Solutions For Denial of Service (DoS) Minimization Ian Quinn APRICOT
34 Slides786.50 KB

Solutions For Denial of Service (DoS) Minimization Ian Quinn APRICOT 2001 Kuala Lumpur, Malaysia

Agenda The Impact Of Denial of Service (D0S) Detecting And Minimising DoS SMURF Attacks SYN Attacks Infrastructure Requirements Proactive Measures
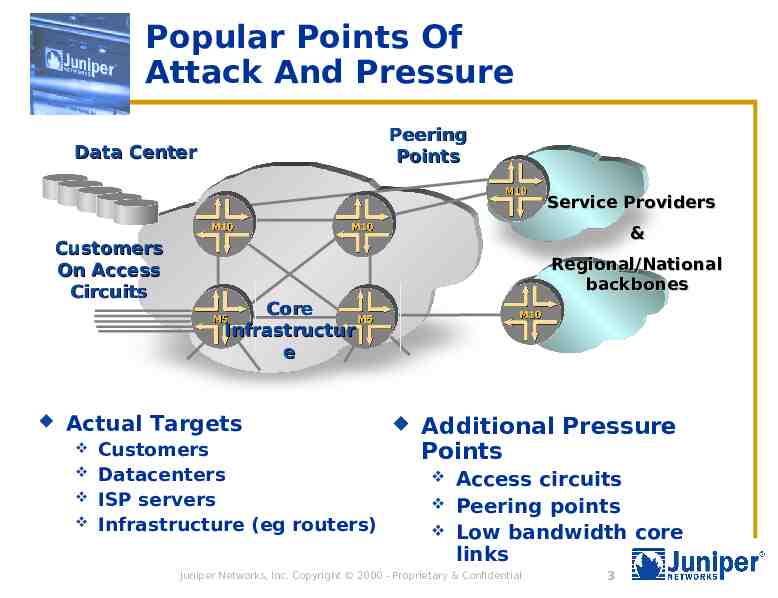
Popular Points Of Attack And Pressure Peering Points Data Center Service Providers Customers On Access Circuits & Regional/National backbones Core Infrastructur e Actual Targets Customers Datacenters ISP servers Infrastructure (eg routers) Additional Pressure Points Access circuits Peering points Low bandwidth core links Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 3

What Are The Threats To A Service Provider Disruption Desirable Of Customer Networks to be able to assist customer Consumption Of Bandwidth Lower bandwidth links susceptible Often a big problem in Asia Pacific Network Stability Frequently a problem for older platforms Related to additional workload, and performance headroom All Affect Service Delivered Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 4
Emergence Of Distributed Denial Of Service (DDoS) Targeted largely at servers Harnessed networks of compromised machines Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 5
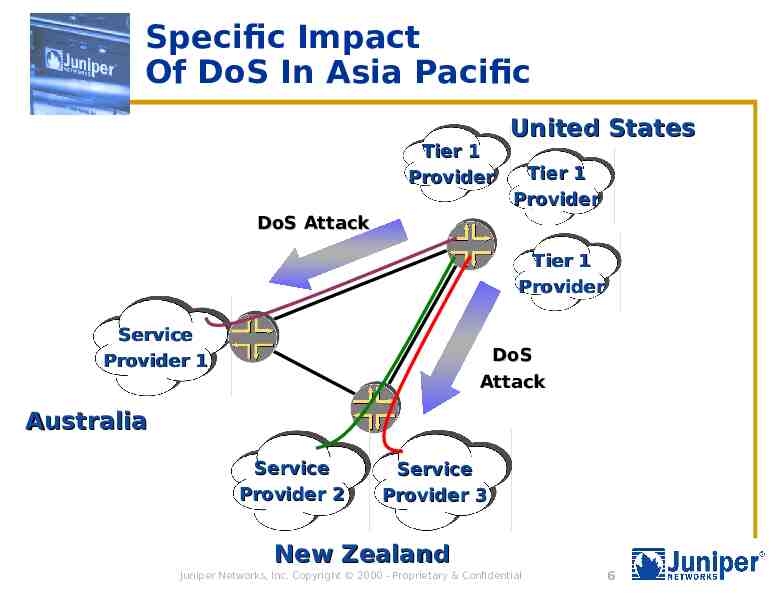
Specific Impact Of DoS In Asia Pacific Tier 1 Provider United States Tier 1 Provider DoS Attack Tier 1 Provider Service Provider 1 DoS Attack Australia Service Provider 2 Service Provider 3 New Zealand Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 6

Impacts Of Security Incidents Customer service levels Internet access, web farms, ecommerce Especially if impact is repeated Support overhead Especially in isolating and blocking Denial of Service (DoS) attacks Service provider reputation Service Level Agreement (SLA) breaches SLA increasingly being offered Multi-service networks change the game STRESS!!! Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 7

Agenda The Impact Of Denial of Service (D0S) Detecting And Minimising DoS SMURF Attacks SYN Attacks Infrastructure Requirements Proactive Measures
Generic Approach To DoS Attacks Use statistics to detect attack in progress Use sampling or logging to capture traffic for analysis Isolate attack Attack type Source (often difficult or impractical) Destination Block or traceback the attack using filters Filter on destination and protocols Drop traffic or rate limit Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 9
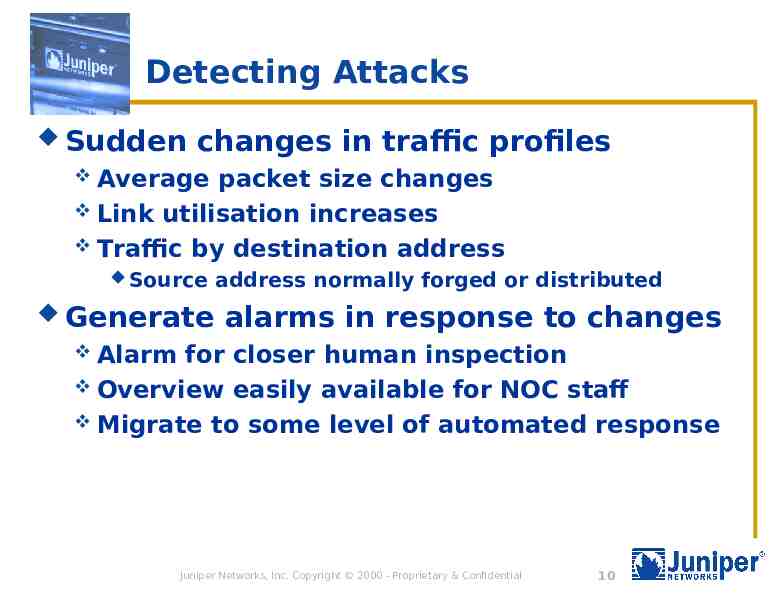
Detecting Attacks Sudden changes in traffic profiles Average packet size changes Link utilisation increases Traffic by destination address Source Generate address normally forged or distributed alarms in response to changes Alarm for closer human inspection Overview easily available for NOC staff Migrate to some level of automated response Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 10

Complicating Factors With DoS Distinguishing DoS traffic from normal usage Forged source address More difficult to isolate and track attack Distributed attacks Attack could enter from multiple points Difficult to track back and shut down Blocking attacks that match valid traffic Disruption of normal service Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 11

Agenda The Impact Of Denial of Service (D0S) Detecting And Minimising DoS SMURF Attacks SYN Attacks Infrastructure Requirements Proactive Measures

SMURF Attacks The attacker sends a broadcast ping to an intermediary subnet using a forged source address The forged source address belongs to the target of the attack The result is an over-burdened CPU on the target server and over-utilized access trunks Intermediary Hosts (Several on Same Subnet) Data Server Attacker’s Work Station Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 13
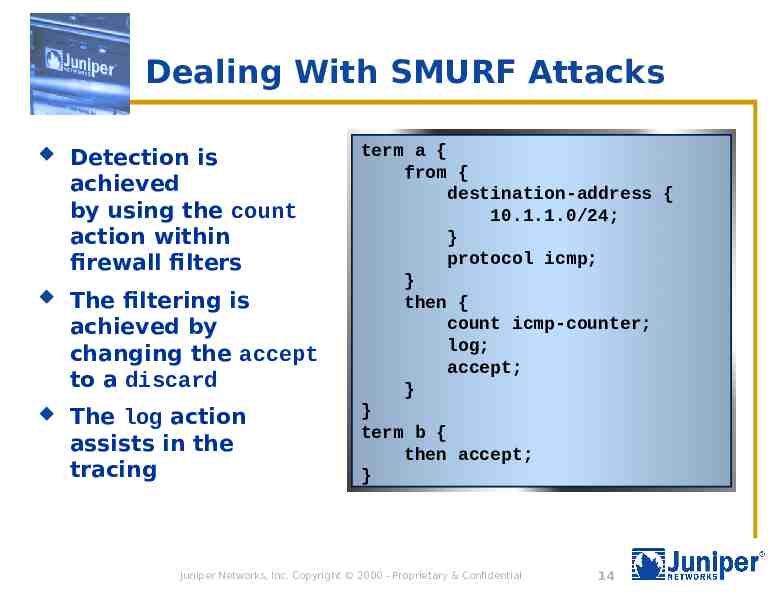
Dealing With SMURF Attacks Detection is achieved by using the count action within firewall filters The filtering is achieved by changing the accept to a discard The log action assists in the tracing term a { from { destination-address { 10.1.1.0/24; } protocol icmp; } then { count icmp-counter; log; accept; } } term b { then accept; } Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 14

Dealing With SMURF Attacks Once the filter is applied to the interface, you can view the firewall counters If the ICMP counter increments quickly, an attack is underway unit 0 { family inet { filter { output count-icmp; } address 10.10.10.1/24; } } root@ballpark show firewall Filter/Counter Packet count Byte count count-icmp icmp-counter 78516 Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 5025000 15

Dealing with SMURF Attacks Stopping the attack is a matter of changing the accept action to a discard Discarding all ICMP traffic to the targeted host at the router closest to that host is not most efficient Bandwidth resources are still wasted Also apply this filter at AS boundaries where the targeted host resides Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 16

Where Did that SMURF Come From? Finding the bad guy is not easy View show firewall log to see source addresses of ICMP traffic; however, this step identifies only the intermediary, not the attacker Contact the owner of the intermediary and ask him to Disable broadcast pings Track back the pings to the attacker Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 17

Agenda The Impact Of Denial of Service (D0S) Detecting And Minimising DoS SMURF Attacks SYN Attacks Infrastructure Requirements Proactive Measures

SYN Attacks Attacker The attacker sends a stream of SYNs to the server under attack using a forged source address The forged source address is unused by anyone The result is overburdened CPU and/or memory exhaustion on the target server and overutilized access trunks Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential Data Server 19

SYN Attacks During a SYN attack, the SYN-ACK never reaches the client Sockets remain open on the server Correct Three-way Handshake Client Server SYN-------------------- The result is --------------------SYN-ACK over-burdened CPU and/or memory ACK-------------------- exhaustion on the target server, and overutilized access trunks Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 20
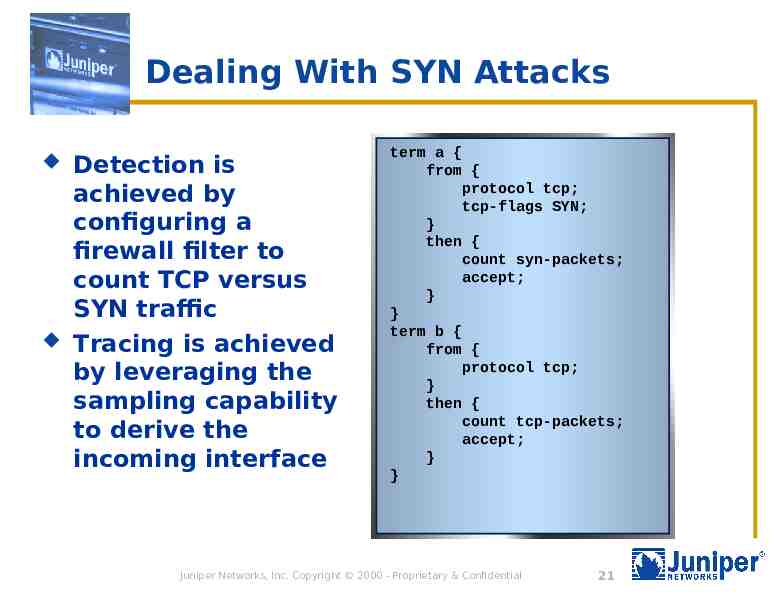
Dealing With SYN Attacks Detection is achieved by configuring a firewall filter to count TCP versus SYN traffic Tracing is achieved by leveraging the sampling capability to derive the incoming interface term a { from { protocol tcp; tcp-flags SYN; } then { count syn-packets; accept; } } term b { from { protocol tcp; } then { count tcp-packets; accept; } } Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 21

Details of the Detection Process Once the filter is applied to the interface, you can view the counters If the ratio of SYN to TCP is high ( 1:5), a SYN attack is underway unit 0 { family inet { filter { output detect-syn-attack; } address 10.10.10.1/24; } root@ballpark# run show firewall Filter/Counter detect-syn-attack tcp-packets syn-packets Packet count Byte count 289144 56388 Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 86743200 16916640 22

Dealing with SYN Attacks Stopping the attack is usually not an option. If the attack is not distributed, you can change the accept action to discard and apply to the ingress of all AS boundary routers If the attack is distributed, filtering SYNs also effectively shuts down the server Tracing the attack requires co-operation with peers of the network under attack Examining the sampled output reveals incoming interface Repeat this process until the source is found Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 23

Agenda The Impact Of Denial of Service (D0S) Detecting And Minimising DoS SMURF Attacks SYN Attacks Infrastructure Requirements Proactive Measures
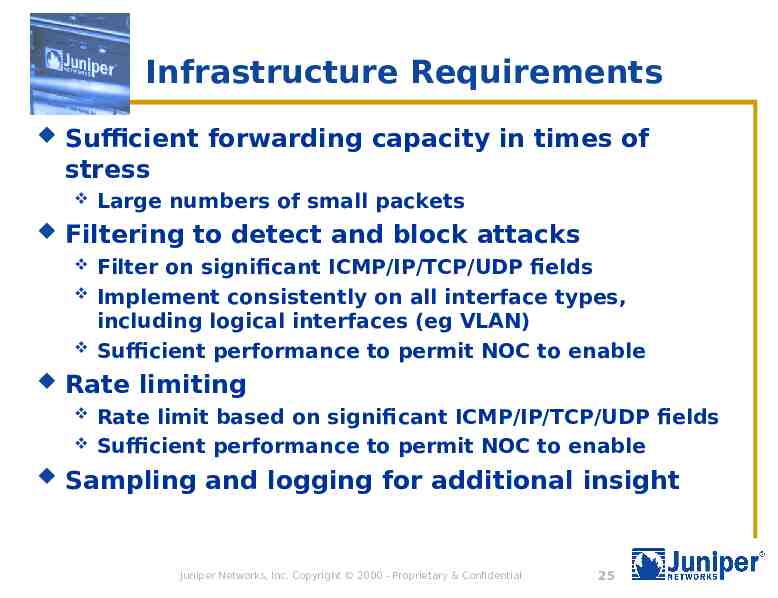
Infrastructure Requirements Sufficient forwarding capacity in times of stress Filtering to detect and block attacks Filter on significant ICMP/IP/TCP/UDP fields Implement consistently on all interface types, including logical interfaces (eg VLAN) Sufficient performance to permit NOC to enable Rate limiting Large numbers of small packets Rate limit based on significant ICMP/IP/TCP/UDP fields Sufficient performance to permit NOC to enable Sampling and logging for additional insight Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 25

Agenda The Impact Of Denial of Service (D0S) Detecting And Minimising DoS SMURF Attacks SYN Attacks Infrastructure Requirements Proactive Measures

Pro-active Approaches Attack Switch Host More reliable and secure network Policy at AS boundaries detect and minimize the effects of DoS attacks Warn NOCs when thresholds are exceeded, and update configurations using scripts to discard the attack Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 27

Proactive Planning Establish procedures for detecting security events Pre-plan response Techniques for isolating problem, tracking it through the network to a source Standard responses to alleviate impact to service Train staff and practice Document and update a security policy Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 28
Further References Juniper Networks Whitepapers Rate-limiting and Traffic-policing Features Fortifying the Core Visibility into Network Operations Minimizing the Effects of DoS Attacks Available from http://www.juniper.net/techcenter Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 29

Thank You [email protected] http://www.juniper.net
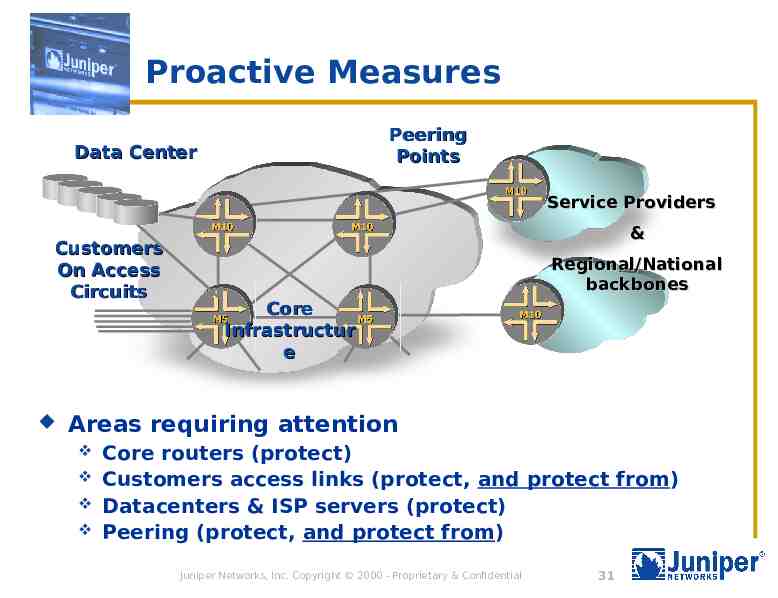
Proactive Measures Peering Points Data Center Service Providers Customers On Access Circuits & Regional/National backbones Core Infrastructur e Areas requiring attention Core routers (protect) Customers access links (protect, and protect from) Datacenters & ISP servers (protect) Peering (protect, and protect from) Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 31
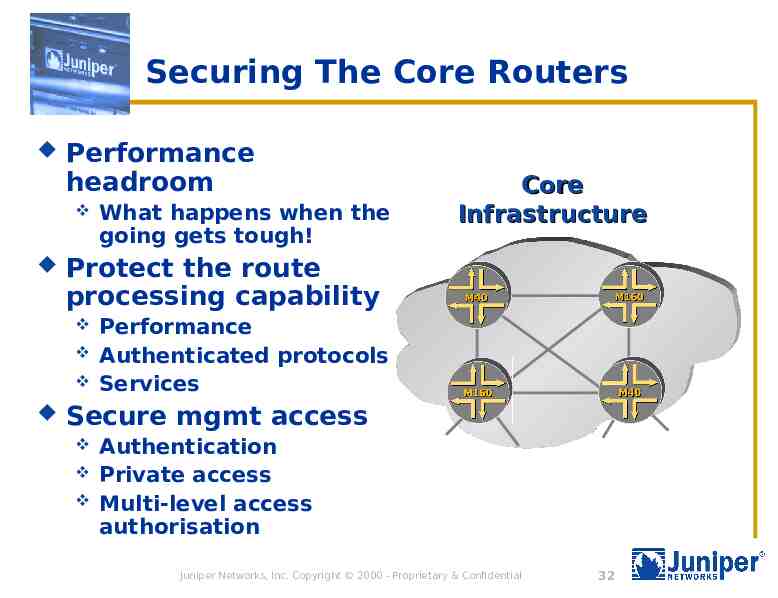
Securing The Core Routers Performance headroom Protect the route processing capability What happens when the going gets tough! Core Infrastructure Performance Authenticated protocols Services Secure mgmt access Authentication Private access Multi-level access authorisation Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 32
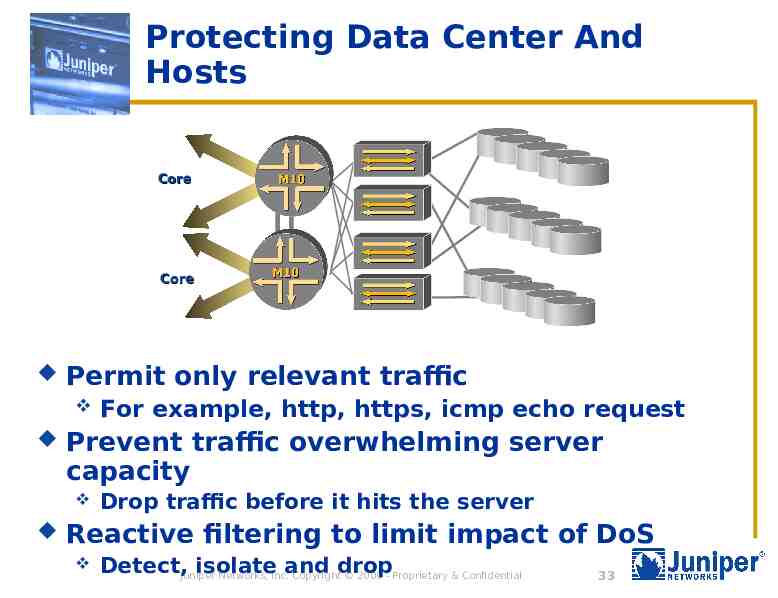
Protecting Data Center And Hosts Core Core Permit only relevant traffic Prevent traffic overwhelming server capacity For example, http, https, icmp echo request Drop traffic before it hits the server Reactive filtering to limit impact of DoS Detect,Juniper isolate and drop Networks, Inc. Copyright 2000 - Proprietary & Confidential 33
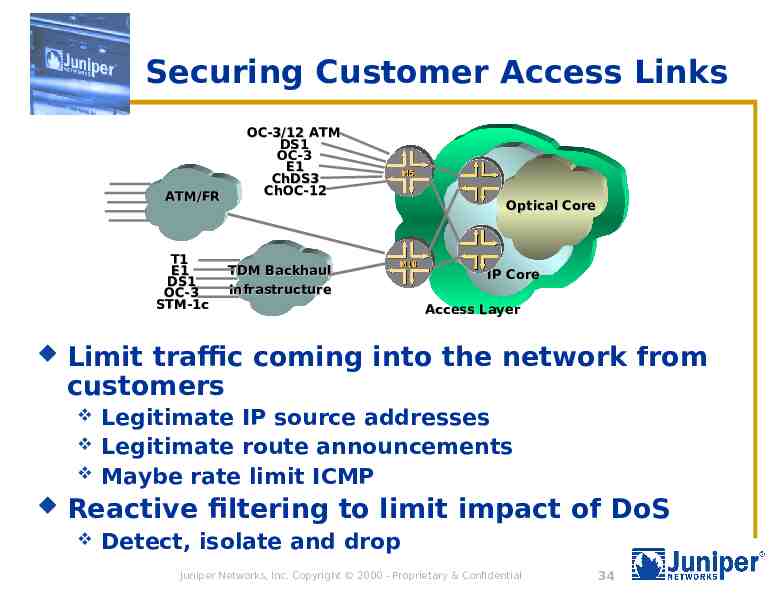
Securing Customer Access Links ATM/FR T1 E1 DS1 OC-3 STM-1c OC-3/12 ATM DS1 OC-3 E1 ChDS3 ChOC-12 TDM Backhaul Infrastructure Optical Core IP Core Access Layer Limit traffic coming into the network from customers Legitimate IP source addresses Legitimate route announcements Maybe rate limit ICMP Reactive filtering to limit impact of DoS Detect, isolate and drop Juniper Networks, Inc. Copyright 2000 - Proprietary & Confidential 34






