VA Research Data Security and Privacy presented by Ellen Graf RCO,
27 Slides148.50 KB

VA Research Data Security and Privacy presented by Ellen Graf RCO, Cincinnati VAMC

What is VA Research and Sensitive VA Research Data? VA research is any research that has been approved (or requires approval) by a VA Research and Development (R&D) Committee. Generally this includes any research conducted with VA resources, including funds, staff time, equipment, or space. VA research data consist of information that has been collected for, used in or derived from the conduct of VA research. VA sensitive information is defined in VA Directive 6504 as all Department data, on any storage media or in any form or format, which requires protection due to the risk of harm that could result from inadvertent or deliberate disclosure, alteration, or destruction of the information. This term includes information whose improper use or disclosure could adversely affect the ability of an agency to accomplish its mission, proprietary information, or records about individuals requiring protection under various confidentiality provisions such as the Privacy Act or the Health Insurance Portability and Accountability Act (HIPAA) Privacy Rule. It also includes information that can be withheld under the Freedom of Information Act (FOIA).
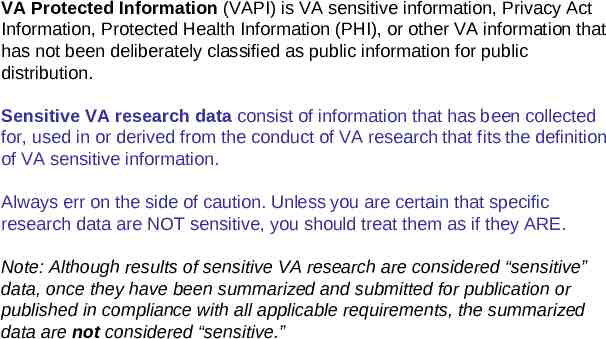
VA Protected Information (VAPI) is VA sensitive information, Privacy Act Information, Protected Health Information (PHI), or other VA information that has not been deliberately classified as public information for public distribution. Sensitive VA research data consist of information that has been collected for, used in or derived from the conduct of VA research that fits the definition of VA sensitive information. Always err on the side of caution. Unless you are certain that specific research data are NOT sensitive, you should treat them as if they ARE. Note: Although results of sensitive VA research are considered “sensitive” data, once they have been summarized and submitted for publication or published in compliance with all applicable requirements, the summarized data are not considered “sensitive.”

As a member of the Research Community it is quite simply our DUTY to protect the sensitive research data of the Veterans who have served and protected our country and who now volunteer as Research Subjects!

WHY ARE WE AT RISK? Approximately one in 10 laptop computers is stolen (Gartner Group, 2001) Hospitals and universities are particularly common targets for theft of laptops and other portable media , thus. We need to be vigilant in the storage, use, security and confidentiality of data and for the privacy of the research subjects

The loss of data: Violates veterans’ and employees privacy. Exposes them to the possibility of identity theft. Possibly resulting in risk to their financial security, employability, insurability and reputation. Instills a lack of trust in the VA system.

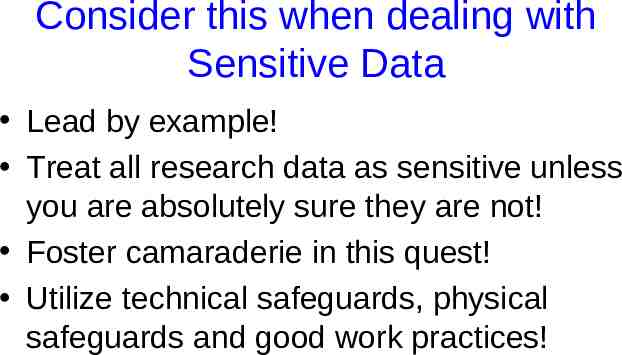
Consider this when dealing with Sensitive Data Lead by example! Treat all research data as sensitive unless you are absolutely sure they are not! Foster camaraderie in this quest! Utilize technical safeguards, physical safeguards and good work practices!

VHA Handbook 1605.1 Utilizing VHA Handbook 1605.1 will lead to compliance with the privacy requirements set forth in all six Federal privacy & confidentiality statures and regulations regarding the – – – – COLLECTION USING SHARNG or DISCLOSING of individually identifiable information
Data Collection & Use Collect the minimum information needed to conduct the research. Use data as outlined by the protocol and signed authorization. Never re-use or share data without the appropriate approvals

Sharing or Disclosing Information Disclosure of individually identifiable information from official VHA records is acceptable only when: The VHA has first obtained the signed, written (HIPAA) authorization of the individual, or Waiver of HIPAA authorization is approved by the Privacy Board.

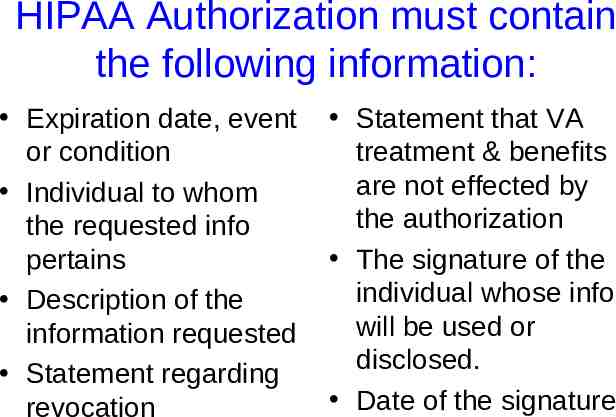
HIPAA Authorization must contain the following information: Expiration date, event or condition Individual to whom the requested info pertains Description of the information requested Statement regarding revocation Statement that VA treatment & benefits are not effected by the authorization The signature of the individual whose info will be used or disclosed. Date of the signature

Waiver of HIPAA Authorization Must be approved by the facility IRB or Privacy Board. Approval is based on 3 criteria: – The use or disclosure must involve no more that minimal risk to the individual – The research cannot practicably be conducted without the waiver – The research cannot be performed without access to, and use of, the protected health information
Data Use Agreements (DUA) A written DUA may be obtained when data will be disclosed outside of the VHA for non-VA research. The DUA must include the following: – – – – – What and how data may be used How data will be stored & secured Who may access data & by what legal authority Disposition of data after the termination of research Actions required if data are lost or stolen

Certificates of Confidentiality Under Federal law, researchers must obtain an advance grant of confidentiality from the NIH, known as a Certificate of Confidentiality, to protect data pertaining to sensitive issues such as illegal behavior, alcohol or drug use, or sexual practices or preferences.

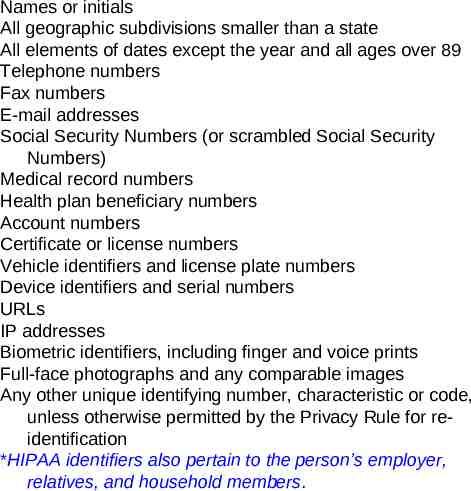
What About De-identified Data? Is your data truly de-identified, thus containing none of the 18 types of identifiers as outlined by VHA Handbook 1605.1, Appendix B? Does your data involve the removal of all information that would identify the individual or would be used to readily ascertain the identity of the individual?

Can you actually recite the 18 types of identifiers that MUST be removed to assure that the data is DE-IDENTIFIED ?

Names or initials All geographic subdivisions smaller than a state All elements of dates except the year and all ages over 89 Telephone numbers Fax numbers E-mail addresses Social Security Numbers (or scrambled Social Security Numbers) Medical record numbers Health plan beneficiary numbers Account numbers Certificate or license numbers Vehicle identifiers and license plate numbers Device identifiers and serial numbers URLs IP addresses Biometric identifiers, including finger and voice prints Full-face photographs and any comparable images Any other unique identifying number, characteristic or code, unless otherwise permitted by the Privacy Rule for reidentification *HIPAA identifiers also pertain to the person’s employer, relatives, and household members.

Limited Data Sets Exclude certain direct identifiers that apply to: – – – – The individual The individual’s relatives The individual’s employers The individual’s household members They may contain: – – – – City, state, ZIP Elements of a date and other numbers Characteristics or codes not used as direct identifiers Identifiable information, such as scrambled SS#s.
Coded Data Coding consists of labeling info with a code that : – Does not include any patient identifiers – Is not derived from or related to the 18 HIPAA identifiers – Cannot be translated so as to identify the individual If data are coded, the key to linking the code with these identifiers must be stored within the VA, but it should not be stored with the coded data.

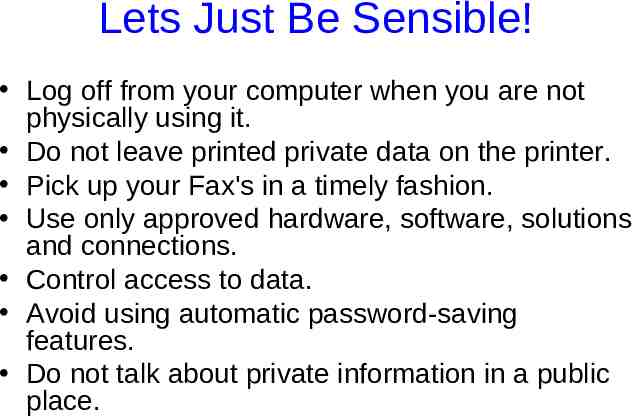
Lets Just Be Sensible! Log off from your computer when you are not physically using it. Do not leave printed private data on the printer. Pick up your Fax's in a timely fashion. Use only approved hardware, software, solutions and connections. Control access to data. Avoid using automatic password-saving features. Do not talk about private information in a public place.

Steps We Have Taken to Assure Compliance with Regulations Additional Medical Center Memorandums to include – Loaning of Research IT Equipment – Research Management of Laptops – Security of PHI/sensitive info held by Researchers
Additional Steps Addition of the Privacy Officer to the R&D Committee. Questions regarding data security and privacy asked at the pre-consenting interview held with the PI and coordinator. More stringent exiting procedures. Annual PI Certification and Data Security Checklist. Annual certification of compliance by MCD.

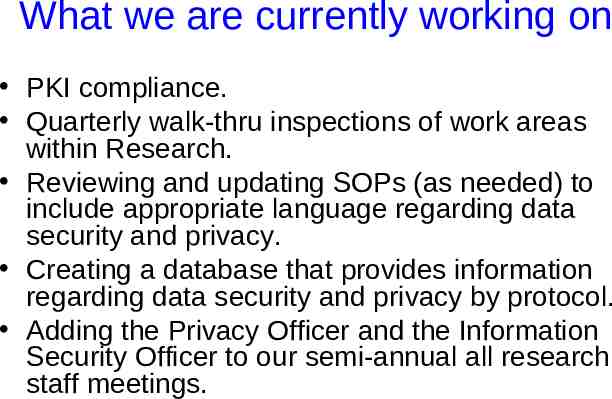
What we are currently working on PKI compliance. Quarterly walk-thru inspections of work areas within Research. Reviewing and updating SOPs (as needed) to include appropriate language regarding data security and privacy. Creating a database that provides information regarding data security and privacy by protocol. Adding the Privacy Officer and the Information Security Officer to our semi-annual all research staff meetings.

Final Words of Wisdom Err on the side of caution! Keep regulations at hand, it is extremely difficult to remember everything! Work closely with your Privacy Officer & the Information Security Officer! Ask for assistance from VACO! Steadily work to improve and modify as necessary in a timely fashion! Be positive and optimistic nothing hinders the process more than pessimism! Keep your Medical Center Director up to date with any new information or process. Be an example!
IT IS A PRIVLEDGE TO NOW SERVE THEM!