Virtualization Technology Introduction Argentina Software
42 Slides4.99 MB

Virtualization Technology Introduction Argentina Software Pathfinding and Innovation Intel Corporation 28 July 2008

Introduction Why is Intel giving this course? Argentina Software Development Center in Córdoba - Strong investment in developing areas of expertise Software Pathfinding and Innovation - Seeking the next technological move Strategic Area in Virtualization Technology - Evolving expertise in Virtualization Technology - Augment critical mass in this area

Introduction What are your expectations from this course? - Learn about virtualization technology - Academia research - Research in grids, cloud - Planning in participate in an Open Source community from virtualization - Business - Using virtualization in my datacenter - Planning to use it - ?

Introduction How is this course? Goal: - Foster virtualization technology, its usages, its capabilities and explore possible research and study projects Audience: - Beginners: provide a guide to start working/researching in Virtualization Technologies - Advanced: solidify concepts and go deep in VMM cases and Hardware assisted Virtualization Course Structure: - Virtualization Technology Introduction - Usages of Virtualization - VMMs / Hypervisors - Hardware Assisted Virtualization - Virtualization Technology Trends

Agenda Introduction Virtualization yesterday – virtualization today Challenges for x86 virtualization Approaches to server virtualization – Host-based server virtualization Full Virtualization Para-virtualization Hardware-assisted Virtualization Approaches to desktop virtualization
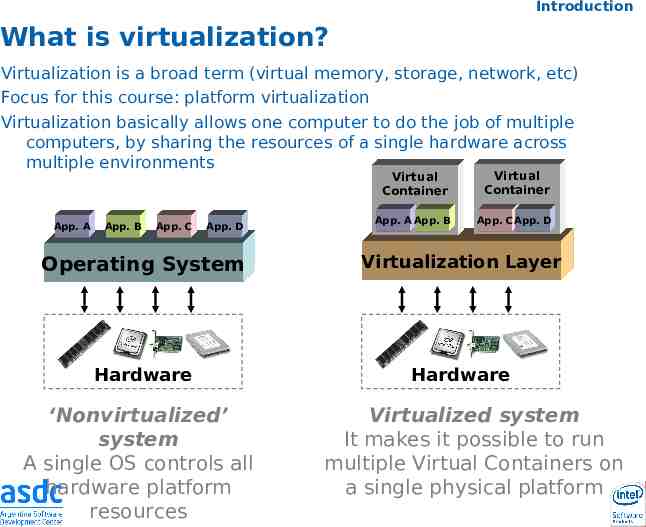
Introduction What is virtualization? Virtualization is a broad term (virtual memory, storage, network, etc) Focus for this course: platform virtualization Virtualization basically allows one computer to do the job of multiple computers, by sharing the resources of a single hardware across multiple environments App. A App. B App. C App. D Virtual Container Virtual Container App. A App. B App. CApp. D Operating System Virtualization Layer Hardware Hardware ‘Nonvirtualized’ system A single OS controls all hardware platform resources Virtualized system It makes it possible to run multiple Virtual Containers on a single physical platform

Introduction Virtualization Requirements Popek and Goldberg describe in their “Formal Requirements for Virtualizable Third Generation Architectures – 1974”: A Model of Third Generation Machines – Machine states: S (E, M, P, R) – Instructions classification Privileged instructions Control sensitive instructions Behavior sensitive instructions Properties for a Virtual Machine Monitor – Equivalence – Resource control – Efficiency Formal analysis described through 2 theorems

Introduction The VMM and the VM Equivalence Resource Control Efficiency Privileged instructions Control sensitive Behavior sensitive For any conventional third generation computer, a VMM may be constructed if the set of sensitive instructions for that computer is a subset of the set of privileged instructions A conventional third generation computer is recursively virtualizable if it is virtualizable and a VMM without any timing dependencies can be constructed for it.

The evolution of virtualization

How did it start? Server virtualization has existed for several decades – IBM pioneered more than 30 years ago with the capability to “multitask” The inception was in specialized, proprietary, high-end server and mainframe systems By 1980/90 servers virtualization adoption initiated a reduction – Inexpensive x86 hardware platforms – Windows/Linux adopted as server OSs Evolution of Virtualization

Computing Infrastructure – 2000 Evolution of Virtualization 1 machine 1 OS several applications Applications can affect each other Big disadvantage: machine utilization is very low, most of the times it is below than 25% App App App App App App App App X86 Windows XP X86 Windows 2003 X86 Suse X86 Red Hat 12% Hardware 15% Hardware 18% Hardware 10% Hardware Utilization Utilization Utilization Utilization

Virtualization again Evolution of Virtualization x86 server deployments introduced new IT challenges: Low server infrastructure utilization (10-18%) Increasing physical infrastructure costs (facilities, power, cooling, etc) Increasing IT management costs (configuration, deployment, updates, etc) Insufficient failover and disaster protection The solution for all these problems was to virtualize x86 platforms

Evolution of Virtualization Computing Infrastructure Virtualization It matches the benefits of high hardware utilization with running several operating systems (applications) in separated virtualized environments – Each application runs in its own operating system – Each operating system does not know it is sharing the underlying hardware with others App. A App. B App. C App. D X86 Windows XP X86 Windows 2003 X86 Suse Linux X86 Red Hat Linux X86 Multi-Core, Multi Processor 70% Hardware Utilization

Challenges for x86 virtualization

x86 virtualization challenge Challenges of x86 virtualization The IA-32 instruction set contains 17 sensitive, unprivileged instructions: – Sensitive register instructions: read or change sensitive registers and/or memory locations such as a clock register or interrupt registers: SGDT, SIDT, SLDT, SMSW, PUSHF, POPF – Protection system instructions: reference the storage protection system, memory or address relocation system: LAR, LSL, VERR, VERW, POP, PUSH, CALL, JMP, INT n, RET, STR, MOV However, x86 is a really big candidate to be virtualized, mainly for business facts
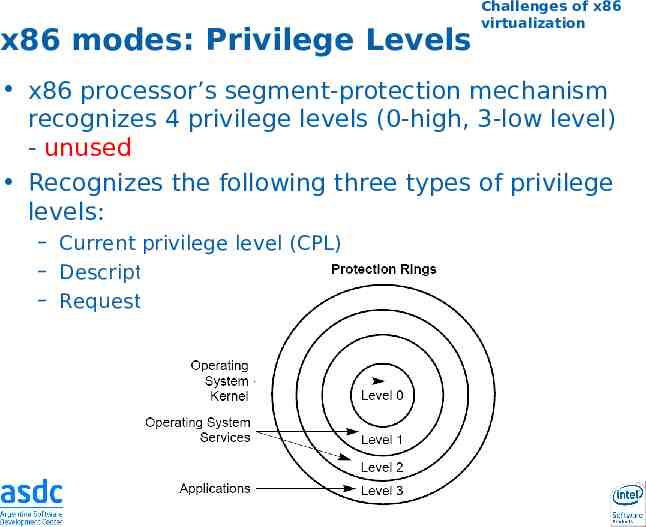
x86 modes: Privilege Levels Challenges of x86 virtualization x86 processor’s segment-protection mechanism recognizes 4 privilege levels (0-high, 3-low level) - unused Recognizes the following three types of privilege levels: – Current privilege level (CPL) – Descriptor privilege level (DPL) – Requested privilege level (RPL)

Challenges of x86 virtualization x86 virtualization challenge example: reading Segment Descriptors – x86 Code Segment and Stack Segment registers: The upper 14 bits of these registers contain the segment index and descriptor table selector. Lower 2 bits of CS and SS registers contains the CPL (Current Privilege Level). – Instructions that explicitly or implicitly access the CS/SS selector (including CALL, MOV from SS and POP SS) do not trap when executed from user mode. Executing POP SS the guest OS will be aware that it is not running on a privileged level when in ring 1 The Equivalence Property could be violated The Resource Control property is violated

Challenges of x86 virtualization X86 virtualization challenge example: reading Segment Descriptors (segment details)

Challenges of x86 virtualization x86 virtualization challenge example (2) GDT, LDT, IDT and TR: – For correct virtualization, these tables should be “shadowing” (the TR, GDTR, IDTR registers should point to VMM’s shadow tables) – Non privileged code can read from these registers (that means that reading these registers do not trap) The Equivalence Property could be violated Table 2-2. Summary of System Instructions - Software Developer’s Manual Vol 3A

Approaches to server virtualization

Server virtualization approaches Evolution of Software solutions 1st Generation: Full 2nd Generation: Paravirtualizatio virtualization n (Binary rewriting) – Software Based – VMware and Microsoft – Cooperative virtualization – Modified guest – VMware, Xen Virtual Machine Virtual Machine Dynamic Translation VM VM 3rd Generation: Silicon-based (Hardware-assisted) virtualization – Unmodified guest – VMware and Xen on virtualization-aware hardware platforms Virtual Machine Virtual Machine Operating System Hypervisor Hypervisor Hardware Hardware Hardware Time Virtualization Logic

All of the hardware is emulated including the CPU Two popular open source emulators are QEMU and Bochs App. A App. B Guest OS – The emulation layer talks to an operating system which talks to the computer hardware – The guest OS doesn't see that it is used in an emulated environment Virtual Machine 1st Generation offering of x86/x64 server virtualization Dynamic binary translation App. C Full Virtualization Server virtualization approaches Device Drivers Emulated Hardware Device Drivers Host OS Hardware

Full Virtualization - Advantages Server virtualization approaches The emulation layer – Isolates VMs from the host OS and from each other – Controls individual VM access to system resources, preventing an unstable VM from impacting system performance Total VM portability – By emulating a consistent set of system hardware, VMs have the ability to transparently move between hosts with dissimilar hardware without any problems It is possible to run an operating system that was developed for another architecture on your own architecture A VM running on a Dell server can be relocated to a HewlettPackard server

Full Virtualization - Drawbacks Server virtualization approaches Hardware emulation comes with a performance price In traditional x86 architectures, OS kernels expect to run privileged code in Ring 0 – However, because Ring 0 is controlled by the host OS, VMs are forced to execute at Ring 1/3, which requires the VMM to trap and emulate instructions Due to these performance limitations, paravirtualization and hardware-assisted virtualization were developed Application Application Ring 3 Operating System Ring 0 Traditional x86 Architecture Ring 3 Guest OS Ring 1 / 3 Virtual Machine Monitor Ring 0 Full Virtualization
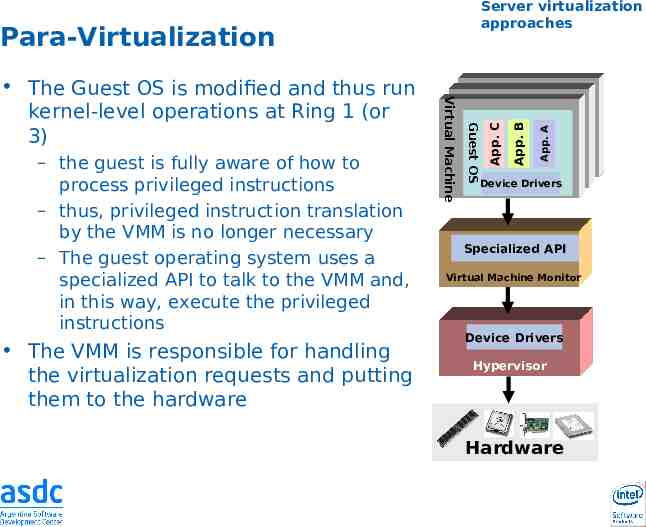
The VMM is responsible for handling the virtualization requests and putting them to the hardware App. A Guest OS – the guest is fully aware of how to process privileged instructions – thus, privileged instruction translation by the VMM is no longer necessary – The guest operating system uses a specialized API to talk to the VMM and, in this way, execute the privileged instructions Virtual Machine The Guest OS is modified and thus run kernel-level operations at Ring 1 (or 3) App. B Para-Virtualization App. C Server virtualization approaches Device Drivers Specialized API Virtual Machine Monitor Device Drivers Hypervisor Hardware

Para-Virtualization Server virtualization approaches Today, VM guest operating systems are paravirtualized using two different approaches: – Recompiling the OS kernel Paravirtualization drivers and APIs must reside in the guest operating system kernel You do need a modified operating system that includes this specific API, requiring a compiling operating systems to be virtualization aware – Some vendors (such as Novell) have embraced paravirtualization and have provided paravirtualized OS builds, while other vendors (such as Microsoft) have not – Installing paravirtualized drivers In some operating systems it is not possible to use complete paravirtualization, as it requires a specialized version of the operating system To ensure good performance in such environments, paravirtualization can be applied for individual devices For example, the instructions generated by network boards or graphical interface cards can be modified before they leave the virtualized machine by using paravirtualized drivers

App. A App. B Guest OS Virtual Machine The guest OS runs at ring 0 The VMM uses processor extensions (such as Intel -VT or AMD-V) to intercept and emulate privileged operations in the guest Hardware-assisted virtualization removes many of the problems that make writing a VMM a challenge The VMM runs in a more privileged ring than 0, a virtual -1 ring is created App. C Hardware-assisted virtualization Server virtualization approaches Device Drivers Specialized API Virtual Machine Monitor Device Drivers Hypervisor Hardware

Hardware-assisted virtualization Server virtualization approaches The hypervisor/VMM runs at Ring -1 – super-privileged mode VMX non-root VMX root

Hardware-assisted virtualization Server virtualization approaches Pros – It allows to run unmodified Oss (so legacy OS can be run without problems) Cons – Speed and Flexibility An unmodified OS does not know it is running in a virtualized environment and so, it can’t take advantage of any of the virtualization features – It can be resolved using paravirtualization partially

Approaches to desktop virtualization

Client virtualization approaches Extending the concept of virtualization for desktops Servers – Hosted virtualization - mainframes – VMMs / Bare Metal hypervisors – OS virtualization Desktops – Desktop virtualization – Server-side workspace virtualization – Client-side workspace virtualization Application virtualization – Application isolation – Application streaming

Desktop Virtualization A VMM or hypervisor running on a physical desktop Examples include: – – – – Use cases include: – – – Microsoft Virtual PC Parallels Desktop for Mac VMware Fusion WINE. Emulating Windows games on the Macintosh, Testing code inside VMs Underpinning client-side workspace virtualization Desktop hypervisors and VMMs don’t necessarily scale to meet enterprise needs; that’s why most of the providers have server products as well Desktop virtualization approaches
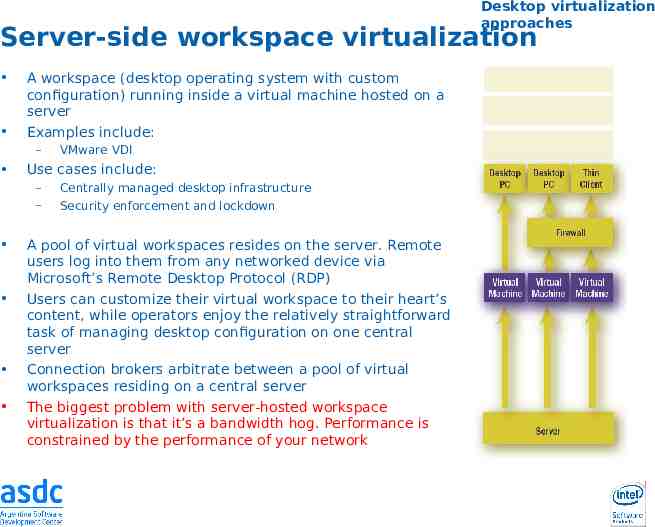
Desktop virtualization approaches Server-side workspace virtualization A workspace (desktop operating system with custom configuration) running inside a virtual machine hosted on a server Examples include: – Use cases include: – – VMware VDI Centrally managed desktop infrastructure Security enforcement and lockdown A pool of virtual workspaces resides on the server. Remote users log into them from any networked device via Microsoft’s Remote Desktop Protocol (RDP) Users can customize their virtual workspace to their heart’s content, while operators enjoy the relatively straightforward task of managing desktop configuration on one central server Connection brokers arbitrate between a pool of virtual workspaces residing on a central server The biggest problem with server-hosted workspace virtualization is that it’s a bandwidth hog. Performance is constrained by the performance of your network

Desktop virtualization approaches Client-side workspace virtualization A workspace (desktop operating system with custom configuration) running inside a virtual machine hosted on a desktop Examples include: – – Use cases include: – – – Kidaro Managed Workspace Sentillion vThere Secure remote access Protection of sensitive data for defense, healthcare industries Personal computer running corporate desktops remotely A virtual workspace is served out to execute on the client device Centralizes management Its big advantage over other models is the security and isolation of data and logic on the client It’s the right model for organizations that need to ensure the security of environments served to remote users – – Defense contractors Healthcare providers

Application Isolation An application packaged with its own virtual copies of the operating system resources it might otherwise need to change (registries, file systems, libraries) Examples include: – – Use cases include: – – Preventing DLL hell Sandboxing desktop applications for secure execution Applications use a virtual registry (Thinstall) and file system embedded in the package with the application – Thinstall Trigence These extra tools insulate applications from changes to and incompatibility with the underlying desktop operating system Mostly in Windows, although Linux and Solaris as well Drawback: increased footprint of the application package and the correspondingly greater memory requirements Desktop virtualization approaches
Application Streaming Just-in-time delivery of a server-hosted application to the desktop, such that the desktop application can execute before the entire file has been downloaded from the server Examples include: – – Use cases include: – Managing the number of instances of running applications, in the case of license constraints Superset of Application Isolation, including a delivery method and an execution mode – AppStream Microsoft SoftGrid You stream the application code to the desktop, where it runs in isolation No full PC environment, just the application, so you have to provide a workspace – Requires to maintain the client-side operating system and ensuring compatibility. This may be why application streaming, which has been around for a long time (AppStream has already raised over 50m in venture capital), has not really lived up to its early hype. Desktop virtualization approaches

Periodic table of Virtualization Extracted from Virtualization II: Desktops and applications are next – the 451 group

Day wrap-up Requirements for HW Architecture Virtualization – Popek and Goldberg Evolution for virtualization: from mainframes to x86 architecture due to business reasons Challenges around x86 virtualization - ISA doesn’t comply with P&G Server virtualization approaches – Full Virtualization – Paravirtualization – Hardware Assisted Virtualization Client virtualization approaches – Desktop virtualization – Server-side workspace virtualization – Client-side workspace virtualization Application virtualization – Application isolation – Application streaming

Questions?

Backup

References http://en.wikipedia.org/wiki/Platform virtualization http://en.wikipedia.org/wiki/Popek and Goldberg virtualization requi rements http://www.vmware.com/virtualization/ http://www.vmware.com/overview/history.html Formal Requirements for Virtualizable Third Generation Architectures – 1974 - Popek (UCLA) and Goldberg (Honeywell Information Systems and Harvard University) Virtualization II: Desktops and applications are next – the 451 group

Contacts Argentina Software Pathfinding and Innovation team from Virtualization Technology: Guillermo Colsani: [email protected] Gisela Giusti: [email protected] Pablo Pássera: [email protected] Duilio Protti: [email protected]






