Securing Data From Risk Unit 2: Data at Rest This document is
35 Slides1.08 MB

Securing Data From Risk Unit 2: Data at Rest This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Learning Objectives When you finish this unit you will: 2.1 Understand the importance of physically securing data; 2.2 Understand how computers implement protections on files; 2.3 Understand the basis for cryptographic encryption schemes; 2.4 Know how encrypting files and disks on various systems works; 2.5 Understand what data compression is and how it interacts with encryption; 2.6 Know what a digital signature is and how it is used; and 2.7 Understand the general techniques for ensuring availability of data. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

What Does “At Rest” Mean? Focus on data sitting on your computer or a portable hard drive Attackers need access to the storage medium to get the data Assumptions: Attacker has access to the storage medium Attacker does not have authorization to access the data This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Who Cares? Anyone who stores data on a computer that is used by other people School computer, office computer Anyone who uses a portable computer If stolen, the thief can read the stored data; and passwords won’t protect you The ubiquity of smartphones makes this a serious issue! Anyone who puts data onto a portable medium Like a memory stick or portable hard drive This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Systems vs. Storage Media The storage media is what the data resides on May be internal disk or solid state disk (SSD) May be external medium like flash drive, memory stick, portable hard drive May be a network drive (like a Network Appliance system) The system is what manipulates the data It may have the data on internal disks You may have to connect the storage medium to the system This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Physical Controls Make disk containing data inaccessible unless user is physically present Attacker must get into room with disk, or otherwise acquire access to it Warning: must be sure there are no other copies of the data Otherwise attacker can go for those copies! Backups may be an issue here This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Example Sensitive files carried on a portable hard drive or DVD Attacker needs to get access to the disk While disk disconnected, attacker must physically take it While disk connected, attacker can access disk through the computer Image by Santeri Viinamäki From Wikimedia Commons Used under Creative Commons Attribution Share-Alike 4.0 International license This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Virtual Controls These protect the data while it is on the system Access control lists Encryption Digital signatures Replication This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

How Do We Think About Protection? An access control matrix describes who can do what to what Rows have actors, such as users, who will act on permissions Columns have passive entities like files and resources that will be acted upon Rights are a set of symbols representing what actions an actor can take over a passive entity Used as the basis for many access control mechanisms This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Example Jane Kimi Louise paper draw paint write wall draw, paint wallpaper Actors: Jane, Kimi, Louise Passive entities: paper, wall, ground, whiteboard Rights: clean, draw, paint, wallpaper, write This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org ground write draw whiteboard write clean draw

Example (continued) Theodora Ursula Wendy Xanthippe paper.pdf orwd r rwd r moon.avi r orwd d Actors: Theodora, Ursula, Wendy, Zanthippe Passive entities: paper.pdf, moon.avi, report.docx Rights: d (delete), o (own), r (read), w (write) This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org report.docx rw r orwd

Access Control Lists (ACLs) Lists made by going down the columns of access control matrix Theodora Ursula Wendy Xanthippe paper.pdf orwd r rwd r moon.avi r orwd d report.docx rw r orwd paper.pdf: ((Theodoras, orwd), (Ursula, r), (Wendy, rwd), (Xanthippe, r)) moon.avi: ((Theodora, r), (Ursula, orwd)) Report.docx: ((Theodora, rw), (Wendy, r), (Xanthippe, orwd)) This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Example: Linux Uses abbreviated form of ACLs Divide everyone into three sets: “user” of the file: one user (called the owner) “group” of the file: a set of users “other”: everyone not the user or in the group of the file Advantage: much more compact than a full ACL! This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org
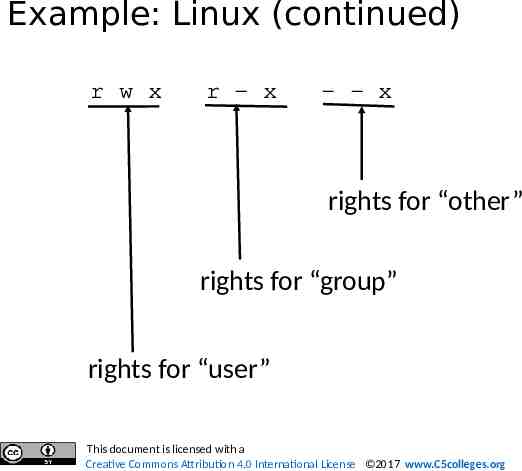
Example: Linux (continued) r w x r - x - - x rights for “other” rights for “group” rights for “user” This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Example: Changing Linux Permissions Do this from the terminal The command ls –l gives information about the file, including the protection bits chmod (change protection mode) changes those protection modes sh-4.3 ls -l xxx -r-xrwx--- 1 bishop user 0 May 12 12:38 xxx sh-4. 3 chmod u w, g-w, o rx xxx sh-4 .3 ls -l xxx -rwxr-xr-x 1 bishop user 0 May 12:38 xxx This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Example: Windows 10 Full control: you can do anything Modify: you can’t delete subfolders and files, change permission, or take ownership but can do anything else Read & execute: you can’t modify or write (including changing permissions or ownership), but you can do anything else Read: you can read but do nothing else Write: you can alter the file or attributes (but not permissions or owner), and read permissions Special permissions: these underlie the others and, with appropriate rights, you can set them individually This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Encryption (continued) Using a piece of information (a key), transform the data (the plaintext) using an algorithm to another form (the ciphertext) Idea: encipher the data If you use a strong cipher, the attacker will be unable to “crack” it Be sure you use a strong cryptographic key, too! AND-encryption: so 2 people must work together to encrypt and decrypt Ann picks a cryptographic key, enciphers the data Bertram picks another cryptographic key, enciphers the result Now to decrypt, Bertram deciphers first, then Ann This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Symmetric Key Encryption One key used to encrypt, decrypt file Common symmetric key algorithms 3DES (Triple DES), TWOFISH, AES192, AES256 Image by Mysid from Wikimedia Commons Released by the author into the public domain This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

How It Works (Symmetric Key Cryptography) “Symmetric Encryption" by Yesem Kurt-Peker, licensed under CC BY 4.0 This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Public Key Encryption One key to encrypt This one is made public (public key) A different key to decrypt This one is kept secret (private key) Chosen such that the private key cannot be derived from the public key Also, private key can’t be derived no matter how many messages you encipher Top image mi brami, bottom from Fred the Oyster from OpenClipArt Released by the authors into the public domain This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

How It Works (Public Key Cryptography) “Asymmetric Encryption" by Yesem Kurt-Peker licensed under CC BY 4.0 Note that no communication is necessary beforehand to agree on a common, shared key This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Some Common Terms Key size: number of units (letters or bits) in the key Caesar cipher has key length of 1 letter Block size: how many units (letters or bits) can be encrypted at once Caesar cipher has a block size of 1 letter This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Data Compression This reduces file size by combining sequences that repeat. Example: The string “aaaaaaaaaa” (10 characters) is replaced by “r10a” (4 characters); the “r” is a command to “replicate” Complication: what happens with the string “r10a”? Answer: use an escape character to indicate the “r” is an ordinary character, so this becomes “rr10a” You can replicate multiple characters like “rabrabrabrabrabrab” (18 characters) as, for example, “r6(rab)” (7 characters) Important: the file must have patterns in it; a file of random characters can’t be compressed (and because of the need to escape characters, will probably be slightly larger) This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Integrity Goal: detect changes to files Easy way: make copies of all files to write-once media Like a CD-R or DVD-R Very expensive in terms of both storage and validation There has to be an easier way! and of course there is! This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Integrity Continued sto rm y a da rk It s wa Compute a cryptographic hash or one-way hash of the data in the file and Really, just a sophisticated math function that crunches the contents to a much shorter set of bits Two sets of data should produce two different checksums Not all will, but you should not be able to find two sets of data that produce the same checksum 98f0d024a25 This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org ni gh t

How Do You Use This? Save the cryptographic hashes To see if the file has changed: Recompute the cryptographic hash of the file Compare this to the stored cryptographic hash associated with the file If they match, the file’s contents produced the cryptographic hash Problem: attacker changes the file’s contents and the stored cryptographic hash This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Digital Signatures Solution: public key cryptography! Encipher the cryptographic hash with your private key Now anyone can find the original hash da rk s wa It a sto rm y and ni gh t Just decipher it using the public key, which everyone knows But no-one can change it They would need to know your private key, which only you know Private key 98f0d024a25 7ed3920a71 This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org store this

Important Note A digital signature is cryptographically based The usual way to do it is with public key cryptography, as in the previous slide 7ed3920a71 A digitized signature is a scan of your paper signature Usually in a GIF or something like that This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Availability Keep enough resources operational to meet quality of service requirements Redundancy: resources are duplicated (or triplicated, or more) so if one fails, the others can detect it and take over In the Space Shuttle, all avionics systems were redundant, in some cases having as many as 4 or 5 duplicate devices Replication: duplicate resources are scattered throughout a set of systems or devices So if the underlying device fails, the resource is still accessible (although elsewhere) This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Replication Make 2 copies of your home key, so if you misplace one, you still have another You replicated the keys Gmail Copies of your mail are kept on servers around the world If one server fails, you are seamlessly switched to another Your mail is replicated for this purpose This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Vendor Encryption You upload the data to the cloud provider. As the cloud provider receives the data, it encrypts the data and stores it. When you request the data, the provider decrypts the data as it sends it to you. The data is encrypted when stored on the cloud provider’s storage. You must trust the cloud provider as it has the key and so can read your data! This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

User Encryption You encrypt the data and then send it to the cloud provider. As the cloud provider receives the data, it stores it. When you request the data, the provider sends it to you and you decrypt it. The data is encrypted when stored on the cloud provider’s storage. You have the key, so you need not trust the cloud provider to keep your data secret. But you have to manage the key you use. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Legal Considerations Sometimes the law constrains where you can store data and how it is protected You must make sure the cloud providers honor these requirements Medical data is controlled by the Health Information Protection Act of America (HIPAA) at the federal level; individual states have additional requirements The law on a third party (law enforcement, etc.) accessing records on a cloud is unclear If the cloud provider has servers all around the world, which nation’s laws apply? This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Conclusion Data at rest is best protected by some form of cryptography So if an attacker accesses it, she can’t read it Physical protection of the media on which the data resides is critical Even if encrypted, the data can be taken by removing the media If you use the cloud, understand who can see your data and how it is protected If you don’t want the provider to be able to read it, encrypt it yourself before you send it to the cloud This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Catalyzing Computing and Cybersecurity in Community Colleges is funded by a National Science Foundation grant and is located at Whatcom Community College 237 West Kellogg Road Bellingham, WA 98226 www.C5colleges.org






