploitation Result (14) Vulnerability Exploitation Lack of input validation (SQL injection) Passed SQL injection test Sanitize the input Use parameterized queries with strongly typed parameters SELECT * FROM MAIN CONFIG TABLE WHERE DEVICE ID PMU ID Number Input validation: ensured to be a 16-bit positive integer 45

Exploit Development Exploit development: Data stream hijacking Exploit vulnerabilities – command frame spoofing and data frame spoofing A practical attack that hijacks the data transmission stream Can be performed with a Scapy script Attackers taking over ongoing phasor phasor data transmission and sending falsified measurement data to the upstream PDC to mislead the user of the data. Demonstrated with WECC 179-bus system model 46
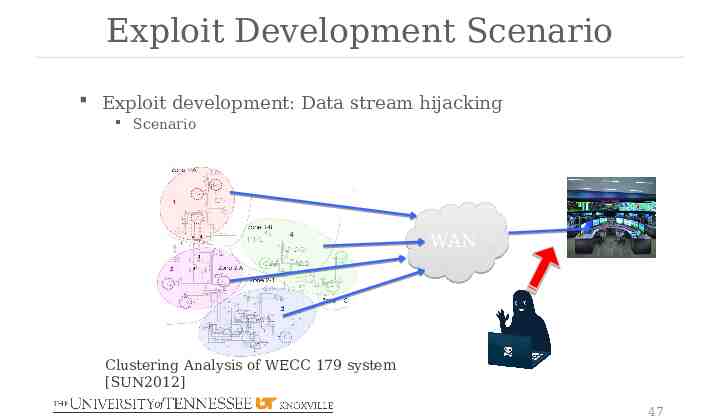
Exploit Development Scenario Exploit development: Data stream hijacking Scenario WAN Clustering Analysis of WECC 179 system [SUN2012] 47
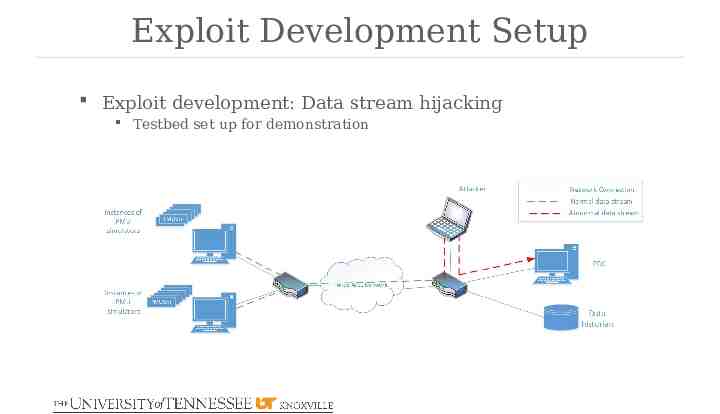
Exploit Development Setup Exploit development: Data stream hijacking Testbed set up for demonstration
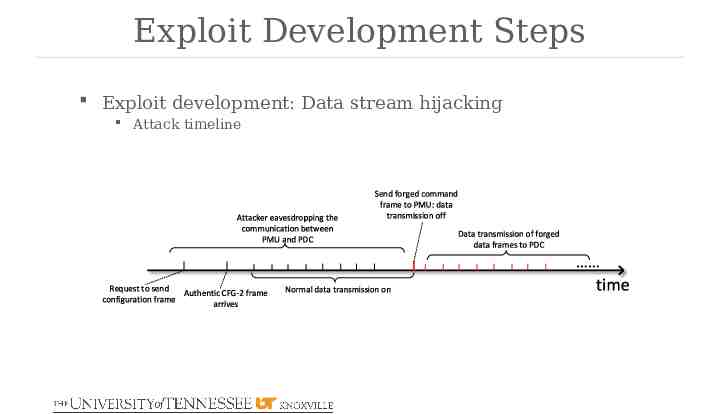
Exploit Development Steps Exploit development: Data stream hijacking Attack timeline
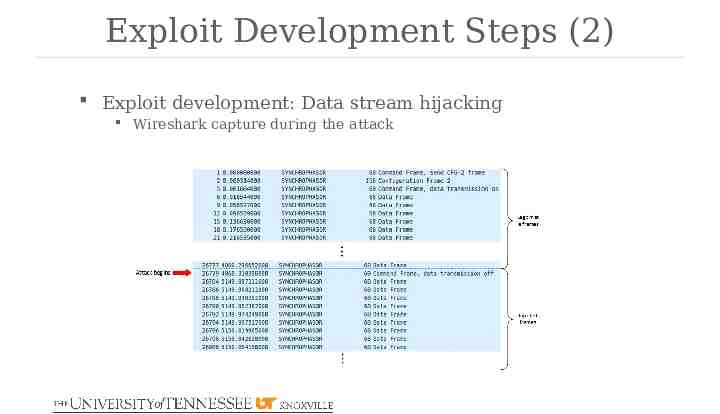
Exploit Development Steps (2) Exploit development: Data stream hijacking Wireshark capture during the attack
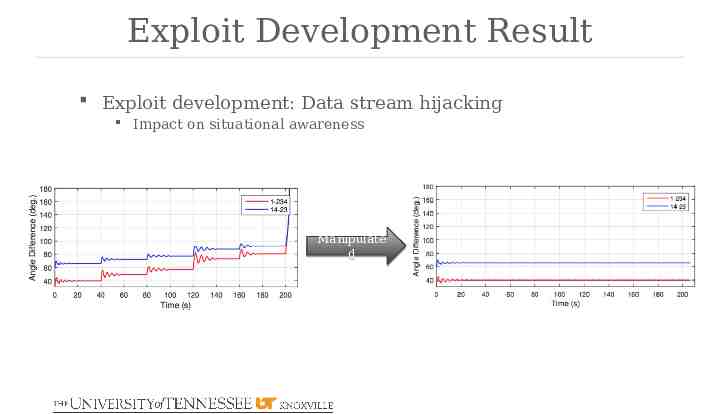
Exploit Development Result Exploit development: Data stream hijacking Impact on situational awareness Manipulate d

Defense and Countermeasures Security recommendations and best practices Use encryption (SSL/TLS, IPsec) Enable mutual authentication (X.509 certificates) Use message authentication code (SSL/TLS, IPsec) End-to-end encryption compatible devices should be preferred Thorough fuzz testing of all network interfaces Follow the guideline to avoid SQL injection attack Deploy an intrusion detection system Use redundant devices and communication infrastructure
Let’s Try Password Cracking with Kali Password cracking - some crackers claim 30% success rate Try with Kali - John the Ripper - Hashcat - and many more

Questions 54






