Survey on Cloud Computing Risk and Security Issues Mahyar Taheri
19 Slides1.56 MB

Survey on Cloud Computing Risk and Security Issues Mahyar Taheri Tehrani Department of Computer Science Email : [email protected] Supervisor : Mr. Hadi Salimi Advanced Topics in Information Systems Mazandaran University of Science and Technology February 4, 2011

Definition of Cloud Computing What is Cloud Computing. Cloud Computing essential characteristics. The services of Cloud Computing. The delivery models of Cloud Computing. 2/19
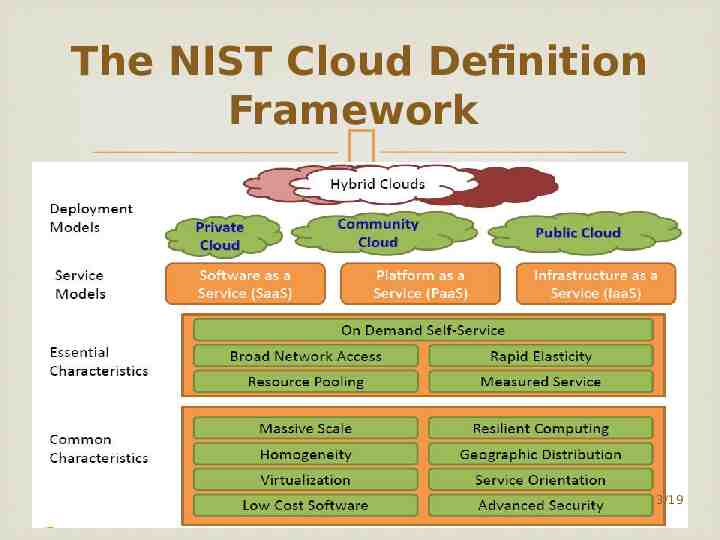
The NIST Cloud Definition Framework 3/19
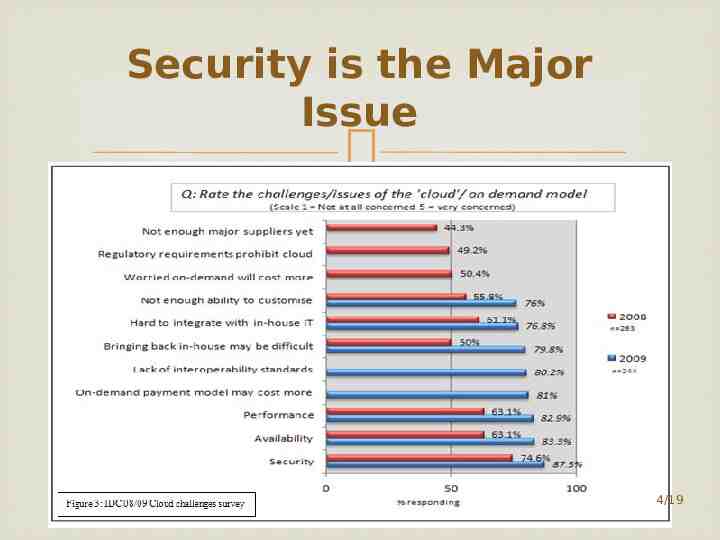
Security is the Major Issue 4/19

Why security is important Cloud Computing targeted to provide better utilization of resources using virtualization techniques. Cloud Computing moves the application software and databases to the large data centers, where the management of the data and services are not trustworthy. Some security challenges: virtualization vulnerabilities, web application vulnerabilities, physical access issues, identity and credential management, data verification, integrity, confidentiality, loss and theft. 5/19
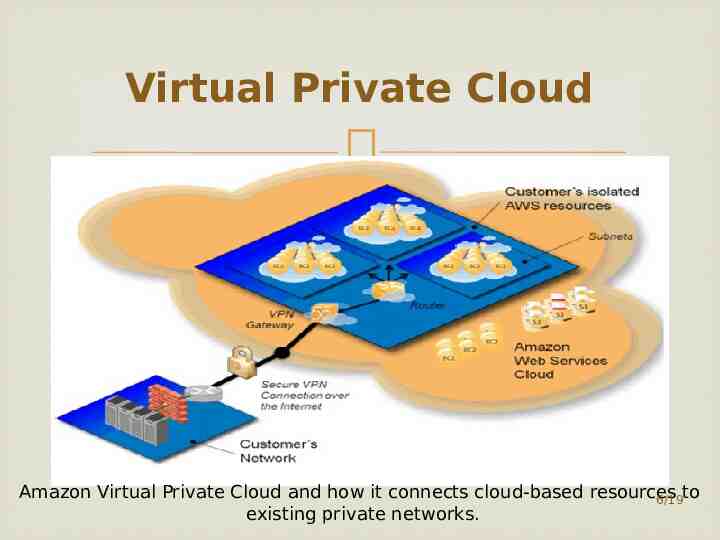
Virtual Private Cloud Amazon Virtual Private Cloud and how it connects cloud-based resources to 6/19 existing private networks.

Cloud Computing Risk Issues Privacy Data and information on cloud are Secure!!? Guarantee of privacy. Hacker. Control and monitor lawfully or unlawfully. secret NSA program, working with AT&T, and Verizon Information preservation Could cloud to keep data and information forever? Provide huge server for keeping and preservation of data. Backup data and information of user. 7/19

Cloud Computing Risk Issues Boycott International politics. Availability and performance Salesforce.com not available at March 11, 2010. Amazon services not available for tow hours. Recovery Time Objectives(RTO). Recovery Point Objectives(RPO). 8/19

Security issues in SaaS Data security Network security Data locality Data segregation Data access Data breaches Backup 9/19

Data security Data is stored outside the enterprise boundary. Strong encryption techniques for data security. Malicious users can exploit weaknesses in security. 10/19
Network security All data flow over the network needs to be secured. Use of strong network traffic encryption techniques. Amazon Web Services (AWS), provides protection against traditional network security. 11/19

Data locality Customer must know where the data stored. Why is locality of data importance? data privacy laws in various countries are different. A secure SaaS must providing reliability on the location of the data. 12/19

Data access Data access issue is related to security policies provided to the users while accessing the data. The SaaS model must be flexible to incorporate specific policies put forward by the organization. 13/19

Security issues in IaaS The security responsibilities of both the provider and the consumer. Physical security of infrastructure and disaster management is of utmost importance. Virtualization vulnerability Virtualization is one of the main components of a Cloud. Running on the same physical machine are isolated from each other is a major task of virtualization. Current VMMs do not offer perfect isolation. 14/19

Virtualization vulnerability example Microsoft Virtual PC and Microsoft Virtual Server could allow a guest operating system user to run code on the host or another guest operating system. vulnerability in Xen caused due to an input validation error in tools/pygrub/src/GrubConf.py. 15/19

Current security solutions Several groups and organization are interested in developing security solutions and standards for the Cloud. European Network and Information Security Agency (ENISA), Cloud Security Alliance (CSA), National Institute of Standards and Technology (NIST), Centre for the Protection of National Infrastructure (CPNI), and, etc. 16/19

Conclusion There are extreme advantages in using aCloudbased. Customers should research about Cloud risk and security issues of Cloud infrastructures that vendors offer. Customers should consider how to continue their business. Public, private or virtual private Clouds. 17/19

Refrence C. Wang, et al., "Ensuring data storage security in Cloud Computing," 2009, pp. 1-9. A. Seccombe, et al., "Security guidance for critical areas of focus in Cloud Computing, v2.1," CSA (Cloud Security Alliance), USA. Disponible en, vol. 1, 2009. V. Choudhary, "Software as a service: Implications for investment in software development," 2007, p. 209a. C. Attanasio, "Virtual machines and data security," 1973, pp. 206-209. [19] Amazon. (10 December 2009). Elastic Compute Cloud(EC2). Available: http://aws.amazon.com/ec2/ 18/19

Questions? 19/19