MONDRIAN: Comprehensive Inter-domain Network Zoning Architecture
27 Slides2.35 MB

MONDRIAN: Comprehensive Inter-domain Network Zoning Architecture Jonghoon Kwon Claude Hahni ETH Zurich ETH Zurich Zurcher Kantonalbank [email protected] [email protected] [email protected] Presented by: Willis Trapp CSCE 715 Spring 2023 Patrick Bamert Adrain Perrig ETH Zurich [email protected]

Presentation Abstract one of the critical elements of designing IT security infrastructures is the segmentation of information groups into network zones sharing the exact security requirement and policies. Many businesses in today’s world ecosystems are migrated to the cloud, making network zoning operations manageable for a large-scale network. Intre-domain transit zone information securely into another zone’s largescale information system.

Why Network Zoning Important Network zoning has long been an essential part of the Internet security infrastructure. protect the network, detect unauthorized access, and protect confidential, integrity, and sensitive data. It groups segments into zones that share the same security and requirement policies It is a set of boundaries that you can use to grant access or restrict access to a network system. Determine how's traffic flows and is filtered at the entry point
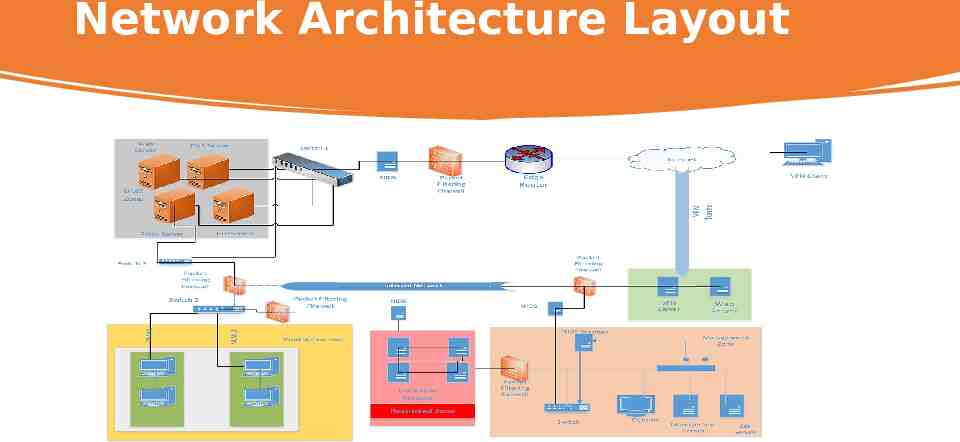
Network Architecture Layout

Mondrian Is a new network zoning architecture that secures inter-zone communication, which operates on layer 3. ensuring scalable cryptographic-key management and flexible security policy enforcement. MONDRIAN provides strong transparent, and efficient controls, minimizing human error and enhancing the security of enterprise networks.
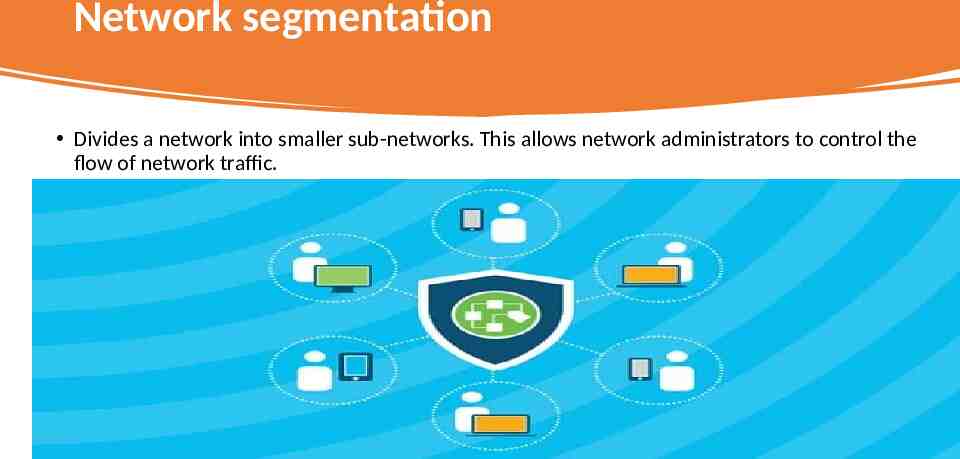
Network segmentation Divides a network into smaller sub-networks. This allows network administrators to control the flow of network traffic.

Network Firewall Security Firewalls are network security systems widely used for filtering inbound and outbound data traffic to protect a host and protect against unauthorized access and malicious attacks. A stateful packet inspection firewall- maintains a state information record that flows through the network system, such as a transmission control protocol (TCP) handshaking between the local and remote hosts. An application-level gateway firewall works as a proxy, with the ability to check the contents of the network traffic and block malicious traffic. Accepts traffic that meets the firewall policies Traffic that doesn’t meet access policies will be blocked Prevent information from being leaked Record user activity
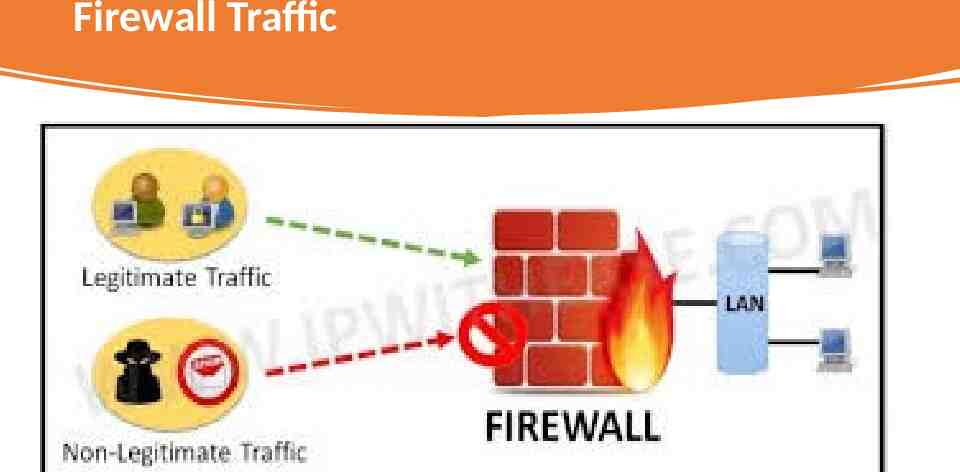
Firewall Traffic

Case Study Over time, the layered network structure has become more sophisticated due to extreme changes in network environments Intra-domain Zone Transition. Within a local network, multiple devices such as servers, databases, and hosts are connected through network switches Inter-domain Zone Transition. To ensure that geographically distributed zones can securely communicate with each other, enterprises employ various networking technologies.
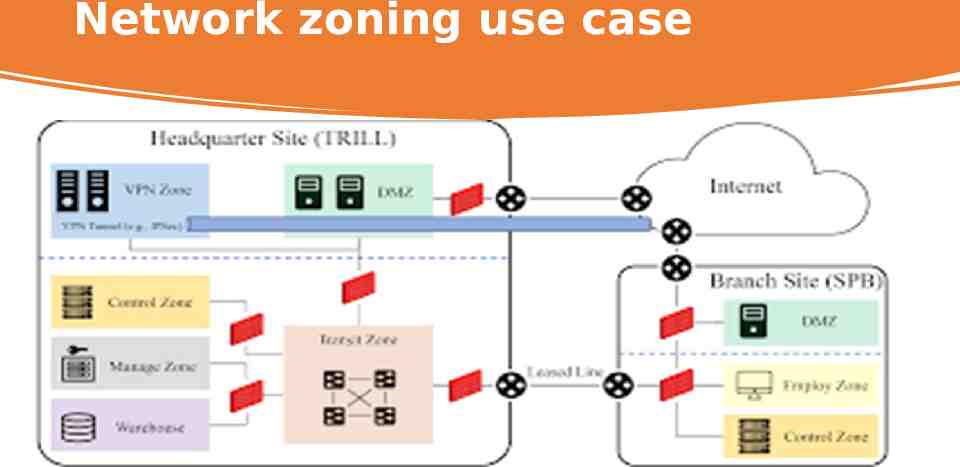
Network zoning use case

Network Zones Transition and Challenge Security Zone Transition allows sensitive data to be transmitted between zones in different locations. However, data can get lost in transition, requiring the data to be re-authenticated on the receiver site. Interoperability, Support seamless interconnection between security zones in different networks. The problem is that different zones might not be on the same internal protocols, making communication difficult between other zones. Management Scalability, dealing with local network zoning architecture grant or restrict access to computers and devices in the organization; The issue with zoning architecture adding new zoning requires reviews updated and redistributed to the network system.
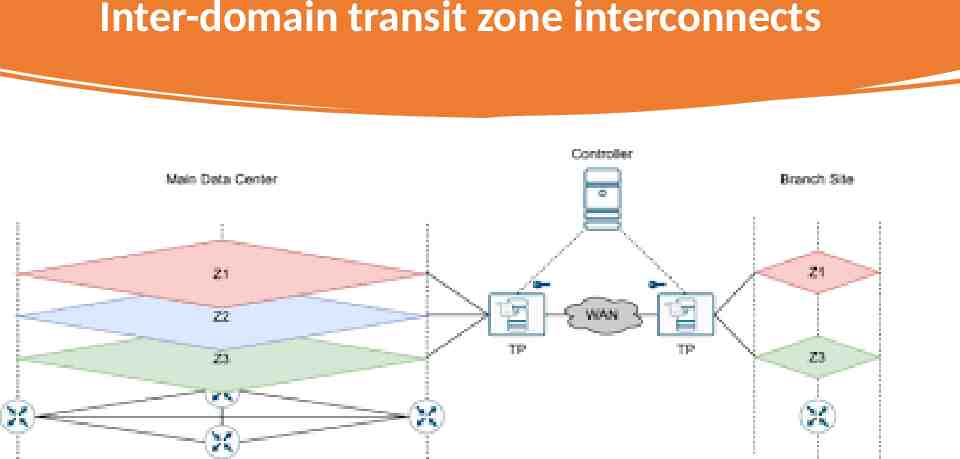
Inter-domain transit zone interconnects
Overview of Mondrian Data confidentiality: through a constructive approach, the zone transition protocol ensures that no information is exposed while being transmitted via the public Internet. Management scalability: Allows network administrators to easily migrate network topologies, update policies and mirror abstract network zones into the actual network Efficiency: the cryptographic primitives introduce only minor performance overhead regarding latency, bandwidth, and operational costs. Deplorability: the MONDRIAN architecture requires minimal changes to the existing network infrastructure to achieve compatibility. Furthermore, firewalls and VPN devices at each entry point of every zone can be replaced with one MONDRIAN gateway, saving operational costs for the same level of network security.

Traffic from the Internet The network can be classified into three types of traffic Public Traffic Authorized Traffic Malicious Traffic

Communication Flow Network administrator establish an IP zone map and transition policies, These policies allow a virtual network configuration and reachability Each pair of TPs exchanges symmetric keys to establish a secure channel. The on-site TP inspects all the packets to be transmitted to another zones If the packet is authorized, the TP looks up the respective endpoint TP and encrypts the packet along with the corresponding zone transition information The remote site TP then decrypts the packet and forward it according to the enclosed zone transition information

Threat Model Unauthorized Access, Attackers may appear as the authorized person to access restricted zones. To override the security system by directly injecting tampered policies. Denial- of-Service attack aims to disrupt the network or services by flooding security middleboxes that perform deep packet inspection.

Zoning Policy Allow network operator to explicitly express their zone transition policies. IP subnet Corresponds to exactly one network zone; the zone identifier (zoneID) of a host can be identified by the host IP address, IP addresses of each host in an enterprise’s network are unique, ensuring inter zones (inter-VLAN) routing. Every zone is under one administration domain in case multiple companies want to collaborate by sharing certain network zones,
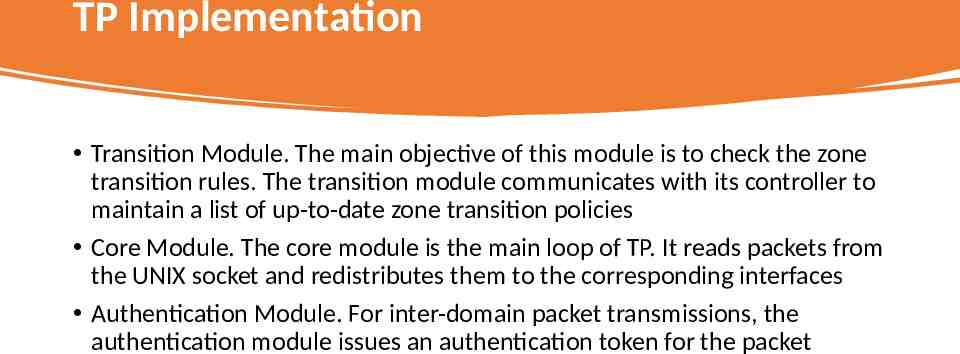
TP Implementation Transition Module. The main objective of this module is to check the zone transition rules. The transition module communicates with its controller to maintain a list of up-to-date zone transition policies Core Module. The core module is the main loop of TP. It reads packets from the UNIX socket and redistributes them to the corresponding interfaces Authentication Module. For inter-domain packet transmissions, the authentication module issues an authentication token for the packet
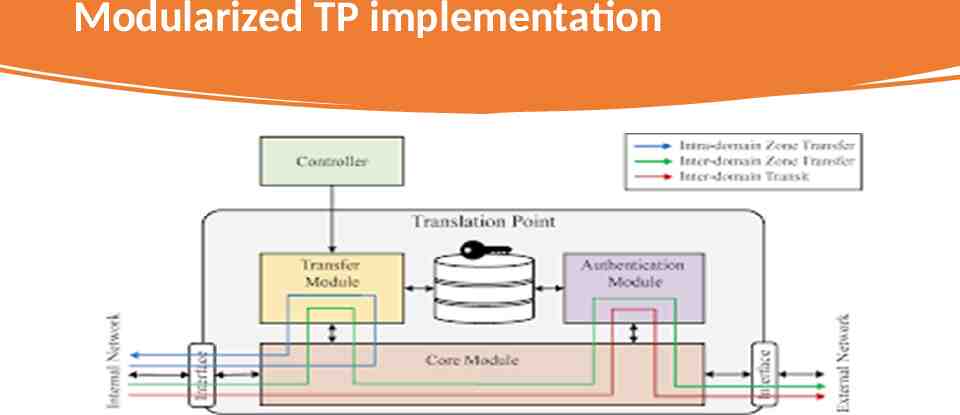
Modularized TP implementation

EVALUATION Authorization. From a technical perspective, the zone transition authorization is a database lookup consisting of three tree searches; upon receiving the packet metadata from the core module, the transition module first looks up the corresponding zone identifiers for the source and destination addresses. Key Derivation. Investigate the key derivation performance. Authentication. The additional processing time for packet encryption and decryption
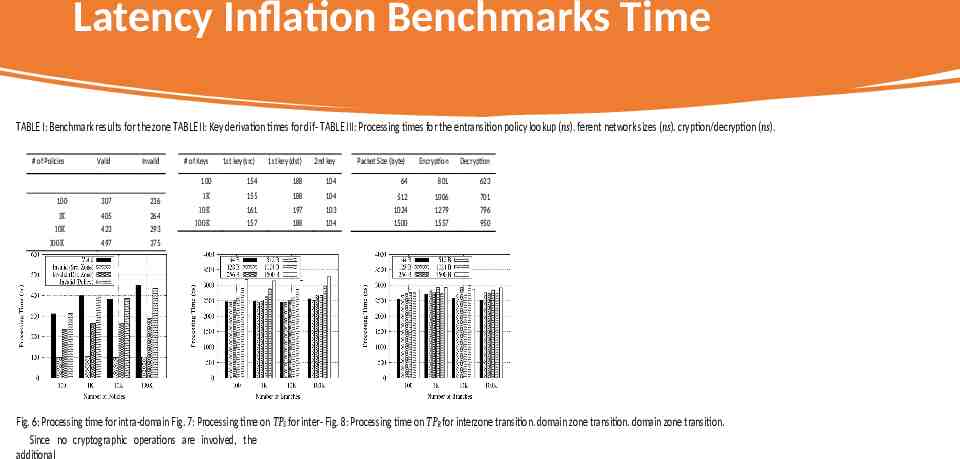
Latency Inflation Benchmarks Time TABLE I: Benchmark results for the zone TABLE II: Key derivation times for dif- TABLE III: Processing times for the entransition policy lookup (ns). ferent network sizes (ns). cryption/decryption (ns). # of Policies Valid Invalid 100 307 236 1K 10K 100K 405 423 497 264 293 375 # of Keys 1st key (src) 1st key (dst) 2nd key Packet Size (byte) Encryption Decryption 100 154 188 104 64 801 623 1K 10K 100K 155 161 157 188 197 188 104 103 104 512 1024 1500 1006 1279 1557 701 796 950 Fig. 6: Processing time for intra-domain Fig. 7: Processing time on TPS for inter- Fig. 8: Processing time on TPR for interzone transition. domain zone transition. domain zone transition. Since no cryptographic operations are involved, the additional
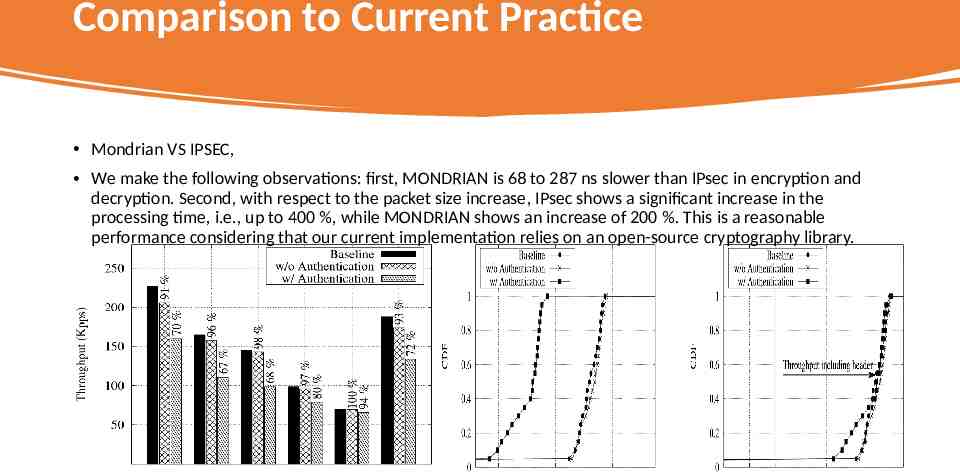
Comparison to Current Practice Mondrian VS IPSEC, We make the following observations: first, MONDRIAN is 68 to 287 ns slower than IPsec in encryption and decryption. Second, with respect to the packet size increase, IPsec shows a significant increase in the processing time, i.e., up to 400 %, while MONDRIAN shows an increase of 200 %. This is a reasonable performance considering that our current implementation relies on an open-source cryptography library.

Coordination. It is important to keep consistency across the distributed controllers. Inconsistency in security policy might grant hosts with a low-security clearance unauthorized access to restricted zones, resulting in leakage

SECURITY ANALYSIS Man-In-The-Middle Attack, The attack could initiate independent communication channels with two TPs and relay messages between them using the attacker’s public key for channel establishment. Packet Replay, The attackers can observe Mondrian packet and attempt to reuse them to transmit attack traffic. Brute-force Attack, The attacker could brute force the using keys used for authentication.

Relate Work VLAN is the most frequently used network segmentation technique. It logically segments a physical LAN into up to 4094 virtual LANs by tagging the layer 2 header with a unique VLAN identifier (VID) Virtual eXtensible LAN (VXLAN) has been introduced for better scalability; it expands the number of virtual LANs to up to 16 million by leveraging a 24bit identifier. SVLAN architecture enhancing security in network isolation by enforcing the receiver’s consent towards incoming traffic.

CONCLUSION Network zoning has long been recognized as the cornerstone of secure network operation and management. In the current practice, operators realize network zones with network segmentation technologies and security middleboxes. This presentation shows that lightweight policy enforcement for inter-zone communication is achievable. MONDRIAN consequently reduces the number of management points of distributed networks while retaining a high degree of security.

THANKS!