REACHING PCI NIRVANA: ENSURE A SUCCESSFUL AUDIT AND MAINTAIN
46 Slides5.79 MB

REACHING PCI NIRVANA: ENSURE A SUCCESSFUL AUDIT AND MAINTAIN CONTINUOUS COMPLIANCE

TOPICS COVERED What you need to know about the upcoming PCI-DSS version 3.2 How to ensure your network is compliant now, and maintains continuous compliance Identifying the latest vulnerabilities and assessing risk before the auditor does How to reduce the scope of your audit, and instantly generate audit-ready reports PCI and the cloud
SSL AND EARLY TLS The cryptography behind https://server.name.here 2014, 2015: run of attacks against SSL 2.0, 3.0. and TLS 1.0 “Heartbleed”, “FREAK”, “POODLE”, “Logjam” Industry consensus: SSL (all versions), TLS 1.0 “broken beyond repair”

PCI RESPONSE PCI-DSS 3.1 (April 2015): “SSL and early TLS are not considered strong cryptography”.“cannot be used as a security control after June 30, 2016”

SWITCH TO TLS 1.1 / 1.2 ? All modern browsers have supported TLS 1.2 for several years: Chrome - v30 Firefox - v27 Internet Explorer - v11 Opera - v17 Safari - v5 on iOS, v7 on OS X All modern libraries and web-server platforms support TLS 1.2 for several years So switching to TLS 1.2 is easy, right?
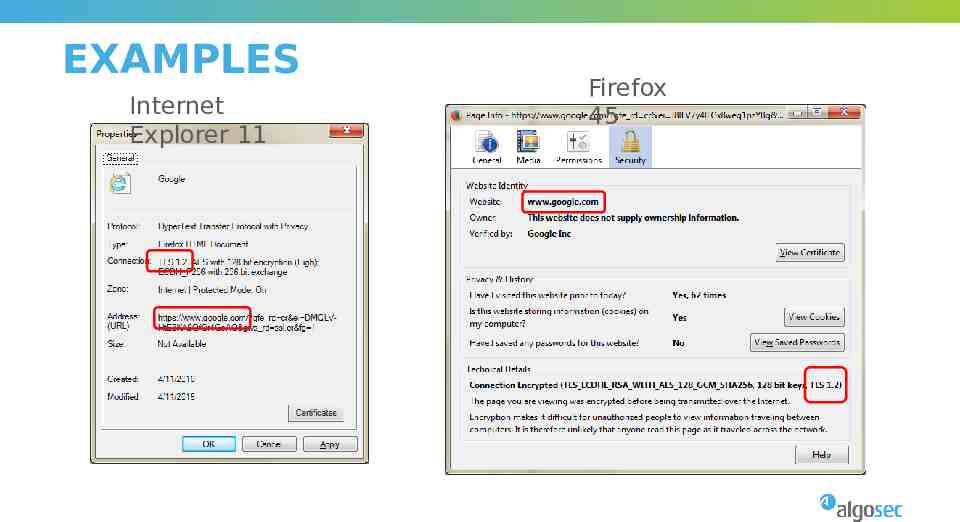
EXAMPLES Internet Explorer 11 Firefox 45
CHECK THE MIDDLEWARE TLS is not only used by browsers and web servers: Machine-to-machine web-service API communication SOAP / REST / etc. Web-page “scraping” utilities Automatic testing platforms E-Mail servers and E-mail clients Embedded web-servers inside devices May need to be upgraded to a TLS-1.2-compatible version Bottom line: Switch to TLS 1.2 requires testing – and time

COMING UP IN PCI 3.2 PCI-DSS 3.2 scheduled for publication at the end of April draft already available to members PCI-DSS 3.1 will be retired Oct 2016 Extending the migration [to TLS 1.1/1.2] date to 30 June 2018 Don’t Wait!

WHAT ELSE IS IN PCI 3.2? From PCI blog: “PCI DSS is a mature standard now” “doesn’t require as significant updates as we have seen in the past” (PCI Blog) From PCI-DSS 3.2 draft: New appendix A.1 for hosting providers Deadline for TLS 1.1/1.2 offering: 30 June 2016 New appendix A.2 focusing on SSL/TLS Other minor changes

COMMON PCI-DSS COMPLIANCE CHALLENGES
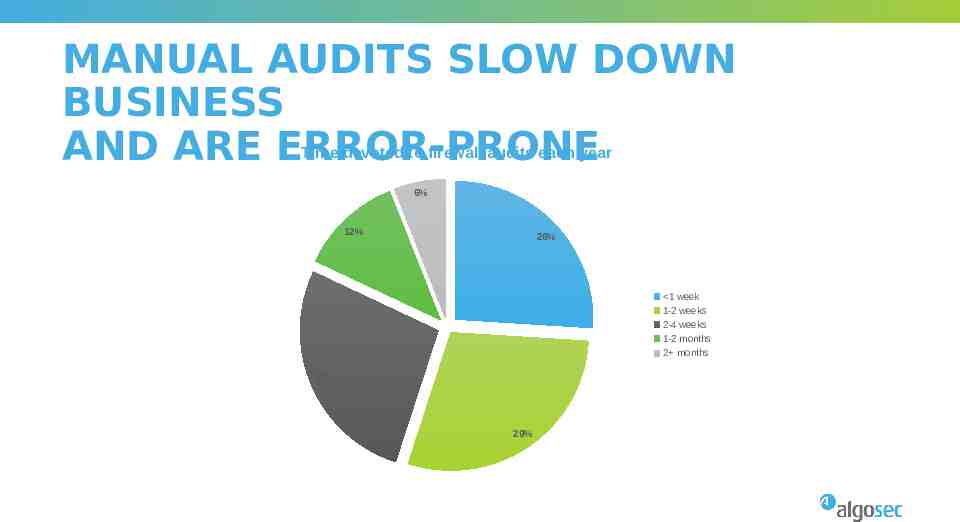
MANUAL AUDITS SLOW DOWN BUSINESS AND ARE ERROR-PRONE Time devoted to firewall audits each year 6% 12% 26% 1 week 1-2 weeks 2-4 weeks 1-2 months 2 months 27% 29%
COMPLIANCE MUST BE CONTINUOUS Report Assess Remediate

PCI-DSS COMPLIANCE WITH ALGOSEC

Manage Security at the Speed of Business AlgoSec simplifies, automates and orchestrates security policy management to accelerate application delivery while ensuring security and compliance. 14 Confidential
KEY CAPABILITIES Secure Business Application Connectivity Security Policy Change Management NGFW and Datacenter Migration Hybrid Cloud Security Security Policy Risk Mitigation Continuous Compliance and Auditing Firewall Policy Optimization
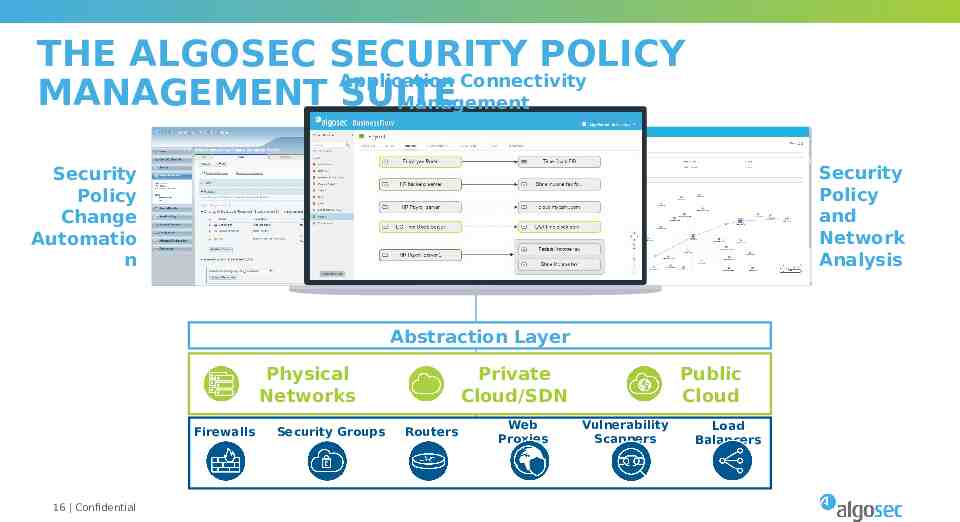
THE ALGOSEC SECURITY POLICY Application Connectivity MANAGEMENT SUITE Management Security Policy and Network Analysis Security Policy Change Automatio n Abstraction Layer Physical Networks Firewalls 16 Confidential Security Groups Private Cloud/SDN Routers Web Proxies Public Cloud Vulnerability Scanners Load Balancers

DEMONSTRATION OF PCI COMPLIANCE WITH THE ALGOSEC SUITE
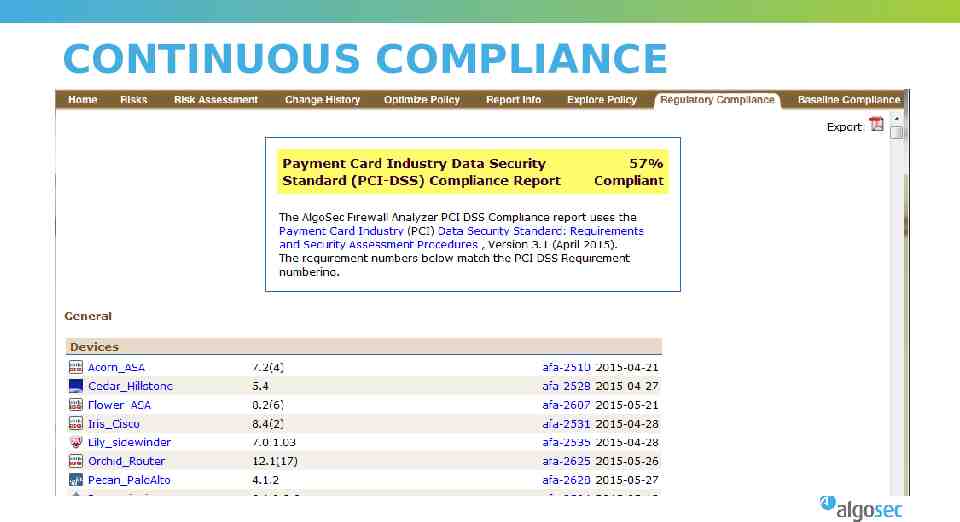
CONTINUOUS COMPLIANCE
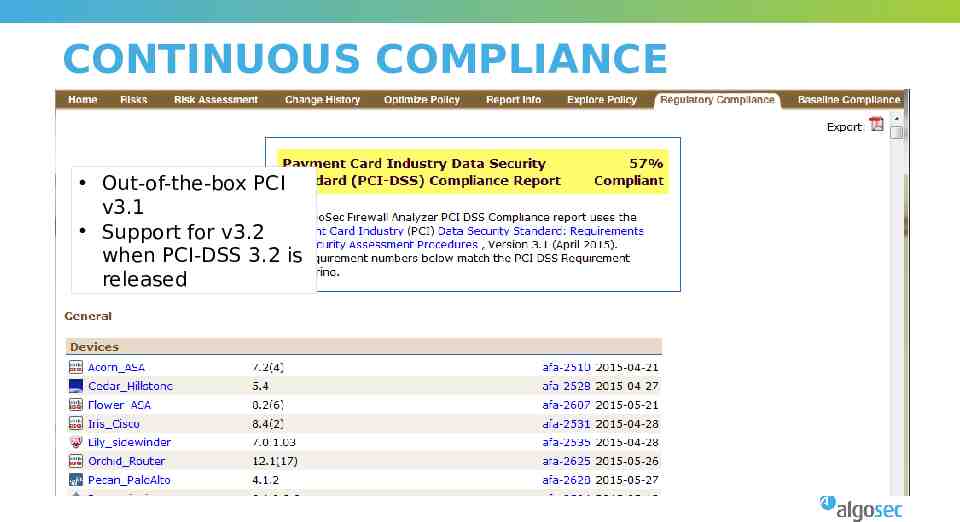
CONTINUOUS COMPLIANCE Out-of-the-box PCI v3.1 Support for v3.2 when PCI-DSS 3.2 is released
CONTINUOUS COMPLIANCE Exportabl e
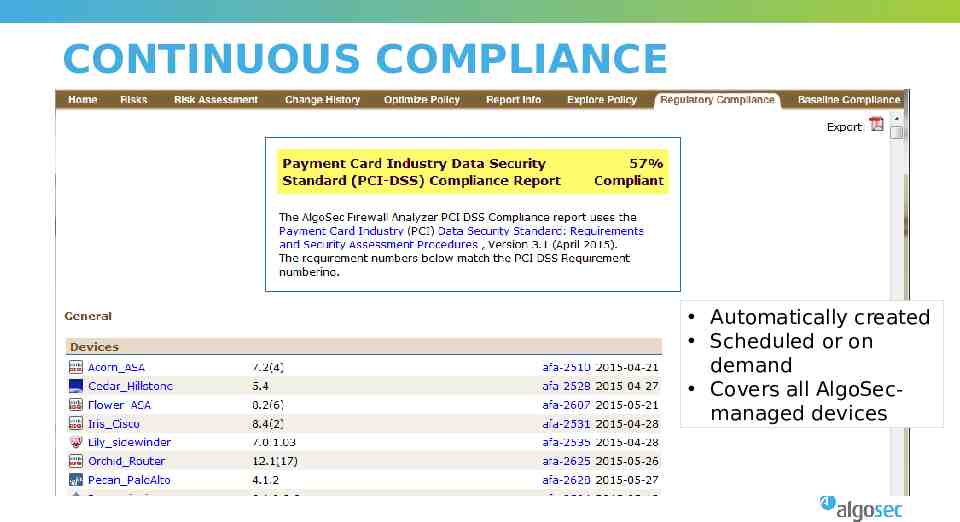
CONTINUOUS COMPLIANCE Automatically created Scheduled or on demand Covers all AlgoSecmanaged devices
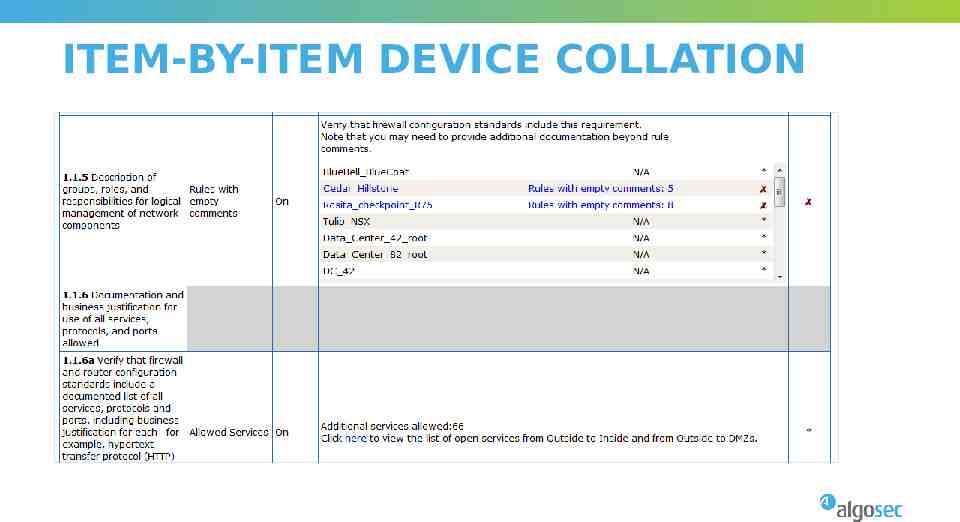
ITEM-BY-ITEM DEVICE COLLATION
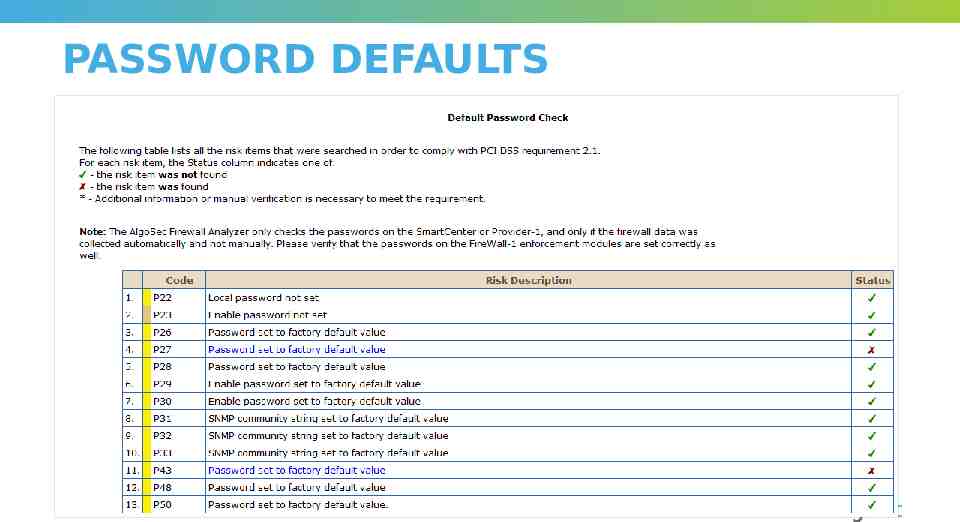
PASSWORD DEFAULTS
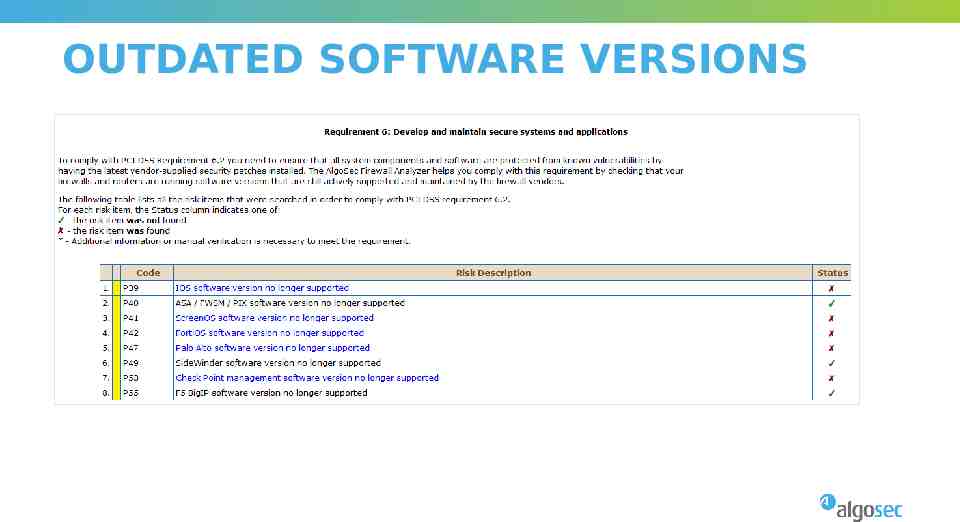
OUTDATED SOFTWARE VERSIONS
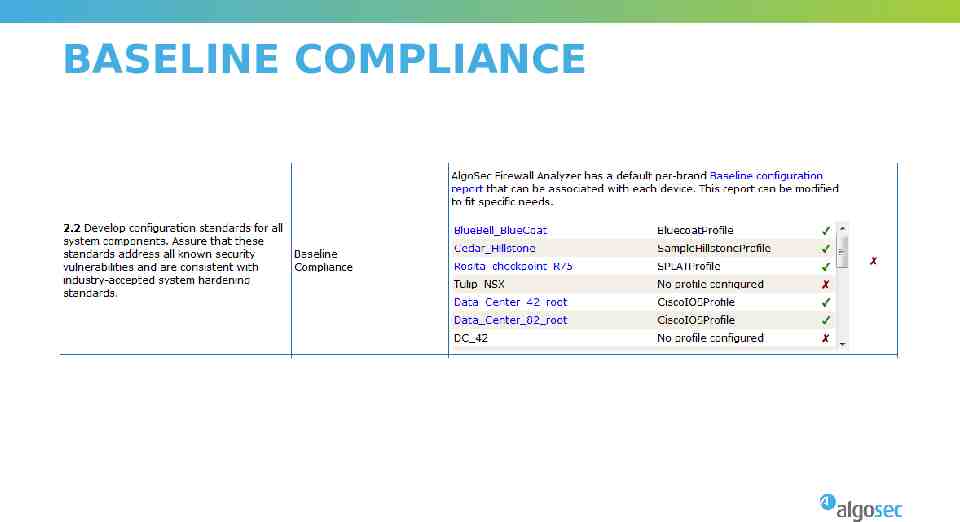
BASELINE COMPLIANCE

BASELINE COMPLIANCE Use AlgoSec Baselines Or Customize your own

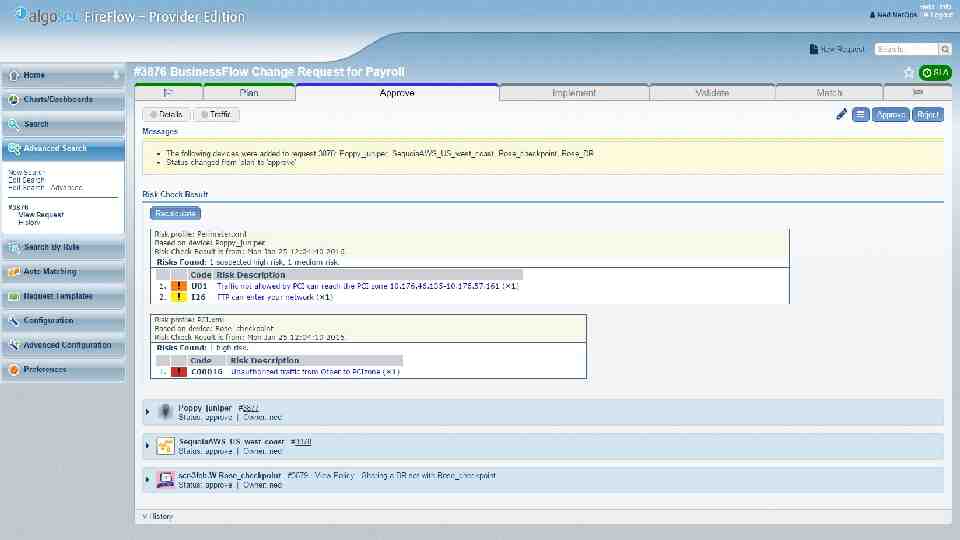
CHANGE PROCESS AlgoSec provides an application-aware workflow system for network security change management AlgoSec PCI group compliance reports on how the AlgoSec system is configured
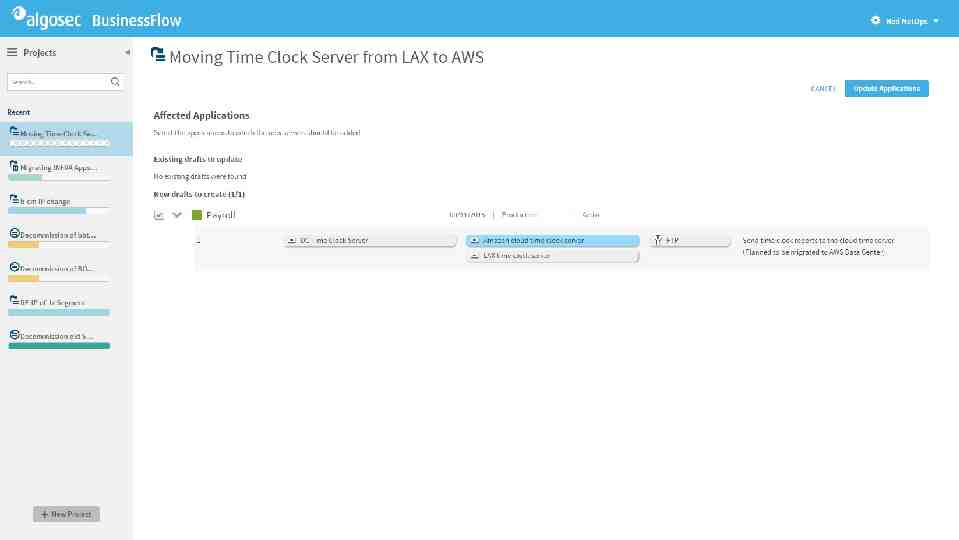
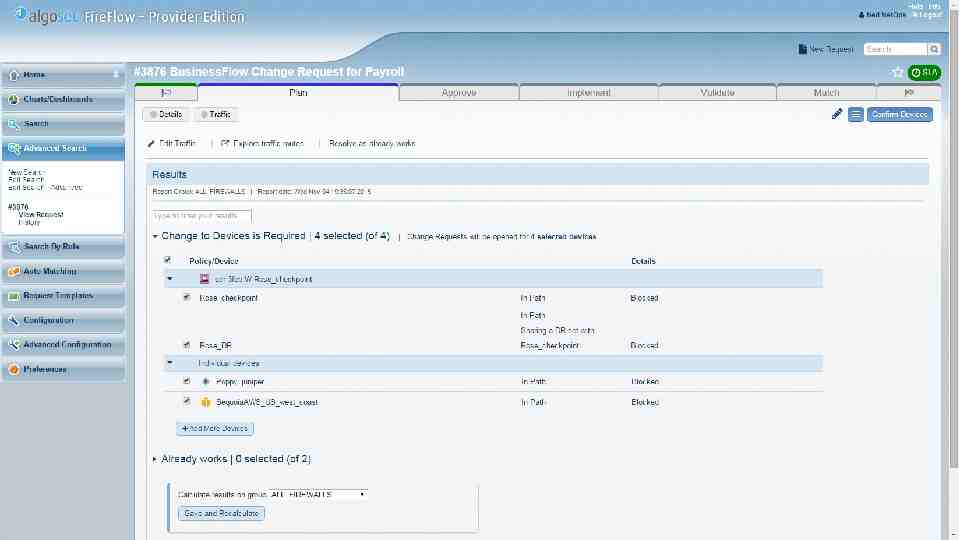
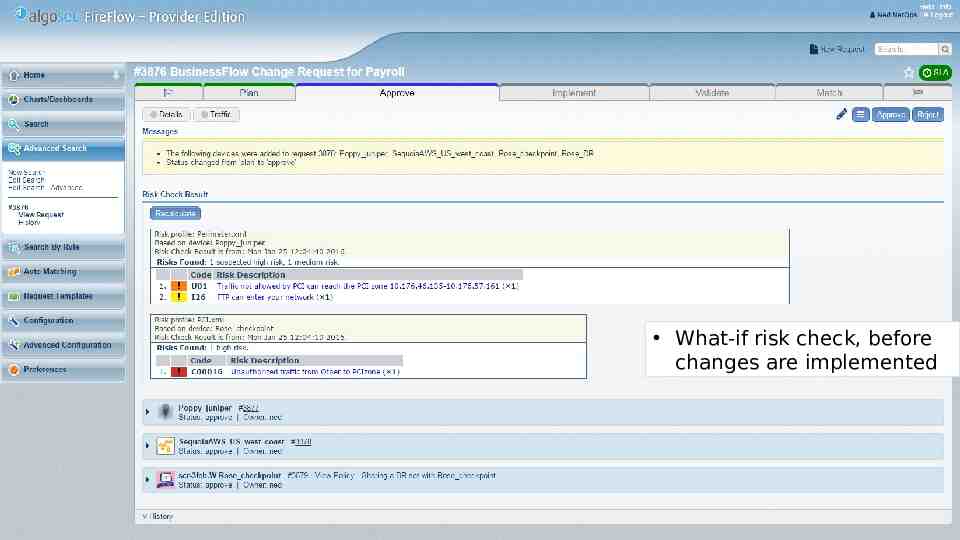
What-if risk check, before changes are implemented
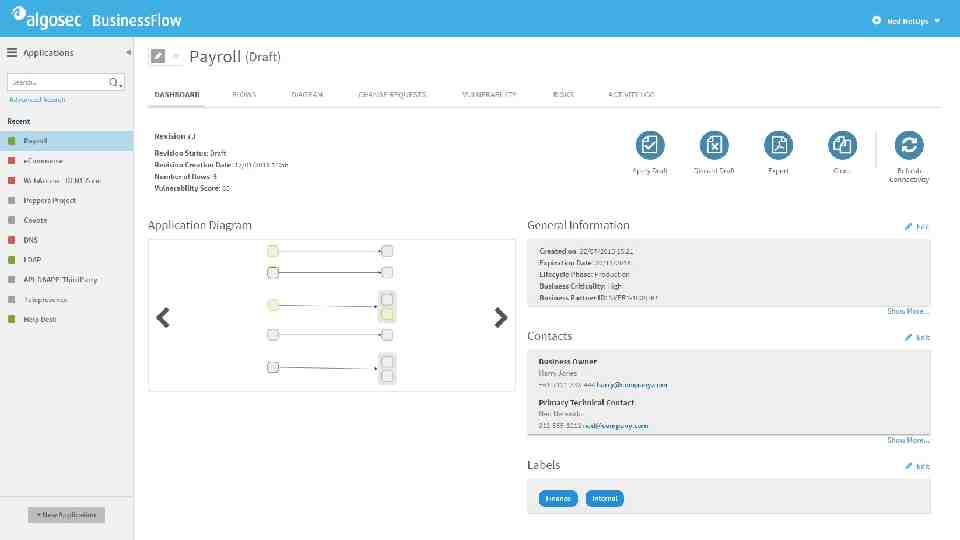
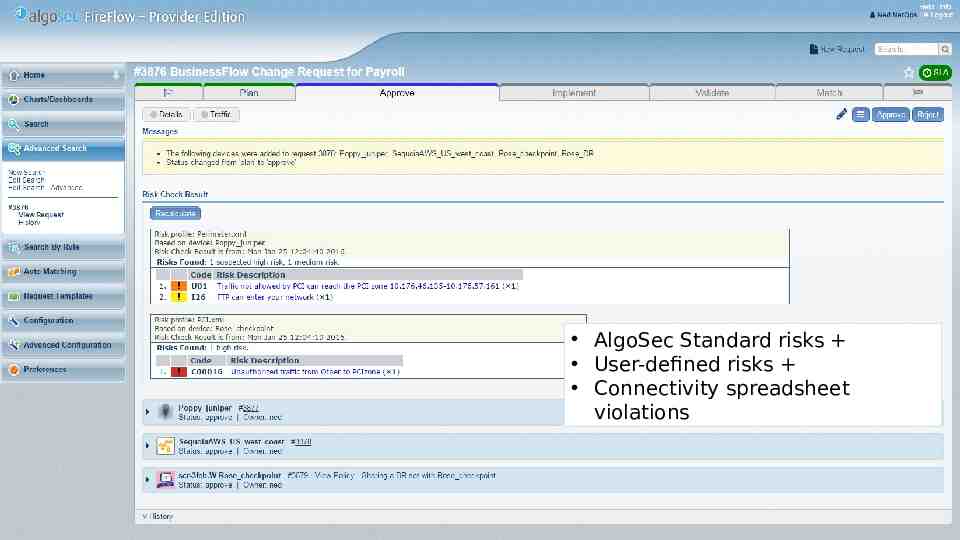
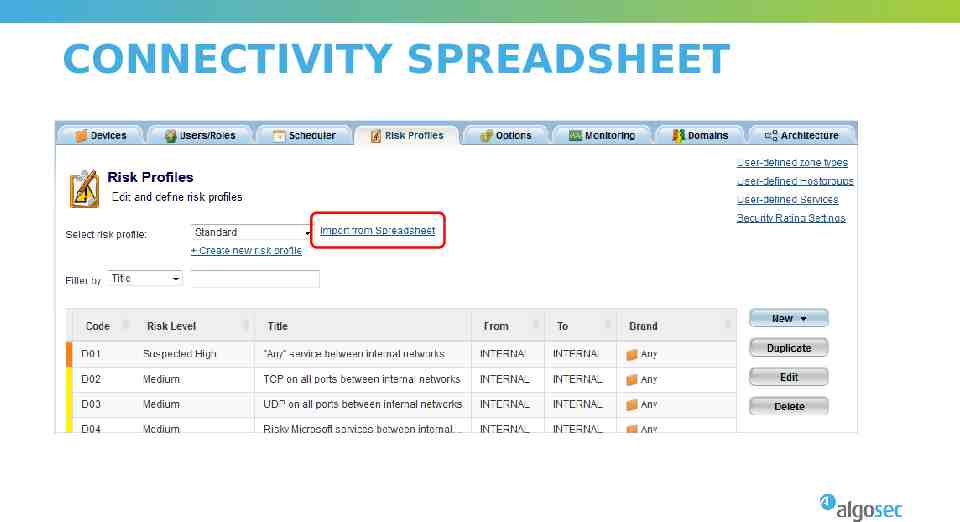
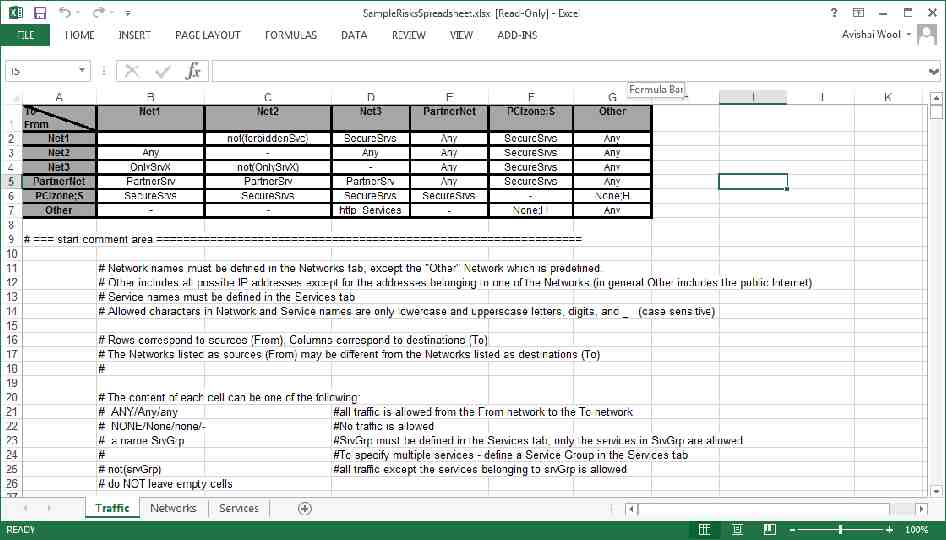
AlgoSec Standard risks User-defined risks Connectivity spreadsheet violations
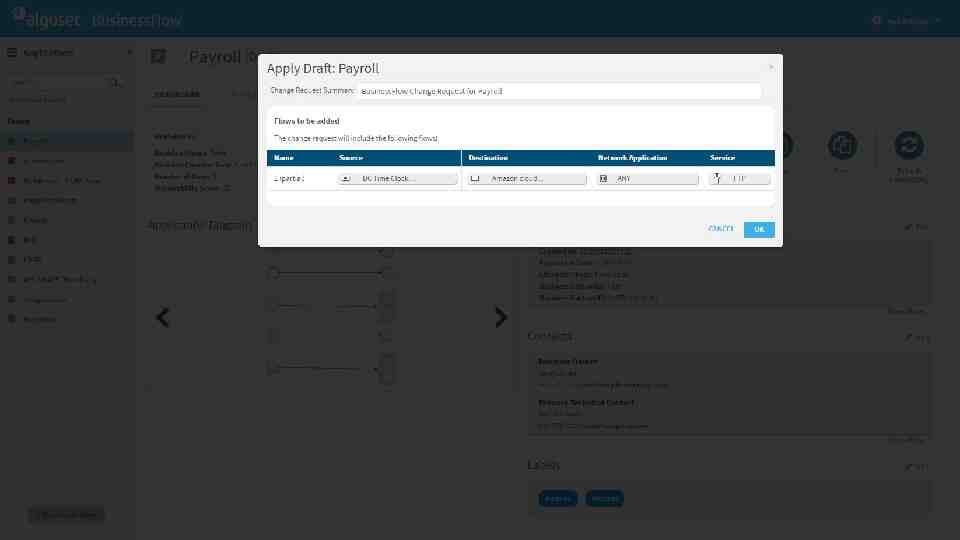
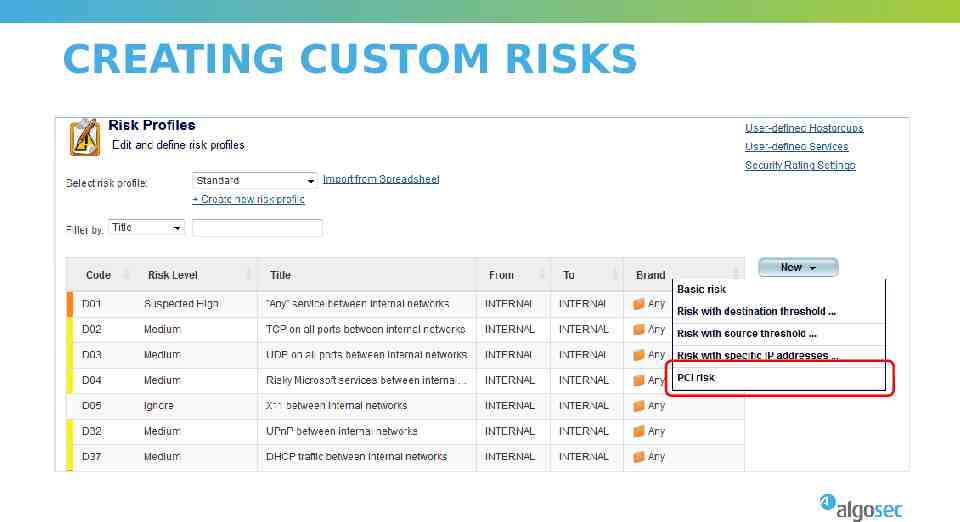
CREATING CUSTOM RISKS
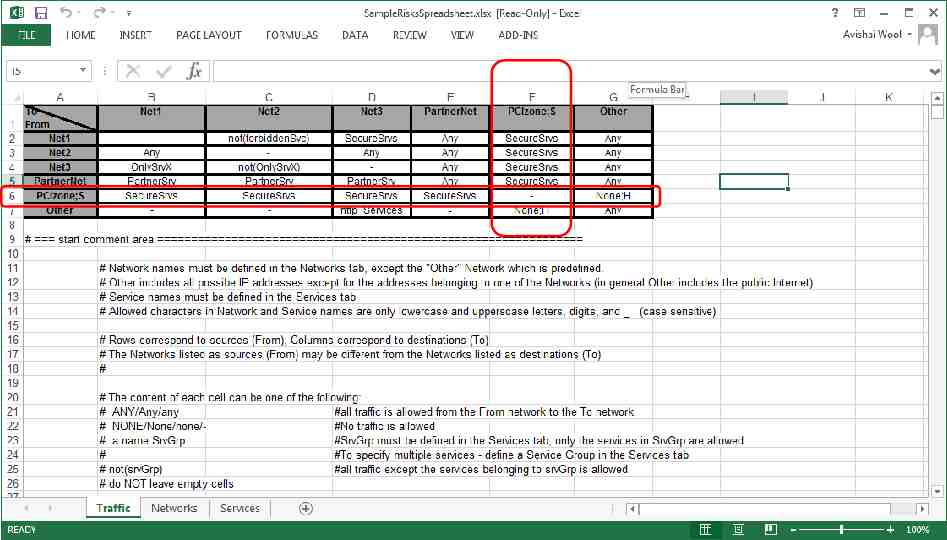
CONNECTIVITY SPREADSHEET
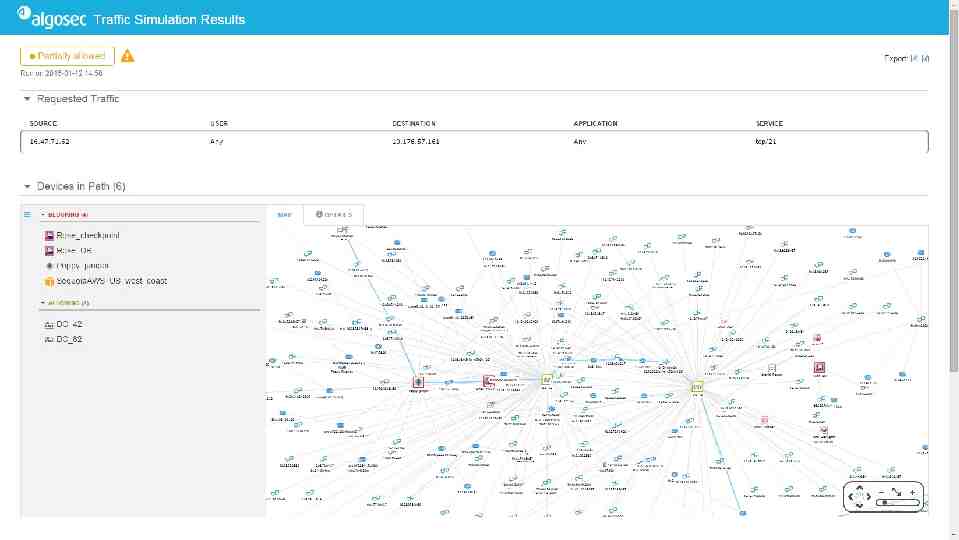
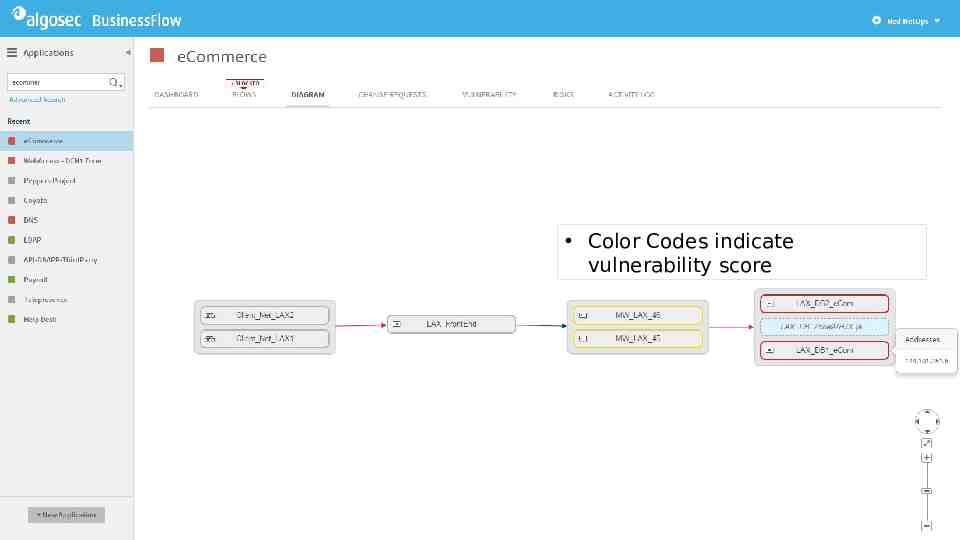
Color Codes indicate vulnerability score
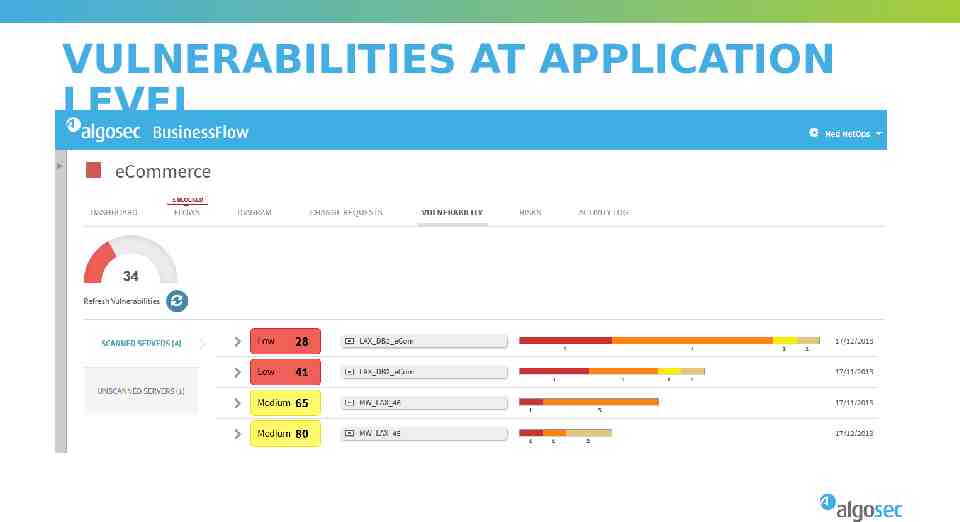
VULNERABILITIES AT APPLICATION LEVEL
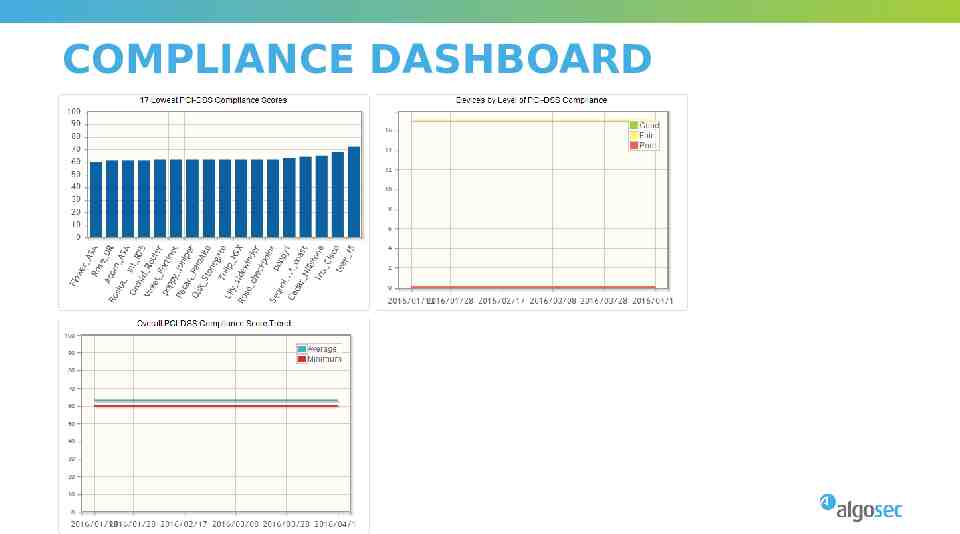
COMPLIANCE DASHBOARD
PCI COMPLIANCE FOR CLOUD Credit-card-processing systems in cloud: same requirements apply but different technologies are in use AlgoSec provides same capabilities for cloud, hybrid, private and legacy environments
SUMMARY PCI 3.2 brings extended timeframe for TLS 1.1/1.2 deployment and some minor updates to the standard itself Continuous compliance to instantly generate audit-ready reports Connectivity and vulnerability reporting per business application “What-if” risk assessment as part of the change workflow PCI and the cloud
MORE RESOURCES
THANK YOU