Randy Beavers CS 585 – Computer Security
17 Slides2.63 MB

Randy Beavers CS 585 – Computer Security

Software Assurance: An Overview of Current Industry Best Practices Software underpins information infrastructure. Organizations widely and increasingly use COTS software. Cyber attacks are becoming more stealthy and sophisticated, creating a complex environment.

Software Assurance: An Overview of Current Industry Best Practices Vendors have undertaken significant efforts to improve and protect software integrity. Software Assurance critical to public safety and economic and national security. Shows how SAFECode members approach software assurance, and how to use best practices for software development.

Software Assurance: An Overview of Current Industry Best Practices Software Assurance Forum for Excellence in Code. A non-profit organization exclusively dedicate to increasing trust in information and communications technology products and services through the advancement of proven software assurance methods.

Software Assurance: An Overview of Current Industry Best Practices Founded by: EMC Corporation Juniper Networks, Inc. Microsoft Corporation SAP AG Symantec Corporation Website: www.safecode.org

Software Assurance: An Overview of Current Industry Best Practices The Challenge of Software Assurance and Security Software Assurance encompasses the development and implementation of methods and processes for ensuring that software functions as intended while mitigating the risks of vulnerabilities, malicious code or defects that could bring harm to the end user.

Software Assurance: An Overview of Current Industry Best Practices Software Assurance: Vital to ensuring the security of critical information. Information and communications technology vendors have responsibility to address assurance in every stage of application development. Integrators, operators, and end users share responsibility for ensuring security of critical information systems.

Software Assurance: An Overview of Current Industry Best Practices Software assurance risks faced by users today can be categorized in three areas: 1. Accidental design or implementation errors. 2. The changing technological environment. 3. Malicious insiders.
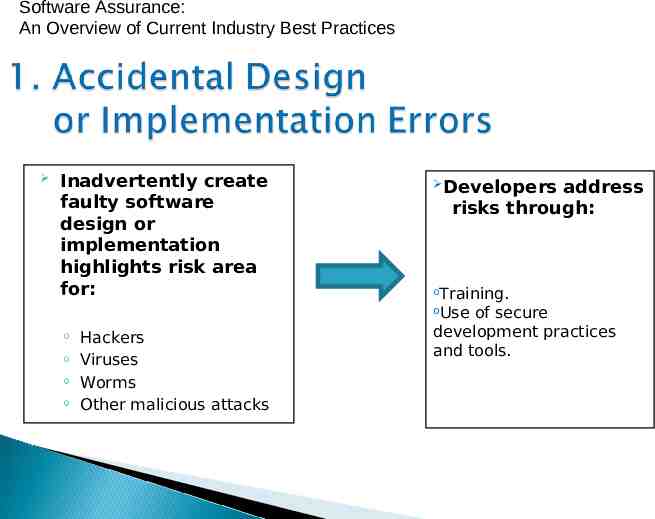
Software Assurance: An Overview of Current Industry Best Practices Inadvertently create faulty software design or implementation highlights risk area for: Developers address risks through: oTraining. oUse Hackers Viruses Worms Other malicious attacks of secure development practices and tools.

Software Assurance: An Overview of Current Industry Best Practices Rapid change and innovation are characteristics of the IT industry. Criminals can and do innovate also. They have created a complex and lucrative criminal economy. The process is one of on-going improvement as new threats are created, and new countermeasures developed and implemented.

Software Assurance: An Overview of Current Industry Best Practices Growing concern that global software development processes could be exploited by a rogue programmer or organized group of programmers. There are proven best practices that companies use to manage their unique development infrastructure and business models.

Software Assurance: An Overview of Current Industry Best Practices Vendors have responsibility and business incentive to ensure product assurance and security. Customers demand software be secure and reliable. Vendors must protect brand names and company reputations.

Software Assurance: An Overview of Current Industry Best Practices Software development varies by vendor and unique products, organizational structure, and customer requirements. No single method that yields software assurance and security. Regardless, there is a core of best practices for software assurance and security.

Software Assurance: An Overview of Current Industry Best Practices

Software Assurance: An Overview of Current Industry Best Practices Across SAFECode’s membership, security best practices and controls are well established: Security Training Security Documentation Defining Security Requirements Security Readiness Secure Design Security Response Secure Coding Integrity Verification Secure Source Code Handling Security Research Security Testing Security Evangelism

Software Assurance: An Overview of Current Industry Best Practices INTEGRATORS. Work in partnership with vendors to mitigate vulnerabilities. OPERATORS. Must deploy standard layered defense security measures. END USERS. Responsible software use a requirement for software assurance and security.

www.safecode.org






